Cloned virtual machines can be used for all except:
Answers
Cloned virtual machines can be used for a variety of purposes, but there are some limitations and considerations to keep in mind. Some of the common uses for cloned virtual machines include:
Testing and development: Cloned virtual machines can be used to create multiple instances of an operating system or application for testing and development purposes.Disaster recovery: Cloned virtual machines can be used to create backup copies of critical systems, which can be quickly deployed in the event of a system failure or disaster.Load balancing: Cloned virtual machines can be used to distribute workloads across multiple instances of an application or service, improving performance and availability.Security: Cloned virtual machines can be used to create isolated environments for testing security policies, penetration testing, or malware analysis.
To learn more about machines click the link below:
brainly.com/question/28259307
#SPJ11
Related Questions
30 points!!! Due Tomorrow. ICT test on memory, CPU, motherboard and dedicated/embedded systems and general purpose systems. Any tips?
Answers
Answer:
Just get it right and don't get stressed
Explanation:
An embedded system is a computer system—a combination of a computer processor, computer memory, and input/output peripheral devices—that has a dedicated function within a larger mechanical or electronic system.[1][2] It is embedded as part of a complete device often including electrical or electronic hardware and mechanical parts. Because an embedded system typically controls physical operations of the machine that it is embedded within, it often has real-time computing constraints. Embedded systems control many devices in common use today.[3] In 2009 it was estimated that ninety-eight percent of all microprocessors manufactured were used in embedded systems.[4]
Which of the following is hardware or software that monitors and controls network traffic to prevent security breaches?
O trojan horse
O firewall
O anti-malware
O keylogger
Need answer now!!!!!
Answers
Answer:
Firewall
Explanation:
A trojan horse and keylogger are types of malware. While an anti-malware software may come with a firewall built in, the firewall is still the thing monitoring network traffic.
an intrusion detection and prevention system is one that determines whether activity is present that is contrary to organization policy and represents a(n) .
Answers
The Intrusion detection system is the one that works on detection and prevention systems and determines whether the activity is present that is contrary to organization policy.
What do you mean by an Intrusion detection system?
A monitoring system called an intrusion detection system (IDS) looks for abnormal activity and sends out alarms when it does. A security operations centre (SOC) analyst or incident responder can analyse the problem and take the necessary steps to eliminate the threat based on these notifications.
What is SOC?
The goal of the security operations centre (SOC) is to continuously monitor, stop, detect, look into, and react to cyber-attacks.
Intrusion detection and prevention system (IDPS) is the collective name for a set of hardware and software that checks for the presence of activity that is against organisational rules and constitutes an intrusion.
Hence, a(n) reprsents the intrusion.
To learn more about the SOC from the given link
https://brainly.com/question/15072085
#SPJ4
At which of the OSI layers IP addressing takes place?
1) Layer 3
2) Layer 1
3) Layer 4
4) Layer 6
Answers
IP addressing takes place at Layer 3 of the 000000 which is also known as the Network Layer. This layer is responsible for logical addressing and routing of data packets across different networks. It uses IP addresses to uniquely identify devices and manage the best path for data to travel from the source to the destination. Some of the key functions of the Network Layer include determining the best route for data transmission, forwarding packets, and handling congestion control.
The OSI model consists of seven layers, each with a specific set of responsibilities. These layers work together to facilitate the end-to-end communication process across networks. The other layers in the OSI model are:
1) Layer 1 - Physical Layer: This layer deals with the physical aspects of data transmission, such as cables, switches, and hubs.
2) Layer 2 - Data Link Layer: This layer is responsible for organizing data into frames and managing error detection, flow control, and media access control.
3) Layer 4 - Transport Layer: This layer ensures reliable data transfer, managing error detection, flow control, and retransmission of lost data.
4) Layer 5 - Session Layer: This layer manages communication sessions between devices, including establishing, maintaining, and terminating connections.
5) Layer 6 - Presentation Layer: This layer is responsible for data formatting, translation, encryption, and compression.
6) Layer 7 - Application Layer: This layer deals with user interfaces, such as web browsers and email clients, and facilitates user interaction with network applications.
In summary, IP addressing takes place at Layer 3 (Network Layer) of the OSI model, which plays a crucial role in routing and managing data communication across networks.
