Find solutions for your homework
Find solutions for your homework
engineeringcomputer sciencecomputer science questions and answerswrite a method that takes an integer array as input. the method will repeatedly read a value from the array, go to the indicated position, read the value at that position, then go there, and so on until a limit of 100 is reached or the index is out of bounds. the first value should be read from the array at index 0. the method must return an integer count
Question: Write A Method That Takes An Integer Array As Input. The Method Will Repeatedly Read A Value From The Array, Go To The Indicated Position, Read The Value At That Position, Then Go There, And So On Until A Limit Of 100 Is Reached Or The Index Is Out Of Bounds. The First Value Should Be Read From The Array At Index 0. The Method Must Return An Integer Count
Write a method that takes an integer array as input. The method will repeatedly read a value from the array, go to the indicated position, read the value at that position, then go there, and so on until a limit of 100 is reached or the index is out of bounds.
The first value should be read from the array at index 0.
The method must return an integer count of how many times it read a value from the array.
Here's an example.
INPUT: {1,3,0,5}
The method reads 1 from index 0
The method reads 3 from index 1
The method reads 5 from index 3
The method identifies that index 5 is out of bounds and returns 3 to indicate that 3 values were read from the array.
Here's another example:
INPUT: {4,-1,0,5,2,8,-2}
The method reads 4 from index 0
The method reads 2 from index 4
The method reads 0 from index 2
The method reads 4 from index 0
...
The method repeats up to a limit of 100 times and returns 100.
Here's another example:
INPUT: {3,-1,4,2,5,-2}
The method reads 3 from index 0
The method reads 2 from index 3
The method reads 4 from index 2
The method reads 5 from index 4
The method reads -2 from index 5
The method identifies that index -2 is out of bounds and returns 5 to indicate that 3 values were read from the array.
Upload your Java file, perhaps named Popcorn.java as your answer to this question. You are encouraged to submit the file with your method alongside any testing code in main. Here is a template to get you started:
public class Popcorn
{
public static void main(String[] args)
{
System.out.println();
int[] example1 = {1,3,0,5};
int x = countPops(example1);
System.out.println("Count is: "+x+"\n\n");
int[] example2 = {4,-1,0,5,2,8,-2};
x = countPops(example2);
System.out.println("Count is: "+x+"\n\n");
int[] example3 = {3,-1,4,2,5,-2};
x = countPops(example3);
System.out.println("Count is: "+x);
}
public static int countPops(int[] arr)
{
return 0; //Placeholder. Change this.
}
}
Answers
Sure! I can help you with that. Below is the modified `Popcorn.java` file with the implementation of the `countPops` method:
public class Popcorn {
public static void main(String[] args) {
int[] example1 = {1, 3, 0, 5};
int x = countPops(example1);
System.out.println("Count is: " + x)
int[] example2 = {4, -1, 0, 5, 2, 8, -2};
x = countPops(example2);
System.out.println("Count is: " + x);
int[] example3 = {3, -1, 4, 2, 5, -2};
x = countPops(example3);
System.out.println("Count is: " + x);
}
public static int countPops(int[] arr) {
int count = 0;
int currentIndex = 0;
for (int i = 0; i < 100; i++) {
if (currentIndex >= arr.length || currentIndex < 0)
break;
count++;
int nextIndex = arr[currentIndex];
if (nextIndex >= arr.length || nextIndex < 0)
break;
currentIndex = nextIndex;
}
return count;
}
}
```
The `countPops` method takes an integer array `arr` as input and implements the required logic. It iterates through the array, following the indicated positions until the limit of 100 is reached or an out-of-bounds index is encountered. It returns the count of how many times it read a value from the array.
You can run the `main` method to test the `countPops` method with the provided examples. Simply compile and run the `Popcorn.java` file.
know more about array: https://brainly.com/question/28061186
#SPJ11
Related Questions
which of the following is not a reserved keyword in python?
Answers
To verify a Windows system meets the minimum processor and memory requirements to install software, use the ________.
Answers
To verify a Windows system meets the minimum processor requirements
to install software, use the system control panel window.
What is System control panel window?This is the window which is found in all computers and comprises of the
following:
Device information such as Hardware and Software.User accountsAccessibility optionsNetworking settings.Checking this window will help to check if the windows system meets the
necessary requirements.
