(Find the index of the smallest element) Write a function that returns the index of the smallest element in a list of integers. If the number of such elements is greater than 1, return the smallest index. Use the following header: def indexOfSmallestElement(lst): Write a test program that prompts the user to enter a list of numbers, invokes this function to return the index of the smallest element, and displays the index.
Answers
Answer:
Here is the function that returns the the smallest element in a list of integers
def indexOfSmallestElement(lst):
smallest = lst.index(min(lst))
return smallest
Explanation:
The function indexOfSmallestElement() takes a list of integers lst as parameter.
smallest = lst.index(min(lst))
In the above statement two methods are used i.e. index() and min().
The first method index returns the index position of the list and the second method min() returns the minimum element of the list.
Now as a whole the statement min() first returns the smallest element in the list (lst) of integers and then the index() method returns the position of that minimum element of lst. At the end the index position of this smallest element in the list (lst) is stored in the smallest variable.
So lets say if we have a list of the following elements: [3,2,1,7,1,8] then min() returns the smallest element in this list i.e. 1 and index() returns the index position of this smallest element. Now notice that 1 occurs twice in the list and index() method only returns the the first index found in the list. So it returns the smallest index of the two index positions of 1 i.e 2. Hence the output is 2.
The test program is given below:
lst=list()
num=int(input("Enter the list size: "))
print("Enter a list of numbers: ")
for i in range(int(num)):
integers=int(input(""))
lst.append(integers)
print("The index of the smallest element is: ")
print(indexOfSmallestElement(lst))
First the list named lst is created. After that the user is prompted to enter the size of the list which determines how many elements user wants to add to the list. num holds the size input by user. After that print statement displays the line"Enter a list of numbers: ". Next the for loop takes the integers from user num times. Suppose user want to enter 3 as list size then loop will take 3 elements from user. int(input("")) in this statement integer type input is taken from user using input() method. lst.append(integers) statement is used to append these input integers into the list i.e. lst. print(indexOfSmallestElement(lst)) the statement calls the indexOfSmallestElement by passing lst to this method to return the index of the smallest element in the list of integers.
Related Questions
The ____ command replaces the ***** in the syntax of the UPDATE command, shown above.
Answers
SET columnname = expression command replaces the ***** in the syntax of the UPDATE command, shown above.
What is UPDATE Command?The update command is a data manipulation tool used to alter a table's records. It can be used to update a single row, all rows, or a group of rows depending on the user-provided condition.The data level will be affected by the update command. The database's relations (tables) can have their attributes added, removed, or modified using the ALTER command. A database's existing records can be updated using the UPDATE command.The update command is a data manipulation tool used to alter a table's records. It can be used to update a single row, all rows, or a group of rows depending on the user-provided condition.To learn more about UPDATE Command refer to:
https://brainly.com/question/15497573
#SPJ4
Reflect on what you think are the biggest threats posed by a world that increasingly relies on digital data. Almost every aspect of modern life is dependent on computers and the data they process working correctly. From energy to transportation, from banking to commerce, and from health care to food production, computers play a significant part of the process of delivering those services.
What are some of the things that ordinary people can and should do to protect themselves from network attackers?
What are the responsibilities of those that deliver these vital services and what can they do to ensure these services are safe?
Instructions:
Write a post of at least 5 sentences outlining your answers to the above questions about threats to a digital world. Are there things you should be doing differently to protect yourself and others from digital disaster?
Answers
As the world becomes increasingly reliant on digital data, there are several threats that pose significant risks to individuals and society as a whole. One of the biggest threats is cybercrime, including hacking, identity theft, and other malicious activities that can compromise personal information and financial security.
What is the use of computers about?The growing interconnectedness of digital networks also makes them vulnerable to cyber attacks that could disrupt critical infrastructure and public services.
To protect themselves from network attackers, ordinary people should take steps such as using strong passwords, keeping software up-to-date, and being cautious about sharing personal information online. It's also important to be aware of common scams and phishing attempts and to avoid clicking on suspicious links or downloading unknown attachments.
Therefore, Those who deliver vital digital services have a responsibility to ensure the security of their systems and data. This includes implementing robust security measures, conducting regular vulnerability assessments and risk management, and investing in employee training and awareness programs to help prevent insider threats.
