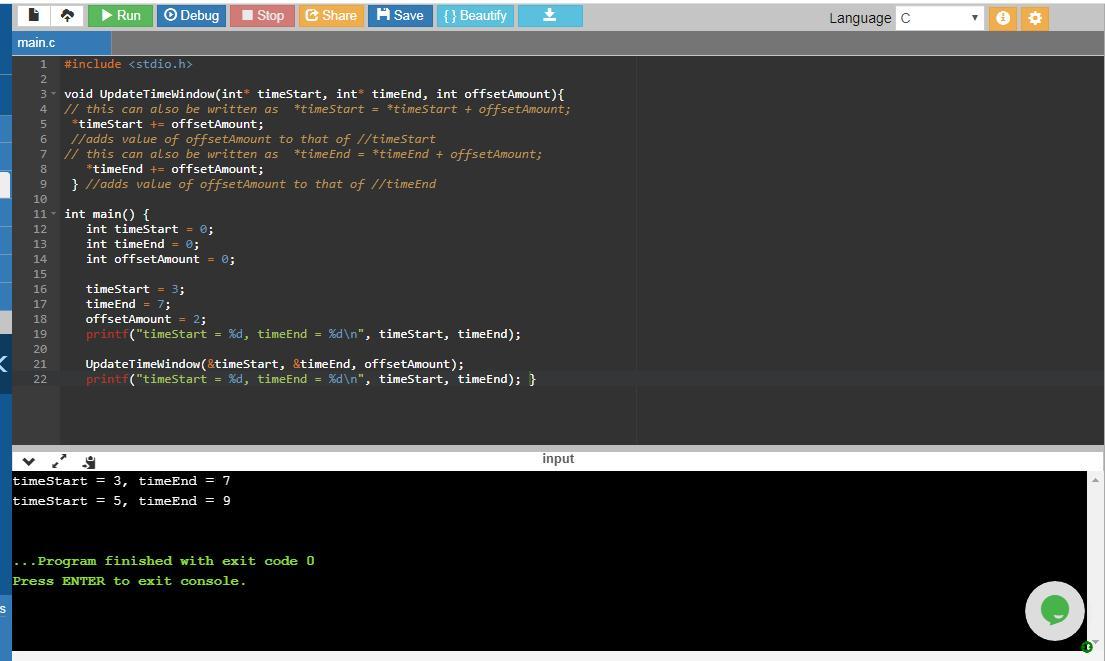
Define a function UpdateTimeWindow() with parameters timeStart, timeEnd, and offsetAmount. Each parameter is of type int. The function adds offsetAmount to each of the first two parameters. Make the first two parameters pass by pointer. Sample output for the given program:
Answers
Answer:
Here is a UpdateTimeWindow() method with parameters timeStart, timeEnd, and offsetAmount
// the timeEnd and timeStart variables are passed by pointer
void UpdateTimeWindow(int* timeStart, int* timeEnd, int offsetAmount){
// this can also be written as *timeStart = *timeStart + offsetAmount;
*timeStart += offsetAmount; //adds value of offsetAmount to that of //timeStart
// this can also be written as *timeEnd = *timeEnd + offsetAmount;
*timeEnd += offsetAmount; } //adds value of offsetAmount to that of //timeEnd
Explanation:
The function has three int parameters timeStart, timeEnd, and offsetAmount.
First two parameters timeStart and End are passed by pointer. You can see the asterisk sign with them. Then in the body of the function there are two statements *timeStart += offsetAmount; and *End+= offsetAmount; in these statements the offsetAmount is added to the each of the two parameters timeStart and timeEnd.
Related Questions
1a) Design an algorithm and draw a flowchart to display a set of even
numbers between 2 and 98 inclusive with their squares,
square roots, cubes and reciprocals.
Answers
what will happen if I upgrade my asus crosshair v formula-z motherboard to a asus rog strix b450-f motherboard?
