Consider the criteria for CPU scheduling algorithms, ___________ is more important for an interactive system.
Answers
Consider the criteria for CPU scheduling algorithms, response time is more important for an interactive system.
CPU scheduling is the technique of distributing CPU time among various processes. The scheduling algorithm is implemented by the operating system. The scheduling algorithm is used to select the process that will execute next. This algorithm uses the CPU efficiently while still ensuring a reasonable response time for interactive users and limiting the effect of I/O-bound processes on the system.CPU utilization – Keep the CPU as busy as possible.
Turnaround time – Total time it takes for a process to execute.Response time – Time from when a request is submitted until the first response is generated. It is more important for an interactive system, as the computer should respond promptly to user requests.Throughput – Number of processes executed per unit time. It can be increased by increasing the number of processes.Terms like Fairness, starvation, etc. are also considered to develop a good scheduling algorithm.
Learn more about CPU scheduling: https://brainly.com/question/19999569
#SPJ11
Related Questions
What are Apps?
How do we interact with them?
Answers
Answer:
Sliding elements in list format.
Cards.
Images.
Buttons.
Overflow screens.
Multiple selection app interactions.
Text input fields.Explanation:
What is wrong with the following code? publicstatic char grade(int score) { if (score >= 9) { return 'A'; } else if (score >= 8) { return 'B'; } else if (score >= 6) { return 'C'; } else if (score > 4) { return 'D'; } else if (score < 4) { return 'F'; } }
Answers
Answer:
c) No return statement for all possible logic paths
What does this code do?
for n in range(10, 0, -1):
print(str( n ) + " Mississippi")
What does this code do?
x = 0
while(x < 10):
print(x)
x = x + 1
Answers
Answer:
The `for` part prints:
"10 Mississippi"
"9 Mississippi"
All the way down to
"0 Mississippi".
The `while` part prints a number a line starting from 0 all the way up to 9.
Explanation:
`for n in range(10, 0, -1) means iterate over all the elements starting at 10, all the way down to 0 by steps of -1. Then using that `n` value, convert it to a string value, because by default it is an integer, and then use it to fill in the string "n Mississippi".
A `while` loop will continue iterating while the parenthesis-enclosed condition is true. That means, while x is smaller than 10 the code inside the while loop will execute. In this case, the variable x is declared and initialised at a value of 0. 0 is smaller than 10 so the variable is printed and then, x is given a new value which is the current value of x plus 1. Then, the while loop is executed again and again, until x equals 9. When that happens and 1 is added to its value, the condition is no longer true, because 10 is not smaller than 10, so the loop won't execute any further.
(03 MC)Why is it important to set goals and share them with others?
A) Sharing goals makes you feel like you are better than the other person.
B) If you share your goals, you are more likely to achieve them.
C) Sharing goals is something you should do in order to get a good grade.
D) If you share your goals with others, people will like you more.
ANSWER: B) If you share your goals, you are more likely to achieve them.
Answers
Answer:
answer is b
Explanation:
hope it was helpful
Answer: B, If you share your goals, you are more likely to achieve them.
We know sharing goals can be helpful to everyone, one of the main reasons people share goals is so that they can get the motivation to carry on doing their work. For example, If you and a friend had a goal of going to the gym 3 times a week you would feel responsible if you told your friend that you wouldn't be able to complete the goal this week. Which would make you feel bad for your friend who wants to complete the goal. It also helps with motivation if your friend doesn't want to go then you encourage them and make sure they remember the goal.
Answer choice A, would not make much sense since you are doing the goal together, and + this is a school question and they wouldn't encourage ego. Answer choice C, could be a result of sharing goals with others but doesn't suit the question as much as B. Answer choice D, does apply to the question at all people could end up liking you more but it could also end up the other way around.
Our answer is without a doubt B
Enjoy!
the most common type of database used with personal computers today is a:_____.
Answers
The most common type of database used with personal computers today is a relational database.
A relational database is the most prevalent type of database used with personal computers. It organizes and stores data in tables with predefined relationships between them. Relational databases utilize structured query language (SQL) to manage and manipulate data, allowing for efficient data retrieval and storage. They provide a flexible and scalable solution for managing and organizing various types of data, making them suitable for a wide range of applications. The relational model's popularity can be attributed to its simplicity, ease of use, and widespread adoption by popular database management systems such as MySQL, Oracle, and Microsoft SQL Server.