Learn more about computers here:
https://brainly.com/question/24540334
#SPJ1
A hard disk drive has 10 surfaces, 10240 tracks per surface, and 512 sectors per track. Sector size is 4 KB. The drive head traverses 1280 track/ms and the spindle spins at 5400 r.p.m.
(a) What is the total capacity of hard disk drive (in GB)?
(b) What is the physical address of the sector whose logical block address (LBA) is 2312349 ?
(c) What is the longest time needed to read an arbitrary sector located anywhere on the disk?
Answers
(a) The total capacity of the hard disk drive is 10 surfaces * 10240 tracks/surface * 512 sectors/track * 4 KB/sector = 204800 MB = 200 GB.
What is the physical address of the sector?(b) The physical address of the sector with LBA 2312349 is calculated as: surface = LBA/(trackssectors) = 2312349/(10240512) = 4; track = (LBA%(trackssectors))/sectors = (2312349%(10240512))/512 = 2512; sector = LBA%sectors = 2312349%512 = 85.
So, it's (4, 2512, 85).
(c) The longest time to read an arbitrary sector is from the outermost track to the innermost track (10240 tracks) at 1280 track/ms speed, plus one full rotation at 5400 RPM: (10240/1280) ms + (60/5400) s = 8 ms + 11.11 ms = 19.11 ms.
Read more about block address here:
https://brainly.com/question/14183962
#SPJ1
when the tv was created (year)
Answers
Answer:
1927
Explanation:
Answer:
1971 is the year
_____ are assigned by the network administrator and enable users to access network resources.
A) NICs
B) Permissions
C) Fiber optics
D) MACs
Answers
Answer:
B) Permissions
Type the correct answer in the box. Spell the word correctly. A company has its branches spread over five places in a state. It has become difficult for employees to transfer information and to collaborate on the work schedule. What can the company do to overcome this drawback? The company can implement a(n) ________ which is an internal network used to connect employees of a company on a single site to enable collaborative tasks and to update work status.
Answers
Answer:
saving
Explanation:
What is a common method used in social engineering?
Answers
Explanation:
they are phishing, pretexting, baiting, quid pro quo and tailgating.
For security reasons, the network administrator needs to prevent pings into the corporate networks from hosts outside the internetwork. Which protocol should be blocked with access control lists
Answers
Answer:
ICMP
Explanation:
GAME DESIGN
If you are designing a video game that will primarily be played on a smartphone or tablet, what considerations about the operation or control methods should you keep in mind?
Answers
If you are designing a video game that will primarily be played on a smartphone or tablet, the considerations about the operation or control methods that you should keep in mind are:
The Orientation of the device; The processing power of the device; andThe size of the device in relation to the spacing of the controlls.What are video games?As a result, there is a growing need for mobile app development services and mobile app development companies. As a result of this demand, various smartphone app development businesses promise to provide excellent services.
Regardless of phone manufacturer improvements, there are still uses for the game design process, such as:
Feature Creep IssueNot Targeting the Correct AudienceGetting the Game NoticedManaging Security ConcernsOperating System Fragmentation.Creating the Monetization ModelUpkeep.Learn more about video games:
https://brainly.com/question/28060919
#SPJ1
Question 2
Complete the for loop and string method needed in this function so that a function call like "alpha_length("This has 1 number in it")" will return the output "17". This function should:
accept a string through the parameters of the function;
iterate over the characters in the string;
determine if each character is a letter (counting only alphabetic characters; numbers, punctuation, and spaces should be ignored);
increment the counter;
return the count of letters in the string.
def alpha_length(string):
character = ""
count_alpha = 0
# Complete the for loop sequence to iterate over "string".
for ___:
# Complete the if-statement using a string method.
if ___:
count_alpha += 1
return count_alpha
print(alpha_length("This has 1 number in it")) # Should print 17
print(alpha_length("Thisisallletters")) # Should print 16
print(alpha_length("This one has punctuation!")) # Should print 21
Answers
The Completion of loop and string method that is needed in the said function so that a function call like "alpha_length("This has 1 number in it")" will return the output "17" is given below.
What is the loop and string method?Based on the code function that is given, a person can be able to make use a for loop to be able to iterate over all of the character in the string.