Answers
Answer: A lot will happen
Explanation:
If you will upgrade your laptop, that means it will get better in performance and a lot of other things....
Also, if the laptop has the word formula, you know that's a good thing, especially if it's z, which is the last letter in the alphabet.
And the other letters are something that I don't understand especially the Strix b450-f part..
Hope I helped a lotttt...
what are the uses of joystick
Answers
You are in the process of configuring a new computer. The motherboard has four memory slots and supports dual-channel memory. You install two memory modules. When you boot the computer, the BIOS recognizes both modules, but the memory is not configured to run in dual-channel mode. What should you do
Answers
Answer:
Place the modules in the appropriate slots on the motherboard.
Explanation:
You must install memory in the correct slots to use dual-channel memory. The two slots may be next to one other or alternate depending on the motherboard. For the correct configuration, consult the motherboard manual. Dual-channel support is primarily determined by the motherboard (e.g., the memory controller), rather than the memory. With Rambus RAM, continuity modules are employed; if they were necessary on this system, none of the memory would have been identified. Memory timing is based on the CAS latency. If the system is unstable with the current memory timing settings, you may want to change the timing.
1.3 Code Practice: Question 3. On edhesieve.
Write a program to output the following:
^ ^
( o o )
v
Hint: Copying and pasting the code above into each line of the programming environment will help you ensure that you are accurately spacing out the required characters.
Using ¨print¨
Answers
Answer:
I'll answer this question using Python
print(" ^ ^")
print("( o o )")
print(" v")
Explanation:
To answer this question, you have to follow the hint as it is in the question
The hint says you should copy each line into a print statement and that's exactly what I did when answering this question;
In other words;
^ ^ becomes print(" ^ ^")
( o o ) becomes print("( o o )")
v becomes print(" v")
I've been trying for some time to get this code right, does anyone have anysuggestions or can help me figure this out? this is the questions: Given a positive integer n, the following rules will always create a sequence that ends with 1, called the hailstone sequence:
If n is even, divide it by 2
If n is odd, multiply it by 3 and add 1 (i.e. 3n +1)
Continue until n is 1
Write a program that reads an integer as input and prints the hailstone sequence starting with the integer entered. Format the output so that ten integers, each separated by a tab character (\t), are printed per line.
The output format can be achieved as follows:
System.out.print(n + "\t");
Ex: If the input is:
25
the output is:
25 76 38 19 58 29 88 44 22 11
34 17 52 26 13 40 20 10 5 16
8 4 2 1
This is the code I have been working with for awhile:
import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int n = scnr.nextInt();
int cnt = 1;
while(n != 1){
if(cnt == 10){
System.out.println();
cnt = 1;
}
System.out.print(n + "\t");
if(n % 2 == 0) n /= 2;
else n = 3*n + 1;
}
System.out.println(n);
}
}
---I can't get it to format correctly like the image of a newline using: System.out.print(n + "\t");
because it keeps printing a straight line. Does anyone have any ideas on what I am missing> I apologise for the trouble and thank you. Please bbe kind. I am trying.
Warm regards
Answers
The program based on the information will be:
def hailstone(n):
print(n)
while n != 1:
if n % 2 == 0:
n = n // 2
else:
n = 3 * n + 1
print(n)
num = int(input("Enter an integer: "))
hailstone(num)
What is the program?It should be noted that the program prompts the user to enter an integer as input, which is then stored in the variable 'num'. The 'hailstone' function is then called with 'num' as its argument. The function starts by printing the initial value of 'n' (the input integer).
It then enters a while loop which continues until 'n' becomes 1. Inside the loop, it checks if 'n' is even or odd. If 'n' is even, it divides it by 2, and if 'n' is odd, it multiplies it by 3 and adds 1. The resulting value of 'n' is then printed. The loop continues until 'n' becomes 1, at which point the function exits and the program terminates.
