Consider the following code.
The legal codewords are those 32-bit sequences in which the number of 1-bits is divisible by 6. That is, a codeword is legal if it is 32-bit long, and of these bits the number of 1-bits is 0, 6, 12, 18, 24, or 30. How much is the Hamming distance of this code, and how many single bit errors can this code detect and correct?
Answers
The Hamming distance of this code is 6. It can detect and correct up to 2 single bit errors.
The Hamming distance of a code is the minimum number of bit flips required to convert one legal codeword into another. In this case, the legal codewords have a fixed number of 1-bits that is divisible by 6.
To find the Hamming distance, we consider the minimum number of bit flips required to change between any two legal codewords. Since the number of 1-bits in a legal codeword can differ by 6, we need to flip at least 6 bits to convert between any two codewords. Therefore, the Hamming distance is 6.
With a Hamming distance of 6, this code can detect up to 2 single bit errors. When a single bit error occurs, it changes the number of 1-bits in the codeword by 1. Since the minimum distance between legal codewords is 6, the code can detect the presence of an error. Furthermore, it can correct the error if there is only a single bit flip, as it can identify the correct codeword based on the remaining 5-bit difference.
To learn more about hamming distance click here
brainly.com/question/32235664
#SPJ11
Related Questions
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
Write a program that reads a list of integers into a vector, and outputs the two smallest integers in the list, in ascending order. The input begins with an integer indicating the number of integers that follow. Ex: If the input is: 5 10 5 3 21 2 the output is: 2 and 3 You can assume that the list of integers will have at least 2 values. To achieve the above, first read the integers into a vector. Hint: Make sure to initialize the second smallest and smallest integers properly. Submit your .cpp code with this question's link. Output runs are not required.
Answers
Answer:
In C++:
#include <bits/stdc++.h>
#include <iostream>
#include <vector>
using namespace std;
int main(){
vector<int> vectItems;
cout << "Vector length: ";
int ln; cin>>ln;
int num;
for (int ikk = 0; ikk < ln; ikk++){
cin >> num;
vectItems.push_back(num);}
int small, secsmall;
small = secsmall = INT_MAX;
for (int ikk = 0; ikk < ln; ikk++){
if(vectItems[ikk] < small){
secsmall = small;
small = vectItems[ikk]; }
else if (vectItems[ikk] < secsmall && vectItems[ikk] != small) {
secsmall = vectItems[ikk];} }
cout<<small<<" "<<secsmall;
return 0;}
Explanation:
See attachment for program file where comments are used for explanation
I have asked that my account that i have been charged all summer long be canceled. i need a return call today to talk to someone asap 724.290.0332
Answers
There is a considerable potential that it could be altered for editing purposes if the aforementioned replay was recorded using editing software.
What is editing software?On a non-linear editing system, video editing software, also known as a video editor, is used to execute post-production video editing of digital video sequences. Both analog video tape-to-tape online editing devices and conventional flatbed celluloid film editing tools have been superseded by it. Any software program that can edit, modify, produce, or otherwise manipulate a video or movie file is referred to as video editing software. With the aid of a video editor, you can chop and arrange a video to improve its flow or add effects to make it more visually appealing.To learn more about editing software, refer to:
https://brainly.com/question/9834558
#SPJ4
hackers often set up their own wireless access points in popular areas with the hope that users connect to them. these are known as:
Answers
A computer worm is a sort of virus that replicates itself and spreads to other computers while still functioning on infected ones. A computer worm multiplies in order to infect other systems.
Transaction processing systems (TPS) handle business transactions for the corporation, supporting overall enterprise operations. The most prevalent topology is by far stars. This system has a star-like form because each node is autonomously connected to a central hub by a physical wire. All information must pass through the central node in order to go to its final location. After the link was established, the malicious access point might have viewed every Internet request that his laptop issued. A worm is a self-replicating, self-propagating, self-contained software that spreads to other computers over networking protocols. Worms can propagate through software flaws, show up in phishing email attachments, or be accessed through malicious URLs.
To learn more about computer worm click the link below:
brainly.com/question/16893265
#SPJ4
Identify the data type of each variable as either int, float, string, list, or boolean.

Answers
Data type of each variable is:
i-int
j-string
k-string
m-boolean
n-list
p-float
q-integer
r- boolean
s-int
t- string
u-string
v- float
w-string
What are data types?Data is categorized into different types by a data type, which informs the compiler or interpreter of the programmer's intended usage of the data. Numerous data types, including integer, real, character or string, and Boolean, are supported by the majority of programming languages. Today, binary data transfer is the most widely used type of data transport for all devices.