Note that For any of the character, a person need to make use of a given isalpha() method to be able to see if it is found to be an alphabet.
Thus, If it any that is found, that person can increase the count_alpha variable. Lastly, one can be able to return the count_alpha as the main of alphabetic characters in that given string.
Learn more about loop and string method from
https://brainly.com/question/31116878
#SPJ1

Assuming the user types the sentence
Try to be a rainbow in someone's cloud.
and then pushes the ENTER key, what will the value of ch be after the following code executes?.
char ch = 'a';
cin >> ch >> ch >> ch >> ch;
(in c++)
Answers
The value of ch will be the character entered by the user after executing the code.
What is the value of ch after executing the code?The code snippet cin >> ch >> ch >> ch >> ch; reads four characters from the user's input and assigns them to the variable ch. Since the user input is "Try to be a rainbow in someone's cloud." and the code reads four characters, the value of ch after the code executes will depend on the specific characters entered by the user.
In conclusion, without knowing the input, it is not possible to determine the exact value of ch. Therefore, the value of ch will be the character entered by the user after executing the code.
Read more about code execution
brainly.com/question/26134656
#SPJ1
Write a Java program called Pattern that prints an 8-by-8 checker box pattern using a For loop structure as follows:
# # # # # # # #
# # # # # # # #
# # # # # # # #
# # # # # # # #
# # # # # # # #
# # # # # # # #
# # # # # # # #
# # # # # # # #
Answers
public class JavaApplication79 {
public static void main(String[] args) {
int count = 0;
for(int i = 0; i < 64; i ++){
if (count == 8){
System.out.println("");
count = 0;
}
System.out.print("#");
count ++;
}
}
}
I hope this helps!
(Print distinct numbers) Write a program that reads in numbers
separated by a space in one line and displays distinct numbers (i.e., if
a number appears multiple times, it is displayed only once). (Hint:
Read all the numbers and store them in list1. Create a new list list2.
Add a number in list1 to list2. If the number is already in the list,
ignore it.)
Answers
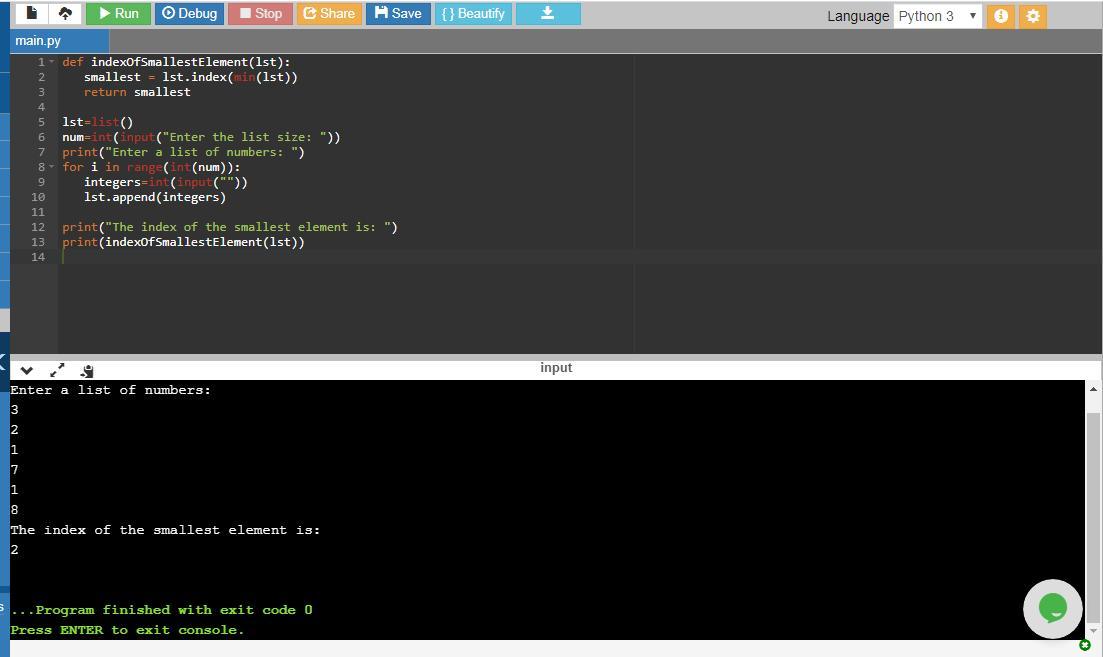
I've included my code in the picture below.