Learn more about IP here:
https://brainly.com/question/16011753
#SPJ11
python
how do I fix this error I am getting
code:
from tkinter import *
expression = ""
def press(num):
global expression
expression = expression + str(num)
equation.set(expression)
def equalpress():
try:
global expression
total = str(eval(expression))
equation.set(total)
expression = ""
except:
equation.set(" error ")
expression = ""
def clear():
global expression
expression = ""
equation.set("")
equation.set("")
if __name__ == "__main__":
gui = Tk()
gui.geometry("270x150")
equation = StringVar()
expression_field = Entry(gui, textvariable=equation)
expression_field.grid(columnspan=4, ipadx=70)
buttonl = Button(gui, text=' 1', fg='black', bg='white',command=lambda: press(1), height=l, width=7)
buttonl.grid(row=2, column=0)
button2 = Button(gui, text=' 2', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button2.grid(row=2, column=1)
button3 = Button(gui, text=' 3', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button3.grid(row=2, column=2)
button4 = Button(gui, text=' 4', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button4.grid(row=3, column=0)
button5 = Button(gui, text=' 5', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button5.grid(row=3, column=1)
button6 = Button(gui, text=' 6', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button6.grid(row=3, column=2)
button7 = Button(gui, text=' 7', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button7.grid(row=4, column=0)
button8 = Button(gui, text=' 8', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button8.grid(row=4, column=1)
button9 = Button(gui, text=' 9', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button9.grid(row=4, column=2)
button0 = Button(gui, text=' 0', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
button0.grid(row=5, column=0)
Add = Button(gui, text=' +', fg='black', bg='white',command=lambda: press("+"), height=l, width=7)
Add.grid(row=2, column=3)
Sub = Button(gui, text=' -', fg='black', bg='white',command=lambda: press(2), height=l, width=7)
Sub.grid(row=3, column=3)
Div = Button(gui, text=' /', fg='black', bg='white',command=lambda: press("/"), height=l, width=7)
Div.grid(row=5, column=3)
Mul = Button(gui, text=' *', fg='black', bg='white',command=lambda: press("*"), height=l, width=7)
Mul.grid(row=4, column=3)
Equal = Button(gui, text=' =', fg='black', bg='white',command=equalpress, height=l, width=7)
Equal.grid(row=5, column=2)
Clear = Button(gui, text=' Clear', fg='black', bg='white',command=clear, height=l, width=7)
Clear.grid(row=5, column=1)
Decimal = Button(gui, text=' .', fg='black', bg='white',command=lambda: press("."), height=l, width=7)
buttonl.grid(row=6, column=0)
gui.mainloop()
Answers
Answer:
from tkinter import *
expression = ""
def press(num):
global expression
expression = expression + str(num)
equation.set(expression)
def equalpress():
try:
global expression
total = str(eval(expression))
equation.set(total)
expression = ""
except:
equation.set(" error ")
expression = ""
def clear():
global expression
expression = ""
equation.set("")
if __name__ == "__main__":
gui = Tk()
equation = StringVar(gui, "")
equation.set("")
gui.geometry("270x150")
expression_field = Entry(gui, textvariable=equation)
expression_field.grid(columnspan=4, ipadx=70)
buttonl = Button(gui, text=' 1', fg='black', bg='white',command=lambda: press(1), height=1, width=7)
buttonl.grid(row=2, column=0)
button2 = Button(gui, text=' 2', fg='black', bg='white',command=lambda: press(2), height=1, width=7)
button2.grid(row=2, column=1)
button3 = Button(gui, text=' 3', fg='black', bg='white',command=lambda: press(3), height=1, width=7)
button3.grid(row=2, column=2)
button4 = Button(gui, text=' 4', fg='black', bg='white',command=lambda: press(4), height=1, width=7)
button4.grid(row=3, column=0)
button5 = Button(gui, text=' 5', fg='black', bg='white',command=lambda: press(5), height=1, width=7)
button5.grid(row=3, column=1)
button6 = Button(gui, text=' 6', fg='black', bg='white',command=lambda: press(6), height=1, width=7)
button6.grid(row=3, column=2)
button7 = Button(gui, text=' 7', fg='black', bg='white',command=lambda: press(7), height=1, width=7)
button7.grid(row=4, column=0)
button8 = Button(gui, text=' 8', fg='black', bg='white',command=lambda: press(8), height=1, width=7)
button8.grid(row=4, column=1)
button9 = Button(gui, text=' 9', fg='black', bg='white',command=lambda: press(9), height=1, width=7)
button9.grid(row=4, column=2)
button0 = Button(gui, text=' 0', fg='black', bg='white',command=lambda: press(2), height=1, width=7)
button0.grid(row=5, column=0)
Add = Button(gui, text=' +', fg='black', bg='white',command=lambda: press("+"), height=1, width=7)
Add.grid(row=2, column=3)
Sub = Button(gui, text=' -', fg='black', bg='white',command=lambda: press("-"), height=1, width=7)
Sub.grid(row=3, column=3)
