does anyone have rrrooobbllloooxx
Answers
Answer:
nope
Explanation:
Related Questions
What is a benefit of using quantitative data in an experiment?
It is objective
It is subjective
It is perceptive
It is descriptive
Answers
Gemima's classmate Tristan sent her an Excel table that shows the amount of vitamin C in seafood. She wants to
paste this table to her Word document.
Which pasting option should she use so that the updates in the Excel table are reflected in her Word document?
Check all that apply.
Picture
Keep as Text
Use Destination Styles
Keep Source Formatting
Link and Use Destination Styles
Link and Keep Source Formatting
Answers
Answer:
E, F
Explanation:
I just took it
Link and Use Destination Styles and Link and Keep Source Formatting.
What is Destination styles?Click and drag in Excel to choose the cells you want to copy. Copy can be chosen by right-clicking on the copied cells. Right-click in your PowerPoint presentation and choose the desired Paste Options:
Employ destination styles to alter your copied cells using the same fonts and color scheme as a PowerPoint table.
Opt to maintain the same source formatting from Excel while keeping your table editable in PowerPoint. Embed - Choose to preserve a duplicate of your table in PowerPoint in the event that you need to modify the information, and Excel will launch.
Therefore, Link and Use Destination Styles and Link and Keep Source Formatting.
To learn more about Destination styles, refer to the link:
https://brainly.com/question/12873475
#SPJ2
a.Distance sensor
b.Programable microcontroller
c.Ambient light sensor
d.Wi-Fi

Answers
D WiFi
It uses wifi to connect to the internet
Answer:
.Wi-Fi
Explanation:
Wi-Fi is the wireless technology used to connect computers, tablets, smartphones and other devices to the internet. ... The device transmits a radio signal back to the router, which connects to the internet by wire or cable.
What is the use of an NDP?
A). identifying pointers at the other end of a network
B). sending an error message if a packet gets lost due to a bad connection
C). finding other computers on the network
D). taking an IP address from a network layer and identifying the associated MAC address
Answers
Answer:
Taking an IP address from a network layer and identifying the associated MAC address
Explanation:
Option D
i need a essay 3-5 sentences on volleyball
Answers
Answer:Volleyball is a team sport that involves two teams of six players, one of which plays offense and the other defense. Each player has a specific role to play on the court:
Setter – The setter positions herself in front of her teammates, and sets up the ball for them to hit. She also controls the pace at which points are played, as well as how long each point lasts. The setter’s job is to make sure that every point goes smoothly without any errors or mistakes by her teammates.
– The setter positions herself in front of her teammates and sets up the ball
Explanation:
pick and choose the sentences from there
What two types of devices have a keyboard integrated into the screen?
Question 1 options:
laptops and smartphones
tablets and electric typewriters
typographers and tablets
tablets and smartphones
Answers
Answer:
tablets and smartphones
Explanation:
Have a good day!
List steps to protect digital data from compromise. List steps to protect digital data from compromise.
Answers
Answer:
1. apply software updates
2. protect password
3. disable lock screen notification
4. lock your apps
5. keep your browsing to yourself
6. encrypt your data
7. back it up
Explanation:
all above
Answer:25 Jan 2021 — Securing Your Devices and Networks · 1. Encrypt your data. · 2. Backup your data. · 3. The cloud provides a viable backup option. · 4. Anti-malware ...
Data Protection Tips for Mobile Devices · Protecting Your Identity
Explanation:25 Jan 2021 — Securing Your Devices and Networks · 1. Encrypt your data. · 2. Backup your data. · 3. The cloud provides a viable backup option. · 4. Anti-malware ...
Data Protection Tips for Mobile Devices · Protecting Your Identity
what is the answer i need them now pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls pls

Answers
Answer: Insert ribbon > table drop down menu
Explanation:
Answer:Insert ribbon > table drop down menu
Explanation:
What are some machines, places or apparatus that sensors could be used in? Give at least five examples.