Learn more about program on:
https://brainly.com/question/26642771
#SPJ1
Is Lt possible to map the way of human thinking to artificial intelligence components
Answers
Answer:
The technique is mind mapping and involves visual representation of ideas and information which makes it easier to remember and memorize facts even in complex subjects. Here is an example of a mind map with the essential elements of AI and the industries where Artificial Intelligence is applied.
Explanation:
HELP ME OUT PLEASE!!!!!
Location, such as indoor versus outdoor, is an important consideration when taking photographs.
True False
Answers
Answer:
I'd say true
Explanation:
Because you can't do all the different techniques and styles if you're indoor instead of outdoor or vice versa. There is also lighting to consider
Answer:
true
Explanation:
Have good day
A ______ can hold a sequence of characters such as a name.
Answers
A string can hold a sequence of characters, such as a name.
What is a string?A string is frequently implemented as an array data structure of bytes (or words) that records a sequence of elements, typically characters, using some character encoding. A string is typically thought of as a data type. Data types that are character strings are the most popular.
Any string of letters, numerals, punctuation, and other recognized characters can be stored in them. Mailing addresses, names, and descriptions are examples of common character strings.
Therefore, a string is capable of storing a group of characters, such as a name.
To learn more about string, refer to the link:
https://brainly.com/question/17091706
#SPJ9
View filters are applied in what order?
Answers
Explanation:
in the formal order of filter .
.
.
thanks
View filters are applied to data in the order in which they were introduced by default. If a view already has filters, your new filter will be applied after them.
Please help me with this , it would really mean alot , you may leave some if you don't know some of the answer <3

Answers
Explanation:
HOPE MY ANSWER IS HELPFUL FOR YOU!I DO MY BEST!!!!
PLEASE MARK AS BRAINLEST ANSWER
1.
Question 1
An online gardening magazine wants to understand why its subscriber numbers have been increasing. What kind of reports can a data analyst provide to help answer that question? Select all that apply.
1 point
Reports that examine how a recent 50%-off sale affected the number of subscription purchases
Reports that describe how many customers shared positive comments about the gardening magazine on social media in the past year
Reports that compare past weather patterns to the number of people asking gardening questions to their social media
Reports that predict the success of sales leads to secure future subscribers
2.
Question 2
Fill in the blank: A doctor’s office has discovered that patients are waiting 20 minutes longer for their appointments than in past years. To help solve this problem, a data analyst could investigate how many nurses are on staff at a given time compared to the number of _____.
1 point
doctors on staff at the same time
negative comments about the wait times on social media
patients with appointments
doctors seeing new patients
3.
Question 3
Fill in the blank: In data analytics, a question is _____.
1 point
a subject to analyze
an obstacle or complication that needs to be worked out
a way to discover information
a topic to investigate
4.
Question 4
When working for a restaurant, a data analyst is asked to examine and report on the daily sales data from year to year to help with making more efficient staffing decisions. What is this an example of?
1 point
An issue
A business task
A breakthrough
A solution
5.
Question 5
What is the process of using facts to guide business strategy?
1 point
Data-driven decision-making
Data visualization
Data ethics
Data programming
6.
Question 6
At what point in the data analysis process should a data analyst consider fairness?
1 point
When conclusions are presented
When data collection begins
When data is being organized for reporting
When decisions are made based on the conclusions
7.
Question 7
Fill in the blank: _____ in data analytics is when the data analysis process does not create or reinforce bias.
1 point
Transparency
Consideration
Predictability
Fairness
8.
Question 8
A gym wants to start offering exercise classes. A data analyst plans to survey 10 people to determine which classes would be most popular. To ensure the data collected is fair, what steps should they take? Select all that apply.
1 point
Ensure participants represent a variety of profiles and backgrounds.
Survey only people who don’t currently go to the gym.
Collect data anonymously.
Increase the number of participants.
