________ contains much metadata that can be used to validate the format and completeness of the document, but includes considerable overhead.
Answers
XML (Extensible Markup Language) contains much metadata that can be used to validate the format and completeness of the document, but includes considerable overhead.
It is a popular data-interchange format that is highly versatile in its applications. The XML markup system is based on a set of rules for document encoding that allow designers to define custom elements for the document. The purpose of this markup system is to allow the content of a document to be read, edited, and analyzed easily.To achieve this purpose, the markup system incorporates much metadata that validates the format and completeness of the document.
This metadata can be used by applications to create indexes, query data, and automate document processing. However, this metadata is associated with considerable overhead that can impact the performance of some applications. The excess metadata may also result in larger file sizes, which can increase storage requirements.XML has proved popular in web design, e-commerce, and content management systems. The structured nature of XML files allows for consistent data exchange between different applications and systems.
Learn more about XML: https://brainly.com/question/22792206
#SPJ11
Related Questions
A bipartite graph is a graphG= (V, E)such that V can be partitioned into two sets (V=V1∪V2andV1∩V2=∅) such that there are no edges between vertices in the same set.
(a) Design and analyze an algorithm that determines whether an undirected graph is bipartite.
(b) Prove the following theorem: An undirected graph, G, is bipartite if and only if it contains no cycles of odd length.
Design and analyze means:
•Give pseudocode for your algorithm.
•Prove that your algorithm is correct.
•Give the running time for your algorithm.
Answers
(a)Algorithm to determine whether an undirected graph is bipartite:
Step 1: Create two empty sets V1 and V2
Step 2: Pick an unvisited vertex and add it to V1
Step 3: For all its unvisited neighbors, add them to V2
Step 4: For all their unvisited neighbors, add them to V1
Step 5: Continue this process until all vertices are visited
Step 6: Check if there is an edge between vertices in V1 or in V2.
If there is, the graph is not bipartite. Otherwise, it is bipartite.
The algorithm first picks an unvisited vertex and adds it to V1. Then it adds all its unvisited neighbors to V2 and all their unvisited neighbors to V1. This process is continued until all vertices are visited. Finally, it checks whether there is an edge between vertices in V1 or in V2. If there is, the graph is not bipartite. Otherwise, it is bipartite. The algorithm is correct because it is based on the definition of a bipartite graph. The running time of the algorithm is O(|V|+|E|), where |V| is the number of vertices and |E| is the number of edges. This is because we visit each vertex and edge at most once.
(b)Proof: Suppose G is a bipartite graph. Then, by definition, we can partition its vertices into two sets, V1 and V2, such that there are no edges between vertices in the same set. Now, suppose G contains a cycle of odd length. Let v be a vertex on this cycle. Without loss of generality, assume v is in V1. Then, its neighbors must be in V2, because there are no edges between vertices in the same set. But then, these neighbors must be connected to each other, because they are on a cycle. This contradicts the assumption that G is bipartite. Therefore, if G contains no cycles of odd length, it is bipartite.
To know more about undirected graph visit:
https://brainly.com/question/13198984
#SPJ11
for which situation would you use the switch function?
Answers
Answer:
Complete answer:
A switch is defined as a device that is used for making and breaking of electric current in a circuit. It is used to turn on and turn off daily used equipment like television, washing machine, fan, light, etc. A switch can be used in series and parallel circuits.
Explanation:
By recording all transactions across business network among participants. What aspect of blockchain creates the system of record?
Answers
By recording all transactions across the business network among participants. The aspect of blockchain that creates the system of record is its distributed ledger technology.
What Is Blockchain?
Blockchain is a decentralized digital ledger technology that allows multiple parties to securely and transparently record, store and verify transactions without the need for intermediaries, such as banks or other third-party institutions. In a blockchain network, transactions are grouped into blocks and then added to a chain of previous blocks, forming an immutable and transparent record of all transactions on the network.
Each block in a blockchain contains a cryptographic hash of the previous block, which creates a secure and tamper-proof link between all the blocks. This makes it virtually impossible to alter or manipulate any transactions on the network without detection, as any changes to a block would affect all subsequent blocks in the chain, causing the hash values to become invalid.
A distributed ledger is a database that is spread across a network of computers, where each computer on the network has a copy of the entire ledger. This means that every transaction that occurs on the network is recorded on multiple copies of the ledger, making it difficult to alter or tamper with the records.
In a blockchain network, transactions are grouped into blocks and then added to the chain of previous blocks, forming a chronological and immutable record of all transactions on the network. This decentralized and transparent system of record provides a high level of security, privacy, and reliability, and eliminates the need for intermediaries or central authorities to validate transactions.
Therefore, the combination of the distributed ledger, consensus mechanism, and cryptographic hash functions used to link each block together creates a transparent, secure, and auditable system of record for all transactions on the network.
To learn more about Blockchain click here
https://brainly.com/question/30088493
#SPJ4
Type the correct answer in each box. Spell all words correctly. Programmers utilize to convert a program from language, which is human readable, to language, which is a low-level language that the system can understand.
Answers
The completed sentences are:
Programmers utilize compilers to convert a program from high level language, which is human readable, to machine language, which is a low-level language that the system can understand.
When working with source codes written in high-level programming languages like Java or C++, software developers rely on specialized professional tools known as compilers.
The purpose of these programs is to translate the human comprehensible language of source codes into low-level binaries like machine code or bytecode that computers can understand better while producing an executable product.
Ultimately, compiling remains a vital step in creating functional applications by translating software's instructions expressing business logic via understandable texts into computer-readable instructions kept within binomial-code-based files.
Learn more about Compliers:
https://brainly.com/question/30780600
#SPJ1
Authentication is concerned with determining _______.
Answers
Authentication can be described as the process of determining whether someone or something is, in fact, who or what it says it is. Authentication technology serves us to access control for systems by checking to see if a user's credentials match the credentials in a database of authorized users or in a data authentication server.
There are three basic kind of authentication. The first is knowledge-based — something like a password or PIN code that only the identified user would know. The second is property-based, meaning the user possesses an access card, key, key fob or authorized device unique to them. The third is biologically based.
You can learn more about authentication at https://brainly.com/question/28398310
#SPJ4
What is shotgun microphone?
Answers
Answer:
A type of microphone characterized by an extremely directional polar pattern. Shotgun mics may be condenser or dynamic, but are almost always built with a long (8 to 24 inch) tube protruding from the front.
Explanation:
Shotgun mics are long, narrow tubes with slits evenly spaced along each side and a capsule near the rear end.
Saving space is not an ideal reason for cropping a photo to be used in technical communication. What is a better reason?.
Answers
Saving space is not an ideal reason for cropping a photo to be used in a technical document is a false statement and a better reason is that if you as a person is doing so, it helps you make your point.
What do you mean by technical document?Technical writing is any form of writing that explains the use, intent, design, or architecture of a good or service. Its objective is to describe a service that a company provides. Technical publications come in a variety of formats, each tailored to a certain audience.
Technical documentation is a catch-all word for the various types of data produced to explain the functionality, use, or architecture of a given good, system, or service.
The point you made mean effectively communicate an idea, as in I understand your point about skateboards being risky; your argument has been conveyed. In this phrase, "point" refers to "an important or crucial argument or suggestion.
Learn more about technical document from
https://brainly.com/question/7805567
#SPJ1
the university of kingston has hired you to install a private area network for its campus so that students and teachers from various departments can exchange data among themselves. which of the following network models would be best suited for such an institution?
Answers
The network models that would be best suited for such an institution is known as CAN.
How does a CAN network work?The CAN is known to be a kind of a peer-to-peer network. This is a term that connote that there is not any master that act to controls when the all the nodes have access to read as well as write data on the CAN bus.
Note that if a CAN node is said to be ready to transmit data, it looks to see if the bus is said to be busy and then it is one that often writes a CAN frame onto the network.