Answers
Answer:
Sorry
Explanation:
What is the Fastest Tesla right now?
(A) Tesla Model X (P100D)
(B) Tesla Model S (P100D)
(C) Tesla Roadster
(D) Tesla Model S (Performance)
(E) Tesla Model 3 (Performance)
Answers
(I made this up teehee) what anime is katski bakugo from
Answers
Does anybody have some good law ideas and why should they be created? Cause I'm stuck on making on.
Answers
Raise the minimum raise
Teachers should make a whole lot more because without them we would be nothing .
2. Law, there must be land over 20 acres just for trees, per state. because we need to heal our outercircle space thing.
PLEASE HELP ME Write a 150-word paragraph about five of the zaniest and/or most novel ways you’ve found online that people earn incomes. Keep in mind that the sites should not be corporate sites. We are looking for unique niches. Have fun. We think you will be surprised when you see what people are willing to pay for online.
Answers
Answer: Disney and video games winning ratings can produced a vast amount of money, making into a job, that anyone could create for example becoming an actor or becoming a gamer.
we could go over the amount of time disney and other companies spent.
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
Why is it important for iOS developers who have learned to program in Swift to also know Objective-C?
A. Objective C is a user interface framework for building software using iOS.
B. Objective C is the integrated development environment best suited for iOS app development.
C. Objective C is the language in which older iOS apps were written, which developers may want to upgrade.
D. Objective C is the newest programming language for building iOS apps.
Answers
Construct pseudocode for a program that prints ‘Hello World’ on the screen.
Answers
Answer:
Declare a class with name A.
Declare the main method public static void main(String args[]){
Now Type the System. out. println("Hello World"); which displays the text Hello World.
Explanation:
Name three computer company's.
Answers
Please help, I can't find the answer but I understand the topic.
Question:
Fill in the missing parentheses to have x equal 15.
int x = _ 2 + 3 _ * 3;
Console.WriteLine(x);
Answers
Answer:
x=(2+3)*3;
Explanation:
Hope this helped and have a nice day : )
How do the text feature help on the text?
Answers
Answer:
Text features help you locate important information in a text. Knowing the purpose of the text feature helps you decide at which text feature to look when you want to understand your text better. Organized by purpose, the chart identifies text features and how they help the reader.
Explanation:

Which of the following describes a hardware error? Select 3 options.
-Nothing happens when you press the Power button on your desktop PC.
-Nothing happens when you press the spacebar on your keyboard, but the other keys are working.
-Every time you try to run your new game, it crashes after displaying the opening screen.
-The mouse pointer on-screen only moves horizontally, not vertically.
-After a recent Windows update, you can no longer access the internet on your laptop.
Answers
Answer: opinion 4 and 5
Explanation:
Answer:
Nothing happens when you press the Power button on your desktop PC.
The mouse pointer on-screen only moves horizontally, not vertically.
Nothing happens when you press the spacebar on your keyboard, but the other keys are working.
Explanation:
Edge 2023

what is bigger that terbites
Answers
Answer:
Units larger than a terabyte include a petabyte, exabyte, zettabyte, yottabyte and brontobyte. A geopbyte is also larger than a terabyte and refers to 10 30 bytes, or 1,000 brontobytes. Additional units of measurement become necessary as the amount of data in the world increases.
Explanation:
Answer:
I think you mean terabyte so the answer would be a petabyte
Explanation:
There are more thing that are bigger than terabytes and petabytes too, here are a few of them. exabyte, zettabyte, and yottabyte
I need help pleaseeeeeee!