Div = Button(gui, text=' /', fg='black', bg='white',command=lambda: press("/"), height=1, width=7)
Div.grid(row=5, column=3)
Mul = Button(gui, text=' *', fg='black', bg='white',command=lambda: press("*"), height=1, width=7)
Mul.grid(row=4, column=3)
Equal = Button(gui, text=' =', fg='black', bg='white',command=equalpress, height=1, width=7)
Equal.grid(row=5, column=2)
Clear = Button(gui, text=' Clear', fg='black', bg='white',command=clear, height=1, width=7)
Clear.grid(row=5, column=1)
Decimal = Button(gui, text=' .', fg='black', bg='white',command=lambda: press("."), height=1, width=7)
Decimal.grid(row=6, column=0)
gui.mainloop()
Explanation:
I fixed several other typos. Your calculator works like a charm!

In three to five sentences, describe how Linux is different from other operating systems.
Answers
Answer:
Linux is an open source operating system whereas Windows OS is commercial. Linux has access to source code and alters the code as per user need whereas Windows does not have access to the source code. In Linux, the user has access to the source code of the kernel and alter the code according to his need.
ProjectStem/Python 3.7 Code Practice:
When we read code and predict its output, it is called tracing code.
For this lesson, you will come up with your own challenging algorithm for other students to trace. It must contain at least 4 if statements, 1 else statement and use at least one and or or boolean condition.
Note: Elif statements will not count - your statements must be if statements. Each if statement should use a unique variable name.
For this challenge, try reading 3 or 4 of your classmates' code as well. Trace their code and predict what it will output, then check the code by running it to see if you got it right, and submit your work for a grade.

Answers
Using the codes in computational language in python it is possible to write a code that Trace their code and predict what it will output, then check the code by running it to see if you got it right.
Writting the code:num = 100
if num < 20:
print('Less than 20')
if num < 30:
print('Less than 30')
if num < 40:
print('Less than 40')
if num < 50:
print('Less than 50')
if num > 100 or num == 100:
print('More than or equal to 100')
See more about python at brainly.com/question/18502436
#SPJ1

a packet analyzer is a program that can enable a hacker to do all of the following except ________.
Answers
A packet analyzer is a computer network that has the ability to intercept and log traffic that flows through the network of a computer. A packet analyzer is a program that can enable a hacker to do all of the following except;
D) Launch a denial of service (DoS) attack on your computerSince it is able to read and capture the raw data moving through a network, hackers can use a packet analyzer to decode the details in a user's debit card.
Identity theft can be executed and passwords can be captured using this program.
However, the computer's network cannot be shut down with this program. Therefore, option D is right.
Options:
A) Use your debit card information to purchase items illegally
B) Assume your identity
C) Steal your logons and passwords for various accounts
D) Launch a denial of service (DoS) attack on your computer
Learn more here:
https://brainly.com/question/14390016
20 Points!
Select the correct answer.
Look at this web page from the National Oceanic and Atmospheric Administration’s (NOAA) website. How does the page use contrast?
a web page on the NOAA website
A.
by providing a search box for users
B.
by using a consistent type of font for all text
C.
by using an image of an actual school of fish
D.
by using lighter font against a darker background

Answers
Answer:
By using lighter font against a darker background
Explanation: Contrast, the state of being strikingly different from something else in juxtaposition or close association! Or opposites for short!
nikko wants to applause presentation on the internet he wanted to make sure that all his audience can access in understand is presentation especially that he has a customer that is color blind with that in mind how should look the best present his lie on the web. please
Answers
Answer:
so if you are aiming to create a color blind friendly palette try to use only two basic hue:blue and red(orange and yellow will also fit). the other colors should be made out of these two hues
Complete the following sentences by choosing the best answer from the drop-down menus. A/an _______ is a device used to protect computer against surges and spikes in power. Sleep and Hibernate are examples of _______. Regular maintenance on a computer is good for _______. Bad sectors are sections of the _______ that are physically damaged. To protect some devices such as flash drives and external hard drives from corruption, it’s best to _______ the devices.
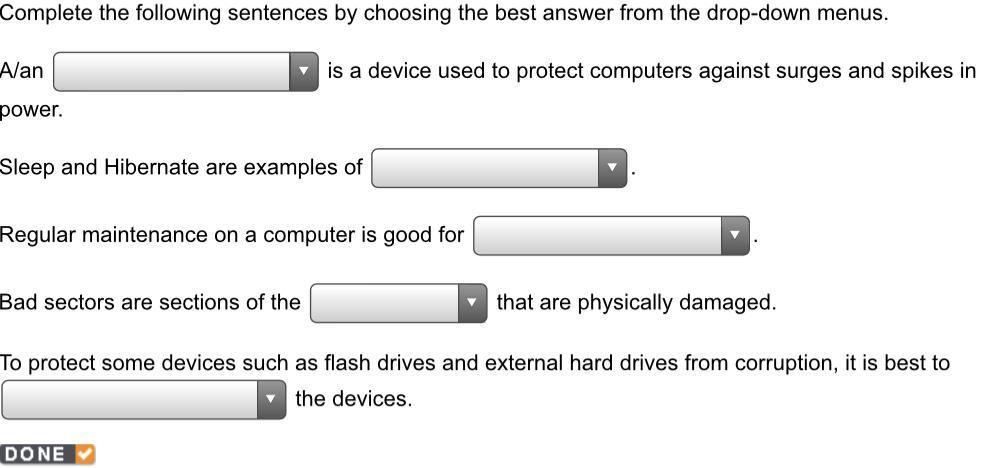
Answers
Answer:
1. Surge protector
2. Power-saving mode
3. Hardware and software
4. Hard disk
5. Eject
Explanation:
sadly my answer has deleted here so i have to start all over again
heya!!
-:QUESTION :-
DEFINE DATA SCIENCE?
Answers
\( \large \underline{ \frak{ ~~~~~~~~~~~~~~~~~~~~\bigstar Solution~~~~~~~~~~~~~~~~~~~~}}\)
Data science helps to understand and analyse the actual scenario and help to take fruitful decisions.
PLSSS HELLLP!!! THE CROWN WILL BE REWARDED FOR THE CORRECT ANSWER!!!
When creating technical writing document, the author should consider _____. Choose all that apply.
Group of answer choices
the setting
the purpose
the audience
the imagery
the organization
Answers
Answer:
The audience
Explanation:
The correct option is - The audience
Reason -
When writing a technical document -
Always describe things in technical terms.
Write for your readers.
Describe things exactly as they're described to you by subject matter experts.
Technical writing :
Addresses particular readers.
Helps readers solve problems.
Help I will mark BRAINLIEST !
Explain looping as an invention strategy. Why is it helpful?
Answers
Answer:
looping?
Explanation:
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
differentiate between organizational policies and organizational procedures?
Answers
Answer:
Policies set parameters for decision making but can still be flexible whereas procedures provide step by step routines for specific tasks and need to be followed
Explanation:
basically policies are not as restrictive as procedures
How do the densities compare for crystalline and amorphous polymers of the same material that have identical molecular weights? (A) Density of crystalline polymer < density of amorphous polymer (B) Density of crystalline polymer = density of amorphous polymer (C) Density of crystalline polymer > density of amorphous polymer
Answers
The correct answer is (C) Density of crystalline polymer > density of amorphous polymer.
Which type of polymer, crystalline or amorphous, generally has a higher density?The density of crystalline polymers is typically higher than that of amorphous polymers of the same material and identical molecular weights.
This is because crystalline polymers have a more ordered and closely packed molecular structure, resulting in a higher density. In contrast, amorphous polymers lack a well-defined molecular arrangement, leading to a lower density.
The crystalline structure allows the polymer chains to align and pack tightly, increasing the overall density. On the other hand, the random arrangement of polymer chains in amorphous polymers leads to a lower density due to the presence of voids and less efficient packing.
The correct answer is (C) Density of crystalline polymer > density of amorphous polymer.
Learn more about amorphous polymer
brainly.com/question/1674832
#SPJ11
WILL MARK BRAIN LIST!
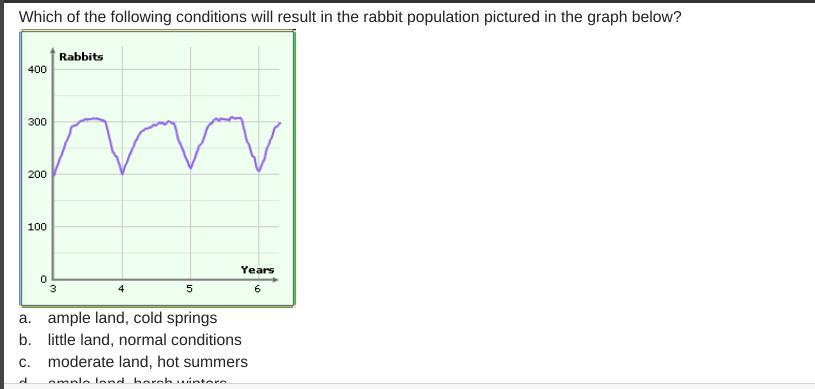


Answers
Answer:
First one is A
Second one is B
Explanation:
One definition of culture suggests that culture is everything you think, everything you do and
everything you possess. The drawing of a cultural system mirrors that definition. In the
drawing, everything you think is represented by:
Technology
Social
Institutions
Ideology
The rectangle
Answers
The drawing that usually represent culture is ideology. The correct option is D.
What is ideology?An ideology is a set of beliefs or philosophies attributed to a person or group of people, particularly those held for reasons other than epistemic ones, in which "practical elements are as prominent as theoretical ones."
Ideology is a type of social or political philosophy in which practical as well as theoretical elements are prominent. It is an idea system that seeks to both explain and change the world.
Culture can be defined as all of a population's ways of life, including arts, beliefs, and institutions that are passed down from generation to generation.
It has been defined as "an entire society's way of life." As being such, it includes etiquette, dress, language, religion, rituals, and art.
Thus, the correct option is D.
For more details regarding ideology, visit:
https://brainly.com/question/24353091
#SPJ1
What are ways to enter a formula in Excel? Check all that apply. Click on the Function Library group and select a function from the drop-down menu. Click on the Function Library group and Insert Function. Click on the File tab in the ribbon. Click on the Insert tab in the ribbon and then Equation. Type = into any cell. Click on the formula bar above the cells.
Answers
Answer:
Answer is these here A B E F
In terms of information systems, a collaboration tool that helps a team communicate, organize, plan, schedule, track, and delegate jobs would be an example of A. a personal information system B. a workgroup information system C. an enterprise information system D. an organizational complement
Answers
An organizational complement is a collaboration tool that helps a team communicate, organize, plan, schedule, track, and delegate jobs. Option D is correct.
How is a computer system operated?An information system can contain information about a company and its surroundings. There are three fundamental processes that produce the information that businesses require: intake, production, and processing Feedback is the output that is provided to the appropriate groups or individuals within an organization so that they can evaluate and enhance the input.
An organizational supplement information system is a technological device that makes it easier for teams within an organization to communicate and work together to plan events, keep track of projects, and submit completed work.
Learn more about information system:
brainly.com/question/5419206
#SPJ4
Final Test CSC 1301 (048) Full Name: 4) a) Write a program to generate Fibonacci sequence: 1 1 2 3 5 8 13 21 34 55 b) What is the output of the following unknown method for (int i-1; ca2; i+) for (int j-1;js 2:j++) for (int k 1; k<3; k++) System.out.print ("&"); System.out.print ("") System.out.println): 5) a) Write a program with a method called maximum that takes three integers as parameters a returns the largest of the three values (using Math.max() method). b) Write a program with a method called slope that take 4 parameters, (x1, y1, x2, y2 co-ordinates) as Inputs and returns the slope as an output. (Cal. Slope with formula y2-y1/x2-x1) 6) a) Write a program with a method called sphereVolume that accepts a radius as parameter and returns the volume of the sphere with that radius. For example, the call sphereVolume(2.0) should return 33.510321 by using the formula 4/3*pi* rr*r (use java constant Math.Pl) b) Write a program with a method revNum that accepts an integer parameter and returns the reverse of the number. For example, the call revNum(29107) returns 70192 7) a) Write a program prompting the user to enter the password. If the password is incorrect, it should continue asking 3 more times, (every time the password is incorrect). Finally, after 3 attempts it should display a message saying, all the attempts are done, try sometime later. If, you have entered correct password it should display message, your password is correct. b) What is the output of the following hello method public class Strange f public static final int MAX 5; public static void hellol1 int number 0; for (int count- MAX; count 3; count--) number +(count*count): System.out.printin(" The result is:"+ number); Public static void main (String [ ) args) hello);
Answers
The code of the subsequent code segment is shown here. The initial loop shall iterate only three times, first loop will loop three times more, or nine times, and the last loop will iterate three times more, or 27 times.
What in coding is segmentation?In addition to or in instead of paging, segmentation is a different method of allocating memory. In its most basic form, the program is divided into several sections, which are each a stand-alone entity that includes a subroutine and data structures. Segments can be any size, unlike pages.
What in C# is a code segment?The term "code segment" refers to a piece of a computer database that includes object code or a segment of the a project's address space that is comparable and provides details on commands and directives that can be executed. A code segment may also be referred to in the computing field as a particular text or just text.
To know more about code segment visit:
https://brainly.com/question/20063766
#SPJ4
Give the usage and syntax of AVERAGE function.
Answers
Write an expression that evaluates to true if and only if the value of the boolean variable workedovertime is true.
Answers
Answer:
import java.io.*;
public class WorkedOvertime
{
public static void main (String[] args)
{
boolean workedovertime = false;
if ( workedovertime )
{
System.out.println("Evaluates to True");
}
else
{
System.out.println("Evaluates to False");
}
}
}
Explanation:
This simple java program evaluates to true if and only if the value of the boolean variable workedovertime is true.
Students have the freedom to design the brochure in a way that helps the general public understand the specific issue. The easiest thing to do is create a new document in Microsoft Word and select a tri-fold brochure. Please remember that a brochure is twosided. The point of the brochures is to highlight an economic issue with solid data and economic reasoning to raise public awareness. Students must clearly favor or oppose the policy in the brochure in a compelling way with strong economic reasoning. A grading rubric has been loaded in Canvas. Policy Issue #1 - President Joe Biden has proposed to increase the federal minimum wage to $15.00 per hour to help underpaid workers. Due Sunday by 11:59pm.
Answers
In this task, students have the freedom to design a brochure to help the general public understand a specific economic issue. The brochure should be two-sided and created using Microsoft Word's tri-fold brochure template. The purpose of the brochure is to raise public awareness about the economic issue by presenting solid data and economic reasoning.
The specific policy issue for this task is President Joe Biden's proposal to increase the federal minimum wage to $15.00 per hour in order to assist underpaid workers. To create a compelling brochure, students must clearly favor or oppose this policy using strong economic reasoning.
Remember to consult the grading rubric provided in Canvas to ensure that you meet all the requirements and criteria for this task.I hope this explanation helps you create a successful and informative brochure. If you have any more questions or need further assistance, feel free to ask!
TO know more about that freedom visit:
https://brainly.com/question/7723076
#SPJ11
What technology can be used by people with a hearing disability to listen to a narration?.
Answers
These days, there are many technologies that we can use to improve our life. For people with a hearing disability to listen to a narration, the technology that can be used is Hearing Loop.
What is Hearing Loop?Many types of Assistive Listening Devices (ALDs) can be used by people with hearing disabilities to help them listen to the narration. These ALDs can improve sound transmission so people with hearing disabilities can hear the sound much more clearer. One of the ALDs that is common to use is a hearing loop. Hearing loop use electromagnetic energy to transmit sound from outside to a miniature wireless receiver built inside the hearing loop. The sound will be much clearer because the sound is picked up directly by the receiver that is built inside the hearing loop.
Learn more about how did the development of schools for the deaf help deafness at https://brainly.com/question/23362896
#SPJ4
Read the following segment of codes.
public void fun1 (LinearNode head){ SingleLinkedNode slow_ptr = head; SingleLinkedNode fast_ptr = head; if (head != null) {
while (fast_ptr != null && fast_ptr.getNext() != null) { fast_ptr = fast_ptr.getNext().getNext(); slow_ptr = slow_ptr.getNext();
}
System.out.println(slow_ptr.data);
}
}
Assume that there is a LinkedNode object, named head, which carries the type of int data and refers to the header of a given linked list, for example, 1->2->3->4->5, what would be output when we execute fun1(head)?
5
3
1
24
Answers
The output when we execute fun1(head) would be 3. This is because the function is using two pointers, one (slow_ptr) moving one node at a time, and the other (fast_ptr) moving two nodes at a time.
The while loop continues until the fast_ptr reaches the end of the linked list. At that point, the slow_ptr will be pointing to the middle node of the list, which in this case is the node containing the value 3. The function then prints out the data value of that middle node, which is 3. Therefore, the output of the function would be 3.
In this segment of codes, the function fun1 takes a LinearNode object as a parameter, which is essentially the header of a linked list. The function then uses two pointers, slow_ptr and fast_ptr, to traverse the linked list. The while loop in the function ensures that the fast_ptr moves two nodes at a time, while the slow_ptr moves one node at a time. This is a common algorithm used to find the middle node of a linked list. Once the loop is exited, the slow_ptr points to the middle node of the list. Finally, the function prints out the value of the data in that middle node. This function can be useful in various applications where we need to access the middle node of a linked list, such as in sorting or searching algorithms.
To know more about output visit :
https://brainly.com/question/14227929
#SPJ11
what's a router?1 pointa physical layer device that allows connections for many computers at oncea device that knows how to forward data between independent networks.a more advanced version of a switcha physical layer device that prevents crosstalk
Answers
A router is a networking device that operates at the network layer of the OSI model and is responsible for forwarding data between independent networks.
It is designed to connect multiple devices and networks together and route data packets based on their destination IP address. Routers use routing tables and algorithms to determine the best path for data to travel between networks, and they provide security features such as packet filtering and network address translation (NAT) to protect against potential security threats. Unlike switches, routers can connect networks with different protocols, and they provide the necessary functions to ensure that data is delivered to its intended destination in an efficient and secure manner.
To learn more about responsible click on the link below:
brainly.com/question/30368671
#SPJ11
under the idea of friendly ai, ai machines would be designed so that they will benefit humans rather than harm them.T/F
Answers
True. Under the concept of Friendly AI, AI machines are designed to prioritize benefiting humans rather than causing harm to them. Friendly AI refers to the approach of designing artificial intelligence systems with the intention of ensuring they act in a way that is beneficial and aligned with human values.
The goal is to create AI systems that are friendly, cooperative, and have a positive impact on human well-being. The concept of Friendly AI acknowledges the potential risks associated with advanced artificial intelligence and aims to mitigate those risks by prioritizing the development of AI systems that prioritize human safety and welfare. This includes designing AI systems that are aligned with human values, exhibit ethical behavior, and work collaboratively with humans rather than posing a threat or harm. By focusing on Friendly AI, researchers and developers strive to create AI systems that can be trusted and relied upon to assist and enhance human capabilities, promoting a symbiotic relationship between humans and machines. The aim is to ensure that AI technologies are developed and utilized for the benefit and well-being of humanity as a whole.
Learn more about artificial intelligence here:
https://brainly.com/question/22678576
#SPJ11
which command can an administrator execute to determine what interface a router will use to reach remot netowrks
Answers
Determine the path between two connections by using the traceroute command. A connection to another device frequently needs to pass via several routers.
How do I get my Cisco router's interface status?Use the show interface summary command to provide a summary of the system interfaces' details. There are no arguments or keywords for this command. Use the show interface command to display the system interfaces' details. information about the redundancy management interface is displayed in full.
What router command would a system administrator enter to check whether the exit interface was operational?The show is interface short command can be used by the network administrator to check that the interface connected to the next hop address or the exit interface is operational. To check if the next hop address is reachable, use the ping command. The routing table is displayed via the show IP route command.
to know more about routers here:
brainly.com/question/29768017
#SPJ4