Create a mobile app plan using PowerPoint slides to show mock-ups of screens, identifying input, process, and output for each screen.
You are going to design a mobile app. Think of something you would like to use or something that fills a need you see among your friends and family. You will create wireframes, visual representations of each screen along with the processes that occur on each screen.
Your app needs to have at least three screens. For each screen, you will "sketch" the screen and identify the input-process-output that occurs on that screen. You will also identify how a screen transfers to another screen. For example, suppose you were designing an app to help students at your school find another student who can tutor them. The welcome screen could look like the one shown here, where the user chooses the subject, times and days available, and then selects the "Find a tutor" button. The note at the bottom explains the processing that occurs on the page. It also identifies how this screen connects to the available tutors screen. One screen may connect to more than one other screen.
Screen Requirements
Each screen should have each of the following. The list shows, in the parentheses, which part of the example meets each requirement.
a title (Welcome Screen)
a sketch of the screen (Notifications table). You can sketch your screens on paper and take a picture of it; you can draw your screens in a drawing application such as Paint
a description of the input-process-output for each screen, which includes how one screen transfers to other screens (the notes at the bottom)
You need at least three screens in your app. The tutor app would have at least three screens: Welcome Screen, Available Tutors, and Scheduled Tutoring Sessions. Your app can have more screens as needed.
Variations
The sample screen shown here is part of a PowerPoint presentation that has a slide for each screen. It uses tables as a simple way to show what the screen looks like. You could also draw your screens by hand and take pictures of your screens. Then add them to a PowerPoint, Word, or similar file. You can include images on your screens as needed.
Reminder
Be sure you remember to describe the input-process-output for each screen and how it connects to other screens. Compare your work to the rubric before you turn it in.
What to Turn In
Your PowerPoint, Word, or other file that has the visual representation of at least three screens, the notes describing the input-process-output that occurs on the screen, and a description of how each screen connects to other screens.
Answers
The three major elements of great PowerPoints are your command of PowerPoint's design tools, your concentration on presentation techniques, and your commitment to upholding a consistent style.
Here are a few simple tips to help you get started learning each of those components. Don't forget to look at the powerpoint presentation and further resources listed at the end of this post.
To help you create presentations with a cohesive style, Microsoft comes with pre-installed themes and color palettes.
To select one of these pre-built themes, select the File tab once more, then select New, choose an option, and finally click Create. Alternately, you can make your own "theme" by utilizing PowerPoint's tools, your own sense of style, and your company's color scheme.
Thus, Your mastery of PowerPoint's design tools, your focus on presenting procedures, and your dedication to maintaining a consistent style are the three primary components of great PowerPoints.
Learn more about Powerpoint, refer to the link:
brainly.com/question/15992747
#SPJ6
Related Questions
(01.01 LC)
Programmers perform which of the following tasks?
Build and maintain network connections
O Create web and mobile applications
O Design graphics for websites
Repair computers and servers
Answers
Answer:
Create web and mobile applacations
Explanation:
Programmers primarily build and maintain software applications, including web and mobile applications.
What is software?Programmers typically work with software, which is a collection of instructions and programmes that instruct a computer or other electronic device on what to do.
They create, test, and maintain software applications for desktops, mobile devices, and the web using programming languages such as Java, Python, and C++.
Programmers create and maintain software applications, such as web and mobile applications.
They may also design the application's user interface and user experience, but they are not typically in charge of designing graphics for websites.
Furthermore, while programmers may be involved in troubleshooting and resolving issues related to the software application they have created, they are not typically in charge of repairing hardware such as computers and servers.
Thus, the correct answer is "Build and maintain network connections".