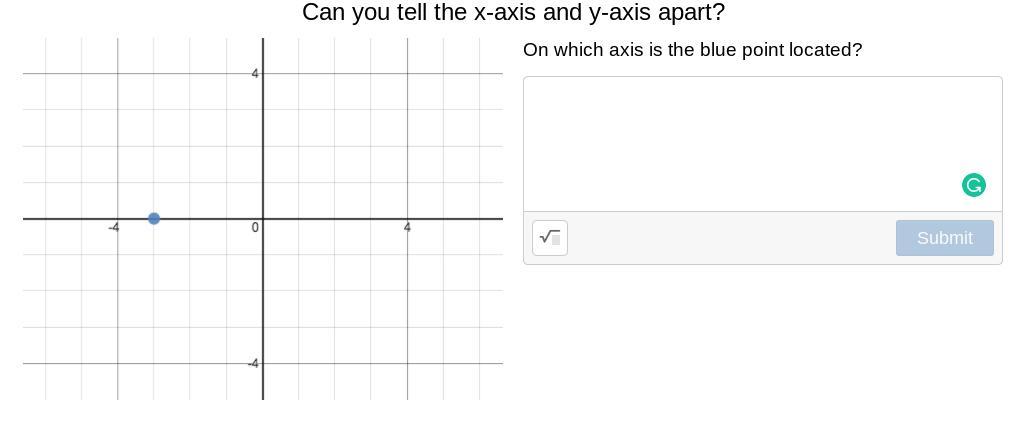
Answers
Answer:
located on the x axis
the x axis is horizontal and y axis vertical
Your friend Tegan is designing a game that involves cats taking over the world. She wants to use obstacles that are difficult at first, and then use simpler obstacles as the game progresses. Would you try to change her approach? Why or why not?
(game design)
Answers
Answer:
I would put levels ranging for level 1 to 50, and start off simple and easy but the game becomes hard during the player plays.
Explanation:
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!
can someone plz help me with this question plz
Question:
what does 64-bit mean? Explain in your own words.
Answers
Answer:
64-bit integers, memory addresses, and other data units are all 64 bits wide in computer architecture. Furthermore, architectures based on 64-bit central processing units and arithmetic logic units are those that use processor registers, address buses, or data buses of that size.
Explanation:

create a 3 to 5 step plan for checking out a post on social media for the next time you encounter something questionable.
Answers
2. Block or unfollow user
3. Tell parent
Answer:
Report. Block. Tell mommy or dada
Explanation:
Which best describes desktop publishing? the process of designing and laying out printed material the positioning of text, graphics, and white space on a page the style of letters and how they are arranged the use of images and colors
Answers
Explanation:
the process of designing and laying out printed material.
Answer:A photographic proof where all colors are shown in blue, best used for spot color jobs, and it is used primarily to ... WYSIWYG is technical jargon that describes.
Explanation:
!!!!PLEASE HELP!!!!! You get to play journalist today. The topic of your story is one of the laws discussed in this lesson. You will select one of them to research. While researching, you will learn more about the law and will locate a case that went to court. Then you will write an unbiased article or broadcast describing the law and summarize the case and the stand of the parties involved. Be sure to review and abide by The Cannons of Journalism. Be sure to include:
a description of the law;
how the law relates to digital media;
one example of a case that went to court;
a discussion of the case and the parties involved; and
a summary of the outcome of the case.
Some helpful hints in finding a case are:
Search for “case law,” “court case examples,” and “case studies.”
Include the full name of the law and the acronym.
Discuss the impact these laws have on one or more media outlets in your community.
You will write your report as an article with at least 500 words that will be posted on an online news site or that a broadcast journalist will report on TV news.
Upload your 500-word story that describes one law, including how it relates to digital media, and summarizes a case that went to the courts and the stand of the parties involved.
Answers
Title: The Digital Privacy Act: Safeguarding Personal Information in the Digital Age
Date: [Insert Date]
Byline: [Your Name]
[City Name] - In an era of rapidly advancing technology and widespread digital connectivity, protecting personal information has become a paramount concern. The Digital Privacy Act, a legislation introduced to address these concerns, aims to safeguard individuals' privacy rights and regulate the handling of personal data in the digital realm.