A collection of 0s and 1s arranged in a precise order makes up a binary kind of data. Every piece of information is translated to binary form and used as needed. Another set of binary data is connected to this binary form to define the type of data being carried since this binary form does not specify what it is carrying. Variables are specific storage units used in computer programming that hold the data needed to carry out tasks.
To know more about Data, check out:
https://brainly.com/question/19037352
#SPJ1
If there are n teams in a league and each team plays each other twice in a season, the total number of games is given by the polynomial n 2 - n = N. A women's basketball league plays a total of 30 games. How many teams are in the league?
Answers
The total number of games played in a league when there are n teams and each team plays each other twice in a season is given by the polynomial:
`n^2 - n = N`.Given, a women's basketball league plays a total of 30 games.Let the number of teams be x.So, `x^2 - x = 30`.We need to solve this equation to find the value of x. We can do this by factorizing the equation: `x^2 - x - 30 = 0`.
This can be further factorized into `(x - 6) (x + 5) = 0`.So, `x = 6` or `x = -5`.Since, the number of teams cannot be negative. Hence, the number of teams in the league is 6.There are six teams in the league if a women's basketball league plays a total of 30 games.
To know more about plays visit:
https://brainly.com/question/32749272
#SPJ11
Having a positive work ethic means accepting
constructive criticism even though it may be
painful. You should: (select all that apply)
show a positive facial expression.
maintain eye contact
not interrupt or speak until you are sure the
other person is finished making a point
question the person frequently throughout the
conversation

Answers
Answer:
2 and 3 (1 is debatable)
Explanation:
Answer:
123 and the next one is all of them
Explanation:

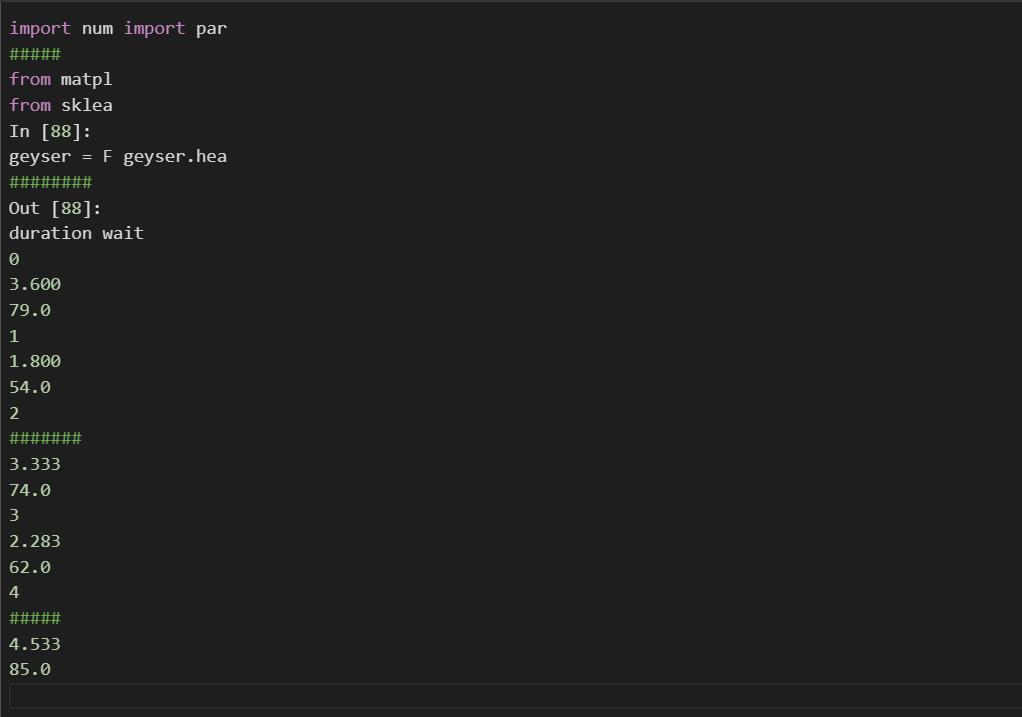
task-4: compute the eruption duration in standard units and append it as a new column named duration (standard units) to the dataframe geyser. also, compute the waiting times in standard units and append it as a new column named wait (standard units) to the dataframe geyser. after appending the 2 new columns successfully, print the first 5 rows of the dataframe geyser to the output.