For more details regarding software, visit:
https://brainly.com/question/985406
#SPJ2
What would be the value of the variable list after the execution of the following code?
list = [1, 2, 3, 4]
list[3] = 10
a.[1, 2, 3, 10]
b.[1, 2, 10, 4]
c.[1, 10, 10, 10]
Answers
Answer: a) [1, 2, 3, 10]
Explanation:
Lists have indexes. Basically, starting from the first element of a list, you count up from 0. So the first element in the list has an index of 0. The second element has an index of 1. And so on.
list = [1, 2, 3, 4] defines a list with four elements. list[3] = 10 assigns the third index to a value of 10. We need to know which element has an index of 10, so we count up. 1 has an index of 0. 2 has an index of 1. 3 has an index of 2. And 4 has an index of 3. So whatever value is in the third index is replaced by a new value of 10.
Therefore the new list will look like [1, 2, 3, 10].
What is 4991 rounded to the nearest thousand
Answers
Answer:
5000
Explanation:
Answer: 5000
Explanation:
This is the answer because of the nine’s.
define the distinction between computer science, information systems, engineering, and information technology.
Answers
The distinction between computer science, information systems, engineering, and information technology.
1. Computer Science: Computer science is the study of algorithms, data structures, and the theory behind computing. It focuses on designing, developing, and analyzing software and hardware systems. Computer scientists aim to create efficient and innovative solutions to complex problems using programming languages and computational theories.
2. Information Systems: Information systems is the study of how organizations use technology to manage, store, and analyze data to make informed decisions. This field combines aspects of computer science and business management to create efficient systems that meet the needs of both technical and non-technical users. Information systems professionals often work on designing, implementing, and maintaining databases, networks, and software applications to optimize organizational processes.
3. Engineering: Engineering is a broad discipline that involves the application of scientific principles to design, build, and maintain structures, machines, systems, and processes. Engineering encompasses various specialized fields, including civil, electrical, mechanical, and software engineering. Engineers use their expertise to develop solutions to real-world challenges, such as constructing bridges, designing electronic devices, or creating software applications.
4. Information Technology: Information technology (IT) is the use of computer systems, hardware, and software to store, process, and transmit information. IT professionals are responsible for managing and maintaining the technology infrastructure of an organization, including servers, networks, and databases. Their primary goal is to ensure the smooth operation and security of information systems, as well as to provide support and troubleshooting services to users.
Learn more about troubleshooting here:
https://brainly.com/question/29736842
#SPJ11
____ comes bundled with Windows. Network Monitor, a component of Microsoft Systems Management Server (SMS), enables you to detect and troubleshoot problems on LANs,WANs, and serial links running the Microsoft Remote Access Server (RAS).
Answers
Answer:
Network Monitor
Explanation:
HOW MANY PROGRAMMING LANGUAGES SHOULD I LEARN TO MAKE A GAME LIKE AGAR.IO, SLITHER.IO ETC
Answers
Answer:
learn to make slither
Explanation:
it is such a cool game
also please can you heart and like my comment and rate it 5 stars please and give it brainliest pls i beg you thx !!!
Answer:
u could learn one as simple as scratch program language the one with the orange cat
Explanation:
coding is really hard i do not understnad java at all
for the ip address, 10.10.40.2/19, what is its subnet address and subnet mask in decimal?
Answers
To find the subnet address and subnet mask in decimal for the IP address 10.10.40.2/19, please follow these steps:
1. Convert the prefix length (/19) to a binary subnet mask:
The prefix length of 19 means that the first 19 bits are set to 1, and the remaining bits are set to 0. The binary subnet mask will look like this: 11111111.11111111.11100000.00000000
2. Convert the binary subnet mask to decimal:
11111111.11111111.11100000.00000000 in decimal is 255.255.224.0. This is the subnet mask.
3. Perform a bitwise AND operation between the IP address and the subnet mask to find the subnet address:
IP address (in binary): 00001010.00001010.00101000.00000010
Subnet mask (in binary): 11111111.11111111.11100000.00000000
Subnet address (in binary): 00001010.00001010.00100000.00000000
4. Convert the binary subnet address to decimal:
00001010.00001010.00100000.00000000 in decimal is 10.10.32.0. This is the subnet address.
Your answer: For the IP address 10.10.40.2/19, its subnet address is 10.10.32.0, and its subnet mask in decimal is 255.255.224.0.
Learn more about subnets here:
https://brainly.com/question/30995993
#SPJ11
What words are familiar to people involved with computers? printer network, mouse and monitor screen software
Answers
The words that are familiar to people involved with computers are network, mouse and monitor screen.
What is a computer?A computer simply refers to an electronic device that is designed and developed to receive data in its raw form as an input and processes these data into an output (information), which could be used by an end user to perform a specific task through the use of the following:
KeyboardNetworkMonitor screenMouseIn Computer technology, we can logically infer that network, mouse and monitor screen are the words that are familiar to people involved with computers.
Read more on computer here: brainly.com/question/959479
#SPJ4
Answer:
B
Explanation:
network, mouse and monitor
Where would you go to access frequently used icons?
File explorer
File manager
Toolbar
Web browser
Answers
Answer:
b
Explanation:
Answer:
C.) Toolbar
Explanation:
The toolbar is a strip of icons that are frequently used.
) Explain in your own words why this is true, and give an example that shows why the sequence space cannot be smaller. Specifically, for your example, consider a window size of 4. In this case, we need at least 8 valid sequence numbers (e.g. 0-7). Give a specific scenario that shows where we could encounter a problem if the sequence space was less than 8 (i.e. Give a case where having only 7 valid sequence numbers does not work. Explain what messages and acks are sent and received; it may be helpful to draw sender and receiver windows).
Answers
Sequence numbers are crucial in telecommunications to detect message loss or duplication. A proper sequence space is required to avoid misinterpretation and ensure accurate packet transmission and acknowledgment in protocols like TCP.
A sequence number is a serial number assigned to each transmitted packet or datagram in a telecommunications network to enable the receiving device to detect message loss or duplication.
Sequence space cannot be smaller because if the window size is too small, a receiver may misunderstand the transmission of a previous packet as a new packet with the same sequence number, resulting in the loss of information transmitted by the sender. As a result, the receiver needs to keep track of the packets sent by the sender and keep track of the sequence numbers that have already been received.
An example of a problem that could occur when the sequence space is less than 8 is that the window size is 4. Suppose, a sender sends packets numbered 0, 1, 2, and 3, with sequence numbers assigned to each of these packets. The receiver receives packets numbered 0, 1, and 2, and acknowledges the receipt of each of these packets.
However, due to the sequence number's limitations, packet 3 is not acknowledged by the receiver. Instead, the sender retransmits packet 3. The receiver misinterprets the retransmitted packet as a new packet with the same sequence number and discards it, believing that it has already received this packet.
In the TCP protocol, messages and ACKs are used to ensure that the sender and receiver are both on the same page. The ACK (Acknowledgement) is a message that is sent by the receiver to the sender to indicate that the receiver has received and accepted a packet. On the other hand, a message is sent by the sender to the receiver to deliver data.
The sender and receiver windows are used to keep track of the messages sent and received. These windows are used to keep track of the number of packets that have been sent and received by the sender and receiver, respectively.
Learn more about telecommunications : brainly.com/question/28551792
#SPJ11
A(n) ____ is a list of homogeneous elements in which the addition and deletion of elements occurs only at one end.
Answers
Answer:
Stack
Explanation:
In the stack, you add elements with push operation and obtain the last element added with pop operation.
A stack is a list of identical elements, where additions and deletions only happen at one end.
What is stack?A stack is defined as an abstract data type used in computer science that functions as a collection of items. It has two basic operations: Push, which adds an element to the collection, and Pop, which removes the most recently added member that hasn't been removed yet.
A person may add items to the stack using the push operation, and you get the most recent element added using the pop operation. The evaluation of expressions with operands and operators can be done using a stack.
Stacks can be used for backtracking, or to verify if an expression's parentheses match. It can also be used to change the phrase from one form to another. It may be applied to formally manage memories.
Therefore, it is stack.
To learn more about the stack, refer to:
https://brainly.com/question/14257345
#SPJ6
Computers and Technology:
"Sanjay sent 23 text messages on Monday, 25 on Tuesday and 40 on Wednesday."
"Develop an algorithm (pseudocode or flowchart) which accepts the number of text messages sent each day, and computes and outputs the average number of text messages sent daily. Remember that a fraction of a text message cannot be sent!
Also, show the answer in pascal code."
Please help me.
Answers
Answer:
The algorithm:
Input days
sum = 0
for i = 1 to \(days\)
input text
sum = sum + text
end for
average = sum/days
print average
The program in pascal:
var days, sum, text, i:integer;
var average : real;
Begin
write ('Days: '); readln(days);
sum:=0;
for i := 1 to \(days\) do \(begin\)
write ('Text: '); readln(text);
sum:=sum+text;
end;
average := (sum/days);
writeln ('The average text is' , average);
End.
Explanation:
This declares all variables
var days, sum, text, i:integer;
var average : real;
This begins the program
Begin
This gets the number of days from the user
write ('Days: '); readln(days);
Initialize sum to 0
sum:=0;
This iterates through the days
for i := 1 to \(days\) do begin
This gets the text for each day
write ('Text: '); readln(text);
This sums up the texts
sum:=sum+text;
End loop
end;
Calculate average
average := (sum/days);
Print average
writeln ('The average text is' , average);
End program
End.
a heap is represented using an array. is the array {64 42 59 32 39 44} a heap?
Answers
The array {64, 42, 59, 32, 39, 44} is indeed a max heap.
A heap is a binary tree with specific properties, and can be represented using an array. In a max heap, every parent node's value is greater than or equal to its children's values, while in a min heap, the parent node's value is less than or equal to its children's values.
For the given array {64, 42, 59, 32, 39, 44}, we can build the binary tree: ``` 64 / \ 42 59 / \ / 32 39 44 ``` As we can see, 64 (parent) > 42 and 59 (children), 42 (parent) > 32 and 39 (children), and 59 (parent) > 44 (child).
The tree satisfies the max heap property.
Learn more about binary tree at https://brainly.com/question/31360793
#SPJ11
features of web browsers
Answers
Explanation:
Navigation buttons. Refresh button is used to go back and forward while browsing. ...
Refresh button. Refresh buttons is used to force web browser to reload webpage. ...
Stop button. ...
Home button. ...
Web browser's address bar. ...
Integrated search. ...
Tabbed browsing. ...
Bookmark buttons.
Go to the Scenario PivotTable worksheet. Madhu wants to make the PivotTable easier to interpret. Remove the filter from the PivotTable. Use Total Revenue as the row label in cell B3, use Total Expenses as the row label in cell C3, and use Net Income as the row label in cell D3. Display the Revenue, Expenses, and Net Income values in the Currency number format with no decimal places. Display negative values in red, enclosed in parentheses. Resize columns B:D to their best fit using AutoFit.
Answers
Answer:
Click and drag the filter out of the "PivotTable Fields" so that is it empty IMG1. Change the row labels to what it tells you IMG2. Change the values as Currency format shown in the top right corner of IMG3. Select cells B4:D6 and press ctrl1 and match IMG4. Now double press the lines in between B&C, C&D, and D&E.

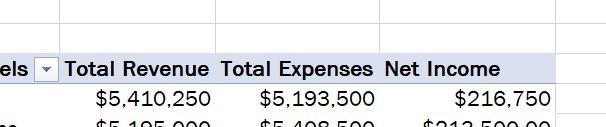


Which option demonstrates when Olga will apply deductive reasoning in the following scenario? Olga is conducting an experiment that compares the spatial reasoning abilities of pigs and dogs.
Olga proposes that pigs will outperform dogs on her spatial reasoning test.
Olga administers a test that allows both pigs and dogs to demonstrate spatial reasoning.
Olga is conducting an experiment that compares the spatial reasoning abilities of pigs and dogs
Olga examines the existing literature concerning spatial reasoning in animals.