Learn more about database here:
https://brainly.com/question/30163202
#SPJ11
A company is looking for an employee to help organize customer information
for the sales team. Which computer field includes this job?
Answers
Answer:
Database
Explanation:
Just took the quiz
The first time you save a file, there is no difference between the Blank Space __________ and Save As commands.
Answers
I think the answer is save.
Hope that helps!
what is the name of the file that has the shape with the largest perimeter from the six files dataset1.txt, dataset2.txt, dataset3.txt, dataset4.txt, dataset5.txt, and dataset6.txt?
Answers
The file with the shape with the largest perimeter is data. It contains the shape with the highest perimeter out of all the shapes in the other five files.
The six files dataset1.txt, dataset2.txt, dataset3.txt, dataset4.txt, dataset5.txt, and dataset6.txt all contain shapes with different perimeters. The shape with the largest perimeter is contained in the file dataset4.txt. This file holds the shape with the highest perimeter out of all the shapes stored in the other five files. The shape contained in dataset4.txt can be identified by the largest perimeter value it has compared to the other shapes in the other files. All the shapes in the other five files have smaller perimeters than the shape in dataset4.txt, thus making it the file with the shape with the largest perimeter. Additionally, the shape in dataset4.txt can be further identified by its other properties such as the number of sides and angles it has. Comparing the values of these properties with the values of the other shapes in the other five files can further confirm that dataset4.txt holds the shape with the largest perimeter.
Learn more about data here-
brainly.com/question/11941925
#SPJ4
What is the answer to this A term career is usually applied to a Someone please HEEEEEEEEEELP MEEEEEEE. THX
Answers
Answer:
Position that allows for professional growth and advancement
The term career is used in a number of ways but is usually applied to means the same thing: a position that allows for professional growth and advancement. It relates to a person’s occupation or profession and his journey of life, learning (training or formal education) and work.
Answer:
Position that allows for professional growth and advancement
Explanation:
a p e x
What is 1+1 me is having trouble +100
Answers
To add 1 + 1 in a program, you can use a programming language like Python. Here's an example of how you can write a program to perform this addition
# Addition program
num1 = 1
num2 = 1
# Add the numbers
result = num1 + num2
# Print the result
print("The sum of 1 + 1 is:", result)
How does this work?This program declares two variables num1 and num2, assigns them the values 1, performs the addition using the + operator, and stores the result in the variable result.
Finally, it prints the result using the print function.
The output eill result in the folluming
The sum of 1 + 1 is - 2
Learn more about Python at:
https://brainly.com/question/26497128
#SPJ1
In a single paragraph, write about the functions of HTML tags.
Answers
Answer:
The main function of HTML Tag is to define the set of rules for browsers to display the content of web page in a certain way. The content could be anything Text, Image and even video (thanks to HTML5). It tells your browser what to display on the Web Page and how to display it. Overview. People use tags to aid classification, mark ownership, note boundaries, and indicate online identity. Tags may take the form of words, images, or other identifying marks. An analogous example of tags in the physical world is museum object tagging.
Explanation:
Hope this helps :)
Answer:
The main function of HTML Tag is to define the set of rules for browsers to display the content of web page in a certain way. The content could be anything Text, Image and even video (thanks to HTML5). It tells your browser what to display on the Web Page and how to display it. Overview. People use tags to aid classification, mark ownership, note boundaries, and indicate online identity. Tags may take the form of words, images, or other identifying marks. An analogous example of tags in the physical world is museum object tagging.
Explanation:
virtual conections with science and technology. Explain , what are being revealed and what are being concealed
Answers
Some people believe that there is a spiritual connection between science and technology. They believe that science is a way of understanding the natural world, and that technology is a way of using that knowledge to improve the human condition. Others believe that science and technology are two separate disciplines, and that there is no spiritual connection between them.
What is technology?