Read more about System control here https://brainly.com/question/14878948
How many bit patterns can be represented by 3 bits?
Answers
Answer:
6312
Explanation: dffe
3. How are you able to create photographs differently than 100 years ago?
Answers
Answer:
it willbe black and white
Explanation:
Answer:
Yes, of course!
Explanation:
Digital Cameras can create photographs very different than 100 years ago, which means the answer is yes.
Which delivery method is used to transmit information to one or more end devices, but not all devices on the network
Answers
A broadcast network is one in which a transmission from any one attached station is received by all other attached stations over a shared medium. Examples are a bus-technology local area network, such as Ethernet, and a wireless radio network. Discuss the need or lack of need for a network layer (OSI layer 3) in a broadcast network.
Answers
Answer:
In a broadcast network such as radio network for example a walkie talkie, the broadcasted transmission is received equally by all receivers indiscriminately which may lead to dissemination of classified information to an unauthorized receiver, therefore, the network layer is required is needed to ensure proper routing of the information
Similarly, when the all the broadcasters in one location are each trying to send messages to different receivers at another given location, there would be potential for network congestion and it would be difficult to send information through the network
When there is need for priority service the presence of a network layer is needed in the network
However, when the above functions performed by the network layer is not required, then, the network layer can be excluded, such as the communication between layers 4 - 7 of the OSI model
Explanation:
Once the reaction time experiment in your MakeCode micro:bit program is
complete, what should you do next?
A. Click the "Export data" button to save a file to your computer.
B. Review the tutorial video to make sure you've completed all the
steps correctly.
C. Add the call reaction Test block to your on logo pressed block.
D. Set up your events and create a function that contains the entire
reaction time experiment.

Answers
Once the reaction time experiment in your MakeCode micro:bit program is complete, Review the tutorial video to make sure you've completed all the steps correctly.
What is reaction time experiment?A reaction time experiment is known to be one that has different set of neural processes. This experiment is known to be one that has been set up to measure or look into the response time for something that one can see.
Note that when the reaction time experiment in your MakeCode micro:bit program is complete, it is better to go over the tutorial video to be sure you that you have completed all the steps correctly.
learn more about reaction time from
https://brainly.com/question/6167212
what aspect of the maneuver does propilot park control?
Answers
Propilot Park is a feature available in some Nissan vehicles that allows for semi-autonomous parking. This feature controls several aspects of the parking maneuver, including steering, acceleration, and braking.
When using Propilot Park, the driver must first find a suitable parking spot and activate the feature. Once activated, the vehicle will begin to scan for obstacles and will prompt the driver to shift into reverse. The driver can then take their hands off the steering wheel and allow the car to take control of the parking maneuver.
Propilot Park controls the steering, acceleration, and braking aspects of the parking maneuver, allowing for semi-autonomous parking in Nissan vehicles. This system uses multiple sensors and cameras to analyze the parking space and calculate the optimal parking path, making parking easier and more accurate.
To know more about Propilot Park visit:-
https://brainly.com/question/27930618
#SPJ11
Which of the following is the name assigned to the WAP to identify itself to clients?security keysecurity set identifiernetIDaccess codepassphrase
Answers
The name assigned to the WAP (Wireless Access Point) to identify itself to clients is the "SSID" (Service Set Identifier).
The SSID is a unique alphanumeric identifier that distinguishes one wireless network from another. It is typically configured in the WAP's settings and is broadcasted so that nearby devices can detect and connect to the wireless network. Clients searching for available wireless networks will see the SSID in their network list and can select it to establish a connection. The SSID helps users identify and connect to the desired wireless network when multiple networks are present in the vicinity.
Learn more about WAP here: brainly.com/question/30010035
#SPJ11
what is the predefined business logic within a blockchain called?
Answers
Smart contracts: With so much being said and published about blockchain, it appears that the technology may be misunderstood by the general public. They see it as a one-man band that can do everything, including enabling bitcoin, safeguard data, brew coffee, and more, rather than a technology.
Blockchain is a distributed, immutable database that simplifies the tracking of assets and the recording of transactions inside a business network. An asset may be tangible (such a home, automobile, sum of money, or plot of land) or intangible (intellectual property, patents, copyrights, branding). A blockchain network allows for the recording and trading of practically everything of value, lowering risk and increasing efficiency for all parties. Business depends heavily on information, which is why blockchain technology is significant. It is preferable if it is received promptly and accurately.Because it provides real-time, shareable, and fully transparent data that is recorded on an immutable ledger and only available to users of a permissioned network, blockchain is the perfect technology for delivering such information.