Answers
Using the knowledge in computational language in C++ it is possible to write a code that compute the eruption duration in standard units and append it as a new column named duration.
Writting the code:import num import par
#####aa
from matpl
from sklea
In [88]:
geyser = F geyser.hea
########
Out [88]:
duration wait
0
3.600
79.0
1
1.800
54.0
2
#######
3.333
74.0
3
2.283
62.0
4
#####
4.533
85.0
What is matplotlib and example?Matplotlib is a cross-platform, data visualization and graphical plotting library for Python and its numerical extension NumPy. As such, it offers a viable open source alternative to MATLAB. Developers can also use matplotlib's APIs (Application Programming Interfaces) to embed plots in GUI applications.
See more about C++ at https://brainly.com/question/29632676
#SPJ1
1. Evaluate the following expressions
Mapping:
a. $\operatorname{map}$ (timesTwo, $[2,4,5])$
b. $\operatorname{map}($ timesTwo, [8])
c. $\operatorname{map}$ (timesTwo, [])
d. $\operatorname{map}(a d d O n e$, map(timesTwo, $[2,2,4,-3])$ )
e. map(timesTwo, map (addOne, [2, 2, 4, -3]))
Folding:
Example: foldFromLeft(plus, $7,[1,2]=((7+1)+2=8+2=10$
Example: foldFromRight(plus, $7,[1,2]=(1+(2+7))=1+9=10$
f. foldFromLeft(plus, $7,[3,-89]$ )
g. foldFromLeft(minus, $7,[3,-8,9]$ )
h. foldFromRight(minus, $7,[3,-8,9]$ )
i. foldFromLeft(minus, 7 , map(timesTwo, $[3,0,8])$ )
Answers
a. map(timesTwo, [2, 4, 5]) = [4, 8, 10]b. map(timesTwo, [8]) = [16]c. map(timesTwo, []) = []d. map(addOne, map(timesTwo, [2, 2, 4, -3])) = [5, 5, 9, -1]e. map(timesTwo, map(addOne, [2, 2, 4, -3])) = [6, 6, 10, -4]f. foldFromLeft(plus, 7, [3, -89]) = -79g. foldFromLeft(minus, 7, [3, -8, 9]) = 3h. foldFromRight(minus, 7, [3, -8, 9]) = 2i. foldFromLeft(minus, 7, map(timesTwo, [3, 0, 8])) = -47
How to evaluate the expressions?Given, the following expressions have to be evaluated: Mapping:a. map(timesTwo, [2, 4, 5])b. map(timesTwo, [8])c. map(timesTwo, [])d. map(addOne, map(timesTwo, [2, 2, 4, -3]))e. map(timesTwo, map(addOne, [2, 2, 4, -3]))Folding:f. foldFromLeft(plus, 7, [3, -89])g. foldFromLeft(minus, 7, [3, -8, 9])h. foldFromRight(minus, 7, [3, -8, 9])i. foldFromLeft(minus, 7, map(timesTwo, [3, 0, 8]))Evaluating the expressions are:Mapping:Map: It applies a function to each element of a sequence, such as a list, and returns a new list of the same size containing the results.
a. map(timesTwo, [2, 4, 5]) = [4, 8, 10]b. map(timesTwo, [8]) = [16]c. map(timesTwo, []) = []d. map(addOne, map(timesTwo, [2, 2, 4, -3])) = [5, 5, 9, -1]e. map(timesTwo, map(addOne, [2, 2, 4, -3])) = [6, 6, 10, -4]Folding:Reduce/ Fold: It is a method in which a function takes two values and returns a single value, reducing the list of values to a single value.f. foldFromLeft(plus, 7, [3, -89]) = -79g. foldFromLeft(minus, 7, [3, -8, 9]) = 3h. foldFromRight(minus, 7, [3, -8, 9]) = 2i. foldFromLeft(minus, 7, map(timesTwo, [3, 0, 8])) = -47Therefore, the final answers are:a. map(timesTwo, [2, 4, 5]) = [4, 8, 10]b. map(timesTwo, [8]) = [16]c. map(timesTwo, []) = []d. map(addOne, map(timesTwo, [2, 2, 4, -3])) = [5, 5, 9, -1]e. map(timesTwo, map(addOne, [2, 2, 4, -3])) = [6, 6, 10, -4]f. foldFromLeft(plus, 7, [3, -89]) = -79g. foldFromLeft(minus, 7, [3, -8, 9]) = 3h. foldFromRight(minus, 7, [3, -8, 9]) = 2i. foldFromLeft(minus, 7, map(timesTwo, [3, 0, 8])) = -47
To know more about map visit:
https://brainly.com/question/1670085
#SPJ11
has technology changed the world or even enhanced it
Answers
Answer:
Yep it has.
Explanation:
Technology has made it easier to farm, more feasible to build cities, and more convenient to travel, among many other things, effectively linking together all countries on earth. All of the technologies of communication, of example like the phone,the laptop, the smart watches your using now are all basic examples of how it has improved. Because of technology there are thousands of advantages and thousands of disadvantages like global warming that you all have learned for years. So yeah, technology really has changed the world and have created so many changes. Without technology you wouldn't even be able to ask people these questions right now!
Write a program that hardcodes N and then computes the average (the arithmetic mean) of N integers selected from [0,1000]. This program should run 10 times, and thus provide 10 results.
You should use an outer loop that runs the inner loop (the one which computer the mean) a total of 10 times, printing out the 10 results, one per line.
Answers
Answer:
Explanation:
Program ( PascalABC) and Result:
const N = 25;
var Summ : integer;
Num : integer;
Sa : real;
begin
Num := 0;
for var j := 1 to 10 do
begin
Summ := 0;
for var i:= 1 to N do
Summ := Summ + Random (1001);
Sa := Summ / N;
Write (' Sa = ', Sa);
WriteLn;
end;
end.
With p = 1 000 000 the result is naturally close to the middle of the interval (0 - 1000), that is, the number 500


if an administrator in an exchange server needs to send digitally signed and encrypted messages, what messaging implementation will best suit the administrator’s needs?
Answers
Using SIPS/SRTP. SIPS/SRTP can be defined as a secure peer to peer connection is used not just used for the audio but also while the connection is established. It means not just the audio is encrypted, but also the connection details (who is calling whom etc.). To use those secure protocols, all involved devices have to support SIPS and SRTP.
SRTP can be described as simply RTP with “secure” in front: secure real-time protocol. RTP can be defined as a protocol, but SRTP is not. Rather, it's the security layer added to RTP for encryption. SRTP extends RTP to contain encryption and authentication so that all WebRTC conversations are as secure as possible.
You can learn more about SIPS/SRTP at https://brainly.com/question/9561645
#SPJ4
which port is the most common port found on today's computing devices?
Answers
The most common port found on today's computing devices is the USB (Universal Serial Bus) port. The USB is a popular type of wired connection technology used to connect devices to computers or laptops.
It is used to connect peripherals such as keyboards, mice, cameras, printers, flash drives, and external hard drives to a computer or laptop.A USB port is usually found on almost all computing devices. It is not only found on computers and laptops, but also on smartphones, tablets, gaming consoles, and many other electronic devices. A USB port provides a fast and efficient data transfer between devices.
The first USB standard was introduced in 1996, and since then, the technology has undergone several improvements, including increased data transfer speeds and the ability to charge devices.USB ports come in different versions, including USB 1.0, USB 2.0, USB 3.0, and USB 3.1.
To know more about wired connection visit:
https://brainly.com/question/29272212
#SPJ11
to copy the content of a letter in another letter we can dash features
ans) mobile
Answers
Answer:
Copy/Cut
Explanation:
Copy option is used to copy the text without removing it from there. To copy any text just hold the text for 2-3 seconds, then you can able to see a box(first image). From there select Copy option. Now text has been copied.
Cut option is also used to copy any text but, it will remove the text from where we have cut it. To Cut any text hold the text which you want to cut. Then, you will see a box(first image), from the box select Cut option. After selecting Cut option the text will get copied in the clipboard and the text you have cut will be removed from there.
Now, to Paste the text you have copied/cut, go to any text field and hold there for 2-3 seconds and a box(Second image) will appear. Now, select Paste option and text will get paste there.


Which of the following is NOT one of the purposes of establishing a security policy for an organization? Question 1 options: Providing legal support for any intrusion or unauthorized use of information. Preventing and monitoring loss of information. Absolving users of individual liability on the network systems. Protecting the value of vital corporate information.
