Consider a multiprocessor system and a multithreaded program written using the many-to-many threading model. Let the number of user-level threads in the program be greater than the number of processors in the system. What relationship is expected for the performance of the system (in terms of total CPU utilization across the multiple processors) in the following scenarios. a. The number of kernel threads allocated to the program is less than the number of processors. b. The number of kernel threads allocated to the program is equal to the number of processors. c. The number of kernel threads allocated to the program is greater than the number of processors but less than the number of user-level threads.
Answers
CSS is used to define and format the HTML elements of a web page.
In two lines:
CSS is a styling language for web pages that allows you to define and format HTML elements.
How does CSS define and format HTML?CSS (Cascading Style Sheets) is a crucial component of web development. It is a styling language that defines the appearance and formatting of HTML elements on a web page. CSS provides a set of rules and properties that specify how the content should be displayed, such as colors, fonts, layout, and positioning.
By separating the presentation layer (CSS) from the structure (HTML), CSS enables developers to create consistent and visually appealing designs across multiple pages or even entire websites. With CSS, you can control the size, spacing, alignment, and various other aspects of the elements on your web page. It simplifies the process of styling and provides flexibility in customizing the look and feel of a website.
Learn more about Format HTML
brainly.com/question/31894258
#SPJ11
The performance of the system in terms of total CPU utilization across multiple processors is expected to vary based on the allocation of kernel threads to the program.
How does the allocation of kernel threads impact system performance in a multiprocessor system with a multithreaded program?When the number of kernel threads allocated to the program is less than the number of processors, the system's performance may be suboptimal. Some processors may remain idle or underutilized, leading to lower overall CPU utilization.
When the number of kernel threads allocated to the program is equal to the number of processors, the system's performance can be maximized. Each processor is assigned a kernel thread, allowing for efficient utilization of available CPU resources.
When the number of kernel threads allocated to the program is greater than the number of processors but less than the number of user-level threads, the system's performance may be constrained. While some user-level threads can run in parallel on different processors, the excess kernel threads compete for CPU time, potentially resulting in lower overall CPU utilization.
Learn more about the impact of kernel thread
brainly.com/question/31570489
#SPJ11
Related Questions
Computers that are close to one another are connected to form a LAN
Answers
Explanation:
different computer are connected to a LAN by a cable and an interface card
Answer:
network is a group of computers (or a group of smaller networks) that are connected to each other by various means, so that they may communicate with each other. The internet is the largest network in the world.
Which of the following is a strategy used to enhance communication in a presentation?
A) using as few slides as possible by increasing the amount of information on each slide
B) using bullets to break up text and to highlight important talking points
C) using a large variety of backgrounds colors and slide transitions
D) using images to fill up unused space on each slide
Answers
A strategy which is used to enhance communication in a presentation is: B. using bullets to break up text and to highlight important talking points.
What is a presentation?A presentation refers to an act that involves the process of speaking to an audience, in order to formally explain an idea, subject matter, piece of work, topic, product, or project, especially through the use of multimedia resources or samples.
Generally, a strategy which can be used by a teacher or presenter to enhance communication in a presentation is by using bullets to break up text while highlighting important talking points.
Read more on presentation here: brainly.com/question/11827791
which of the following is a fast and easy way to gather information about a company? (choose all that apply.) a. conduct port scanning. b. perform a zone transfer of the company's dns server. c. view the company's website. d. look for company ads in publications.
Answers
Option C is correct look at the company's webpage is a quick and easy method to learn about a business.
What is one method for gathering topic information?Look for email accounts of IT workers on the internet. A DNS entry containing the DNS Server details. Port scanning is a technique for identifying which network ports are accessible and potentially getting or sending data. It is also a method of transmitting packets to particular ports on a host and examining the replies to find weaknesses. Port Monitoring Methods. Nmap is one of the most widely used open-source port monitoring applications. Nmap offers a variety of port scanning methods for various situations. You'll need an A record for your mail server first. Of course, your ISP's unchanging IP address was the first stage. 2.21. Log into the web interface for the example.com name and make a "A" entry for "mail" for 192.0.
Learn more about network ports from here;
https://brainly.com/question/13068616
#SPJ1
what page orientation has more room across the page?
Answers
Answer:
What is an advantage of landscape page orientation? Landscape lets you put more across the page.The page orientation that typically has more room across the page is landscape orientation.
Landscape orientation refers to a page layout where the width of the page is greater than its height.