To learn more about " database " Click on below link brainly.com/question/28391263
#SPJ4
Viết thuật toán và chương trình: Tính tổng:
S=1+2+...i
Answers
Answer:
skdjsjwjdjcdjejxjdjxjdjwjsjxjdwiskxmdjxkdnejxj
Explanation:
justnejedjdfhjxnfbcjccjcuvjjfhedcjcjchcjeidchdjchcjdjcjcucjf
A ____ contains the description of the entire database as seen by the database administrator.
Answers
A data dictionary contains the description of the entire database as seen by the database administrator.
The data dictionary, which describes the complete database as seen by the database administrator, is an essential component of every database management system. It gives a full and accurate record of a database's contents, structure, and organization. The data dictionary also includes information on the relationships between other database objects like tables, indexes, views, and procedures. The data dictionary contains information that is needed to administer the database, verify data integrity, and offer metadata to other applications.
A data dictionary is an essential tool for database administrators, developers, and users. It serves as a single point of reference for all of the information required to comprehend the database's structure and content. The data dictionary may also be used to automate operations like report generation, data analysis, and documentation creation. Organizations may enhance data quality, minimize mistakes, and boost efficiency by adopting a data dictionary. Overall, the data dictionary is an essential component of every database management system, ensuring the optimal use of data resources.
To learn more about DBMS, visit:
https://brainly.com/question/12125305
#SPJ11
PLEASE PLEASE PLEASEEEE HELP
Explain why quality is important (use the word accuracy in your answer)
Answers
Answer:
Quality is critical to satisfying your customers and retaining their loyalty so they continue to buy from you in the future. Quality products make an important contribution to long-term revenue and profitability.
have a nice day! (^o^)
1. Distinguish between
a) Optical and Magnetic scanning
(2marks)
Optical scanning
1.They use principles of light to scan document
Magnetic scanning
1. They use principles of magnetism to
document
sense
Answers
Answer:
They use principles of light to scan document
Magnetic scanning
Explanation:
you want to ensure there are redundant dhcp services available for your network. What should you set up on your server to make this possible
Answers
There is need to follow the right steps. To ensure there are redundant DHCP services available for your network, try and open the DHCP console and then you input or add the primary server.
Furthermore, you then right-click on any of the scope through which you want to make sure that there is availability and then you have to select Configure Failover.What are the methods that gives redundant highly available DHCP solution?The DHCP server role in Windows Server 2012 is known to be one that helps in terms of redundancy using split scope, failover and failover clustering.
Always know that the DHCP failover helps availability only on a per-scope basis.
Learn more about DHCP services from
https://brainly.com/question/14407739
A relational database has been created to store data about subjects that students are studying. The following is a
selection of some data stored in one of the tables. The data represents t he student's name, the personal tutor group,
the personal tutor, the subject studied, the level of study and the subject teacher but there is some data missing:
Xiangfei 3 MUB Computing A DER
Xiangfei 3 MUB Maths A BNN
Xiangfei 3 MUB Physics AS DAB
Mahesh 2 BAR History AS IJM
Mahesh 2 BAR Geography AS CAB
Define the terms used to describe the components in a relational database table using examples from
this table.
ii If this represented all of the data, it would have been impossible to create this table.
What is it that has not been shown here and must have been defined to allow the creation as a relational
[2]
database table? Explain your answer and suggest examples of the missing data.

Answers
Mention two charactarestics of money that make it a sustainable medium of exchange
(Maximum 400 words) Describe how this period of Coronavirus (COVID-19) will influence and affect the STEM (Science, Technology, Engineering, and Mathematics) fields.
Answers
The period of coronavirus will have both negative and positive impacts on STEM fields.
However, the STEM (Science, Technology, Engineering, and Mathematics) fields have shown significant changes and impacts.
Here is how this period of COVID-19 will affect the STEM fields.
1. Technology
The current situation has increased the use of technology in various fields. Remote work and online meetings are becoming more popular, and this has led to increased technology usage. Technological advancements are expected in the future, leading to new business models that are more efficient.