Answers
Answer:
Initially, national security was defined as the government's ability to protect its citizens from military attacks. Today, this definition also includes other non-military areas such as defense against crime and terrorism, economic security, environmental security, food security, energy security and cyber security.
It is early in the season and the night of the big football rivalry game, and you are so excited to spend time with friends and watch your boyfriend play ball. However, you are assigned to one of the football spreads and must take pictures. What do you do?
Answers
Answer:
take the pictures while watching him play
Explanation:
The colors of the pixels in a digital image are often represented by red, green, and blue values
between 0 and 255 (an RGB triplet). A photographer is manipulating a digital image to lighten it
because all of the RGB values in the image are less than 100, making it very dark. He does this
by adding 20 to the R, G, and B values of each pixel, then overwriting the original image. What
type of transformation is the photographer using on the digital image? plz help !!
Answers
Answer:
Lossless Transformation
Explanation:
ap computer science principles practice quiz unit 9 What is data?I. Computer readable informationII. Information collected about the physical worldIII. Programs that process imagesIV. Graphs and charts
Answers
Data refers to computer-readable information that can be used for various purposes, including analysis and decision-making. It is typically collected from various sources, including human input, sensors, and automated systems. This information can be stored and processed by computer programs to generate insights and inform actions.
The scope of data is vast and includes information collected about the physical world, such as environmental conditions, and information about human behavior, such as social media usage patterns. It can also include programs that process images, such as facial recognition software or satellite imagery analysis.
Data can be represented in various ways, including graphs and charts, which can help to visualize complex information and make it easier to understand. These visualizations can be used to identify patterns, trends, and relationships between different data points, and inform decision-making in various fields, including business, healthcare, and government.
To learn more about, analysis
https://brainly.com/question/19671930
#SPJ11
how many columns are there in ms-excel 2016.
Answers
Answer:
16,384 columns
Explanation:
Answer:
Madharchod.............
If we use the square wave to transmit digital data (0s and 1s), what will be the data rate. Note data rate is the bits per second. (if two bits contain in one period) 2. Then, if we use the first three components to represent square wave, what is the bandwidth? (Refer to lecture) 3. Consider a noiseless channel with a bandwidth of 3000 Hz transmitting a signal with two signal levels. What can be the maximum bit rate?
Answers
PLS HURRY!!! Look at the image below!
The choices for the second part are number +1, number, number -1

Answers
1. <1
2. -1
Explanation:
2
ng and Upgrading Computers: Mastery Test
Select the correct answer.
Which of the following can computer maintenance software determine?
O A.
O B.
O C.
O D.
whether your hard drive is about to fail
whether your monitor or screen is drawing too much power
the humidity inside your desktop computer
the amount of dust inside your laptop
Reset
Next
Answers
whether your hard drive is about to fail can computer maintenance software determine.
What is computer maintenance software ?
Software that centralises maintenance data and streamlines maintenance operations is known as a computerised maintenance management system, or CMMS. It aids in maximising the use and accessibility of tangible assets like machines, transportation, communications, plant infrastructures, and other assets. CMMS systems, also known as computerised maintenance management information systems (CMMIS), are used in the manufacturing, energy, transportation, building, and other sectors where physical infrastructure is essential.
A CMMS's database is its fundamental component. The information regarding the assets that a maintenance organisation is responsible for maintaining, as well as the tools, supplies, and other resources needed to do so, are organised using a data model.
Read more about computer maintenance software:
https://brainly.com/question/28561690
#SPJ1
anti-malware software fails to detect a ransomware attack that is supposed to be within its capabilities of detecting. what is this an example of?
Answers
When anti-malware software fails to detect a ransomware attack that is supposed to be within its capabilities of detecting, it is an example of a False Negative.The term false negative refers to the error that arises when a test result suggests that a condition is absent when it is actually present.
It is most often used in medical diagnosis, but it can also apply to other fields where testing is done, such as computer security.The occurrence of false negatives in computer security is undesirable. It means that malicious software is able to bypass the computer's security defenses. False negatives may result from the anti-malware program being outdated, misconfigured, or simply not recognizing a new or uncommon type of malware.To reduce the likelihood of false negatives, it is recommended that anti-malware software be kept up to date with the most recent signatures and definitions. In addition, a multi-layered approach to security, combining several tools and techniques, can help to minimize the risk of a single tool failing to detect a threat.The minimum length of the answer should be 100 words. The above answer consists of 150 words.