Answers
The correct options are:
Reports that examine how a recent 50%-off sale affected the number of subscription purchasespatients with appointmentsa way to discover informationA business taskData-driven decision-makingWhen conclusions are presentedFairnessa. Ensure participants represent a variety of profiles and backgrounds.c. Collect data anonymously.d. Increase the number of participants.What is the sentences about?This report looks at how many people bought subscriptions during a recent sale where everything was half price. This will show if the sale made more people subscribe and if it helped increase the number of subscribers.
The report can count how many nice comments people said and show if subscribers are happy and interested. This can help see if telling friends about the company has made more people become subscribers.
Learn more about gardening from
https://brainly.com/question/29001606
#SPJ1
Reports, investigating, fairness, data-driven decision-making, gym classes
Explanation:Question 1:A data analyst can provide the following reports to help understand why the subscriber numbers of an online gardening magazine have been increasing:
Reports that examine how a recent 50%-off sale affected the number of subscription purchasesReports that describe how many customers shared positive comments about the gardening magazine on social media in the past yearReports that compare past weather patterns to the number of people asking gardening questions on their social mediaReports that predict the success of sales leads to secure future subscribersQuestion 2:A data analyst could investigate the number of patients with appointments compared to the number of doctors on staff at a given time to help solve the problem of longer waiting times at a doctor's office.
Question 3:In data analytics, a question is a topic to investigate.
Question 4:When a data analyst is asked to examine and report on the daily sales data from year to year to help with making more efficient staffing decisions for a restaurant, it is an example of a business task.
Question 5:The process of using facts to guide business strategy is called data-driven decision-making.
Question 6:A data analyst should consider fairness when conclusions are being presented during the data analysis process.
Question 7:Transparency in data analytics is when the data analysis process does not create or reinforce bias.
Question 8:To ensure the collected data is fair when surveying 10 people to determine popular classes for a gym, a data analyst should: ensure participants represent a variety of profiles and backgrounds, collect data anonymously, and increase the number of participants.
Learn more about Data analysis here:https://brainly.com/question/33332656
You are the computer forensics investigator for a law firm. The firm acquired a new client, a young woman who was fired from her job for inappropriate files discovered on her computer. She swears she never accessed the files. You have now completed your investigation. Using what you have learned from the text and the labs, complete the assignment below. You can use your imagination about what you found!
Write a one page report describing the computer the client used, who else had access to it and other relevant findings. Reference the tools you used (in your imagination) and what each of them might have found.
Answers
Confidential Computer Forensics Investigation Report
Case Number: 2023-4567
Date: June 22, 2023
Subject: Computer Forensics Investigation Findings
I. Introduction:
The purpose of this report is to provide an overview of the computer forensics investigation conducted on behalf of our client, Ms. [Client's Name], who was terminated from her employment due to the discovery of inappropriate files on her computer. The objective of the investigation was to determine the origin and access of these files and establish whether Ms. [Client's Name] was involved in their creation or dissemination.
II. Computer Information:
The computer under investigation is a Dell Inspiron laptop, model XYZ123, serial number 7890ABCD. It runs on the Windows 10 operating system and was assigned to Ms. [Client's Name] by her former employer, [Company Name]. The laptop's storage capacity is 500GB, and it is equipped with an Intel Core i5 processor and 8GB of RAM.
III. Access and Usage:
During the investigation, it was determined that Ms. [Client's Name] was the primary user of the laptop. The computer was password-protected with her unique login credentials, indicating that she had exclusive access to the system. The investigation did not uncover any evidence of unauthorized access by third parties or multiple user accounts on the laptop.
IV. Forensic Tools and Findings:
Digital Forensic Imaging: A forensic image of the laptop's hard drive was created using the industry-standard forensic tool, EnCase Forensic. The image provided an exact replica of the laptop's data, preserving its integrity for analysis.
Internet History Analysis: The forensic examination of the laptop's web browser history was conducted using specialized software, such as Internet Evidence Finder (IEF). This analysis revealed that Ms. [Client's Name] had not accessed any inappropriate websites or content during the relevant timeframe.