In this orientation, the content spans a wider area, providing more horizontal space on the page.
This makes landscape orientation suitable for displaying or working with content that requires a wider layout, such as tables, charts, wide images, or multiple columns of text.
On the other hand, portrait orientation has the height greater than the width.
Portrait orientation is more commonly used for documents like letters, books, and standard text-based content.
While portrait orientation allows for more vertical space, it generally provides less room across the page compared to landscape orientation.
Thus, landscape orientation offers more room across the page, making it preferable for content that requires a wider layout or more horizontal space.
For more details regarding landscape orientation, visit:
https://brainly.com/question/31008729
#SPJ2
windows evolved from a microsoft operating system called _____.
Answers
Windows evolved from a Microsoft operating system called MS-DOS (Microsoft Disk Operating System). MS-DOS was a command-line-based operating system that served as the foundation for early versions of Windows.
In the early days of personal computing, Microsoft developed MS-DOS as its primary operating system. MS-DOS was a command-line-based operating system that provided a text-based interface for users to interact with the computer. It was primarily used on IBM-compatible personal computers. As technology advanced and graphical user interfaces (GUIs) became more prevalent, Microsoft saw an opportunity to enhance the user experience by introducing a GUI-based operating system. This led to the development of the first version of Windows, known as Windows 1.0, which was released in 1985. Windows 1.0 built upon the foundation of MS-DOS, providing a graphical interface that allowed users to navigate and interact with the computer using a mouse and windows-based applications. Subsequent versions of Windows, such as Windows 3.1, Windows 95, Windows XP, and the modern Windows 10, continued to evolve and improve upon the initial Windows concept, eventually becoming the widely used operating system we know today. However, it is important to note that while Windows evolved from MS-DOS, it gradually moved away from its dependence on MS-DOS and developed its own standalone operating system architecture.
Learn more about MS-DOS here:
https://brainly.com/question/31941186
#SPJ11
Tristan has successfully deleted the blank row. The next thing he wants to do is to increase the length of the first column. A 2 column table with 7 rows. Column 1 is labeled Use with entries Space cooling, Water heating, Lighting, Space heating, Refrigerators and freezers, Television and related equipment, All other uses. Column 2 is labeled Percentage with entries 17.5, 9.5, 9.2, 9.1, 8.8, 5.9, 40. How does he resize the column? Move the Move Table Column marker on the ruler to the left. Move the Move Table Column marker on the ruler to the right. Put the cursor on the right side of the first column and drag the cursor to the left. Put the cursor on the left side of the first column and drag the cursor to the right.
Answers
Answer:
Move the Move Table Column marker on the ruler to the right.
Explanation:
The true statement is: (b) Move the Move Table Column marker on the ruler to the right.
From the question, we understand that:
The blank row has been deletedThe length of the first column is to be increased.When the first column is increased, each cell on that column would occupy more space.
A table can be refitted by rulers
To increase the length of the column, he needs to place the move table column marker on the ruler to the right-hand side of the table
Hence, the true statement is (b)
Read more about tables at:
https://brainly.com/question/17338228
Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive File Definition
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option. The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files athttps://brainly.com/question/15355917.
#SPJ4
Which cloud concept describes the ability of a cloud service to be accessed quickly from any location via the internet
Answers
The cloud concept that describes the ability of a cloud service to be accessed quickly from any location via the internet is called cloud computing. Cloud computing refers to the delivery of computing resources such as servers, storage, applications, and services over the internet. These resources are provided by a third-party provider and can be accessed and used on demand by users from anywhere with an internet connection.
Cloud computing offers several benefits such as scalability, flexibility, cost-effectiveness, and ease of access. The ability to access cloud services quickly from any location via the internet is one of the key advantages of cloud computing. Users can access their applications and data from any device and location, making it easier to collaborate and work remotely.
Cloud computing has revolutionized the way businesses operate and has become an essential part of modern IT infrastructure. The rise of cloud computing has also enabled new technologies such as artificial intelligence, machine learning, and the internet of things to flourish. As the demand for cloud services continues to grow, the industry is constantly evolving and developing new solutions to meet the needs of businesses and consumers.
In summary, cloud computing is a cloud concept that enables quick access to cloud services from any location via the internet. It offers several benefits and has become an essential part of modern IT infrastructure.
More on clouds : https://brainly.com/question/9759640
#SPJ11
Tell me 2-6 computer parts that are inside a computer.
Spam answers will not be accepted.