Technology is the use of knowledge in a specific, repeatable manner to achieve useful aims. The outcome of such an effort may also be referred to as technology. Technology is widely used in daily life, as well as in the fields of science, industry, communication, and transportation. Society has changed as a result of numerous technological advances. The earliest known technology is indeed the stone tool, which was employed in the prehistoric past. This was followed by the use of fire, which helped fuel the Ice Age development of language and the expansion of the human brain. The Bronze Age wheel's development paved the way for longer journeys and the development of more sophisticated devices.
To learn more about technology
https://brainly.com/question/25110079
#SPJ13
A 1kg block is being pushed against a wall by a force F = 75 N as shown. The coefficient of friction is
0.25. The magnitude of acceleration of the block is
Answers
Answer:
37deg
Explanation:
Answer:
37n
Explanation:
URGENT!!!! What is the concept of using the internet to trade goods and services called?
Answers
Answer:
barter
Explanation:
is the direct trade of goods, services and resources without the use of money
Answer:
e-commerce
Explanation:
just took the test, see pic below

Can anyone help with this

Answers
b) Hard Disk
c) Solid state drives (SSD)
The answer to this problem
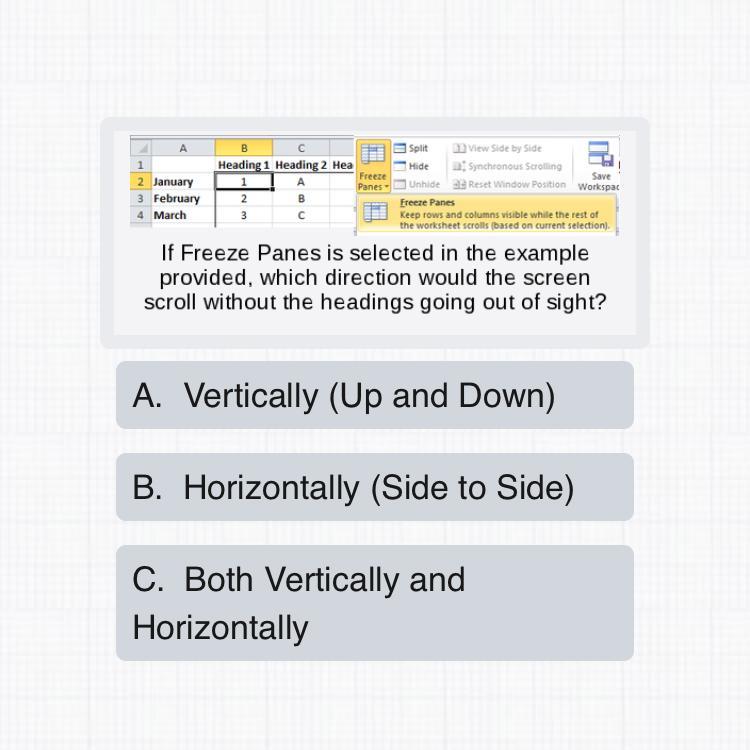
Answers
who sang devil went down to georgia
Answers
Answer:
Charlie Daniels sang that one for sure
Question 8 of 10
What does DOS stand for?
A. Disk override system
B. Disk only system
C. Disk opening system
D. Disk operating system
Answer: D
Answers
Answer:
Dis operating system
Explanation:
refers to the original operating system developed by Microsoft for IBM
Answer:
disk
Explanation:
Standard search engine spiders are typically unable to index?
Answers
Standard search engine spiders are typically unable to index because of databases of unlinked content and sites that needs user login.
What is a search engine?A search engine is known to be a form of an web-based tool that helps users to be able to find information that can be gotten from the World Wide Web.
Note that Popular examples of search engines are , Yahoo and others.
Note that a search engine is also seen as a kind of a software system that is made to carry out some work such as web searches.
They are known to help users to search the World Wide Web in a a way that is systematic in nature for particular information which is said to be specified in a textual web search query.
Hence, Standard search engine spiders are typically unable to index because of databases of unlinked content and sites that needs user login.
Learn more about search engine from
https://brainly.com/question/504518
#SPJ1
Why are the letters on a keyboard not in alphabetical order.
Answers
Answer:
The reason dates back to the time of manual typewriters.
Explanation:
When first invented , they had keys arranged in an alphabetical order, but people typed so fast that the mechanical character arms got tangled up. So the keys were randomly positioned to actually slow down typing and prevent key jams
which of the following are typically associated with human resource security policies
background checks, termination
Answers
Both background checks and termination are typically associated with human resource security policies. Background checks are commonly used to screen potential employees and ensure that they have no criminal history or other red flags that could pose a security risk to the organization.
Termination policies are also a key component of human resource security, as they help to ensure that employees who are no longer authorized to access sensitive information or systems are promptly removed from the organization. Additionally, termination policies may also include protocols for returning company equipment and revoking access credentials, further protecting the organization from potential security breaches. Overall, both background checks and termination policies play important roles in protecting the security and integrity of an organization's information and assets.
learn more about human resource security policies here:
https://brainly.com/question/15351151
#SPJ11
que significa DESFRAGMENTAR EL DISCO DURO?????
Answers
Answer:
DESFRAGMENTAR
Explanation:
es el proceso de reorganizar los datos almacenados en el disco duro para que los datos relacionados se vuelvan a juntar, todos alineados de manera continua.
Unethical behavior in a media house can be reduced if management does all of the following except.
Answers
Unethical behavior in a media house can be minimized if management does all of the following except A: "depends totally on workers' personal ethics".
Unethical behavior can be described as actions that are against social norms and values or acts that are considered unacceptable to people. In the context of the given scenario where management wants to reduce unethical behavior in the media house, to obtain the purpose they can take the following steps:
Punish unethical behavior stronglyLimit the opportunities for unethical behaviorIntroduce clear policies on unethical behavior"
Complete question:
Unethical behavior in a media house can be reduced if management does all of the following except.
depends totally on employees' personal ethics.
Punish unethical behavior firmly
Limit opportunities for Unethical behavior
establish clear policies on unethical behavior
"
You can learn more about Unethical behavior at
https://brainly.com/question/2258356
#SPJ4
A stop check valve is a type of check valve that Cannot be shut remotely. Can be used to prevent flow in both directions. Contains both a gate valve disk and a check valve disk. Can be opened manually
Answers
A stop check valve is a unique type of check valve that contains both a gate valve disk and a check valve disk and can be used to prevent flow in both directions. However, unlike regular valves, it cannot be shut remotely but can be opened manually.
- A stop check valve is a type of check valve that cannot be shut remotely.
- It can be used to prevent flow in both directions.
- It contains both a gate valve disk and a check valve disk.
A stop check valve is a combination of a lift check valve and a globe valve. It is commonly used in applications where it is necessary to prevent reverse flow and regulate forward flow. The disk in a stop check valve is designed to work with the flow of fluid. The disk is guided by a stem and travels linearly to shut off the flow. When there is reverse flow, the valve's disk closes against the valve seat and prevents backflow. This is because the stop check valve has a check valve disk that opens to allow flow in only one direction. This feature helps prevent any damage to the downstream system.
However, a stop check valve is different from a regular check valve. Unlike regular check valves, a stop check valve can be opened manually, making it useful in case of emergencies. This means that the valve can be locked open to allow for maximum flow during a fire or any other emergency. A stop check valve is often used in systems such as power plants, chemical plants, and water treatment facilities. These facilities require a type of valve that can prevent backflow and reverse flow while being able to regulate forward flow.
In conclusion, a stop check valve is a type of valve that is designed to prevent reverse flow, regulate forward flow, and lock open in case of an emergency. This type of valve is commonly used in power plants, chemical plants, and water treatment facilities, where there is a need for a valve that can regulate and control flow. Even though a stop check valve cannot be shut remotely, it is a useful valve in case of an emergency. It is designed to work with the flow of fluid and contains a check valve disk that opens to allow flow in only one direction. The valve's disk closes against the valve seat to prevent backflow when there is reverse flow.
To know more about stop check valve, visit:
https://brainly.com/question/31938355
#SPJ11
Write a program that gets a list of integers from input, and outputs non-negative integers in ascending order (lowest to highest). Ex: If the input is: 10 -7 4 39 -6 12 2 the output is: 2 4 10 12 39
Answers
Answer:
Following are the code to this question:
#include <iostream>//defining header file
using namespace std;
int main()//defining main method
{
int a[]={10,-7,4,39,-6,12,2};//defining single deminition array and assign value
int i,x,j,t; //defining integer variable
cout<<"Before sorting value: ";
for(i=0;i<7;i++) //using loop to print value
{
cout<<a[i]<<" ";//print value
}
cout<<endl <<"After sorting value: ";
for(i=0;i<7;i++)//defining loop to sort value
{
for(j=i+1;j<7;j++)//count array value
{
if(a[i]>a[j]) //defining condition to inter change value
{
//performing swapping
t=a[i]; //integer variable t assign array value
a[i]=a[j];//swapp value
a[j]=t;//assign value in array
}
}
}
for(i=0;i<7;i++) //defining loop to print value
{
if(a[i]>=0) //defining condition to check positive value
{
cout<<a[i]<<" ";//print value
}
}
return 0;
}
Output:
Before sorting value: 10 -7 4 39 -6 12 2
After sorting value: 2 4 10 12 39
Explanation:
Following are the description to the above code:
In the above program code, Inside the main method, an array a[] is declared that assign some value, and another integer variable "i, j, x, and t" is declared, in which variable "i and j" are used in the loop, and "x, t" is used to sort value.In the next step, three main for loop is declared, in which the first loop is used to print array value.In the second loop, inside another loop is used that sorts array values.In the last loop, a condition is defined, that check the positive value in the array and print its values.Answer:
integers=[]
while True:
number=int(input())
if number<0:
break
integers.append(number)
print("",min(integers))
print("",max(integers))
Explanation:
what is role can ICT play in helping school take part in social responsibility
Answers
Answer:
The answer is below
Explanation:
Given that Social responsibility deals with ideas that individuals or groups of people are expected or bound to work in alliance with other individuals or groups of people in favor of the generality of society.
Hence, some of the role ICT can play in helping school take part in social responsibility are:
1. Helps students to have independent access to knowledge
2. It assists the students with special needs
3. It helps the teachers to teach outside the comfort of the classroom only.
4. It exposes teacher and students to more knowledge and opportunities
5. The school governing body can access people and the community's opinions about ways to improve the school better.
6. It exposes the school to more ideas and opportunities.
7. It can be used to assist the school in improving the quality of education, both for the teachers and students side.
What does the following code result in
bold
A.bold
B.bold
C.Bold ( in bold )
D. BOLD
Answers
Answer:
c
Explanation:
changing the column width in a datasheet changes the structure of a table. T/F?
Answers
Changing the column width in a datasheet can change the structure of a table as it affects the arrangement of the data within the columns and can impact the overall layout of the table.
The correct answer is False .
It is important to consider the impact of column width changes on the table's structure and functionality before making any adjustments. Changing the column width only affects the visual display of the table, making it easier to read and navigate, but it does not alter the underlying structure or organization of the data within the table.
The column width in a datasheet does not affect the structure of the table. Changing the column width only affects the visual display of the table, making it easier to read and navigate, but it does not alter the underlying structure or organization of the data within the table.
To know more about structure visit :
https://brainly.com/question/30051017
#SPJ11
Explain the expression below
volume = 3.14 * (radius ** 2) * height
Answers
Answer:
Explanation:
Cylinder base area:
A = π·R²
Cylinder volume:
V = π·R²·h
π = 3.14
R - Cylinder base radius
h - Cylinder height
which attack is typically used specifically against password files that contain cryptographic hashes?
Answers
The decryption of data using a birthday attack is a form of cryptographic attack that looks for matches in the hash function.
What is meant by birthday attack?However, only the birthday attack expressly targets the cryptographic hashes kept in a system's password file. All of the other attack techniques listed may be used against passwords.
An example of a cryptographic attack that takes advantage of the birthday problem's math is the birthday attack. A communication breach between two or more parties may be caused by this attack.
You have a one in 365 chance of having a birthday in the same year as each of the other 22 people in a room of 23, or a total of 22/365 chances, if there are 23 people present. Joe has a 21/365 probability of having a birthday in common with the persons who are still present if you don't match.
A birthday attack is a type of cryptographic attack that decrypts data by searching for matches in the hash function.
Therefore, the answer is birthday attacks.
To learn more about birthday attacks refer to:
https://brainly.com/question/18566296
#SPJ4