The Digital Privacy Act, formally known as the Personal Information Protection and Electronic Documents Act (PIPEDA), was enacted in [Insert Year]. This federal law governs how private sector organizations collect, use, and disclose personal information in the course of commercial activities. It establishes rules and principles for obtaining consent, ensuring transparency, and safeguarding personal data from unauthorized access or disclosure.
In the realm of digital media, the Digital Privacy Act plays a crucial role in governing the practices of online platforms, social media networks, and e-commerce websites. It requires organizations to obtain informed consent when collecting personal information, inform individuals of the purpose for its collection, and implement appropriate security measures to protect sensitive data from breaches or unauthorized use.
One prominent case that exemplifies the intersection of the Digital Privacy Act and digital media is the landmark lawsuit of Doe v. SocialMediaCo. In this case, Jane Doe, a user of a popular social media platform, filed a complaint against the company for unauthorized disclosure of her personal information.
According to court documents, the plaintiff alleged that SocialMediaCo, without her consent, shared her private messages with third-party advertisers, resulting in a breach of her privacy. The case brought into focus the importance of user consent and the responsibility of online platforms in protecting personal information.
During the trial, the plaintiff argued that the actions of SocialMediaCo violated the provisions of the Digital Privacy Act. She contended that the company failed to obtain proper consent and did not adequately safeguard her personal data, leading to emotional distress and reputational harm.
On the other hand, SocialMediaCo maintained that their practices were in compliance with the Digital Privacy Act. They argued that users implicitly consented to the sharing of their information with third-party advertisers through the platform's terms of service agreement.
After careful deliberation, the court ruled in favor of Jane Doe, emphasizing the importance of explicit consent and the duty of organizations to protect user privacy. The court found SocialMediaCo liable for the unauthorized disclosure of personal information and awarded damages to the plaintiff.
The outcome of the case set a precedent for other digital media companies, reinforcing the need for stringent privacy practices and ensuring compliance with the Digital Privacy Act. It also served as a reminder to individuals about the importance of understanding privacy policies and exercising caution when sharing personal information online.
As we navigate the digital landscape, the Digital Privacy Act stands as a crucial safeguard, protecting individuals from the potential risks associated with the collection and use of personal data. It places the responsibility on organizations to respect privacy rights, obtain informed consent, and prioritize the security of sensitive information.
In an ever-evolving digital world, the Digital Privacy Act serves as a shield, empowering individuals to assert their rights and reinforcing the notion that personal information deserves protection, both offline and online.
I hope this helps. Cheers! ^^
What is the name given to the parts of a computer that you can actually
touch?
Software
Computer Parts
Computer Case
Hardware
Answers
Answer:
Hardware
Explanation:
Hardware, is the parts of the computer that you can physically touch. Examples include, the keyboard and mouse.
Hope this helps. <3
Hardware is the name given to the parts of a computer that you can actually touch.
What is Hardware?
The physical components of a computer, such as its chassis, CPU, RAM, monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers, and motherboard, are referred to as computer hardware.
Software, on the other hand, is a collection of instructions that may be stored and executed by hardware. Software is referred to as "soft" because it is flexible, but hardware is referred to as "hard" because it is rigid in terms of modifications.
Software often instructs hardware to carry out any command or instruction. A useful computer system is one that combines hardware and software, while there are also systems that use simply hardware.
Therefore, Hardware is the name given to the parts of a computer that you can actually touch.
To learn more about Hardware, refer to the link:
https://brainly.com/question/15232088
#SPJ5
Hello everyone! Happy Wednesday, or Thursday! (Depending on where you are in the world, because of the atmosphere and what not :,) ) but either way, I hope your day will/went well! Starting off for the first QOTD for this morning:
I have keys, but no locks and space, and no rooms. You can enter, but you can’t go outside. What am I?
Check the comment under.
Answers
Answer:
Keyboard
Explanation: