Compound expressions are a facet of Boolean logic and are part of most programming languages. Which of the following operators are both examples of Boolean operators used in complex expressions?
A) IF ELSE
B) AND OR
c) LIST REPEAT
D) NOT LOOP
Answers
The Boolean operators used in complex expressions are B) AND OR. The AND and OR operators are commonly used Boolean operators used in complex expressions.
Compound expressions in programming languages involve the use of Boolean operators to evaluate multiple conditions at once. Boolean logic involves the use of true/false values to make logical decisions. The IF ELSE operator is used to conditionally execute code based on a single condition. It is not a Boolean operator used in complex expressions.
The AND operator evaluates to true only if both conditions being compared are true. The OR operator evaluates to true if either of the conditions being compared are true. AND and OR are both Boolean operators used in complex expressions. These operators are a part of Boolean logic and are widely used in programming languages for making decisions and comparisons between true and false values.
To know more about Boolean operators visit:
https://brainly.com/question/26680966
#SPJ11
Related Questions
write a statement that declares a real number variable hours and assigns it to the value returned from a call to the method getdouble. the method takes no parameters and returns a double.
Answers
Declares a double variable "hours" and assigns it the value returned by "getDouble()" method with no parameters.
This statement declares a double variable called "hours" and assigns it the value returned from the "getDouble()" method. The method takes no parameters and returns a double value, which is then assigned to the "hours" variable. The "getDouble()" method is likely a custom method defined elsewhere in the code, or it could be a built-in method from a library. In this statement, we're using the data type "double" to declare the variable "hours". This data type is used to store decimal numbers with a high degree of precision. By assigning the value returned from the "getDouble()" method to this variable, we're able to store and use that value elsewhere in the code.
Overall, this statement is a simple example of how to declare and assign a variable in Java, using a method that returns a double value.```
learn more about double variable hours here:
https://brainly.com/question/21663764?
#SPJ11
Declares a double variable "hours" and assigns it the value returned by "getDouble()" method with no parameters.
This statement declares a double variable called "hours" and assigns it the value returned from the "getDouble()" method. The method takes no parameters and returns a double value, which is then assigned to the "hours" variable. The "getDouble()" method is likely a custom method defined elsewhere in the code, or it could be a built-in method from a library. In this statement, we're using the data type "double" to declare the variable "hours". This data type is used to store decimal numbers with a high degree of precision. By assigning the value returned from the "getDouble()" method to this variable, we're able to store and use that value elsewhere in the code.
Overall, this statement is a simple example of how to declare and assign a variable in Java, using a method that returns a double value.```
learn more about double variable hours here:
https://brainly.com/question/21663764?
#SPJ11
Mr. Simmons has assigned a research project. Every student in the class will create a single page report about the recycling habits of an assigned state. The individual reports will then be combined to form a single 50 page reference manual. What can Mr. Simmons require each student use so that all page layouts follows a consistent style
Answers
Answer: template
Explanation:
In order for each student to have a page layout that follows a consistent style, then the students should have a template.
A template refers to a predesigned document that can be used can to create documents without having to think about formatting. When a template is used, the margin size, spacing, font style, etc are predetermined.
A ________ is represented by a 0 or 1.
Question content area bottom
Part 1
A.
bit
B.
megabit
C.
file
D.
kilobyte
E.
byte
Answers
Answer:
A. Bit
Explanation:
Everything in a computer is 0's and 1's. The bit stores just a 0 or 1: it's the smallest building block of storage.
A bit is represented by a 0 or 1. Bit is the smallest unit of data in a computer system, consisting of either a 0 or 1. Bit is also the short form of binary digit, which is either of the two digits (0 or 1) represented in binary notation.In computing and digital communication, a bit is the smallest unit of data that can be processed.
It can be used to represent two distinct values, such as Yes/No or True/False. A byte, on the other hand, is a collection of bits (usually eight bits) that represents a single character or other data element in a computer system.Therefore, the correct option is A. bit.
This standard is often used as a benchmark for measuring performance and identifying areas for improvement. On the other hand, a realistic standard is one that is achievable with reasonable effort and resources, and takes into account factors such as time, budget, and available resources.
To know more about smallest visit:
https://brainly.com/question/2505055
#SPJ11
30 POINTS PLS HURRY
Choose the correct phrase to complete the sentence.
Being interconnected through technology means that .
A.there are more risks involved than benefits
B. our lives are less complicated than ever before
C. the benefits of technology also bring risks
D. we live with more freedom than ever before
Answers
Answer:
the answer is the benefits of technology also brings risks
Explanation:
The correct phrase to complete the sentence is the benefits of technology also bring risks. The correct option is C.
What is technology?Technology is the application of knowledge to the attainment of realistic objectives in a repeatable manner.
The term "technology" can also refer to the end results of such endeavors, encompassing both material instruments like machinery or utensils and immaterial ones like software.
People may now communicate with each other and obtain information from all over the world more easily thanks to technology.
There are potential disadvantages associated with this increasing connectivity and reliance on technology, such as security issues, privacy problems, and detrimental effects on mental health.
Hence, it is important to properly handle the hazards that frequently accompany the advantages of technology.
Thus, the correct option is C.
For more details regarding technology, visit:
https://brainly.com/question/9171028
#SPJ2
when inserting a hyperlink, what can you link to? select all that apply.
Answers
When inserting a hyperlink, you can link to the following:
An email addressA place in the current document.A fileA webpageA hyperlink can be defined as an element in a hypertext markup language (HTML) document that provides a link or direct access to another document, webpage, location, file, and an image.
Basically, a hyperlink can be used to directly link to the same path in a HTML document or another HTML document. Also, the text contained in a hyperlink is usually highlighted and it is only activated by a click.
In Computer programming, you can insert a hyperlink to directly link to the following:
An email addressA place in the current document.A fileA webpageIn conclusion, a typical example of a hyperlink on a webpage is demonstrated below;
Read more on hyperlink here: https://brainly.com/question/25760645
_________ is pestware that users your computer as a launch pad for unsolicited e-mail, usually advertising for products and services.
Answers
Spamware is pestware that users your computer as a launch pad for unsolicited e-mail, usually advertising for products and services.
What Exactly Is Spamware?A piece of software called spamware was created by spammers with spamming in mind. Spamware offers an automatic email broadcasting solution and lets a user search, sort, and generate a list of email addresses. Unsuspecting recipients may get spam or unsolicited emails using this method.
Note that not all bulk email software is spamware since email listserver software can be used for things other than sending spam.
Therefore, one can say that Software created by or for spammers is known as spamware. Spamware comes in many different forms, but some may have features like the ability to import tens of thousands of addresses, create random addresses, add phony headers to messages, use dozens or even hundreds of mail servers at once, and use open relays.
Learn more about Spam from
https://brainly.com/question/28096829
#SPJ1
the mrp program accesses the status segment of the record according to specific time periods called in mrp slang.
Answers
In MRP (Material Requirements Planning), the specific time periods in which the MRP program accesses the status segment of the record are commonly referred to as "time buckets" in MRP terminology.
Time buckets in MRP are intervals or divisions of time that are used to analyze and track the status of material requirements. These buckets represent specific time periods, such as days, weeks, or months, and are used to organize and aggregate data related to material planning and scheduling.
By dividing time into these predefined buckets, the MRP program can effectively manage and monitor the demand, supply, and inventory levels of materials within each time period. It allows for the analysis of material requirements over different time horizons and facilitates planning and decision-making based on the aggregated information within each bucket.
For example, if the time bucket is set to one week, the MRP program will access the status segment of the record for each week and evaluate the demand and supply data for materials during that specific week. It helps in determining the material requirements, such as the quantity to be ordered or produced, based on the demand forecasts and available inventory.