2. Biomedical research
The COVID-19 pandemic has sparked the need for more biomedical research and led to an increase in research funding. Scientists are researching vaccines, treatments, and diagnostic tools, which is expected to lead to a better understanding of viruses and other infectious diseases.
3. Education
The pandemic has affected the education system globally, with many institutions closing and students learning from home. Teachers and educators are now incorporating technology in teaching, and the pandemic has accelerated the adoption of e-learning platforms. This has led to the development of new ways to learn and teach, and new online learning platforms are expected to emerge in the future.
4. Engineering
The pandemic has led to an increase in demand for essential supplies such as ventilators, personal protective equipment (PPE), and other medical devices. This has led to the development of new designs and manufacturing processes that are more efficient. The need for innovation has also led to the development of new solutions, such as 3D printing of medical supplies.
5. Mathematics
Mathematical models are used to understand the transmission of diseases, and the COVID-19 pandemic has led to the development of new models to understand the spread of the virus. These models help policymakers and public health officials make decisions to control the pandemic.
In conclusion, the COVID-19 pandemic has impacted STEM fields significantly, leading to new developments and innovations. With increased technology adoption, biomedical research, e-learning platforms, and engineering, the STEM fields are expected to change and adapt to the new normal. It is crucial to keep up with these changes and find ways to take advantage of the opportunities presented by the pandemic.
learn more about STEM fields here:
https://brainly.com/question/30082530
#SPJ11
true/false: when an operator has two operands of different data types, c always converts them both to double before performing the operation.
Answers
False, when an operator has two operands of different data types, C does not always convert them both to double before performing the operation.
Instead, C follows a set of rules known as the "usual arithmetic conversions" to determine the type of the result. These rules include:
- If one operand is a long double, the other is converted to a long double
- If one operand is a double, the other is converted to double
- If one operand is a float, the other is converted to float
- If one operand is an unsigned long int, the other is converted to unsigned long int
- If one operand is a long int, the other is converted to long int
- If one operand is an unsigned int, the other is converted to unsigned int
- Otherwise, both operands are converted to int
So, while it is possible for both operands to be converted to double, it is not always the case.
Learn more about operands here:https://brainly.com/question/26891746
#SPJ11
If I want to make it look like slide number one is turning a page to slide number two, what
effect needs to be applied?
Answers
Answer:
Im not certain but I think thwir is one called flip
Explanation:
Kind of works like a book if thats what your asking for
You can enter more than one element of data in the same field. *
True
False
Answers
Answer:
true
Explanation:
im smart
Feasibility Analysis for Software Development (testing
software):
1. Operational
2. Technical
3. Schedule
4.Legal
5. Contractual and Political
Answers
Feasibility analysis is a critical step in software development, considering factors such as operational, technical, schedule, legal, contractual, and political aspects to ensure successful and effective software implementation while mitigating risks.
Conducting a feasibility analysis is essential in software development to assess the operational, technical, schedule, legal, contractual, and political factors.
Evaluating these factors helps determine whether the software can be effectively used in the business environment, built with available technology, completed within the proposed time, compliant with legal requirements, and aligned with contractual and political goals.
This analysis minimizes risks and ensures the success and effectiveness of the software. It enables the development team to make informed decisions and consider necessary adjustments or mitigations during the development process.
By addressing feasibility considerations, software development projects can increase their chances of meeting user requirements, delivering value, and achieving desired outcomes.
Learn more about software development: brainly.com/question/26135704
#SPJ11
given the following rules: factorial(0,1). factorial(n,f) :- n > 0, factorial(n-1, f1), f is n * f1. which line of the code will generate a compilation error?
Answers
Option C; factorial(n-1, f1) line of the code will generate a compilation error.
The term "compilation error" describes a situation in which a compiler fails to compile a section of source code for a computer program, either because of flaws in the source code or, more rarely, because of problems in the compiler itself. When programmers are debugging source code, a compilation error message is frequently helpful. Despite the ambiguity in the definitions of compilation and interpretation, faults in compilation often only apply to static compilation and not dynamic compilation. Although many programmers and sources may refer to them as run-time faults, dynamic compilation can still theoretically have compilation errors,[citation needed]. Since syntax errors are checked for at run time by the majority of just-in-time compilers, including the Javascript V8 engine, compilation errors are frequently referred to as such.