You are creating a presentation for your school Photography project and you want to make the pictures stand out. Which tool would be most efficient to use to enhance the images?
A. Symbols
B. Alt text
C. Tables
D. Picture styles
Answers
Answer:
D
Explanation:
Question 9 of 25
A computer programmer will often use a
by other programmers.
which includes code written
A. website
B. library
C. copyright
O D. license
Answers
Question providede in the document please use my provided codes!!
Answers
Answer:
become successful in your Photo to the best of all time favorite
Write a program that defines the following two lists:
names = ['Alice', 'Bob', 'Cathy', 'Dan', 'Ed', 'Frank','Gary', 'Helen', 'Irene', 'Jack',
'Kelly', 'Larry']
ages = [20, 21, 18, 18, 19, 20, 20, 19, 19, 19, 22, 19]
These lists match up, so Alice’s age is 20, Bob’s age is 21, and so on. Write a program
that asks the user to input the number of the person to retrieve the corresponding
data from the lists. For example, if the user inputs 1, this means the first person
whose data is stored in index 0 of these lists. Then, your program should combine
the chosen person’s data from these two lists into a dictionary. Then, print the
created dictionary.
Hint: Recall that the function input can retrieve a keyboard input from a user. The
signature of this function is as follows:
userInputValue = input("Your message to the user")
N.B.: userInputValue is of type String
Answers
Answer: I used colab, or use your favorite ide
def names_ages_dict():
names = ['Alice', 'Bob', 'Cathy', 'Dan', 'Ed', 'Frank','Gary', 'Helen', 'Irene', 'Jack', 'Kelly', 'Larry']
ages = [20, 21, 18, 18, 19, 20, 20, 19, 19, 19, 22, 19]
# merging both lists
names_ages = [list(x) for x in zip(names, ages)]
index = []
# creating index
i = 0
while i < len(names):
index.append(i)
i += 1
# print("Resultant index is : " ,index)
my_dict = dict(zip(index, names_ages))
print('Input the index value:' )
userInputValue = int(input())
print(f'data at index {userInputValue} is, '+ 'Name: ' + str(my_dict[input1][0] + ' Age: ' + str(my_dict[input1][1])))
keys = []
values = []
keys.append(my_dict[input1][0])
values.append(my_dict[input1][1])
created_dict = dict(zip(keys, values))
print('The created dictionary is ' + str(created_dict))
names_ages_dict()
Explanation: create the function and call the function later

advantages of the Existing System
Answers
The advantages of the Existing System is cost-effective and offers many facilities in a single application.
What is the Existing system?An existing system refers to a system or application which is used by the organization on a current basis. The existing sytem will be replaced when there is a more advanced option available in technology.
In the given case, the name of the Existing system is not provided so it is assumed thta the existing system is Cloud computing, and its advantages are provided in the given context.
Improved efficiency and effectiveness, operational opportunities and dependability, and a reduction in IT expenditures are all provided by the cloud. Compared to conventional data centers, the cloud provides far greater mobility.
Learn more about Cloud Computing, here:
https://brainly.com/question/29846688
#SPj1
The back panel is the best place for which of the following?
Question 3 options:
charts appropriate for the brochure
main title and purpose of brochure
contact information and maps
touching story about cause
Answers
Answer:
Imma contact info and maps
Explanation:
It's the most reasonable
Answer:
contact information and maps
A staff member at a medical research company is creating a query of patient data that is archived at a Health Maintenance Organization (HMO). The query includes patient’s social security numbers (SSN), which are querying as XXX-XX-1234, and dates of births (DOB), which are showing as XX-XX-1974. While the staff member would like to obtain the entire SSN and DOB, they are unable to reverse the queried data to view the entire data fields. Which de-identification method is being used by the HMO to protect the patient data?
Answers
While the staff person would like to access all of the SSN and dob fields, they are unable to reverse the queried data. The HMO uses the Safe Harbor approach for de-identification in order to protect patient data.
What techniques are used for de-identification?De-identification is the process of finding identifiers that relate to a person (or other entity) either directly or indirectly and deleting them from the data Safe Harbor method.