Answers
Answer:
i think a
Explanation:
The group that provides direction for the configuration of the new system in the existing computing environment are called _______.
Answers
The group that provides direction for the configuration of the new system in the existing computing environment are called technical stakeholders.
Technical stakeholders is the group that provides direction for the configuration of the new system in the existing computing environment.
Technical stakeholders include data and technical architects, staff members that work on process improvement, and DevOps teams that may need to give the sprint team advice or direction. The team is able to stay within the organization's environmental limits thanks to the technical comments.
Demos require widespread participation in order to effectively gather feedback and support. The team and a variety of pertinent stakeholders must be included. The interests of both the business and technical environments should be represented by stakeholders.
Learn more about internal stakeholders https://brainly.com/question/4414143
#SPJ4
Why should data be not taken from the internet directly?
Please solve it..!!
Answers
Answer:
Explanation:
some files and websites are out of controllable. because of the hackers
Data obtained from the internet should not always be taken at face value and used directly in important decision-making processes or analysis.
What is internet?The Internet (or internet) is a global network of interconnected computer networks that communicate using the Internet protocol suite (TCP/IP).
For several reasons, data obtained from the internet should not always be taken at face value and used directly in important decision-making processes or analysis.
Accuracy: Internet data accuracy cannot always be verified, and there is no guarantee that the information is correct.Reliability: The dependability of internet data is also debatable.Relevance: Internet data may or may not be relevant to your specific research or project needs.Legal and ethical concerns: Using data obtained from the internet may raise legal and ethical concerns, particularly regarding intellectual property rights, copyright, and privacy.Thus, data should not be taken from the internet directly.
For more details regarding internet, visit:
https://brainly.com/question/13308791
#SPJ2
Write a function called min that returns the minimum of the two numbers passed in as parameters.
Note: Be sure to include comments for all functions that you use or create.
For example, if you made a call like
x = min(10, 14)
x should have the value 10.
For your program, you need to define the function and call it and print out the result like this:
x = min(10, 14)
print("The min is " + str(x))
min(1,2);
min(9000,9001);
it is in python
Answers
def min(x,y):
smallest = x
if y < smallest:
smallest = y
return smallest
x = min(2,1)
print("The min is "+str(x))
Although I wouldn't recommend using the name min for a function because min is the name of an existing function. Best of luck.
The function is an illustration of conditional statements.
Conditional statements are statements whose execution depends on their truth values.
The function in Python, where comments are used to explain each line is as follows:
#This defines the function
def min(num1,num2):
#This initializes minVal
minVal = num2
#If num1 is less than num2, then
if num1 < num2:
#minVal equals num1
minVal = num1
#This returns the smaller value
return minVal
At the end of the program, the smaller value is returned to the main
Read more about similar programs at:
https://brainly.com/question/6973180
How many times will the while loop execute? *
a) 2
b) 3
c) 4
d) 5
Answers
The number of times a while loop will execute depends on the conditions specified in the loop.
Without the specific conditions, it is not possible to determine the exact number of iterations. However, I can provide a general explanation of how a while loop works and how the number of iterations can be controlled.
In a while loop, the loop continues executing as long as the given condition is true. The condition is checked before each iteration. If the condition evaluates to true, the loop body is executed, and then the condition is checked again. If the condition evaluates to false, the loop terminates, and the program moves on to the next statement.
To determine the number of times a while loop will execute, we need to consider the condition and the factors that can affect its evaluation. The condition can be based on a counter variable, user input, or some other condition that changes during the loop execution.
For example, if the condition is based on a counter variable and the loop body increments the counter by 1 in each iteration, the loop will execute a specific number of times until the condition becomes false. If the condition is initially true and the counter variable increases until it reaches a certain value, then the number of iterations will be equal to that value.
In the case of the given question, without additional information about the condition or the code inside the loop, it is not possible to determine the exact number of iterations. Therefore, it is not possible to select a specific option (a, b, c, or d) as the answer.