Note that network model is seen as a kind of database model that is set up as a flexible method to showing objects and their relationships
Therefore, The network models that would be best suited for such an institution is known as CAN.
Learn more about network models from
https://brainly.com/question/23369075
#SPJ1
what class access modifier should you utilize to limit access to the assembly (a group of code modules compiled together) to which the class belongs? group of answer choices private
Answers
When creating a class, the `private` class access modifier can be used to limit access to the assembly (a group of code modules compiled together) to which the class belongs.
What is an assembly in programming?An assembly is a collection of types and resources that are designed to work together and form a logical unit of functionality in .NET.
An assembly is created when the compilation process is finished, and it contains code that is translated into machine-readable instructions that are ready to be executed by the computer. The assembly is self-contained, which means that it contains everything it needs to execute, including metadata that describes the types defined within the assembly.
There are four access modifiers in C#: `public`, `private`, `protected`, and `internal`. These access modifiers are used to define the accessibility of the classes, methods, and other members of the program's source code. The `private` access modifier is used to limit access to the class only within the same class in which it is defined.
Private class access modifierIn C#, the `private` class access modifier is used to limit the access to the members and types of the class only within the same class.
This means that the class can only be accessed by the methods that belong to that class. No other code outside the class can access it, including code in other classes in the same assembly.
The `private` access modifier is used to ensure that sensitive data or functionality of the class is not accidentally accessed by other code in the same assembly.
It's essential to consider the security and functionality of your code when deciding on the class access modifier to use, and it's also important to be consistent in the use of the access modifiers throughout your program.
Learn more about assembly in programming at
https://brainly.com/question/14728681
#SPJ11
Sebastian is working on a web page that includes both essential and non-essential information about an event that is happening at his shop. How
Answers
Sebastian can organize the essential and non-essential information about the event on his webpage in the following steps:
1. Identify the essential information: Determine the key details that visitors to the webpage need to know about the event. This may include the date, time, location, and purpose of the event.
2. Highlight the essential information: Make sure that the essential information stands out on the webpage. Use headings, bullet points, or bold text to draw attention to these important details.
3. Provide additional details: Include non-essential information about the event that may be of interest to visitors but is not crucial for understanding the event. This could include background information, special features, or testimonials.
4. Use clear formatting: Arrange the essential and non-essential information in a logical and easy-to-read manner. Consider using sections or tabs to separate the different types of information, making it clear what is essential and what is non-essential.
5. Prioritize the essential information: Place the essential information prominently on the webpage so that it is easily noticeable. This ensures that visitors can quickly find the most important details without having to search through the entire page.
In summary, Sebastian can organize the essential and non-essential information about the event on his webpage by identifying the key details, highlighting them, providing additional non-essential details, using clear formatting, and prioritizing the essential information.
#SPJ11
Learn more about Information
https://brainly.com/question/26260220
Sebastian can organize the web page by distinguishing between essential and non-essential information about the event happening at his shop. Here's how he can do it:
1. Identify essential information: Sebastian should determine the key details that visitors must know about the event, such as the date, time, location, and any important announcements or updates.
2. Prioritize essential information: Once he has identified the essential information, Sebastian should place it prominently on the web page, ensuring that it is easily visible and accessible to visitors. This could include using headings, subheadings, bullet points, or highlighting key details.
3. Separate non-essential information: Sebastian should then identify any additional details or supplementary information that is not essential for visitors to know. This could include things like event background, history, or optional activities.
4. Organize non-essential information: Sebastian can create separate sections or tabs on the web page to present the non-essential information. This way, visitors who are interested in learning more can easily access it, while those who are looking for essential details can find them without being overwhelmed.
5. Use clear and concise language: Regardless of whether it's essential or non-essential information, Sebastian should ensure that all text on the web page is written in a clear, concise, and easy-to-understand manner. This will help visitors quickly grasp the important details and navigate through the web page effectively.
By following these steps, Sebastian can create a well-organized web page that presents both essential and non-essential information about the event happening at his shop.
#SPJ11
Learn more about Web page here:
brainly.com/question/32613341
After removing the printed paper from your laser printer, the toner smudges and can be wiped off in places.Which of the following is the MOST likely problem?Fuser rollersPrimary coronaPrint drum
Answers
The MOST likely problem in this case would be the fuser rollers. The fuser rollers in a laser printer are responsible for applying heat and pressure to fuse the toner onto the paper.
If the toner smudges and can be wiped off in places after removing the printed paper, it suggests that the fuser rollers are not functioning properly. Possible causes could be worn-out or damaged fuser rollers, improper temperature settings, or inadequate pressure being applied. As a result, the toner fails to adhere effectively to the paper, leading to smudging and easy removal. To resolve this issue, the fuser rollers may need to be inspected, cleaned, or replaced to ensure proper fusion of the toner onto the paper.
Learn more about printer here:
https://brainly.com/question/5039703
#SPJ11
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
What will be the results from running the following code?
print("Grades")
print(92)
print(80)
print("Total")
print(92 + 80)
Answers
Answer:
Grades
92
80
Total
172
Explanation:
Python is a very simple language, and has a very straightforward syntax. It encourages programmers to program without boilerplate (prepared) code. The simplest directive in Python is the "print" directive - it simply prints out a line (and also includes a newline, unlike in C).
Answer:
Grades
92
80
Total
172
Explanation:
why is it necessary to consider the client safety and comfort
Answers
Essentially, you have to focus on customer comfort in order to ensure your customer can concentrate on your business only, without distractions or concerns over their physical well-being
Find true or false. A hacker is hacking software with access in sensitive information from your computer
Answers
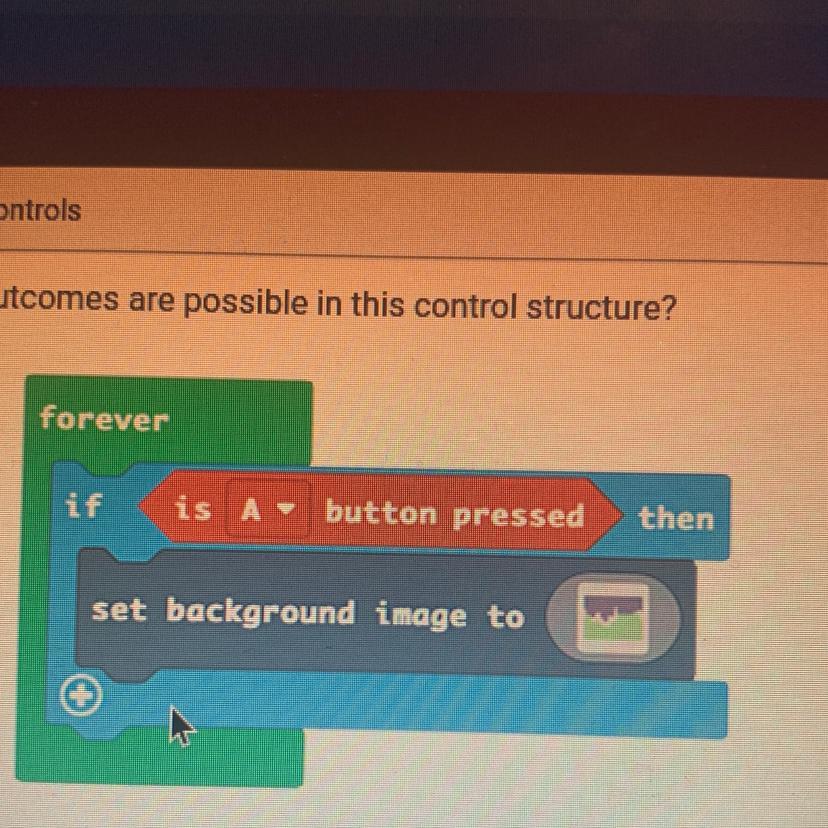
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
Why should we not underestimate the widespread of mass media?
Select one:
a.
While we do not seem to be aware of it, media has always been a useful and influential part of our lives.
b.
Media's span of influence knows no bounds
c.
All of the given choices are correct
d.
The media could reach almost anywhere in the world
Answers
We should not underestimate the widespread of mass media because C. All of the given choices are correct.
It should be noted that media has always been a useful and influential part of our lives and its span of influence knows no bounds.
Also, it's important for one not to underestimate mass media because media could reach almost anywhere in the world. Therefore, all the options are correct.
Read related link on:
https://brainly.com/question/23270499
How many grenades are thrown in CoD games over 5 years?
175 million
300 billion
579 billion
Answers
When a program is being implemented, which step comes after executing
a) linking
b) compiling
c) maintaining
d)interpreting
Answers
Answer:
c) maintaining
Explanation:
A software development life cycle (SDLC) can be defined as a strategic process or methodology that defines the key steps or stages for creating and implementing high quality software applications. There are seven (7) main stages in the creation of a software and these are;
1. Planning.
2. Analysis.
3. Design.
4. Development (coding).
5. Testing.
6. Implementation and execution.
7. Maintenance.
Hence, when a program is being implemented, the step which comes after executing is maintaining. This is ultimately the last stage of the software development process and it involves regular updates and other management tasks.
Providing products or services that could be raffled off by a non-profit organization to raise money is an example of a business _____.
Answers
Once the location is acquired (ip address 88. 151. 243. 8) what does your computer do with that information?.
Answers
When you search for the IP address, it will take you to the requested webpage.
An IP address is a one-of-a-kind identifier for a device on the internet or a local network. IP is an abbreviation for "Internet Protocol," which is a collection of rules that governs the format of data transferred over the internet or a local network.
IP addresses, in essence, are the identifiers that allow information to be exchanged between network devices: they contain location information and make equipment available for connection. The internet requires a method to distinguish between various computers, routers, and webpages. IP addresses enable this and are a critical component of how the internet operates.
An IP address is a numeric string separated by periods. IP addresses are represented as a string of four digits, such as 192.158.1.38. Each integer in the set can have a value ranging from 0 to 255. As a result, the whole IP addressing range is 0.0.0.0 to 255.255.255.255.
Learn more about IP Address here https://brainly.com/question/29345454
#SPJ4
A browser ___ is a separate program that adds a variety of useful features to the web browser, such as sending instant messages or playing mobile-style games.
Answers
Answer:
The correct option is;
Extension
Explanation:
A browser extensions are available small applications plug-ins that allow the modification of the web browser by customizing and changing how information flows through the browser. Browser capabilities include the hosting of varying forms of browser extensions, and settings for ad blocking. Web experiences are vastly enhanced by browser extensions by providing personalized experience.
Select the correct answer from each drop-down menu.
Identify the technology from the given description.
___ are small independent computers that are capable of ___
display, sensing, and wireless communication.
1.
A. Haptics
B. Siftables
C. White boards
2.
A. Graphics
B. Audio
C. Visuals
Please i need this ugently! 15 points! Please dont answer if you dont know it.
Answers
Answer:
Siftable are small independent computer that are capable of BLANK (graphics audio video)
Answer:
I think its Siftables and Graphics
Explanation:
this network layer device uses one or more routing metrics to determine the optimal path along which network traffic is forwarded. true or false
Answers
Network layer devices, such as routers, utilize one or more routing metrics to determine the optimal path for forwarding network traffic.
These metrics help determine the most efficient and reliable route for data transmission. Routing metrics are criteria or values used by routers to make decisions about the best path to direct data packets. They can include factors like hop count, bandwidth, delay, reliability, and cost. By evaluating these metrics, routers can select the most suitable path for forwarding network traffic, considering factors such as speed, reliability, and congestion.
Learn more about routing metrics here:
https://brainly.com/question/32138053
#SPJ11
What are 3 examples of Chassis Wiring?
Answers
Answer:
.
Explanation:
Unethical behavior in a media house can be reduced if management does all of the following except.
Answers
Unethical behavior in a media house can be minimized if management does all of the following except A: "depends totally on workers' personal ethics".
Unethical behavior can be described as actions that are against social norms and values or acts that are considered unacceptable to people. In the context of the given scenario where management wants to reduce unethical behavior in the media house, to obtain the purpose they can take the following steps:
Punish unethical behavior stronglyLimit the opportunities for unethical behaviorIntroduce clear policies on unethical behavior"
Complete question:
Unethical behavior in a media house can be reduced if management does all of the following except.
depends totally on employees' personal ethics.
Punish unethical behavior firmly
Limit opportunities for Unethical behavior
establish clear policies on unethical behavior
"
You can learn more about Unethical behavior at
https://brainly.com/question/2258356
#SPJ4
EASY POINTS what favorate food
so easy
Answers
Answer:
ramen
Explanation:
Answer:
Pizza and RAMEN
Explanation:
Python
Use a series if and elif statements to check one of the variables

Answers
Step by step soluton:
print("Enter percentage =")
percentage =input()
if percentage < 49:
print("F")
elif percentage >49.5 && percentage <59 :
print("C-")
elif percentage > 59.5 && percentage <66:
print("C")
elif percentage > 66.5 && percentage <72:
print("C+")
elif percentage > 72.5 && percentage <85:
print("B")
elif percentage > 85.5:
print("A")
How to use if, elif, else in python ?
The script's statements are typically carried out in order from first to last by default. The sequential flow can be changed in one of two ways if the processing logic calls for it:
Python's if keyword is used to implement decision-making. The following is the syntax for conditionally running a block in Python:
Syntax for using IF:
if [boolean expression]:
statement1
statement2
...
statementN
If the boolean expression in the if condition evaluates to False, an alternative block of instructions to be executed can be specified in addition to the if statement using the otherwise condition.
Syntax for using ELSE :
if [boolean expression]:
statement1
statement2
...
statementN
else:
statement1
statement2
...
statementN
When adding additional conditional expressions after the if or in between the if and else conditions, use the elif condition.
Syntax for using ELIF:
if [boolean expression]:
[statements]
elif [boolean expresion]:
[statements]
elif [boolean expresion]:
[statements]
else:
[statements]
Hence, if, else, elif are also sequential control statements.
You can learn more about if elif in python from given link:
https://brainly.com/question/866175
#SPJ13
why has base 2 been accepted and used as the basis for computing?
Answers
Answer:
Binary numbers which are essentially in base 2 has been accepted and used as the basis for computing because they consist of 0s and 1s, which are the only language the computer recognizes and understands.
Explanation:
In Computer science, a bit is a short word for the term binary digit and is primarily the basic (smallest) unit measurement of data or information.
A bit is a logical state which represents a single binary value of either one (1) or zero (0). This ultimately implies that, a single bit in computer science represents a boolean value of;
1. True or ON, which is equal to one (1).
2. False or OFF, which is equal to zero (0).
Machine and assembly are referred to as a low level programming language used in writing software programs or applications with respect to computer hardware and architecture. Machine language is generally written in 0s and 1s, and as such are cryptic in nature, making them unreadable by humans but understandable to computers.
On the other hand, assembly language use commands written in English such as SUB, MOV, ADD, etc.
A binary numbering system represents all numeric values that are to be written in sequences of ones (1s) and zeroes (0s).
Binary numbers which are essentially in base 2 has been accepted and used as the basis for computing because they consist of 0s and 1s, which are the only language the computer recognizes and understands.
PLS HURRY!!
Look at the image below

Answers
Answer:
1. A function can use variables as parameters.
2. A function can have more than one parameter.
3. The definition of a function must come before where the function is used.
Explanation:
The definition of a function can come before or after it is used - I am pretty sure it cannot be placed after the function is being used. It should always come before it is used, so this statement is false.
A function can use variables as parameters - this is true, variables are just labels to hold data.
A function can have more than one parameter - this is true.
A function must have a return value - functions do not always have to return values. It could simply print, so this statement is false.
The definition of a function must come before where the function is used - As said earlier, the definition of functions must come before it is used/called. This statement is true.
Hope this helps :)