In order to comply with the HIPAA Privacy Rule's de-identification requirement, covered companies or business partners must eliminate personal information from their systems.
Therefore, the Safe Harbor method is used.
Learn more about the Safe Harbor method, here:
https://brainly.com/question/13120522
#SPJ1
Answer: data masking
Explanation: final
Globalization has brought many new complications for businesses. true or false
Answers
Answer: True
Explanation: Globalization has exploit labor. Prisoners and child workers are used to work in inhumane conditions. Safety standards are ignored to produce cheap goods. There is also an increase in human trafficking that lead to increase in crime.
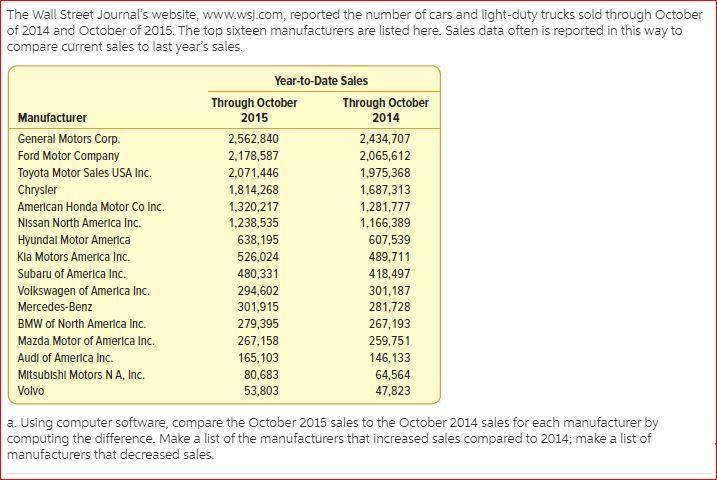
A furniture rentingstore rents severaltypes of furnituretocustomers.It charges a minimum fee for the first month. The store charges an additional fee every monthin excess of the first month. There is amaximum charge forany givenyear. Write a program that calculates and prints the chargefor a furniturerental.
Answers
Incomplete question. Attached is an image of the full question.
Explanation:
The best program to use is MS Excel. By using the Summation formula MS excel we can derive the difference in sales for the two years.

What is the purpose of saving code snippets?
A stores code for later re-use
B provides the application users more flexibility
C allows you to make the application available in different languages
D makes the application more accessible
Answers
Answer:
A stores code for later re-use
Explanation:
To find - What is the purpose of saving code snippets?
Solution -
Code Snippet" is used to describe a small portion of re-usable source code, machine code, or text.
They allow a programmer to avoid typing repetitive code during the course of routine programming.
So,
The correct option is - A stores code for later re-use
The technique for locating the source of an error is to set up _____, which are locations where the browser will pause the program, allowing the programmer to determine the error at that position.
a. breakpoints
b. thresholds
c. blocks
d. lapses
Answers
The technique for locating the source of an error is to set up breakpoints, which are locations where the browser will pause the program, allowing the programmer to determine the error at that position. So, the right answer is a.
Breakpoints are locations in a program where the execution of the code is paused, allowing the programmer to inspect the state of the program at that point. This is a useful technique for locating errors, as it allows the programmer to see the values of variables and the sequence of events leading up to the error.
Breakpoints can be set at specific lines of code or at specific conditions, and the programmer can step through the code line by line to see how it is executing and identify any issues. This technique is particularly useful for finding errors that are difficult to reproduce or that only occur under certain conditions.
Learn more about breakpoints, here https://brainly.com/question/14674523
#SPJ4
is a language composed of commands within a file that can be executed without being compiled.
Answers
Answer:
A Scripting Language
Explanation:
Edge 2021
An interpreted language is a type of programming language for which several of its iterations explicitly and voluntarily implement instructions, without translating code into machine-language directives before.
What is the work of interpreter?An interpreter converts orders of a high-level into an intermediary type which instead performs. Interpreters are also used in learning as they provide immersive content for pupils.Simply stated, an editor is a program where you construct and tweak programs. The program is encoded, or compiled, using the compiler.
IDEs are a formidable collection of tools designed to make programming as simple as it can be. A code editor is essentially a text editor with strong built-in functionality and dedicated features that are geared to simplify and expedite the editing of code.