Answers
Answer:
Memory: enables a computer to store, at least temporarily, data and programs.
Mass storage device: allows a computer to permanently retain large amounts of data. Common mass storage devices include solid state drives (SSDs) or disk drives and tape drives.
Input device: usually a keyboard and mouse, the input device is the conduit through which data and instructions enter a computer.
Output device: a display screen, printer, or other device that lets you see what the computer has accomplished.
Central processing unit (CPU): the heart of the computer, this is the component that actually executes instructions.
Explanation:
assume an algorithm takes 4.4 seconds to execute on a single 3.4 ghz processor. 44% of the algorithm is sequential. assume that there is zero latency and that the remaining code exhibits perfect parallelism. how long (in seconds) should the algorithm take to execute on a parallel machine made of 3 3.4 ghz processors? round answers to one decimal place (e.g. for an answer of 17.214 seconds, you would enter 17.2).
Answers
Assume an algorithm takes 4.4 seconds to execute on a single 3.4 GHz processor. 44% of the algorithm is sequential. assume that there is zero latency and that the remaining code exhibits perfect parallelism. The algorithm should take approximately 2.3 seconds to execute on a parallel machine made of three 3.4 GHz processors.
Given that the algorithm takes 4.4 seconds to execute on a single 3.4 GHz processor. 44% of the algorithm is sequential.
The time needed for the sequential part of the algorithm to execute = 44% of 4.4 seconds = 1.936 seconds
Time needed for the parallel part to execute = 4.4 seconds - 1.936 seconds = 2.464 seconds
Since there is zero latency, the total time needed for the algorithm to execute on three 3.4 GHz processors =Sequential time + parallel time/number of processors = 1.936 + (2.464/3) seconds= 2.347 seconds (rounded to one decimal place).
Hence, the algorithm should take approximately 2.3 seconds to execute on a parallel machine made of three 3.4 GHz processors.
Know more about the Algorithm here :
https://brainly.com/question/24953880
#SPJ11
how do you take a screenshot on a Samsung tablet
Answers
Explanation:
to capture a screenshot press and hold the power and volume down button at the same time for approximately 2 seconds
The process of increasing the length of a metal bar at the expense of its thickness is called
Answers
The process of increasing the length of a metal bar at the expense of its thickness is called drawing out.
The technique of growing the duration of a metallic bar at the rate of its thickness is known as "drawing out" or "elongation." Drawing out entails applying tensile forces to the steel bar, causing it to stretch and end up longer even as simultaneously reducing its move-sectional location.
During this technique, the steel bar is normally clamped at one give up at the same time as a pulling pressure is carried out to the other give up. As the force is exerted, the metal undergoes plastic deformation and elongates. This outcomes in a decrease in the bar's thickness, because the material redistributes alongside its duration.
Drawing out is normally utilized in various manufacturing strategies, which includes wire manufacturing, where a thick steel rod is drawn through a sequence of dies to gradually lessen its diameter whilst increasing its period. This elongation process can enhance the mechanical properties of the metallic, inclusive of its power and ductility, whilst accomplishing the desired dimensions for specific programs.
Read more about elongation at:
https://brainly.com/question/29557461
Rafe is transportation engineer working on a light rai, system. Who are the other two
specialized civil engineers Rafe is LIKELY working with?
(1point)
Answers
The other two specialized civil engineers Rafe is LIKELY working with are: Structural Engineers and geotechnical engineer
The specialized civil engineersThe second engineer is a geotechnical engineer who deals with the challenges related to ground conditions and provides recommendations for foundation design and slope stability.
Together, these specialized civil engineers collaborate with Ra e to address different engineering aspects of the project, ensuring the construction of a safe and efficient light rail system.
In summary Rafe would work with Structural Engineers and geotechnical engineer.
Read more on civil engineers
https://brainly.com/question/14559197
#SPJ1
Customizable diagrams, including List, Process, and Cycle diagrams, are built into Word and can be found in
O SmartArt.
O WordArt.
O Clip Art
O Pictures
Please help ASAP
Answers
Answer:
clip art
Explanation:
i hope this helps you
what is the most popular web server application? group of answer choices microsoft internet information services nginx lighttpd apache
Answers
Option D is correct. Apache is the most popular web server application.
A web server is software and hardware that responds to client requests sent over the World Wide Web using Hypertext Transfer Protocol (HTTP) and other protocols. A web server's main task is to display the content of a website by storing, processing, and sending web pages to users. A free and open-source web server called Apache HTTP Server delivers web information over the Internet. Often referred to as Apache, shortly after its creation it surpassed all other HTTP clients as the most used HTTP client on the Internet.
Learn more about Server here-
https://brainly.com/question/7007432
#SPJ4
Make each word to its correct meaning baiting click-jacking cross-site scripting
Answers
Answer:
Explanation:
Sure! Here are the correct meanings for the given terms:
1. Baiting: Baiting refers to the act of enticing or luring someone into a trap or a specific action, often through deception or manipulation.
2. Click-jacking: Click-jacking is a technique used by malicious actors to trick users into clicking on a seemingly innocent element or link on a webpage, which actually performs a hidden action or leads the user to unintended destinations. It is designed to deceive and hijack the user's clicks for nefarious purposes.
3. Cross-site scripting: Cross-site scripting (XSS) is a security vulnerability that occurs when an attacker injects malicious scripts into a trusted website or web application. When other users visit the affected site, the injected scripts can execute on their browsers, potentially allowing the attacker to steal sensitive information, perform unauthorized actions, or manipulate the website's content.
I hope this clarifies the meanings of the terms "baiting," "click-jacking," and "cross-site scripting" for you.
Select the education and qualifications that are most helpful for Insurance Services careers. Check all that apply.
leadership skills
critical thinking skills
knowledge of credit systems
research skills
O certification and licensure
bachelor's and master's degrees
Answers
Answer:
critical thinking skills
research skills
certification and licensure
bachelor's and master's degree
Explanation: edge 2020
The education and qualifications that are most helpful for Insurance Services careers are as follows;
Critical thinking skills.Research skills.Certification and license.Bachelor's and master's degrees.Thus, the correct options for this question are B, D, E, and F.
What is the significance of Insurance Services careers?The significance of Insurance Services careers is understood by the fact that it is one of the most lucrative sectors in the entire world. The demand for this sector is rapidly growing. It provides various opportunities in specific countries along with global levels like World Monetary funds, world banks, etc.
It is required for all sectors to have particular criteria and eligibility. So, if you are interested to make your career in Insurance Services you definitely have bachelor's and master's degrees along with certain certifications and licensure.
Therefore, the correct options for this question are B, D, E, and F.
To learn more about Insurance services, refer to the link:
https://brainly.com/question/25855858
#SPJ5
The objectives of a(n) _____ degree typically include the theory, design, and development of computing systems. Question 5 options: a) information technology b) computer science c) information systems d) computer engineering
Answers
Answer:
Computer Science is the correct answer.
who is responsible for information security at Infosys?
Answers
The information security council is responsible for information security at Infosys.
Where can you find the Infosys information security policy?It is accessible by all employees and can be accessed in InfyMe Web under the 'Policy' section within the Information Systems (IS) portal (InfyMe web - > World of Infosys - > Business Units and Subsidiaries - > Information Systems - > Repository - > Policies).
The Information Security Council (ISC) is the governing body at Infosys that focuses on establishing, directing, and monitoring our information security governance framework.
Therefore, the information security council is responsible for information security at Infosys.
To learn more about the Security council, refer to the link:
https://brainly.com/question/97111
#SPJ1
What does else do in an if/else statment?
O Gives the if statement a command to run if the condition is false
O Runs a command regardless of whether the condition is tru or false
O Determines whether the condition is true or false
O Tells the condition which code to run
Answers
Answer:
Gives the if statement a command to run if the condition is false
A technician is performing routine preventative maintenance on a laser printer and has been asked by the client to check the printer's paper feeder for issues.
Which of the following printer parts should the technician check first for problems related to paper feeding? (Select TWO.)
a. Transfer belt
b. Toner cartridge
c. Pickup rollers
d. Tractor feede.
e. Separation pad
f. Print head
Answers
Laser printer and has been asked by the client to check the printer's paper feeder for issues, c. Pickup rollers and e. Separation pad.
Paper jams are usually caused by dirty, worn, or damaged rollers. Paper pickup rollers can be cleaned with alcohol or replaced if they are worn out. Similarly, separation pads can cause paper jams. The separation pad is responsible for ensuring that the paper feed rollers only take one page at a time. If the separation pad is worn or sticky, it will cause multiple pages to be fed through the printer at once. Separation pads can usually be cleaned or replaced if they are worn out.Answer in 200 words:Therefore, the technician should check the pickup rollers and separation pad first for paper feeding issues.
A laser printer has a lot of moving parts that are designed to work together. The paper feeder is one of these parts, and it's crucial to ensure that it's in good working condition. Laser printers are known for their ability to handle a lot of paper, and it's not uncommon for them to be used in environments where they're frequently printing. This means that the paper feeder is likely to get a lot of wear and tear, which can lead to problems like paper jams.If the paper feeder is not working correctly, it can cause paper jams, and it can also damage the printer itself. This is why it's essential to check the paper feeder regularly, and to ensure that it's functioning correctly. The technician should start by checking the pickup rollers and separation pad, as these are the most common causes of paper jams in a laser printer. If the issue is not resolved, the technician may need to investigate other parts of the printer, such as the transfer belt or toner cartridge, but it's essential to start with the paper feeder.
Learn more about printer :
https://brainly.com/question/5039703
#SPJ11
Question 5: Which category best represents: a student has a friend who's
parent is a teacher at their school. The student uses his friend to obtain the
teachers username and password. Grades end up getting changed in the
digital grading system and it is soon discovered that the teacher also has the
same password in their family's online banking system.
A. illegal file sharing
B. software pirating
C. cyber bullying
D. identity theft
E. it's just not right or responsible.
Answers
Answer:
E
Explanation:
it's not right and it is also irresponsible and the teacher shouldn't have used that as her bank details and also that student's mother is Bankrupt by now
How are hyperlinks created and used within a presentation? Check all that apply. Hyperlinks are set to open another source file. Linked files are stored in the same folder location. Hyperlinks are permanently embedded within a slide. Hyperlinks can open websites, files, or other presentations. Hyperlinked content typically cannot be opened by end users. Hyperlinks can be assigned to text, graphics, and other objects.
Answers
Hyperlinks are created and used within a presentation included with another source file. Linked files are stored in the same folder location. It can open websites, and files or be assigned to text, graphics, etc.
What do you mean by presentation?Hyperlinks are created and can be used within a presentation. These are set to open another source file. Linked files are stored in the same folder location.
These can open websites, files, or other presentations and can be assigned to text, graphics, and other objects.
Learn more about Presentation here:
https://brainly.com/question/649397
#SPJ2
Answer:
A, B, D, F
Explanation:
right on edge22
write the home cell of MS Excel.
Answers
Answer:
MS Excel
Explanation:
What is the use of the Mode option shown in the given image?

Answers
The Mode option is used to change how the colors in a particular layer blend with colors that are contained in another layer.
What is Photoshop?Photoshop can be defined as a software program that is designed and developed to enable the use of an artistic process and tools for the creation of art works or graphic designs such as logos.
In a graphic design software such as Adobe Photoshop, the Mode option is used to change how the colors in a particular layer blend with colors that are contained in another layer.
In conclusion, the Mode option is used to blend colors for Photoshop layers.
Read more on layers here: https://brainly.com/question/14354492
What is a word for a loss of quality?
Answers
Answer:
Failing, declining, degenerating, deteriorating, diminishing, fading
Explanation: yep
What are examples of object dependencies? check all that apply. a button with an anchor property a report that is based on a query a macro with conditional formatting a query that uses data from a table a table that underlies the report information a text box control aligned to the edge of a report
Answers
A text box control aligned to the edge of a report is not an example of object dependencies as it does not have any dependencies on other objects in the database.
Object dependencies refer to the relationships between different objects in a Microsoft Access database. Examples of object dependencies include a report that is based on a query, a query that uses data from a table, and a table that underlies the report information. These objects are dependent on each other, as changes to one object may impact the others. Another example of object dependencies is a button with an anchor property, which may be dependent on the form or report it is placed on. A macro with conditional formatting may also have object dependencies if it is linked to a specific form or report. However, a text box control aligned to the edge of a report is not an example of object dependencies as it does not have any dependencies on other objects in the database.
To know more about aligned visit:
https://brainly.com/question/17465619
#SPJ11
Object dependencies are used to identify which objects depend on which other objects. In Microsoft Access, for example, an object dependency is used to determine which forms, reports, and other objects depend on a particular table, query, or other object. There are several examples of object dependencies that are listed below:1. A button with an anchor property: When you create a button with an anchor property, the button will depend on the form or report that it is anchored to. This means that if you change the location or size of the form or report, the button will also be affected.2. A report that is based on a query: If you create a report that is based on a query, the report will depend on the query. This means that if you change the query, the report will also be affected.3. A macro with conditional formatting: If you create a macro with conditional formatting, the macro will depend on the control that you apply the formatting to. This means that if you change the control or remove it from the form or report, the macro will no longer work.4. A query that uses data from a table: If you create a query that uses data from a table, the query will depend on the table. This means that if you change the table, the query will also be affected.5. A table that underlies the report information: If you create a report that is based on a table, the report will depend on the table. This means that if you change the table or its fields, the report will also be affected.6. A text box control aligned to the edge of a report: If you create a text box control that is aligned to the edge of a report, the control will depend on the report. This means that if you change the size or position of the report, the control will also be affected.
#SPJ11
What are the best steps to learn a 2d animation software?
Answers
Answer:
this is the correct answer
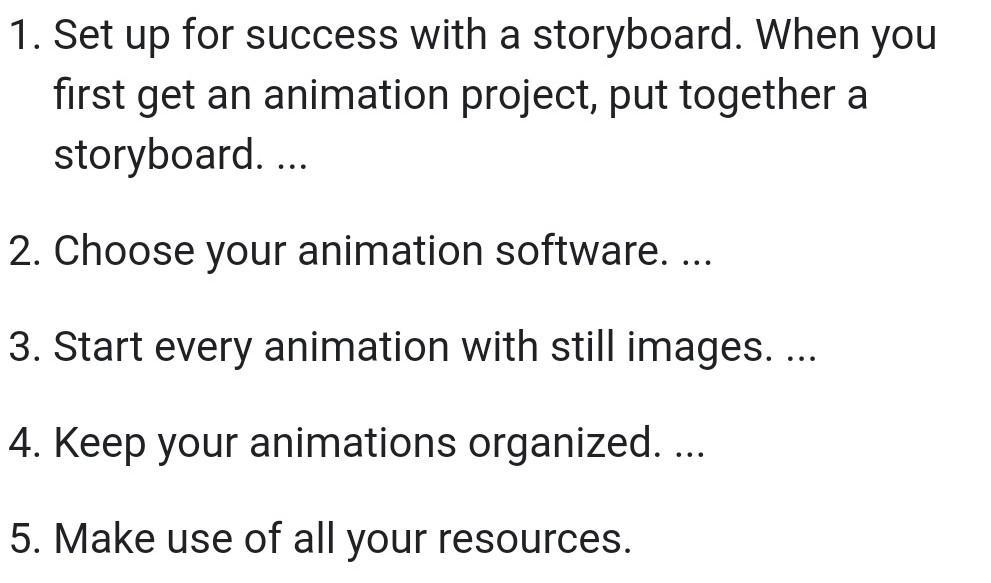
1. Familiarize yourself with the user interface of the software.
2. Read tutorials and watch videos from experts on how to use the software.
3. Practice with simple projects like animations, short films, or motion graphics.
4. Get feedback on your projects from other professionals in the field.
5. Attend online workshops or classes to learn more advanced techniques.
6. Experiment and try different approaches to create unique pieces.
Early versions of HTML supported presentational _____ and presentational attributes designed to describe how each element should be rendered by web browsers.
Answers
Answer: element
Explanation:
Hypertext Markup Language (HTML) is simply is markup language which is standard for documents that is designed so that it'll be displayed in the web browser.
Early versions of HTML supported presentational elements and presentational attributes designed to describe how each element should be rendered by web browsers.
9. in the array version of the stack class (with a fixed-sized array), which operations require linear time for their worst-case behavior? a) is empty b) peek c) pop d) push e) none of these operations require linear time.
Answers
In the array-based stack class, none of these operations require linear time for their worst-case behavior. The stack uses the Last-in-first-out (LIFO) algorithm and is a linear data structure (LIFO).
The stack's implementation using arrays is a technique whereby all operations supported by the stack are carried out using an array as the fundamental data structure. The various operations are:
Push: This operation adds a new item to the stack; if the stack is already full, an exception is thrown.Pop: If the provided stack is empty, it will raise an underflow exception and remove the most recent element from the stack, which is removed in reverse order of when it was inserted.Peek: This action returns the stack's topmost element.IsEmpty: Determines whether or not a stack is empty. If the supplied stack is empty, it returns true; otherwise, it returns false.IsStackFull: Determines whether or not a stack is full. if the specified stack is full, returns true; else, it returns false.To learn more about array-based stack click here:
brainly.com/question/28274775
#SPJ4