For more questions on loop
https://brainly.com/question/19706610
#SPJ11
Which option would a computer engineer most likely create? A) a programming language to run a new software program B.) the part of a computer that controls its function C.) the part of a software program that solves problems D.) an interconnected group of computers
Answers
Answer:
B
Explanation:
just did it
Computer engineer most likely create the part of a computer that controls its functions.
What have computer engineers Inventions?Computer engineers are known as people who create or build computers. Computer engineers have created a lot of super computers.
The computer engineer invented many things and it includes,
PC'swork-stationssupercomputersMonitorsWebsites and products used in the computers.Computer engineers invent many things inside and outside the computer. The parts are known to create or build computer-based systems that can be seen in cars, planes, appliances, electronics, phones, etc., and other computer based products.
So, A computer engineer most likely to create the part of a computer that controls its functions.
Hence, Option B is the correct answer.
Learn more about Computer engineers,
brainly.com/question/18954219
#SPJ2
T/F: A remote access link enables access to network resources using a wide area network (WAN) link to connect to the geographically distant network
Answers
True. A remote access link enables access to network resources using a wide area network (WAN) link to connect to the geographically distant network.
A remote access link is a connection that allows users or devices to access resources on a network from a remote location. This can be achieved using a WAN link, which is a telecommunication network that spans a large geographical area. WAN links are designed to connect distant networks, enabling the exchange of data and communication between them.
In a remote access scenario, a user at a remote location can connect to a network resource, such as a file server or an application server, through a WAN link. This connection is established using various protocols and technologies, such as Virtual Private Networks (VPNs) or secure shell (SSH), which ensure data security and privacy during transmission.
VPNs, for instance, create a secure, encrypted tunnel between the user's device and the remote network. This allows the user to access network resources as if they were directly connected to the local network, even though they are physically distant. Similarly, SSH provides a secure channel for remote access to a network resource, typically for system administration purposes.
In summary, a remote access link utilizes WAN links to enable users or devices to connect to geographically distant networks and access their resources securely and efficiently.
Know more about the Virtual Private Networks click here:
https://brainly.com/question/30463766
#SPJ11
What does a builder have to consider when preparing to build for a construction project?
Answers
Answer:
things to consider before you begin any construction project to ensure success:
- Below are some key factors to consider before you begin construction.
Choosing the right Architect to help with the Design.Make sure your project has the right amount of details. Have a realistic budget.Always do your own research. Selecting the right Builder.Explanation:
With respect to iot security, what term is used to describe the digital and physical vulnerabilities of the iot hardware and software environment?
a. Traffic Congestion
b. Device Manipulation
c. Attack Surface
d. Environmental Monitoring
Answers
Answer: Answer Surface
Explanation:
Question 7 (1 mark) In a computer information system control procedures that provide reasonable assurance that the recording, processing and reporting of data are properly performed for specific appli
Answers
Control procedures in a computer information system ensure proper recording, processing, and reporting of data for specific applications.
In a computer information system, control procedures play a vital role in maintaining the integrity, accuracy, and reliability of data. These procedures are designed to provide reasonable assurance that the recording, processing, and reporting of data are performed correctly and in accordance with predefined standards and objectives.
Control procedures encompass a range of measures implemented to minimize the risks associated with data manipulation and ensure the system operates effectively. They can include both preventive and detective controls. Preventive controls aim to prevent errors or irregularities from occurring in the first place, while detective controls focus on identifying and correcting errors or discrepancies that may have occurred.
Examples of control procedures include access controls, segregation of duties, data validation and verification, data backup and recovery mechanisms, error handling procedures, and audit trails. These procedures are typically documented and enforced through policies, protocols, and system configurations.
By implementing control procedures, organizations can reduce the risk of data inaccuracies, unauthorized access, and fraudulent activities. They provide a level of assurance that data is processed in a controlled and secure manner, ensuring the reliability of the information produced by the computer information system.