Therefore, An interpreted language is a type of programming language for which several of its iterations explicitly and voluntarily implement instructions, without translating code into machine-language directives before.
Learn more about interpreted language on:
https://brainly.com/question/23838084
#SPJ3
In the five C's, how is cost different from price?
A. It includes the company's operating costs.
B. It makes it easier to promote the product.
C. It reduces the company's operating expenses.
D. It includes all of the costs related to the product.
Please select the best answer from the choices provided
А
B
Ο Ο Ο Ο
С
OD
Answers
Answer:
D
Explanation:
Well you cost is the opposite meaning of price
Option D It includes all of the costs related to the product is cost different from price.
What are five C's while the product is priced?1. Cost - While pricing the product, the product price should contain all the costs interconnected to the product exists marketing, selling and distribution, and another cost.
2. Customers - Whether the customer will be capable to pay the price and exists the best judge.
3. Channels of distribution - Through which method it will reach its customers
4. Competition - which exists the competitors in the market and at what price the product stands sold by them.
5. Compatibility - Pricing stands to be done based on how much the product exists compatible with its supplement products.
Hence, Option D It includes all of the costs related to the product is cost different from price.
To learn more about product pricing refer to:
https://brainly.com/question/27432513
#SPJ2
For python, Write a function named getResults that accepts radius of a sphere and returns the volume and surface area. Call this function with radius = 3.5 , and display results in one decimal format.
volume = 4/3 * pi * r ^ 3
Surface Area = 4pi * r ^ 2
Answers
import math
def getResults(r):
return "Volume = {}\nSurface Area = {}".format(round((4/3)*math.pi*(r**3),1), round((4*math.pi)*(r**2),1))
print(getResults(3.5))
I hope this helps!
Why is it important to put the most specific case first? What types of errors does it help avoid?
Answers
Answer and Explanation:
The more specific cases require more commitment and attention from the employee. For this reason, it is necessary that the employee is less tired and more focused and, as we know, the focus decreases as the work progresses, due to tiredness. Thus, it is preferable that simpler cases that require less attention and thoroughness are placed last, while more specific cases and that require greater thoroughness are placed first, when the employee is more focused. This avoids problems of organization and functioning of the most different levels of intensity, it also avoids problems of specificity and efficiency.
role of the computer for the development of a country
Answers
Computers have a transformative impact on the development of a country by driving economic growth, revolutionizing education, fostering innovation, improving governance, and promoting connectivity.
Economic Growth: Computers play a crucial role in driving economic growth by enabling automation, streamlining processes, and increasing productivity. They facilitate efficient data management, analysis, and decision-making, leading to improved business operations and competitiveness.
Education and Skills Development: Computers have revolutionized education by providing access to vast amounts of information and resources. They enhance learning experiences through multimedia content, online courses, and virtual simulations.
Innovation and Research: Computers serve as powerful tools for innovation and research. They enable scientists, engineers, and researchers to analyze complex data, simulate experiments, and develop advanced technologies.
High-performance computing and artificial intelligence are driving breakthroughs in various fields, such as medicine, energy, and engineering.
Communication and Connectivity: Computers and the internet have revolutionized communication, enabling instant global connectivity. They facilitate real-time collaboration, information sharing, and networking opportunities. This connectivity enhances trade, international relations, and cultural exchange.
Governance and Public Services: Computers play a vital role in improving governance and public service delivery. They enable efficient data management, e-governance systems, and digital platforms for citizen engagement. Computers also support public utilities, healthcare systems, transportation, and security infrastructure.
Job Creation: The computer industry itself creates jobs, ranging from hardware manufacturing to software development and IT services. Moreover, computers have catalyzed the growth of other industries, creating employment opportunities in sectors such as e-commerce, digital marketing, and software engineering.
Empowerment and Inclusion: Computers have the potential to bridge the digital divide and empower marginalized communities. They provide access to information, educational opportunities, and economic resources, enabling socio-economic inclusion and empowerment.
For more such questions on economic growth visit:
https://brainly.com/question/30186474
#SPJ11
can the charger of my laptop get infected with viruses also when it was connected to it?
Answers
Answer:
Technically… yes. Because if the charging port is the same as a USB/etc connector port, then it can travel over that.
Explanation: