Creating a Venn diagram takes specialized computer software.
Please select the best answer from the choices provided
T
F
Answers
Answer:
F
Explanation:
false because you don't need a computer software to make a venn diagram you can make one
Answer:
f
Explanation:
Related Questions
Que ventajas podria traer el internet a la educacion artistica? Ayuda porfa telo pido porfavor
Answers
Answer:
"Informacion"
Explanation:
La internet puede traer las mismas ventajas para la educacion artistica que cualquier otra materia y eso es "Informacion". El arte tiene muchas tecnicas. Tambien hay muchos differentes estilos de arte. La internet tiene toda la informacion sobre los artistas mas famosos de las historia, incluyendo su arte, tecnicas, estilos, temas, historias, etc. Esta informacion es sumamente importante y util por que te enseña a utilizar todos los metodos ya creados y usarlos como herramientas para crear arte que representa el artista que sos.
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
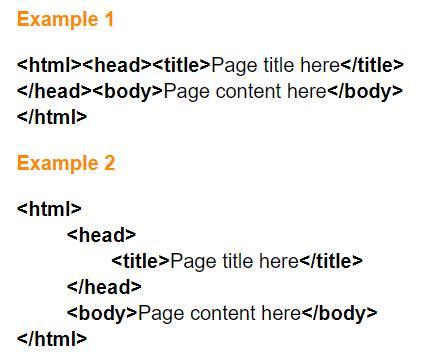
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
can u give me 3 principle of design and explain and write with paragraph?

Answers
Answer:
There are twelve basic principles of design: contrast, balance, emphasis, proportion, hierarchy, repetition, rhythm, pattern, white space, movement, variety, and unity.
Which application software would a teacher use to compute a student's course percentage?
a. presentation software
b. word processors
c. spreadsheets
d. database
Answers
Answer:
spreedsheet
Explanation:
This would help them easily average grades
Which of the following procedures will enable you to sort your spreadsheet by city (Column K) in ascending order? Select all that apply.
Use the SORT function syntax: =SORT(A2:R210, K, TRUE)
Use the SORT function syntax: =SORT(A2:R210, 11, TRUE)
Select A2-R210, then use the drop-down menu to Sort Range by Column K from A to Z
Select A2-R210, then use the drop-down menu to Sort Sheet by Column K from A to Z
Correct. To sort your spreadsheet by city in ascending order, you can use one of two methods. You can use the SORT function syntax =SORT(A2:R210, 11, TRUE)*. You can also select A2-R210, then use the drop-down menu to Sort Sheet by Column K from A to Z.
Answers
It is to be noted that the option that would allow one to sort their spreadsheet is:
SORT function syntax =SORT(A2:R210, 11, TRUE)*. (Option B)A2-R210, then use the drop-down menu to Sort Sheet by Column K from A to Z. (Option D).What does it mean to sort a spreadsheet?When sorting data in a spreadsheet, you may rearrange the data to rapidly discover values. Sorting a range or table of data on one or more columns of data is possible. You can, for example, rank personnel first by the department and then by last name.
Systematic representation is one of the advantages of sorting data. Sorting allows users to represent facts in a fairly methodical way that allows for precise display.
Better data understanding - when data is presented in a sorted and filtered manner, data decoding and understanding become very simple.
Learn more about spreadsheets:
https://brainly.com/question/26919847
#SPJ1
HELP ASAP!!!!
What is the difference between your active and passive digital footprints?
Answers
In the U6_L2_Activity_Three class, write a public static method called hasDuplicates, which has a single parameter of an array of int values. The method should return a boolean which is true if the parameter array contains the same value more than once, and false otherwise. Use the runner class to test this method: do not add a main method to your code in the U6_L2_Activity_Three. Java file or it will not be scored correctly
Answers
Answer:
Here is an implementation of the hasDuplicates method in the U6_L2_Activity_Three class:
import java.util.HashSet;
public class U6_L2_Activity_Three {
public static boolean hasDuplicates(int[] array) {
// Create a HashSet to store the values in the array
HashSet<Integer> set = new HashSet<>();
// Iterate through the array and add each value to the set
for (int value : array) {
if (set.contains(value)) {
// If the value is already in the set, return true
return true;
}
set.add(value);
}
// If no duplicates were found, return false
return false;
}
}
To test this method, you can use the Runner class like this:
public class Runner {
public static void main(String[] args) {
int[] array1 = {1, 2, 3, 4, 5};
int[] array2 = {1, 2, 2, 3, 4, 5};
int[] array3 = {1, 1, 2, 3, 4, 5};
System.out.println(U6_L2_Activity_Three.hasDuplicates(array1)); // should print false
System.out.println(U6_L2_Activity_Three.hasDuplicates(array2)); // should print true
System.out.println(U6_L2_Activity_Three.hasDuplicates(array3)); // should print true
}
}
Explanation:
This will print false, true, and true to the console, indicating that the hasDuplicates method is working as expected.
A digital computer has a memory unit with 26 bits per word. The instruction set consists of 756 different operations. All instructions have an operation code part (opcode) and an address part (allowing for only one address). Each instruction is stored in one word of memory. a. How many bits are needed for the opcode? b. How many bits are left for the address part of the instruction? c. What is the maximum allowable size for memory? d. What is the largest unsigned binary number that can be accommodated in one word of memory?
Answers
Answer:
a. the number of bits needed for the opcode = 10
b. address part is = 16 bits
c. maximum allowable size of memory = 65536
d. Maximum memory size per word = 67108864
Explanation:
The memory size of the instruction set is 756 which is less than 2^10 (that is 1024).
Since the word size is 26 bits and the instruction takes 10, the remaining 16 is for the address part which is 65536 memory address. The maximum number of memory size for a word is 67108864.
Help!!! Who is this? Who is it from?

Answers
Character: Vegito
Convert the following into binary system
and vice versa.
106
Answers
which meaning does the abbreviation c/c represent?
Answers
The phrase "carbon copy" alludes to the message's recipient whose location appears after Cc: header.
What does CC stand for?Carbon copies: To let the recipients of a business letter know who else received it, a cc designation would be placed at the bottom of the letter, followed by the names of those who received carbon copies of the original. The term "cc" in emails refers to the additional recipients who received the message.
A typical email will have a "To" box, a "CC" field, and only a "BCC" section that allows you to enter email addresses. The abbreviation for carbon copy is CC. "Blind carbon copy" is what BCC stands for. The abbreviation BCC stands in blind carbon copy, while Cc stands for carbon copy. When copying someone's email, use Cc for copy them openly or Bcc to copy them secretly.
To learn more about carbon copy refer to :
brainly.com/question/11513369
#SPJ4
Suppose that before you began your college application process, you were offered a job to work as a floor-trainer at a local yoga studio, accompanied by a yearly salary of $27,000 (after taxes). Assume however that you decided to turn down this offer and instead attend a year of college. The total monetary cost of the year of college, including tuition, fees, and room and board expenses, is $43,000.You likely chose to attend college because ____a. you value a year of college less than $43.000b. you value a year of college at $27.000c. you value a year of college at more than $70.000d. you value a year of college at $43.000
Answers
Based on the scenario given, it is safe to assume that the reason why you chose to attend college instead of accepting the job offer as a floor-trainer at a local yoga studio with a yearly salary of $27,000 (after taxes) is because you value a year of college at $43,000.
This means that you believe the benefits of attending college and obtaining a degree are worth the monetary cost of $43,000, which includes tuition, fees, and room and board expenses.It is important to note that the value of a college education extends beyond just the monetary cost. Attending college can provide individuals with opportunities for personal and professional growth, networking, and gaining valuable skills and knowledge that can lead to higher earning potential in the long run. While the decision to attend college may require sacrifices in the short term, the long-term benefits are often worth it for many individuals.Ultimately, the decision to attend college is a personal one that should be based on an individual's goals, values, and priorities. While the cost of college may be a significant factor to consider, it should not be the only one. It is important to weigh the potential benefits and drawbacks of attending college and make an informed decision that aligns with one's personal aspirations and values.For such more question on monetary
https://brainly.com/question/13926715
#SPJ11
joann turned on her windows 10 computer today, and while the computer was booting up, it shut down. she restarted the computer and it booted fine but ran slowly. she opened task manager and noticed that her cpu was running at 98% capacity and her network at 75% capacity. when she checked to see what process was using so much network connectivity, she received a message saying that access to the process was denied.
Answers
Based on these indicators, the clear actions which Joann should do with her computer are:
Run antivirus software.Disconnect from the network.Check the file permissions.What is System Security?This refers to the precautions or measures that are taken in order to safeguard or protect a computer system or network from unauthorized usage through the use of things like firewalls, etc.
Hence, we can see that based on the given question, we are told that Joann turned on her windows 10 computer today, and while the computer was booting up, it shut down and when she re-booted it, she found out that her CPU was running at 98% capacity and her network at 75% capacity.
The best actions that she has to take in order to address these issues and also the issue of network connectivity are listed above which are using an antivirus to scan, disconnect from the network, and check file permissions.
Read more about system security here:
https://brainly.com/question/25720881
#SPJ1
The complete question is:
Joann turned on her Windows 10 computer today, and while the computer was booting up, it shut down. She restarted the computer and it booted fine but ran slowly. She opened Task Manager and noticed that her CPU was running at 98% capacity and her network at 75% capacity. When she checked to see what process was using so much network connectivity, she received a message saying that access to the process was denied.
Based on these indicators, what should Joann do with her computer? (Select all that apply.)
consider a virtual address space of 64 pages of 1,024 bytes each, mapped onto a physical memory of 32 page frames.
Answers
The page size is 1,024 bytes and the page frame size is 2,048 bytes.
Given a virtual address space of 64 pages and a physical memory of 32 page frames, we can determine the size of the pages and page frames.
Virtual address space:
Number of pages = 64
Page size = 1,024 bytes
Physical memory:
Number of page frames = 32
To calculate the page size, we divide the size of the virtual address space by the number of pages:
Page size = (Size of virtual address space) / (Number of pages)
Page size = (64 * 1,024) / 64
Page size = 1,024 bytes
To calculate the page frame size, we divide the size of the virtual address space by the number of page frames:
Page frame size = (Size of virtual address space) / (Number of page frames)
Page frame size = (64 * 1,024) / 32
Page frame size = 2,048 bytes
Know more about bytes here:
https://brainly.com/question/15166519
#SPJ11
Use the traceroute program to find the path to a destination of your choice. After you have obtained the output, supply the following information. Destination address Number of hops IP addresses of the five nodes where there is the maximum delay and the delay experienced on these hops. Perform the traceroute to the same destination at another day and time. Check whether there exist any changes. Explain possible reasons for the appearance of some differences. Ans -
Answers
Traceroute is a networking program that is used to trace the route between a network host and a destination device by computing an Internet Protocol (IP) network path.
It uses User Datagram Protocol (UDP) datagrams to do so. Using the traceroute command, you can trace the path a packet takes from your computer to a remote computer over an IP network. The hop count can vary, so the number of network devices the packet passes through varies. You can run the traceroute command multiple times to determine the path the packet takes to the destination.
You may also use the program to troubleshoot network issues such as slow network speeds and high latency. Destination address: I will use brainly.com as the destination address. Number of hops: The number of hops taken to reach the destination address is 12.
IP addresses of the five nodes where there is the maximum delay and the delay experienced on these hops are as follows: 1. 192.168.1.1 - Delay: 1ms 2. 67.59.255.61 - Delay: 27ms 3. 173.231.56.50 - Delay: 12ms 4. 173.231.56.54 - Delay: 0ms 5. 207.148.24.29 - Delay: 78ms.
To know more about networking visit:
https://brainly.com/question/29350844
#SPJ11
Write a Scientific report modeling a written reasearch paper on big data applications.

Answers
Big data applications is known to be the methods and ways that are often used to handle large amount of data.
What is Scientific data modeling in big data?Data modeling is known to be the ways of analyzing the “areas” of interest to one's organization and how these things is linked to each other.
Note that The data modeling helps us to know and also helps in documentation of the data resources needed for one's business.
Big data are often measured by terabytes and lots more and as such managing them is one that is time-consuming,.
Learn more about Big data from
https://brainly.com/question/19049345
#SPJ1
create constructors and destructors for each class you make from a converted ""struct""
Answers
In C++, a struct and a class are nearly identical, except that a struct defaults to public member access, while a class defaults to private member access. To convert a struct to a class, you simply change the keyword struct to class. Here's an example:
class Person {
public:
// Constructor
Person(std::string n, int a) : name(n), age(a) {}
// Destructor
~Person() {}
// Public member variables
std::string name;
int age;
};
In this example, we've converted a struct called Person into a class called Person. We've added a constructor that takes a std::string and an int as arguments and initializes the name and age member variables. We've also added an empty destructor. Since all member variables are now private by default, we've added the public: access specifier to the top of the class to indicate that the name and age member variables are public.
If you have multiple classes, you would create constructors and destructors for each class in the same way, by defining them within the class definition.
To learn more about keyword
https://brainly.com/question/10055344
#SPJ11
R CODING QUESTION: I have been given a set of 141 values. The question is asking me to remove the largest 10 elements of the given vector. How would I go about doing that? I know the max() function gives me the single greatest value, but I'm not sure if I'm on the right track or not.
Answers
To remove the largest 10 elements from a vector in R, you can follow these steps:
1. Create a vector with 141 values. Let's call it my_vector.
2. Use the order() function to obtain the indices of the vector elements in ascending order. This will give you the indices of the smallest to largest values.
sorted_indices <- order(my_vector)
3. Use the tail() function to select the last 131 values from the sorted_indices vector. These will correspond to the indices of the 10 largest values in the original vector.
largest_indices <- tail(sorted_indices, 10)
4. Use the negative sign (-) to subset the original vector and exclude the elements at the largest_indices.
trimmed_vector <- my_vector[-largest_indices]
Now, trimmed_vector will be a new vector with the largest 10 elements removed from the original my_vector.
To know more about vector
https://brainly.com/question/30508591
#SPJ11
72.7% complete question a government agency is getting rid of older workstations. the agency will donate these workstations, along with other excess computer systems, to nearby schools. management reminds the systems administrators about data sanitization and security concerns. what actions secure the systems prior to donating to the schools?
Answers
There are a few steps that the systems administrators can take to secure the systems prior to donating them to the schools:
Erase all data: It is important to ensure that all data on the systems is erased prior to donating them. This can be done by performing a factory reset on the systems or by using a data erasure tool.Remove any sensitive information: If the systems contain any sensitive information, such as passwords or confidential documents, it is important to remove this information prior to donating the systems.Update the operating system: Make sure that the operating system on the systems is up to date with the latest security patches and updates. This will help to protect against any vulnerabilities that may have been discovered since the systems were last used.The other steps that the systems administrators can take to secure the systems prior to donating them to the school is shown below:
Disconnect any external storage devices: Any external storage devices, such as hard drives or USB drives, should be disconnected from the systems before they are donated.Remove any proprietary software: If the systems contain any proprietary software, it is important to remove this software prior to donating the systems. This will ensure that the software is not used without the proper license.Learn more about workstation, here https://brainly.com/question/13085870
#SPJ4
To prevent and remove malware infections you should manually install and run anti-malware software, keep software and OSes up to date with current patches, and be careful when downloading files, programs, attachments, and such.
True
False
Answers
introduction of waste management
Answers
Answer:
Waste management (or waste disposal) includes the activities and actions required to manage waste from its inception to its final disposal. ... Waste management deals with all types of waste, including industrial, biological and household. In some cases, waste can pose a threat to human health.
Michaela has been tracking the temperatures of the dirt, pond water, and air near her home for a science investigation. She is ready to analyze the data to prepare for her science report. Based on each application’s strengths and weaknesses, which one would be the best to choose for this task?
Answers
Answer:
The science of investigation
Explanation:
hope it help
Which two devices are used to connect iot devices to a home network? (choose two. ).
Answers
The most widely used LAN technology is Ethernet, which offers a connected connectivity system to link numerous IoT devices using an Ethernet switch.
What are the two IoT gadgets?Smart Home: Amazon Echo and Gogl Home The Amazon Echo and Gogl Home are two of the most well-liked linked gadgets in the consumer IoT.
How does the IoT integrate with household appliances?IoT home automation refers to the capacity to operate domestic appliances through internet-connected, electronically controlled systems. Complex heating and lighting systems, as well as alarms and home security controls, may all be pre-programmed and remotely managed via a mobile app.
To know more about LAN visit :-
https://brainly.com/question/13247301
#SPJ4
If you have created users with administrator privileges on your windows 7 or linux systems, why bother creating other user accounts?
Answers
The reason one bother creating other user accounts so that others such as friends can be able to make some changes that you want them to do and it is also to make sure that an administrator does not inadvertently make alterations without knowing that is any form of administrative change.
What Does Administrative Privileges Mean?The term Administrative privileges are known to be the ability to have or create some major changes to any given system, such as an operating system.
Note that based on the above, The reason one bother creating other user accounts so that others such as friends can be able to make some changes that you want them to do and it is also to make sure that an administrator does not inadvertently make alterations without knowing that is any form of administrative change.
Learn more about administrator privileges from
https://brainly.com/question/26389124
#SPJ1
What six things can you do with GIS?
Answers
Answer:
You can:
- Change detection
- Transport route planning
- Flood risk mapping
- Site selection
- Weed and pest management
- Koala habitat mapping
Hope this helps! :)
Shellsort (more accurately Shell’s sort) is an important sorting algorithm that works by applying insertion sort to each of several interleaving sublists of a given list. On each pass through the list, the sublists in question are formed by stepping through the list with an increment hi taken from some predefined decreasing sequence of step sizes, h1 > ... > hi > ... > 1, which must end with 1. (The algorithm works for any such sequence, though some sequences are known to yield a better efficiency than others. For example, the sequence 1, 4, 13, 40, 121, . . ., used, of course, in reverse, is known to be among the best for this purpose.)
a. Apply shellsort to the list
E F A J K I P Z B W C
b. Is shellsort a stable sorting algorithm?
Plot the data from all your runs on 1 graph. What does the resulting graph tell you about the efficiency of each of these algorithms?
Answers
Shellsort is a sorting algorithm that applies insertion sort to interleaving sublists with decreasing step sizes. In this case, we are given a list of elements: E, F, A, J, K, I, P, Z, B, W, C. We need to apply shellsort to sort this list. Additionally, we need to determine if shellsort is a stable sorting algorithm. Finally, we are asked to plot the data from all the runs on a graph to analyze the efficiency of the algorithm.
To apply shellsort to the given list, we start with a predefined sequence of step sizes, such as 1, 4, 13, 40, 121, ..., in reverse order. We perform insertion sort on sublists created by stepping through the list using each step size. The algorithm continues with smaller step sizes until the final step size of 1 is reached.
Applying shellsort to the list E, F, A, J, K, I, P, Z, B, W, C would involve multiple passes and comparisons between elements in the sublists. After applying shellsort, the list would be sorted in ascending order.
Shellsort is not a stable sorting algorithm. A stable sorting algorithm maintains the relative order of elements with equal values. However, shellsort's swapping operations during the sorting process can disrupt the relative order of equal elements.
To analyze the efficiency of shellsort and other sorting algorithms, we need to plot the data from multiple runs on a graph. The resulting graph can provide insights into the performance and efficiency of different sorting algorithms, allowing us to compare their time complexities, execution times, or other metrics. By analyzing the graph, we can determine which algorithm performs better in terms of efficiency for the given dataset.
Learn more about algorithm here :
https://brainly.com/question/33344655
#SPJ11
Which of these best describes the sculpting process?