File Metadata Examination: Using the forensic software Autopsy, a comprehensive analysis of file metadata was performed. The investigation determined that the inappropriate files in question were created and modified during hours when Ms. [Client's Name] was not logged into the system, indicating that she was not responsible for their creation.
Deleted File Recovery: Utilizing the tool Recuva, the investigation team conducted a thorough search for any deleted files related to the case. No evidence of deleted files or attempts to conceal inappropriate content was discovered on the laptop.
V. Conclusion:
Based on the findings of the computer forensics investigation, it is evident that Ms. [Client's Name] was not involved in the creation or dissemination of the inappropriate files found on her laptop. The analysis of digital evidence, including internet history, file metadata, and deleted file recovery, supports her claim of innocence.
The investigation did not uncover any evidence of unauthorized access to the laptop, indicating that Ms. [Client's Name] was the sole user of the system. It is recommended that our law firm presents these findings to [Company Name] in defense of our client, highlighting the lack of evidence implicating her in the inappropriate content discovered on her computer.
Please note that this report is confidential and intended for internal use within our law firm.
Sincerely,
[Your Name]
Computer Forensics Investigator
[Law Firm Name]
I hope this helps. Cheers! ^^
Which of the following clauses will stop the loop when the value in the intPopulation variable is less than the number 5000?
Answers
Answer:All of the above
Explanation:
Georgia is using a specific type of encryption method that only codes a certain section of the files on her hard drive. What type of
encryption is Georgia using?
A device encryption
B. private key encryption
C. volume encryption
D.
half encryption
Answers
the
Wnte
that
Program
will accept three
Values of
sides of a triangle
from
User and determine whether Values
carceles, equal atera or sealen
- Outrast of your
a
are for
an
Answers
Answer:
try asking the question by sending a picture rather than typing
Write a C++ program that creates a word-search puzzle game where the user should find the hidden
words in a square array of letters. Your program should first read from the user their choice for the
game: a) easy, b) medium, c) hard, d) exit the game. If the user selects easy, then the 6x6 puzzle,
shown in Figure 1, will be generated and displayed to the user. If the user selects medium, then the
14 x 14 puzzle shown in Figure 2 should be generated and displayed and lastly, if the user selects
the hard choice, the program should generate a random puzzle, filling the square array of 20 x 20
using random characters/words.
Then your program should repeatedly read from the user, a word to be searched for in the puzzle,
the row and column number where the word starts from and which orientation to search for. The
words can be searched vertically (top to bottom), horizontally (left to right), diagonally (upper left
to lower right) and diagonally (upper right to lower left). The program should check if the column
and row number given by the user are inside the puzzle (array) boundaries, otherwise should display
an error message and ask the user to enter another position. For each word the user inputs, the
2
program should display whether the word was found or not. The program should stop reading
words when the user will press “X” and then the total number of found words will be displayed to
the user.
The program should repeatedly display the game menu until the user will select to exit the game
Answers
C++ program to create a word-search puzzle game. #include <iostream> #include <cstring> using namespace std; int main() { char input; cout << "Choose.
What is program technology?Any technology (including, without limitation, any new and practical process, method of manufacture, or composition of matter) or proprietary material developed or first put into use (actively or constructively) by either Party in the course of the Research Program is referred to as "Program Technology."
A 33 board with 8 tiles (each tile has a number from 1 to 8) and a single empty space is provided. The goal is to use the vacant space to arrange the numbers on the tiles so that they match the final arrangement. Four neighboring (left, right, above, and below) tiles can be slid into the available area.
Therefore, C++ programs create a word-search puzzle game. #include <iostream> #include <cstring>
Learn more about the program here:
https://brainly.com/question/11023419
#SPJ1
Describe the first generation of computer based on hardware, software, computer characteristics, physical appearance and their applications?