Overall, time buckets in MRP enable the program to break down time into manageable units and facilitate effective planning, control, and optimization of material requirements based on specific time intervals.
learn more about data here:
https://brainly.com/question/21927058
#SPJ11
UHM, THIS IS A VERY IMPORTANT QUESTION!!!
My cords in my house are heating up REALLY FAST. Any idea what will hapen ro how to stop it?!?!
Answers
Answer:
Maybe you can check if there is a instant power source going to the wires
or you can check for a resistor?
Explanation:
i think this could help
Answer:
unplug the cords!
Explanation:
call the fire department if ANYTHING goes wrong!
How do I separate ones, tens, hundreds, and thousands from a four-digit user input in C programming?
Answers
We may therefore simplify it by applying modulo 10. Like, \s12 % 10 => 2 ( we have split the digit 2 from number 12) ( we have split the digit 2 from number 12) The number 12 must now be divided by ten to get the digit one: 12/10 = 1. Now, take 10 modulo. 1 % 10 = 1.
What is C programming?A universal computer programming language is C. Dennis Ritchie developed it in the 1970s, and it is still heavily utilized and regarded as important. By design, C's features neatly reflect the CPUs it is intended to run on. C++ offers a much increased number of libraries and functions when compared to C. Because there are more libraries available in C++, it is a better choice if you're dealing with complicated software. C++ proficiency is frequently a necessity for a number of programming professions, to put it simply. The majority of C++ is a subset of C. A superset of C is C++ (mainly). C provides procedural programming for the creation of code. Due to its support for both procedural and object-oriented programming paradigms, C++ is regarded as a hybrid language.To learn more about C programming refer to:
https://brainly.com/question/26535599
#SPJ4
How do you access the dark web? What are the negatives of doing this?
Answers
Write a method that takes a parameter for the number of a month and prints the month's name. You may assume that the actual parameter value passed to the method is always between 1 and 12 inclusive.
This method must be called monthName() and it must have an integer parameter.
Calling monthName(8) should print August to the screen.
Answers
Answer:
Get month number from month name
Use Java's Calendar class. It can parse any given string into a valid calendar instance. Here is an example (assuming that the month is in english). Date date = new SimpleDateFormat("MMMM").parse(monthName); Calendar cal = Calendar.getInstance(); cal.setTime(date); println(cal.get(Calendar.MONTH)); You can specify the language in SimpleDateFormat: String monthName = "März"; // German for march Date date = new SimpleDateFormat("MMMM", Locale.GERMAN).parse(monthName); Calendar cal = Calendar.getInstance(); cal.setTime(date); println(cal.get(Calendar.MONTH)); By default, Java uses the user's local to parse the string. Keep in mind that a computer starts counting at 0. So, January will be 0. If you want a human readable date, you should format the calendar instance: SimpleDateFormat inputFormat = new SimpleDateFormat("MMMM"); Calendar cal = Calendar.getInstance(); cal.setTime(inputFormat.parse(monthName)); SimpleDateFormat outputFormat = new SimpleDateFormat("MM"); // 01-12 printlng
MARK ME BRAINIEST FOR MORE INFO
What security factors do companies need to consider when buying an operating system?
Answers
Answer:
What they can do to prevent malware and hacking.
Explanation:
They would want the ability to have high security including strong firewalls and a minimal amount of loopholes in the OS itself. A company can't always rely on a patch to come through and would instead need something guaranteed to be nearly perfectly secure. For this reason, some companies choose Linux or Unix.
If you want to open the Navigation pane to do a Find, what should you first click on the Home tab? Paragraph, Editing, Styles, or View
Answers
Answer:
You would first click view.
Explanation:
hope this helps
Answer:
editing (b)
Explanation:
Assignment 1
Q: In this course, you will be creating an advertising campaign
for an existing product or company-you will not be creating
a new product or company.
An advertising campaign Is created to
Answers
An advertising campaign is created to make a product, service, or brand more popular among the target audience. Its primary aim is to persuade or encourage a specific group of people to buy or take some action toward a product, service, or brand.
In this course, you will be creating an advertising campaign for an existing product or company; you will not be creating a new product or company.
The advertising campaign includes a series of coordinated marketing activities that help to achieve specific business objectives.
These activities can include various forms of media such as print, television, radio, online, and social media.
The advertising campaign is generally created by a team of creative professionals who work to develop a message that is engaging, relevant, and persuasive.
The advertising campaign generally includes a theme or tagline, creative visuals, a target audience, a unique selling proposition, and a specific call to action.
Read more about An advertising campaign.
https://brainly.com/question/11698706
#SPJ11
Which of the following are server types that a sysadmin for a small company might manage?
- SSH
- Email
- SSD
- VR
Answers
The server types that a sysadmin for a small company might manage are SSH and Email.
SSH, or Secure Shell, is a network protocol that provides remote access to a computer or server in a secure manner. It is often used by system administrators to remotely administer servers, allowing them to securely conduct command-line operations on a server from a distant location.
In contrast, email servers enable users to send, receive, and store emails. A sysadmin is usually in charge of configuring and administering the company's email server, ensuring that it is properly setup, maintained, and secure.
As a result, SSH and Email are the server kinds that a sysadmin for a small business may administer.
To learn about, Email Spoofing, visit:
https://brainly.com/question/23021587
During the game, the quotes helped by enabling you to use Multiple Choice over-the-top processing. top-down processing. bottom-up processing. in-through-the-out-door processing.
Answers
Answer:
top-down processing.
Explanation:
Array must be initialized with a brace-enclosed initializer.
a. true
b. false
Answers
It is TRUE to state that Array must be initialized with a brace-enclosed initializer.
What is the explanation for the above?In many programming languages, including C++, arrays must be initialized with a brace-enclosed initializer. This initializer specifies the initial values of the elements in the array. For example, to initialize an array of integers in C++, you might use code like this:
int myArray[] = {1, 2, 3, 4, 5};
This initializes an array with 5 elements, with the values 1, 2, 3, 4, and 5. Without the brace-enclosed initializer, it is not clear what the initial values of the array elements should be.
Learn more about Array at:
https://brainly.com/question/30757831
#SPJ1
a user cannot delete one of their files but is able to delete other files in their directory. john, a system administrator, is attempting to troubleshoot this issue. what command should he use first on the file?
Answers
The first command John should use is the ls -l command to check the file's permissions and ownership.
The output of this command will show the file permissions and the owner of the file. John can check whether the user has the appropriate permissions to delete the file or if the file ownership needs to be changed. If the file is owned by another user or group, John may need to change the ownership of the file to the user who wants to delete it. If the file permissions are incorrect, John may need to use the chmod command to modify the permissions of the file so that the user can delete it.
You can learn more about command at
https://brainly.com/question/31624655
#SPJ11
PLEASE ANSWER FAST IM TIMED
A WYSIWYG editor will save time and make the process of Web site design an artistic practice rather than a ------- practice.
Answers
This open source software helps you either create a website through code, or design it with the help of templates and facile customizations.
What is the difference between HTML and WYSIWYG?A WYSIWYG editor shows you a rendered web page as you edit the page. You do not see the actual HTML. When using manual coding, you see the HTML, but you must load the document in a web browser to view the rendered page.
Is WYSIWYG easy to use?An efficient free WYSIWYG Editor comes with an easy-to-use toolbar, keyboard shortcuts, and other features that allow you to easily add or edit content, images, videos, tables, or links. A WYSIWYG editor saves time and makes web content creation quick and easy.
To know more about WYSIWYG visit:
https://brainly.com/question/12340404
#SPJ1
Answer:
Programming
Explanation:
WYSIWYG (sometimes pronounced "wizzy wig") is an acronym that stands for "What You See Is What You Get." It is a phrase that was coined when most word processing, desktop publishing, and typesetting programs were text and code based. HTML, at its code level, is much like the early interfaces on this sort of software. A WYSIWYG editor saves time and makes the process of website design an artistic practice rather than a programming practice.
Wesellyoubuy, a consumer electronics company, received consumer complaints about its employees not being able to communicate with consumers properly. After investigating the prime reason behind these complaints, the management found that the consumer service employees were following the same strategy to address all types of consumer issues. The management immediately started a new training program for the consumer service employees where they were trained to respond to every possible query a consumer might have. Eventually, their service ratings and sales showed improvement. In this scenario, the consumer service team improved _____.
Answers
Answer:
customer satisfaction
Explanation:
The consumer electronics company started a new training program for the consumer service employees as the company found that the consumer service employees were following the same strategy to address all types of consumer issues due to which they were not able to communicate with consumers properly.
This leads to improvement in service ratings and sales.
In this scenario, the consumer service team improved customer satisfaction
The goal of a system is to
a) be natural or human-made
b) use energy
c) perform a task
d) be social or physical
Answers
Answer:
d it is d I know cause I answered it on a test I had
hope it helps
please can someone help me with this?

Answers
Explanation:
there fore 36:4 = m¤
46:6
20:16
#von5
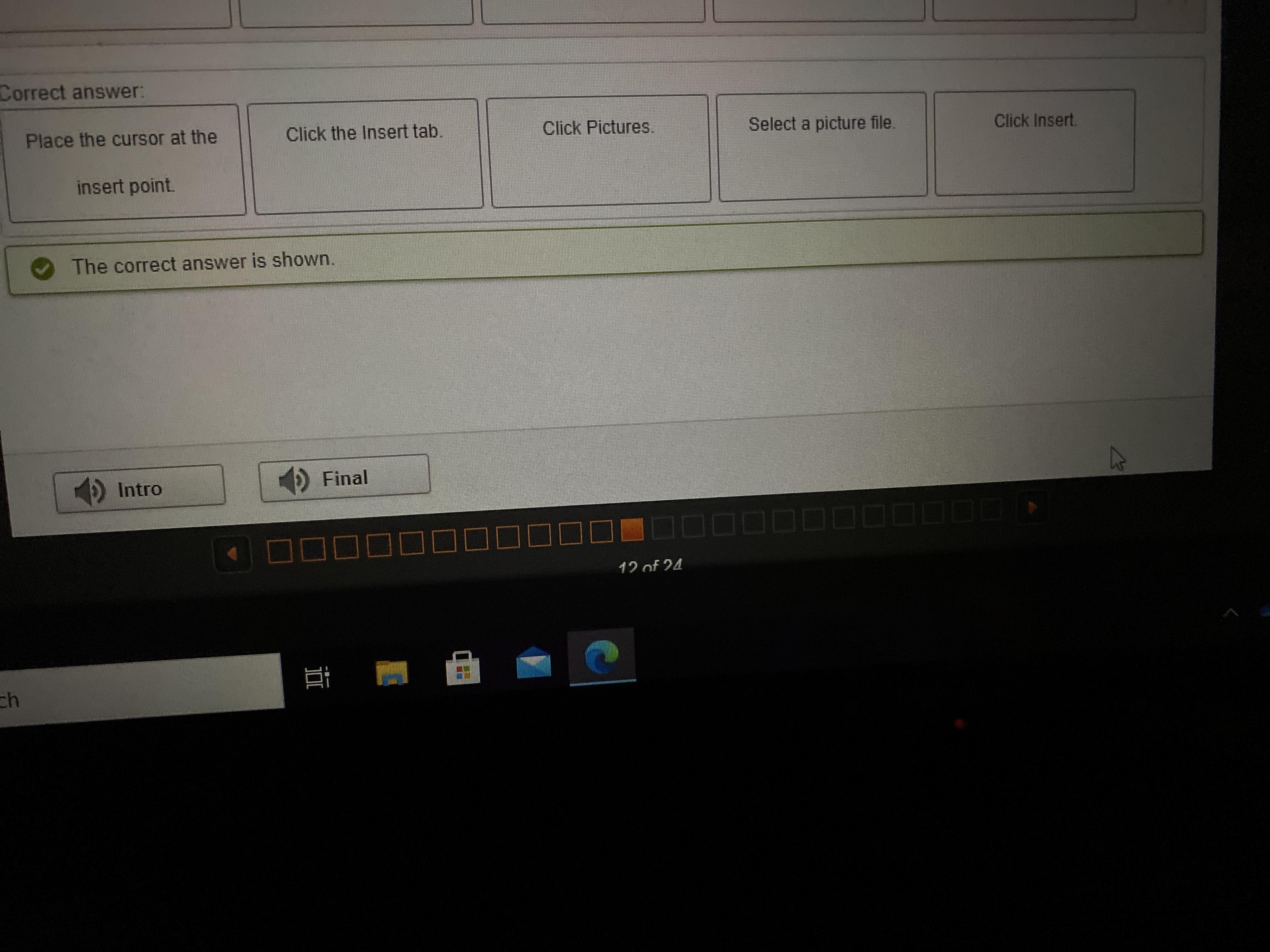
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
Identify the true statements about collaboration software. Multiple select question. Provides and online work site to post share and save data. Promotes highly interdependent interactions. Used for face-to-face communication. Provides an electronic meeting site
Answers
The true statements about collaboration software are:
Provides an online work site to post, share, and save data.Promotes highly interdependent interactions.Provides an electronic meeting site.What is collaboration software?Collaboration computer program may be a sort of computer program that empowers clients to work together on a extend or task, regardless of their area. It gives a web workspace for clients to post, share, and spare information, which promotes exceedingly forbid intuitive among group individuals.
One of the most highlights of collaboration computer program is that it gives an electronic assembly location where group individuals can communicate and share data.
Learn more about collaboration software from
https://brainly.com/question/28482649
#SPJ1
Why would desktop be better for classrooms instead of laptops
Answers
Answer:
A quality desktop or laptop PC prepares your children for the skills they need to function as productive adults in our tech-savvy world. The convenience of a laptop is undeniable, but desktop PC is great if you want more computing power for the price.
Explanation:
can someone pelaseee help

Answers
Answer:
Explanation:
develloppemetn de grace en option est logiquement une biologiste experimenter des annes 1256 a toulouse en france
This question has two parts : 1. List two conditions required for price discrimination to take place. No need to explain, just list two conditions separtely. 2. How do income effect influence work hours when wage increases? Be specific and write your answer in one line or maximum two lines.
Answers
Keep in mind that rapid prototyping is a process that uses the original design to create a model of a part or a product. 3D printing is the common name for rapid prototyping.
Accounting's Business Entity Assumption is a business entity assumption. It is a term used to allude to proclaiming the detachment of each and every monetary record of the business from any of the monetary records of its proprietors or that of different organizations.
At the end of the day, we accept that the business has its own character which is unique in relation to that of the proprietor or different organizations.
Learn more about Accounting Principle on:
brainly.com/question/17095465
#SPJ4
3.1. in pam encoding, the general rule is that we need to sample at twice the bandwidth. in addition, if we use n bits for each sample, we can represent 2n loudness (amplitude) levels. what transmission speed would you need if you wanted to encode and transmit, in real time and without compression, two-channel music with a bandwidth of 22 khz and 1000 loudness levels? (10 points) note: the sampling size, in bits, must be an integer. to minimize quantizing errors, it is customary to select a sampling rate that is twice as much as the signal bandwidth. 3.2. how much disk space would you require to store 1 minutes of digital music as you calculated above? (10 points)
Answers
3.1) Transmission speed would you need if you wanted to encode and transmit, in real time and without compression is 640kbps.
3.2) 137.33MB disk space would required to store 1 minutes of digital music.
What is transmission speed?
The rate at which data packets travel a computer network from one server to another is referred to as transmission speed.
3.1) According to the inquiry, the bandwidth is 20 kHz.
The bandwidth will be doubled using Nyquist sampling.
So, bandwidth = 2 × 20 kHz= 40 kHz.
Loudness level = 40, 000 that is log₂ (40,000)~ 16 bits for each samples transmitted.
Now compute the transmission speed using the below way
Transmission speed = 16 bits × 40 kHz
= 640 kbps
Therefore, transmission speed is 640 kbps.
3.2) 30 minutes must be saved from the given question.
Now convert the given minutes to seconds that is 30 minutes × 60 sec = 1800 sec.
The disc space required to store 30 minutes of digital music is listed below.
= transmission speed × 1800 sec.
=640kbps ×1800sec
=640×1000bps × 1800 sec (that is 1kbps=1000bps)
=1152000000bits
1152000000/8 bytes (For convert bits to bytes)
=144000000bytes
144000000/1024 KB (For convert bytes to kilobytes)
=140625KB
=140625/1024MB (For convert kilobytes to mega bytes)
=137.33MB
Therefore, disk space for storing 30 minutes of digital music is 137.33 MB.
To learn more about transmission speed
https://brainly.com/question/13013855
#SPJ4
Which of the following is not a security strategy?
Question 12 options:
A) A. Defense diversity
B) B. Firewall policies
C) C. Weakest link
D) D. Forced universal participation
Answers
Forced universal participation is not a security strategy.
Security strategies are essential for protecting computer systems and data from unauthorized access or damage. There are several security strategies that organizations use to safeguard their information.
One security strategy is defense diversity. This involves implementing multiple layers of security to protect against different types of threats. By using a combination of firewalls, antivirus software, intrusion detection systems, and other security measures, organizations can create a more robust defense against potential attacks.
Another security strategy is firewall policies. Firewalls are a crucial component of network security. They act as a barrier between a trusted internal network and an untrusted external network, filtering incoming and outgoing network traffic based on predefined rules. Firewall policies define these rules and determine which types of traffic are allowed or blocked.
The weakest link is another security strategy. It involves identifying and strengthening the most vulnerable areas of a system. This could include patching software vulnerabilities, implementing strong authentication mechanisms, or training employees on security best practices.
However, forced universal participation is not a security strategy. It is a concept that refers to ensuring all users comply with security measures. This can include enforcing password policies, requiring regular security training, and monitoring user activity to detect any suspicious behavior.
Learn more:About security strategy here:
https://brainly.com/question/29888542
#SPJ11
Forced universal participation is not a security strategy.
Explanation: Forced universal participation is not a security strategy. Security is designed to provide the authorized and legitimate user access while keeping unauthorized individuals out. Security policies and plans should be used to help maintain a consistent level of security throughout the organization and manage security risks.
The following are security strategies:
A. Defense diversity: This is the use of multiple security measures to protect a system. It ensures that a single vulnerability cannot be exploited.
B. Firewall policies: A firewall is used to create a barrier between a trusted internal network and an untrusted external network.
C. Weakest link: This refers to identifying and securing the weakest point in a system. This would help to prevent attackers from entering the system.
D. Forced universal participation: This is not a security strategy.
Learn more about Organization here,https://brainly.com/question/19334871
#SPJ11
A _____ is a large group of infected computers, controlled without the user's knowledge, to perform tasks such as sending spam.
Answers
A large group of infected computers, controlled without the user's knowledge, to perform tasks such as sending spam is called; botnet
To answer this question, we need to first define an internet bot. An Internet bot is simply defined as a software application that runs tasks in an automated manner over the Internet.
Now, a number of connected internet devices that run one or more bots is referred to as a botnet and this botnet tends to control tasks on the infected computers without the user's knowledge.
Read more on botnets at; https://brainly.com/question/13624552