Consider the following preferences where men are proposing and women are rejecting; to depict this, we write a column for each woman, with the list of proposals received underneath. Find a stable matching. Ann Beth Cher Dot Ann Beth Cher Dot Al 1 1 3 2 Al 3 4 1 2 Bob 2 2 1 3 Bob 2 3 4 1 Cal 3 3 2 1 Cal 1 2 3 4 Dan 4 4 4 4 Dan 3 4 2 1 Women's Preferences Men's Preferences
Answers
In the given scenario of men proposing and women rejecting, a stable matching needs to be found based on the preferences of both men and women. The table provided shows the preferences of women (Ann, Beth, Cher, and Dot) for each man (Al, Bob, Cal, and Dan) and the proposals they received.
To find a stable matching, we need to consider the preferences of both men and women. In this case, the goal is to ensure that there are no unstable pairs where a man and a woman prefer each other over their current partners.
To determine a stable matching, we can apply the Gale-Shapley algorithm. The algorithm works by having each man propose to his most preferred woman, and women compare the proposals they receive. If a woman receives a proposal from a man she prefers over her current partner, she accepts the proposal and rejects the previous partner.
In this particular scenario, the stable matching can be found as follows:
- Ann receives proposals from Al (1st choice), Bob (2nd choice), Cal (3rd choice), and Dan (4th choice). She accepts Al's proposal and rejects the rest.
- Beth receives proposals from Al (1st choice), Bob (2nd choice), Cal (3rd choice), and Dan (4th choice). She accepts Bob's proposal and rejects the rest.
- Cher receives proposals from Al (3rd choice), Bob (4th choice), Cal (1st choice), and Dan (2nd choice). She accepts Cal's proposal and rejects the rest.
- Dot receives proposals from Al (2nd choice), Bob (1st choice), Cal (4th choice), and Dan (3rd choice). She accepts Bob's proposal and rejects the rest.
After this process, the resulting stable matching is:
Al - Ann
Bob - Dot
Cal - Cher
Dan - None (unmatched)
This matching is stable because there are no pairs where a man and a woman prefer each other over their current partners. In this case, Dan remains unmatched as there is no woman who prefers him over her current partner.
It's important to note that the stable matching algorithm ensures that the resulting matches are stable, meaning there are no incentives for any man or woman to break their current match in favor of another person they prefer.
To learn more about Algorithm - brainly.com/question/21172316
#SPJ11
Related Questions
3 things in terms of photography to learn about.
Answers
The three important principle in photography are;
Photography is about light. Without it, you couldn't even take images, let alone excellent ones.
The quality of light varies from one to photograph, yet it is always what gives your photographs their underlying structure. It doesn't get any more basic than that.
Most of us snap photos because something catches our attention.
Unsurprisingly, that "something" is your subject.
If you're explaining a photograph to someone else, the topic is most likely the first thing you'll mention.
Finally, the composition is the third and most important aspect of every shot.
Simply said, composition is the arrangement of the things in your shot. It includes your camera position, the connections between photo elements, and the things you accentuate, deemphasize, or altogether eliminate. Composition is the method through which you communicate your tale.
Learn more about photography:
https://brainly.com/question/30685203
#SPJ1
li, a helpdesk technician, is troubleshooting a system. based on experience, li has narrowed down the problem and believes it is related to either the motherboard, processor, or ram. which symptoms would have allowed li to narrow down the problem? select three.
Answers
Based on experience, Li has narrowed down the problem and believes it is related to either the motherboard, processor, or RAM. The symptoms that would have allowed Li to narrow down the problem are as follows:
No image on the screenBeep codesComputer keeps rebootingNo image on the screen: A problem with the motherboard may cause the system to turn on, but there is no image on the screen. This could be due to a faulty or unseated graphics card or other issues, such as a dead monitor, but Li has likely checked those items.Beep codes: When the motherboard or RAM malfunctions, the system will emit beep codes. Li would have listened for any beep codes to diagnose the issue, and this could have narrowed down the issue to the motherboard or RAM.Computer keeps rebooting: When the processor has issues, the computer will restart or crash frequently. This symptom could have been a sign that the problem is related to the processor.Learn more about malfunctions here https://brainly.com/question/28249099
#SPJ11
How many screws secured the side panels
Answers
The answer to this question may significantly vary but normally there are two screws for each on each side of the panel on a mid-tower case.
What is the function of Screws?The function of screws is to tighten the parts which are arranged in a complex arrangement. A Screw is a type of simple machine which visualize like an inclined plane that wounded around a complex arrangement with a pointed tip.