Answers
Answer:
The first generation of computers was developed in the 1940s and 1950s, and was characterized by the use of vacuum tubes as the primary component of their electronic circuits. These computers were large, expensive, and required a lot of power to operate. Here are some key characteristics of first-generation computers:
Hardware: First-generation computers used vacuum tubes for logic circuitry, which were large, fragile, and generated a lot of heat. They also used magnetic drums or tape for data storage.
Software: Early computer programming languages were developed during this time, including machine language and assembly language. Programs were written on punched cards or paper tape and fed into the computer by operators.
Computer characteristics: First-generation computers were slow and had limited memory capacity. They were also very expensive and often required specialized operators to use them.
Physical appearance: First-generation computers were large and took up entire rooms. They consisted of racks of electronic equipment, with wires and tubes connecting everything together. The user interface was typically a console with switches and lights.
Applications: First-generation computers were primarily used for scientific and military applications, such as calculating missile trajectories or decrypting codes. They were also used in business for accounting and payroll purposes.
Some examples of first-generation computers include the ENIAC (Electronic Numerical Integrator and Computer), UNIVAC (Universal Automatic Computer), and IBM 701. Despite their limitations, these early computers represented a major milestone in the development of computing technology and laid the foundation for future generations of computers.
What will the output of the statements below? System.out.println(9%2); System.out.println(12%6); The output of the first statement is * The output of the second statement is
Answers
Answer:
You get Exact 30 print of that sentence on a comadore 64
Explanation:
Just simple basic science. hope this helps
How does a fully integrated Data and Analytics Platform enable organizations to
convert data into consumable information and insight?
Answers
A fully integrated Data and Analytics Platform enable organizations to convert data into consumable information and insight by:
How does a fully integrated Data and Analytics Platform enable convert data?This is done by putting together or the archiving of all the captured data and also the act of getting them back if and when needed for business purpose.
Note that it is also done by making analytics reports and creating Machine Learning models to refine the data.
Learn more about Analytics Platform from
https://brainly.com/question/27379289
#SPJ1
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Which famous British physicist wrote A Brief History of Time?
Answers
Answer:
Stephen Hawking
What are the letters associated with home rows keys?
Answers
Answer:
The letters are 'a s d f g h j k l ;' .These are the letters associated with the home keys.
Answer:
In order to maximize the range your two hands can reach on a keyboard, they should be positioned in the middle of the keyboard.Your left fingers should be resting on the letters A,S,D and F.And your right fingers should be resting on the keys J,K,Land semicolon.This set of eight keys is known as home row
Which of the following organizations maintains a database of vulnerabilities and uses the CVE format?
Answers
NIST, A section of the US Department of Commerce is the National Institute of Standards and Technology.
How do CVE details work?NVD data is combined with information from other databases, such the Exploit Database, in a database called CVE Details. You can browse vulnerabilities by vendor, product, type, and date using this tool. It contains vulnerabilities specified by Bugtraq ID, Microsoft Reference, CVE, and others.
How is CVE made?A potential cybersecurity vulnerability is first identified before a CVE Record is created. The CVE Program Secretariat then posts the CVE Record on the CVE website after a CVE Numbering Authority (CNA) has assigned the information a CVE ID and provided a description and references.
To know more about CVE visit:
brainly.com/question/29451810
#SPJ4
I am working on "8.8.7 Chart of Lots of Rolls" in JavaScript if anyone has done this lesson please tell me your code i cant seem to figure this out
Answers
Using knowledge in computational language in JAVA it is possible to write a code that print the results os each roll.
Writting the code:sim_t_ind <- function(n, m1, sd1, m2, sd2) {
# simulate v1
v1 <- rnorm(n, m1, sd1)
#simulate v2
v2 <- rnorm(n, m2, sd2)
# compare using an independent samples t-test
t_ind <- t.test(v1, v2, paired = FALSE)
# return the p-value
return(t_ind$p.value)
}
Can arrays copyOf () be used to make a true copy of an array?There are multiple ways to copy elements from one array in Java, like you can manually copy elements by using a loop, create a clone of the array, use Arrays. copyOf() method or System. arrayCopy() to start copying elements from one array to another in Java.
See more about JAVA at brainly.com/question/12975450
#SPJ1

• List 2 examples of media balance:
Answers
Answer: balance with other life activities
spending time with family
studying / school work
Explanation:
Which of the following statements best represents the impact vaudeville had on the film industry? Early silent films were more realistic than vaudeville shows and less expensive for audiences to see, therefore, silent films became more popular than vaudeville shows. Early silent films used many of the same storylines as vaudeville performances and incorporated vaudeville music. Early silent film producers used many of the same acting techniques popularized in vaudeville performances, even using popular vaudeville stars as actors in their productions. Early silent films were poorly produced and audiences did not enjoy the lack of sound, therefore, it would be some time before films overtook the popularity of vaudeville.
Answers
Answer:
Answer is B: Early silent film producers used many of the same acting techniques popularized in vaudeville performances, even using popular vaudeville stars as actors in their productions.
Explanation:
Answer:
Early film used elements of vaudeville to draw in audiences.
Explanation:
edg2021
Vaudeville were silent films and came first so they did not use early film stars in their theatre.
What additional uses of technology can u see in the workplace
Answers
Answer:
Here are some additional uses of technology in the workplace:
Virtual reality (VR) and augmented reality (AR) can be used for training, simulation, and collaboration. For example, VR can be used to train employees on how to operate machinery or to simulate a customer service interaction. AR can be used to provide employees with real-time information or to collaborate with colleagues on a project.Artificial intelligence (AI) can be used for a variety of tasks, such as customer service, data analysis, and fraud detection. For example, AI can be used to answer customer questions, identify trends in data, or detect fraudulent activity.Machine learning can be used to improve the accuracy of predictions and decisions. For example, machine learning can be used to predict customer churn, optimize marketing campaigns, or improve product recommendations.Blockchain can be used to create secure and transparent records of transactions. For example, blockchain can be used to track the provenance of goods, to manage supply chains, or to record financial transactions.The Internet of Things (IoT) can be used to connect devices and collect data. For example, IoT can be used to monitor equipment, track assets, or collect data about customer behavior.These are just a few of the many ways that technology can be used in the workplace. As technology continues to evolve, we can expect to see even more innovative and creative uses of technology in the workplace.
Treat others the way
a
Like they are your enemy
b
That is all the same
c
You want to be treated
d
The same as you treat your friend
Answers
Answer:
C.
Explanation:
But shi.it i dont treat ppl good when they disrespecting me or my friends i be putting them in hush mode.
This project assumes that you have
completed Project 1. Place several
Student objects into a list and
shuffle it. Then run the sort
method with this list and display all of
the students' information. Print to the
console the unsorted list first of all
students followed by the sorted list of
all students
Answers
Answer:ty
Explanation:ty
The following code shown in the image can be utilized to implement the required functionality, assuming Project 1 entailed developing a class called "Student" with attributes like name, ID number, and GPA.
What is Coding?The process of developing, writing, testing, and maintaining software programme is known as coding, commonly referred to as computer programming. It entails writing code or instructions that a computer can comprehend and use to carry out a certain operation or address an issue.
In the illustrative code, a class called "Student" is first created and given attributes for name, ID number, and GPA. After that, we make a list of some sample students. The student list is shuffled using the random.shuffle() technique.
The list of students is then sorted based on GPA in descending order using the sort() method in conjunction with a lambda function. Then the sorted list of students is printed, followed by the unsorted list.
Thus, the following code shown in the image can be utilized to implement the required functionality, assuming Project 1 entailed developing a class called "Student" with attributes like name, ID number, and GPA.
Learn more about Coding, here:
https://brainly.com/question/17204194
#SPJ2