Learn more about control procedures
brainly.com/question/30623695
#SPJ11
the first step in implementing a systems solution is to: group of answer choices identify information requirements. evaluate alternative solutions. create detailed design specifications. perform a feasibility study. prepare training and documentation.
Answers
Detailed design specifications must be created as the initial stage in developing a systems solution.
What stage of a system's lifespan is it at at the moment?Preliminary analysis is the first stage of the systems development life cycle, which includes any alternative solutions that are suggested, the cost benefit analysis, and finally the submission of the preliminary plan for recommendations. This stage determines whether the concept is viable at the beginning of a project.
What constitutes the last stage of the systems implementation life cycle?Maintenance. Following the conclusion of the implementation phase is this last stage. A defined support mechanism is in place for the system during the maintenance phase.
To know more about implementing visit :-
https://brainly.com/question/13142009
#SPJ4
The most common HD format is 1080p, which uses a screen resolution of 1,920 Χ 1,080 and displays screen images one line at a time, called ____.
Answers
The most popular HD standard is 1080p, which employs a pixel density of 1,920 by 1,080 and uses progressive display to show screenshots one line at the time.
What does 1920x1080 mean on a screen?This screen has a display of 1920 x 1080 when compared to a Full HD 1080p monitor, which is the industry standard. This indicates that the screen's width will be 1,920 pixels, and its height will be 1,080 px. A total of 2,073,600 images are displayed as a result.
2560x1440 or 1920x1080: Which is better?With 2560 x 1440, you get more screen space and more vivid details than with 1920 x 1080. (just how much more depends on the screen size and pixel per inch ratio), However, it consumes more power when playing games.
To know more about screen resolution visit:
https://brainly.com/question/14810971
#SPJ4
assume that a vector named numbers has been declared of type integer. also assume that numbers.size() is equal to 10.we want to add the value 7 to the vector. how can an 11th element be added to the vector?
Answers
To add an 11th element to the vector, we can use the push_back() method in C++. This method adds an element to the end of the vector. In this case, we can add the value 7 to the vector by calling numbers.push_back(7). This will increase the size of the vector to 11 and add the value 7 as the last element.
To add an element to a vector in C++, we can use the push_back() method which adds an element to the end of the vector. In this scenario, an 11th element needs to be added to a vector named numbers of type integer with a size of 10. This can be achieved by calling numbers.push_back(7) which will increase the size of the vector to 11 and add the value 7 as the last element. The push_back() method is a convenient way to add elements to a vector without having to worry about manually resizing the vector or specifying the index of the new element. Overall, the push_back() method is a useful tool for manipulating the size and contents of a vector in C++.
In conclusion, to add an element to a vector in C++, we can use the push_back() method which adds an element to the end of the vector. In this case, to add the value 7 to the vector named numbers with a size of 10, we can call numbers.push_back(7) to increase the size of the vector to 11 and add the value 7 as the last element.
To know more about vector visit:
brainly.com/question/24256726
#SPJ11
The row's range of permissible values is known as its domain. True or False?
Answers
The given statement "The row's range of permissible values is known as its domain" is true because the permissible values called as domain.
In the context of mathematics and data analysis, a row is a horizontal sequence of values or observations in a table or matrix. The domain of a row refers to the range of permissible values that each element in the row can take. For example, consider a dataset that includes a row of measurements for the temperature of a particular location over the course of a year.
The domain of this row might be restricted to a certain range of values, such as -50 to 50 degrees Celsius, depending on the context of the data and the properties of the location being measured. The domain of a row can be specified by the researcher or analyst who is working with the data, or it may be determined by external factors such as physical constraints, measurement tools, or other contextual factors.
Learn more about domain: https://brainly.com/question/28934802
#SPJ11
Marvin is a very tall, very large man. Why might he dislike using a laptop keyboard? Question 1 options: The keys are laid out differently than on a computer keyboard. A laptop keyboard doesn't have function keys. The keys are generally smaller than on a computer keyboard. The keys are harder to press than on a computer keyboard
Answers
Answer:
The answer is 'the keys are generally smaller than on a computer keyboard'