A.
manipulating vertices with the move, rotate, and scale tools
B.
adding modifiers to the geometry adjust and add detail
C.
using brush-like tools to push, pull, and carve detail into the mesh
D.
using carefully crafted curves to create a mesh
Answers
The best option that describes the sculpting process is C. Using brush-like tools to push, pull, and carve detail into the mesh. Sculpting is a method of creating a 3D model by manipulating a digital mesh using a set of tools. In sculpting, the artist can add and subtract from the mesh, carve details, and refine shapes until the desired form is achieved.
The process is similar to molding or sculpting with clay, where the artist shapes the material with their hands. To achieve the desired form in digital sculpting, the artist uses brush-like tools that simulate the behavior of real-world tools such as clay sculpting tools or chisels. These tools include brushes that can push, pull, smooth, and add details to the mesh. The sculpting process is an iterative one, where the artist continually refines the shape and details until the desired level of realism or stylization is achieved.
Options A and D are not correct because they refer to the creation of the mesh, not the sculpting process. Manipulating vertices with move, rotate, and scale tools is a technique used in 3D modeling to create the basic shape of the mesh. Using carefully crafted curves to create a mesh is a technique used in 3D modeling, but it is not specific to the sculpting process. Option B is not the best description of the sculpting process because adding modifiers to the geometry to adjust and add detail is more commonly associated with 3D modeling, where the focus is on creating precise shapes and objects rather than artistic expression. While modifiers can be used in sculpting, they are not the primary tool used for adding detail and refining the shape of the mesh.
To know more about sculpting process visit :
https://brainly.com/question/31961687
#SPJ11
An office building has two floors. A computer program is used to control an elevator that travels between the two floors. Physical sensors are used to set the following Boolean variables.
The elevator moves when the door is closed and the elevator is called to the floor that it is not currently on.
Which of the following Boolean expressions can be used in a selection statement to cause the elevator to move?
answer choices
(onFloor1 AND callTo2) AND (onFloor2 AND callTo1)
(onFloor1 AND callTo2) OR (onFloor2 AND callTo1)
(onFloor1 OR callTo2) AND (onFloor2 OR callTo1)
(onFloor1 OR callTo2) OR (onFloor2 OR callTo1)
Answers
The following Boolean expressions, "onFloor1 AND callTo2" or "onFloor2 AND callTo1," can be used in a selection statement to move the elevator.
The commands to move the lift may be simply determined based on the other commands designed to be provided and received by the lift, which indicate what operation it is engaged in.
When the elevator is on the first floor and has to be taken to the second floor, the order "onFloor1 AND callTo2" can be used. The order "onFloor2 AND callTo1" would serve as the reverse of the previously given instruction and cause the lift to operate in the exact opposite manner.
To know more about elevator visit:-
https://brainly.com/question/2168570
#SPJ4
Complete the following sentence.
Tony ___________ is considered an expert in the field of mind mapping.
Answers
Answer:
The answer is Buzan.
Answer:
Buzan
Explanation:
what is a disease a health problem as it is experienced by the one affected a consequence of foraging quizlet
Answers
A disease is a health problem that occurs as a result of various factors, including genetic predisposition, environmental influences, lifestyle choices, and exposure to pathogens or harmful substances. It is experienced by the individual affected and manifests through symptoms, signs, or abnormal physiological functions.
Diseases can have diverse causes and can affect different body systems or organs. They can be infectious, caused by pathogens such as bacteria, viruses, fungi, or parasites, or they can be non-infectious, resulting from factors like genetic mutations, immune system dysfunction, or lifestyle factors.
Foraging, which refers to the act of searching and obtaining food, is not typically considered a direct consequence of disease. However, malnutrition or inadequate dietary intake due to difficulties in foraging can indirectly contribute to the development or progression of certain diseases. For example, if an individual is unable to obtain a balanced diet or lacks access to essential nutrients, it can lead to malnutrition-related diseases, such as vitamin deficiencies or protein-energy malnutrition.
While foraging is not directly linked to disease development, it indirectly affects health outcomes through its impact on nutrition and overall well-being. Diseases are complex and multifactorial, influenced by a combination of genetic, environmental, and lifestyle factors. Understanding the causes and consequences of diseases is crucial for prevention, diagnosis, and effective treatment.
To know more about disease , visit
https://brainly.com/question/30166675
#SPJ11