Learn more about compilation error here:
https://brainly.com/question/9926411
#SPJ4
Which computing component is similar to the human brain
Answers
2. You go to an intemet cafe to send an email to your friend upon returning home you
realize that you forgot to log out your account. What probably could happen to your
account?
Answers
Pueden cojer los datos privados hackear la cuenta
Which of the following best explains the ability to solve problems algorithmically? Group of answer choices Any problem can be solved algorithmically, though some algorithmic solutions require a very large amount of data storage to execute. There exist some problems that cannot be solved algorithmically using any computer. Any problem can be solved algorithmically, though some algorithmic solutions must be executed on multiple devices in parallel. Any problem can be solved algorithmically, though some algorithmic solutions may require humans to validate the results.
Answers
Answer:
I think it’s There exist some problems that cannot be solved algorithmically using any computer.
Explanation:
There exist some problems that cannot be solved algorithmically using any computer represent the best explanation of the ability to solve problems algorithmically.
The following information should not be considered:
It does not required large amount of data store to excute. The algorithmic solutions that must be executed should not be in multiple devices in parallel. It does not required humans for validating the results.Learn more: brainly.com/question/17429689
To figure out how to use her MacBook Pro graphics software to update designs originally created on a DEC10, Marianne needs to use a ______ language?
Answers
Answer:
Glue Language
Explanation:
I'm not 100% sure, but here is the definition.
Glue language- A programming language that can be used to provide interoperability between systems not originally intended to work together
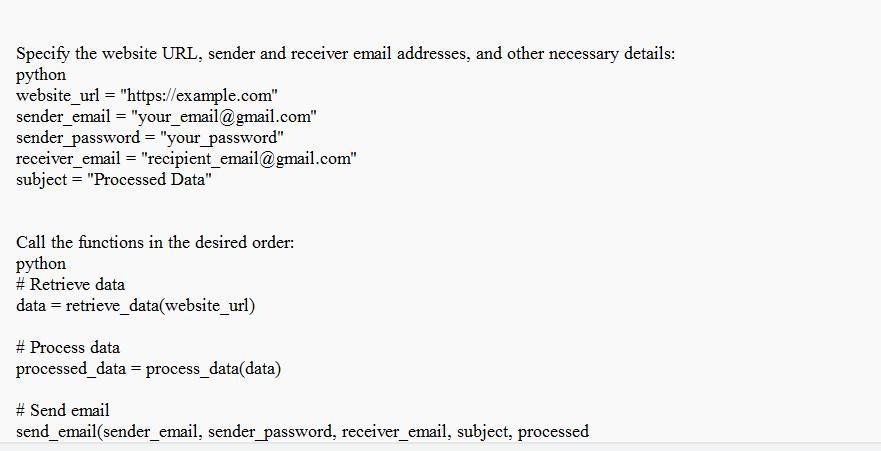
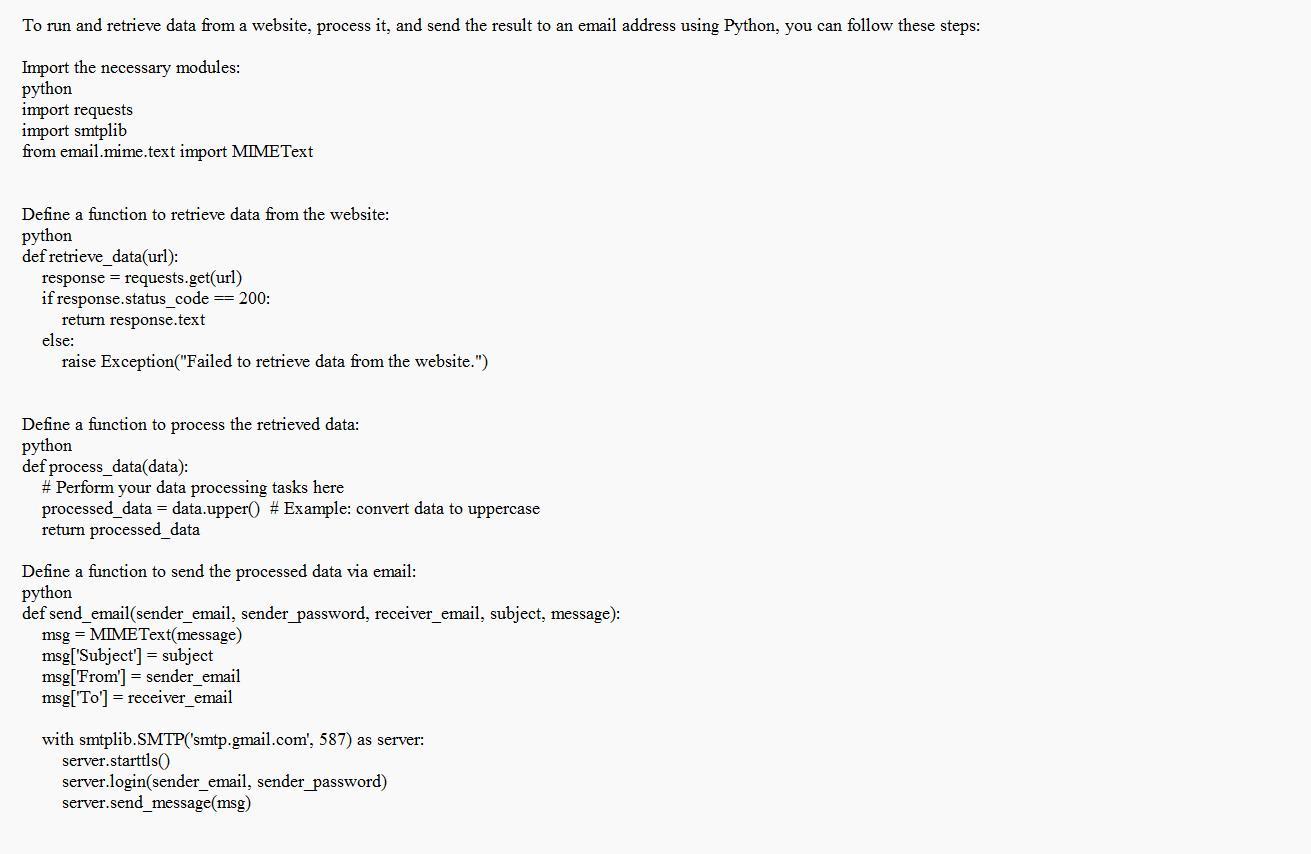
Use knowledge of Network Programming to run and retrieve data from any website and process the data then send the result to your email. (Python)
Answers
To do the aove, Be certain to substitute "your_emailgm/ail. com" and "your_password" with your genuine email login information.