According to this question, very frequently there are two screws that can be secured to the side panels but there can be anywhere from one to six screws for the case is also seen in some kinds of systematic arrangements.
Therefore, the answer to this question may significantly vary but normally there are two screws for each on each side of the panel on a mid-tower case.
To learn more about Screws, refer to the link:
https://brainly.com/question/9620666
#SPJ1
Explain what Tom should do in the following scenario, and why.
Situation: Tom is writing a program that will be used to store car descriptions for all cars in the dealership. He already has code for a public class name CarDetails.
Answers
Answer:
Tom should most definitely continue writing his program, and its good that he has a code for a public class name. Tom should keep going with the project and see what others think, if they approve then its truly ready. Because In order to write the rest of his program that he wants, he needs to continue what he's doing.
Explanation:
Which of the following is a notation that uses a name in angle brackets to annotate a piece of Web page information?A. HTMLB. tagC. attributeD. markup languageE. hypertext
Answers
The notation that uses a name in angle brackets to annotate a piece of Web page information is called an HTML tag. So option b is the correct one.
HTML, or Hypertext Markup Language, is the markup language used to create web pages and includes a set of tags that define how the content of a web page should be displayed. Tags can be used to define headings, paragraphs, lists, links, images, and many other elements. Attributes can also be added to tags to provide additional information, such as the source URL of an image or the target of a link. Overall, HTML is the backbone of the World Wide Web, providing the structure and formatting necessary for web pages to be displayed and accessed by users.
To know more about Hypertext Markup Language visit:
https://brainly.com/question/5560016
#SPJ11
How can your web page design communicate your personal style
Answers
Answer:
Web design is very unique, you can express your feelings through creating a page.
Someone help pleaseee
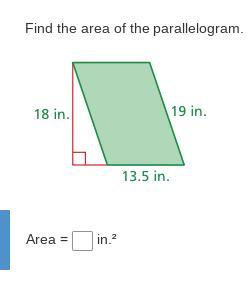
Answers
Answer:
243in^2
Explanation:
Area= base x height
base=13.5
height=18
A= 13.5 x 18
A=243in^2
hope this helps :)
In an array-based implementation of the Stack ADT, spreading the cost of the push operation when the stack is full yields a performance of O(n). True or false?
Answers
False. Spreading the cost of the push operation when the stack is full does not always result in a performance of O in an array-based implementation of the Stack ADT (n).
A popular method for implementing data structures including lists, stacks, queues, and heaps is array-based implementation. The data structure's elements are stored in an array, and operations are carried out by accessing the elements by their indices. The size of the data structure is constrained in an array-based solution since the size of the array is normally set and chosen at construction. Moreover, expanding an array can be a costly procedure. However, array-based implementation provides the benefit of constant-time access to elements, making it appropriate for applications that need frequent access to elements, such as in signal processing and numerical computing.
Learn more about array-based implementation here:
https://brainly.com/question/17017454
#SPJ4
what happens when an object's reference count is zero?group of answer choicesthe object is no longer referenced.the object is ready for memory allocation.the object is being referenced.the object will be deallocated from memory immediately.
Answers
When an object's reference count is zero, it means the object is no longer referenced and the object will be deallocated from memory, making it ready for memory allocation for other purposes.
When an object's reference count is zero, it means that there are no more references to it in the program. This is an indication that the object is no longer needed and can be removed from memory.
The object will be deallocated from memory immediately. This process is known as garbage collection, where the system automatically detects and removes objects that are no longer needed in the program. So, the correct answer would be: "The object will be deallocated from memory immediately."Thus, when an object's reference count is zero, it means the object is no longer referenced and the object will be deallocated from memory, making it ready for memory allocation for other purposes.Know more about the garbage collection,
https://brainly.com/question/30457823
#SPJ11
5 Van en sentido vertical
Answers
Answer: 5
Explanation:
The code segment int *ptr; has the same meaning asa int ptr;b int ptr*;c *int ptr;d int* ptr;e None of the above
Answers
The code segment "int *ptr;" and "int ptr*;" both have the same meaning, which is declaring a pointer variable named "ptr" that points to an integer data type.
However, "int ptr;" declares a regular integer variable named "ptr", not a pointer variable. The difference lies in the placement of the asterisk (*) symbol, which indicates that the variable is a pointer. " *int ptr" is also a valid declaration but it is not commonly used because it can be confusing. "int* ptr" is another valid declaration, where the asterisk is placed next to the data type instead of the variable name, indicating that the variable is a pointer to an integer. Therefore, the correct answer is "a int ptr; and b int ptr*;".
learn more about code segment here:
https://brainly.com/question/30614706
#SPJ11
Where in the dashboard would you primarily view and engage with your audience and the social media content published by others?.
Answers
Answer is Tabs and Streams.
The Dashboard Would You Primarily View And Engage With Your Audience And The Social Media Content Published By Others is tabs and streams.
You can learn more about at :
brainly.com/question/28926771#SPJ4
You are the administrator for the ABC Company. You are looking to install Windows Server 2016, and you need to decide which version to install. You need to install a version of Windows that is just for logon authentication and nothing else. You want the most secure option and cost is not an issue. What should you install
Answers
Signs and symbols can be used to communicate.
True
False
Answers
Answer:
True
Explanation:
There are two major categories of signals people send: signs and symbols. Signs are the foundation of all communication
Hi there! I need a bit of help on my computer's assignment. Question is below!
\(\underline{\large\text{Question}}\)
Selena would like go back to a page that she visited recently. She should use the _____.
A) links in the display window
B) scroll bar to scroll up through the pages
C) back button in the navigation bar
D) click on the back button in the display window
\(\underline{\large\text{Exceptions:}}\)
The answer must:
- Be correct.
- Be well explained
The answer must not include:
- Spams
- Incorrect answers
- Incomplete explanation
Good luck :)
Answers
Answer:
The back button of the navigation bar
Explanation:
The back and forward buttons are standard on the many web browsers. The navigation bar is the same place where you type your URLs. In this case, Selena would use the back button to go back to an active window she had previously visited. It helps you move backward in the same order you previously made your visits.
The view that perceptual processes take place over time and can be thought of in terms of a software/hardware metaphor is known as the ______.
Answers
The view that perpetual processes can be thought of in terms of a software/hardware metaphor is known as the: information processing view.
What is the Information Processing View?Information processing view is explained by the cognitive theory to explain how the brain encodes information and how information are filtered from what we pay attention to in a particular moment. This also determines what is stored in the short-term or in our long-term memory.
Therefore, the view that perpetual processes can be thought of in terms of a software/hardware metaphor is known as the: information processing view.
Learn more about the information processing view on:
https://brainly.com/question/24863946
What are some limitations when it comes to testing and ensuring program quality? List at
least two limitations; you may refer to specific kinds of testing in your answer.
Answers
Answer:
the two limitation i can think about is the efficiency like if there are bugs or glitches or if it can get broken into and the second one is if it is running the correct program or not a lot of people deal with this problem.
Explanation: personally these are the two i can come up with at the moment
The two limitations that come arrive in the process of testing and ensuring program quality are as follows:
The errors and kinds of glitches in modern technology seem like distractions in usual life. The overdependency on these resources may harmful to a larger extent. What is Program quality?Program quality may be defined as the fundamental properties of the program's source code and executable code, including reliability, robustness, usability, portability, maintainability, efficiency, and readability.
According to the context of this question, there are various limitations in each and every field of development whether it is science or technology. Similarly, there are a lot of drawbacks in testing and ensuring program quality. You have to manage each and everything in a systematic way in order to ensure the testing of program quality.
To learn more about Program quality, refer to the link:
https://brainly.com/question/13381607
#SPJ2
you are troubleshooting a windows pc that will not load the operating system. you insert the windows cd and reboot. which utility can you use to repair windows?
Answers
IF we are attempting to fix a Windows computer that won't load the operating system. We restart after inserting the Windows CD. Recovery Environment is the program you can use to repair Windows.
What is operating system ?The most crucial piece of software that runs on a computer is the operating system. It controls the memory, operations, software, and hardware of the computer. You can converse with the computer using this method even if you don't understand its language. A computer cannot function without an operating system. Any computer you buy often comes pre-loaded with an operating system. The default operating system that comes with computers is used by the majority of users, however it is possible to update or even switch operating systems. Microsoft Windows, macOS, and Linux are the three most popular operating systems for personal computers. A graphical user interface, or GUI, is used by contemporary operating systems (pronounced gooey).
To know more about operating system, visit
https://brainly.com/question/22811693
#SPJ4
Which computer is the fastest to process complex data?
Answers
Answer:
Supercomputers for sure.
which one of the following is not hardware
Answers
Answer:
There r no options
Explanation:
I think the application r not the hardware.
what is the size of each memory locaiton for arm processor based systems? (each memory location has a unique address).
Answers
The size of each memory location for ARM processor-based systems is usually determined by the width of the data bus and the size of the address bus. ARM processors usually support different memory architectures, each with a different memory map.
ARM processors have different memory access types, including byte, halfword, and word, which correspond to 8, 16, and 32 bits of data, respectively. A single memory location has a unique address, which is used to access and store data in the memory. For example, if an ARM processor has a 32-bit data bus and a 32-bit address bus, each memory location would be 32 bits or 4 bytes in size.
To sum up, the size of each memory location for ARM processor-based systems is determined by the width of the data bus and the size of the address bus. Each memory location has a unique address that is used to access and store data in the memory. The size of a memory location is usually measured in bytes and can vary depending on the specific ARM processor and memory architecture used.
You can learn more about memory at: brainly.com/question/14829385
#SPJ11
Which of the following is the correct way to code a try statement that displays the type and message of the exception that’s caught?
A. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception as e:
print(e(type), e(message))
B. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception as e:
print(type(e), e)
C. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception:
print(Exception(type), Exception(message))
D. try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception:
print(type(Exception), Exception)"
Answers
The correct way to code a try statement that displays the type and message of the exception that's caught is option B:
In this option, the except block catches any exception that occurs within the try block. The exception object is assigned to the variable e using the as keyword.
To display the type of the exception, type(e) is used, which returns the class/type of the exception object. To display the message associated with the exception, e is directly printed, which will output the message contained within the exception object.
Therefore, option B is the correct way to code the try statement for displaying the type and message of the caught exception.
try:
number = int(input("Enter a number: "))
print("Your number is: ", number)
except Exception as e:
print(type(e), e)
To know more about exception object, visit:
https://brainly.com/question/32880399
#SPJ11
barking up the wrong tree? reconsidering policy compliance as a dependent variable within behavioral cybersecurity research
Answers
In this commentary, we examine the limitations of using cybersecurity policy compliance as a dependent variable by presenting three assertions.
What is cybersecurity?-Cybersecurity is the practice of protecting critical systems and sensitive information from digital attacks. Also known as information technology (IT) security, cybersecurity measures are designed to combat threats against networked systems and applications, whether those threats originate from inside or outside of an organization.In 2020, the average cost of a data breach was USD 3.86 million globally, and USD 8.64 million in the United States.
-These costs include the expenses of discovering and responding to the breach, the cost of downtime and lost revenue, and the long-term reputational damage to a business and its brand. Cybercriminals target customers’ personally identifiable information (PII) — names, addresses, national identification numbers (e.g., Social Security number in the US, fiscal codes in Italy), and credit card information — and then sell these records in underground digital marketplaces. Compromised PII often leads to a loss of customer trust, the imposition of regulatory fines, and even legal action.
To know more about cyber security visit:-
https://brainly.com/question/24856293
#SPJ1
A music producer is recording a soundtrack for a new television wildlife programme that is being produced in collaboration with the OU. The music producer wishes to use a sampling rate of 96 kHz with each sample being 3 bytes of data. The recording is being made on a single (mono) channel. i. How many bits are there in each sample? ii. How many bits per second are processed while the music is being recorded? Express your answer in scientific notation to 3 significant figures. iii. One piece of music is 5 minutes 10 seconds long, how many bits are processed in total? Express your answer in scientific notation to 3 significant figures. iv. If the sampling rate is reduced to 24 kHz how many bits will be processed using the same piece of music? Express your answer in scientific notation to 3 significant figures. v. What is the percentage decrease in the number of bits processed as a result of reducing the sampling rate from 96 kHz to 24 kHz. Express your answer to 2 decimal places.
Answers
i. Each sample consists of 24 bits of data.ii. The processing rate while recording is 2.304 x 10^6 bits/s.iii. The total number of bits processed for a 5 minutes 10 seconds music piece is 7.1344 x 10^8 bits.iv. If the sampling rate is reduced to 24 kHz, the number of bits processed is 5.76 x 10^5 bits.v. The percentage decrease in the number of bits processed is 75%.
i. Each sample consists of 3 bytes of data, and since 1 byte is equal to 8 bits, there are 3 * 8 = 24 bits in each sample.
ii. The sampling rate is 96 kHz, which means 96,000 samples are processed per second. Since each sample is 24 bits, the number of bits processed per second is 96,000 * 24 = 2,304,000 bits/s.
iii. The duration of the music is 5 minutes 10 seconds, which is equivalent to 310 seconds. Since there are 2,304,000 bits processed per second, the total number of bits processed is 2,304,000 * 310 = 713,440,000 bits.
iv. If the sampling rate is reduced to 24 kHz, the number of samples processed per second becomes 24,000. With each sample still being 24 bits, the number of bits processed per second is 24,000 * 24 = 576,000 bits/s.
v. The percentage decrease in the number of bits processed is given by ((original bits - new bits) / original bits) * 100. Substituting the values, ((2,304,000 - 576,000) / 2,304,000) * 100 = 75%.
To know more about original bits visit :
https://brainly.com/question/33445462
#SPJ11
What security feature on a smartphone prevents the device from being used until a passcode is entered?
Answers
Answer:
Lock Screen
Explanation:
what are the methods used in research methodology?
Answers
Surveys. ...
Questionnaires. ...
Interviews. ...
Case studies. ...
Participant and non-participant observation. ...
Observational trials. ...
Studies using the Delphi method.
Give three examples of the following types of data?
Give three examples for each category in the software domain ?
CCDI :)??


Answers
An example of transactional data are:
Sales ordersPurchase ordersShipping documentsIts software domain are: Personal meeting, a telephone call, and a Video call
An example of financial data are: assets, liabilities, and equity. The software are: CORE Banking, Retail Banking, and Private banking
An example of intellectual property data are: books, music, inventions. The software domain are Patents, trademarks, and copyrights
What types of software are used in the financial industry?Through sales and marketing tools, data-driven contact management, and workflow automation, customer relationship management (CRM) software assists financial services organizations in fostering new relationships and maximizing the value of existing customers.
You can see how your consumers are utilizing your website to complete a transaction by using transaction management software. It may demonstrate both how each website element functions on its own and as a part of the overall technological infrastructure.
Note that Information that is gathered from transactions is referred to as transactional data. It keeps track of the date and location of the transaction, the time it took place, the price ranges of the goods purchased, the mode of payment used, any discounts applied, and other quantities and characteristics related to the transaction.
Learn more about transactional data from
https://brainly.com/question/28081430
#SPJ1
identify the areas in which preventative exercise programs are commonly found. (more than one option may be correct.)
Answers
Common areas where preventative exercise programs can be found include workplaces, schools, gyms, sports teams, and healthcare facilities.
What are some common areas where preventative exercise programs can be found?The paragraph is referring to identifying the areas in which preventative exercise programs are commonly found.
These programs aim to prevent injuries and promote overall health and wellness through regular physical activity.
Some common areas where such programs can be found include workplaces, schools, gyms, sports teams, and healthcare facilities.
Workplace wellness programs often include preventative exercise programs to promote employee health and reduce healthcare costs.
Schools may offer exercise programs as part of physical education classes or after-school activities.
Gyms and sports teams may provide training programs for injury prevention and performance enhancement.
Healthcare facilities may offer exercise programs as part of physical therapy or rehabilitation services.
Learn more about preventative exercise
brainly.com/question/27524234
#SPJ11
Comments should
give the reader the background of the programmer.
be written for every line of code.
communicate the purpose of the code that follows it.
give information about how many hours it took to write the code.
Answers
Answer:
Correct answer is:
communicate the purpose of the code that follows it.
Explanation:
Let have a look at each option
comment should give the reader the background of the programmer.
Comments are unable to do so.
Be written on every line
No, it is not need as comment are useful only to explain difficult or complex part of code.
communicate the purpose of the code that follows it.
yes, this option is true, as comments will give hints to programmer about the piece of code.
give information about how many hours it took to write the code
No, comments can answer it,
Answer:
c.
Explanation:
Directions: write necessary work instructions to your employees by using the different criteria in testing electronic components.
Answers
To ensure proper testing of electronic components, follow these instructions using criteria liketi visual inspecon, electrical testing, and performance evaluation.
Now, let's dive into the step-by-step process:
1. Visual Inspection: Start by examining the components for any physical damage, deformations, or signs of overheating. Check the integrity of solder connections and verify that all parts are securely mounted on the PCB.
2. Electrical Testing: Utilize multimeters and oscilloscopes to measure parameters like resistance, capacitance, and inductance. Confirm that the components meet their specified values within acceptable tolerances.
3. Functional Test: Set up the test environment by connecting the electronic components to the power supply, input/output devices, and any necessary test equipment. Run the components through their intended functions to verify proper operation.
4. Performance Evaluation: Compare the actual performance of the components against their specifications. This may include evaluating signal quality, power consumption, or response time.
5. Record Keeping: Document the results of each test, noting any deviations from specifications or identified defects. Include details on the component's make, model, and serial number, as well as the date and time of the test.
6. Review and Analysis: Analyze the test results to identify trends or potential issues. Use this information to improve the testing process or make necessary adjustments to the electronic components.
7. Communicate Results: Share the test findings with relevant stakeholders, such as quality assurance teams or product developers. Address any issues found and implement corrective actions as needed.
By following these steps, you will ensure that electronic components are tested thoroughly and meet the required quality standards.
Know more about the power consumption click here:
https://brainly.com/question/30122759
#SPJ11