To know more about anti-malware visit:
https://brainly.com/question/29064342
#SPJ11
A homeowner is planning to use carpet tiles to cover the floor of a room measuring 9 feet by 10 feet 8 inches. If the carpet tiles are 8 inches wide and 1 foot long and there are no gaps between the tiles as they are placed on the floor, how many carpet tiles will the homeowner need to cover the floor of the room?
Answers
If the carpet tiles are 8 inches wide and 1 foot long, and there are no gaps between them as they are placed on the floor, the homeowner will need 144 carpet tiles to cover the floor of the room.
Given room dimensions of 9feet*10feet 8inch
tile dimensions of 8inch*1foot,
we can calculate
the number of tiles required. 1 foot=12 inch
number of tiles=area of room/area of tiles
=(9*12)inch*(12*10+8)inch/8inch *12 inch
=144
A homeowner is someone who owns a house or apartment in which they live.
This is the most common written policy for a homeowner, and it is intended to cover all aspects of the home, structure, and contents.
Most homeowner policies include replacement cost coverage for the home and actual cash value coverage for personal property.
A homeowner is someone who owns a house or apartment in which they live.
Learn more about homeowner here:
https://brainly.com/question/15243238
#SPJ4
Question 1 (1 point)
These errors can be difficult to identify, because the program still runs but it does
not do what you expect it to do.
1.Runtime
2.Logic
3.Syntax
4.Executing
Answers
Answer:
Logic
Explanation: I took the test in k12 and got it correct
help is always very appreciated

Answers
16.
num = float(input("Enter a number: "))
if num >= 0:
print(num**0.5)
17.
num1 = float(input("Enter the first number: "))
num2 = float(input("Enter the second number: "))
operation = input("Which operation would you like to perform (a/s/m/d): ")
if operation == "a":
print("{} + {} = {}".format(num1, num2, num1+num2))
elif operation == "s":
print("{} - {} = {}".format(num1, num2, num1-num2))
elif operation == "m":
print("{} * {} = {}".format(num1, num2, num1*num2))
elif operation == "d":
print("{} / {} = {}".format(num1, num2, num1/num2))
18.
The answer is algorithm
19.
The correct answer is C
20.
We analyze algorithms to see which algorithm is the best fit for the job.
I hope this helps!
You have been assigned the task to store a number in a variable. The number is 51,147,483,647,321. You have different data types like Integer, Float, Char, and Double. Which data type will you use from the given data types to store the given number and why? Justify your answer with logical reasoning.
Answers
To store the number 51,147,483,647,321, the data type that can be used is long int. The reason why long int is the best choice is because it can store large values of data like 51,147,483,647,321 and it does not need any floating-point calculations.
A data type is a fundamental concept in programming. A data type specifies a particular type of data and defines a set of operations that can be performed on the data. In programming, data types are used to define variables. The data type of a variable determines the type of data that can be stored in the variable.
The best data type to use to store the number 51,147,483,647,321 is long int because it is a 64-bit integer that can store large values like 51,147,483,647,321. It is a perfect fit for the given number and it does not need any floating-point calculations. Thus, the long int data type is the best choice to store the number 51,147,483,647,321.
To know more about store visit:
https://brainly.com/question/29122918
#SPJ11
c)The online sales pack for each property includes: PDF
documents giving details such as location, floor plans
and energy ratings•photographs•a virtual tour
video. (i)Describe the use and implications of codecs
when using video in digital format. 4 MARKS
Answers
Answer:
https://gcseprep.com/wp-content/uploads/2020/04/Unit-1-Information-Technology-Systems-Jan-2019-Qs.pdf
Explanation:
nobody learns this bro
I love how it's Saturday and you guys still have like a billion questions :P, but have a good rest of you're weakened. Bye!
Answers
Which type of GUI control would be best to use if you wanted the user to select one date from a list of three possible dates to take an exam
Answers
A type of GUI control that is best to use if you want the user to select one date from a list of three possible dates to take an exam is radio buttons.
What is a GUI control?A GUI control is an abbreviation graphic user interface control and it can be defined as a form of user interface that is designed and developed to make it easier for end users to interact, control and use an electronic device, especially through a combination of graphical icons, symbols, images and audio indicator.
In this scenario, radio buttons are a type of graphic user interface control (GUI control) that is best to use if you want end users to select one date from a list of three possible dates to take an examination because they are specifically used for mutually exclusive options.
Read more on GUI control here: https://brainly.com/question/4138138