What is Network Programming?In the code example, it is based on the assumption that your email service is G/m/ail. In the event that you utilize an email service provider different from the one suggested, it will be necessary to adjust the SMTP settings accordingly.
For those with a G/m/ail account, it's important to ensure that "Less Secure Apps" is enabled in the account settings prior to using this script, as it utilizes SMTP for email transmission.
Learn more about Network Programming from
https://brainly.com/question/13105401
#SPJ4
Write the steps to create labels in OpenOffice writer
Answers
1. Start up Open Office.Org.
2. Click on File >> New >> Labels.
3. In the label dialog box, click on the brand box. This will allow you to choose the type of paper that you use.
4. Select the type of document that you want. The usual standard is Avery, but feel free to explore and discover what you like.
5. Select if you want a single label, a document, and any other options. Some of the things you might want to do are:
- Create a variety of labels for folders or drawers
- Create a sheet of address labels
- Create decorative labels
6. Click New Document. Here, you see a sheet of blank labels.
7. Create the type of format/placement that you want for your labels. Once you are happy with it, copy it to the rest of the labels.
8. Fill your labels with necessary information.
9. Print them out.
Find the cost of 2m 20cm at 25p per metre
Answers
Answer:
length * cost per unit
2.2*25
= 50 pounds
Working with text in presentation programs is very ____ using text in other applications.
A.) different from
B.) similar to
Answers
Answer:
A
Explanation:
Your inquiry states that "Working with text in presentation programs is very ____ using text in other applications." Working in presentation software such as Microsoft PowerPoint and Microsoft Word, is very different. Microsoft PowerPoint allows you to do so much more on the visuals, Microsoft PowerPoint and other presentation software also has capabilities to present information than displaying it in a text-editor.
Working with text in presentation programs is very similar to using text in other applications.
What is a presentation?A presentation is known to be any kind of work or things that is shown to others during a formal ceremony.
Conclusively, Note that Working with text in presentation programs is very similar to using text in other applications as it all involves typing or inputting words.
Learn more about presentation from
https://brainly.com/question/24653274