Can two characters of the same element activate an elemental resonance in co-op mode?.
Answers
Elemental Resonance is a concept that comes into play in Genshin Impact. It's a party-based system that grants additional benefits to a team of characters based on their element. Elemental Resonance can be activated by having two or more characters with the same element in a team.
In the co-op mode of Genshin Impact, this concept is a bit different. So, can two characters of the same element activate an elemental resonance in co-op mode?The answer is yes, two characters of the same element can activate an elemental resonance in co-op mode. However, the resonance bonus will be limited to just 15% rather than the usual 25% bonus for two characters. The reason for this limitation is to ensure that the co-op mode is not overpowered and that the players don't get an unfair advantage over other players.Genshin Impact has several elements, such as Pyro, Cryo, Hydro, Electro, Geo, and Anemo. The resonance bonus for each element is different. For example, Pyro resonance grants a 25% increase to attack damage against enemies affected by Pyro. Cryo resonance increases critical hit rate by 15% against enemies affected by Cryo. Electro resonance reduces the elemental skill cooldown by 1 second when the character triggers an Electro-related reaction. Similarly, the other elements also have their respective resonance bonuses.
In conclusion, two characters of the same element can activate an elemental resonance in co-op mode, but the bonus will be limited to 15%.
To know more about Elemental Resonance visit:
https://brainly.com/question/31999306
#SPJ11
Related Questions
Samantha is part of a project management team working on the initiation phase of a project. What is her team expected to do in this phase?
In the initiation phase, Samantha’s team needs to clarify the project’s ______
and justify it.
PLATO!
Answers
Answer:
Doubts, demands, and details
Explanation:
in this first phase the project management team does the basic work required for the subsequent stages of the project. They discuss and clarify doubts, demands, and details of the project with the client. They then select team members for the project, and discuss the project goals.
Ryan is applying a sort to the data in a table that you have inserted in Word. Which option is important for most tables that have column headings?
• Sort in descending order.
• Sort in ascending order.
• Select the option "My List has Header Row."
• Choose the correct sort field.
Answers
Ryan is applying a sort to the data in a table that you have inserted in Word.By Choose the correct sort field option is important for most tables that have column headings.
What is statistics?A statistics desk is a number cell wherein you may alternate values in a number of the cells and give you one-of-a-kind solutions to a problem. An appropriate instance of a statistics desk employs the PMT feature with one-of-a-kind mortgage quantities and hobby fees to calculate the low-priced quantity on a domestic loan you can set up in descending, or you may set up in ascending.
And D, has not have anything to do with this requirement. You do not have this feature to be had with you. Select the option, "My listing has header row" isn't always to be had to us. And clearly, you want to pick out the excellent type of discipline first. And then you may set up or type accordingly.
Read more about the column headings:
https://brainly.com/question/1788884
#SPJ2
Please help with my assignment! Use python to do it.
Answers
Answer:
I cant see image
Explanation:
can you type it and I'll try to answer
100 POINTS!!! Write in python

Answers
Here's a Python statement to create a label widget with the text "Programming is fun!" as a child of self.main_window:
The Python Programtk.Label(self.main_window, text="Programming is fun!").pack()
This statement creates a new Label widget with the specified text as the child of the self.main_window parent widget using the tk.Label() constructor.
\
The .pack() method is then called on the Label widget to add it to the window.
The pack() function is among the various layout managers offered by Tkinter, which is the premier Python GUI toolbox. Multiple geometry managers, such as .grid() and .place(), offer varied options for controlling the spatial placement and arrangement of widgets in a window.
Read more about programs here:
https://brainly.com/question/28938866
#SPJ1
If you are one of the famous CEO now a days, what kind of product you can share to the world
Answers
Answer:
cosmetics
Explanation:
for beauty and to help young people to make they glow up
how many different permutations of the letters abcdef contain the strings abc and cde?
Answers
The number of ways to arrange the two strings abc and cde as a single unit, the number of ways to arrange the remaining letters f and g, and then combine the arrangements to get the total number of permutations.
To solve this problem, we can use the concept of counting techniques. Firstly, we need to determine the number of ways we can arrange the letters abc and cde. Since we want both strings to be included, we can treat them as a single unit and arrange them as a group. Therefore, there are 2! = 2 ways to arrange the letters abc and 3! = 6 ways to arrange the letters cde. So, the total number of ways to arrange both strings as a single unit is 2 x 6 = 12.Next, we need to determine the number of ways to arrange the remaining letters f and g. There are 2! = 2 ways to arrange these two letters. Finally, we can combine the arrangements of the two groups of letters (abc and cde, and f and g) to get the total number of permutations. The number of permutations is given by:12 x 2! = 24Therefore, there are 24 different permutations of the letters abcdef that contain the strings abc and cde.
For such more questions on permutations
https://brainly.com/question/28065038
#SPJ11
To count the number of different permutations of the letters abcdef that contain the strings abc and cde, we can break down the problem into two cases:
Case 1: The strings abc and cde are adjacent.
In this case, we can treat the strings abc and cde as a single entity, let's call it X, and count the number of permutations of the letters X, a, b, f, and g. This can be done in 5! ways. However, since the strings abc and cde can be arranged in 2! = 2 ways within X, we need to multiply by 2. Therefore, the total number of permutations in this case is 5! x 2 = 240.
Case 2: The strings abc and cde are not adjacent.
In this case, we need to place the strings abc and cde in the permutation first, and then fill in the remaining slots with the remaining letters d, e, and f. There are 4! ways to arrange the strings abc and cde, and then 3! ways to arrange the remaining letters. Therefore, the total number of permutations in this case is 4! x 3! = 144.
To obtain the total number of permutations, we can add the results of both cases: 240 + 144 = 384. Therefore, there are 384 different permutations of the letters abcdef that contain the strings abc and cde.
Learn more about permutations here:
https://brainly.com/question/30649574
#SPJ11
Which of the following is something that would NOT appear in the Reviewing pane?
a. The date on which a specific insertion was made.
b. The length of the document being reviewed.
c. The name of the person making an insertion.
d. The total number of revisions made to the document.
Answers
Answer:
A
Explanation:
Why is it important to plan out the design of an app?
Answers
Answer:
you could mess it up
Explanation:
let me explain an app may be easy if you know what your doing. if you dont you most likely might miss a code or mess up the hole code.
2.7 code practice question 1 edhesive
Answers
I will edit this if you edit your question..
Im confused. This is not a question..
Kelly is fond of pebbles, during summer, her favorite past-time is to cellect peblles of the same shape and size
Answers
The java code for the Kelly is fond of pebbles is given below.
What is the java code about?import java.util.Arrays;
public class PebbleBuckets {
public static int minBuckets(int numOfPebbles, int[] bucketSizes) {
// Sort the bucket sizes in ascending order
Arrays.sort(bucketSizes);
// Initialize the minimum number of buckets to the maximum integer value
int minBuckets = Integer.MAX_VALUE;
// Loop through the bucket sizes and find the minimum number of buckets needed
for (int i = 0; i < bucketSizes.length; i++) {
int numBuckets = 0;
int remainingPebbles = numOfPebbles;
// Count the number of buckets needed for each size
while (remainingPebbles > 0) {
remainingPebbles -= bucketSizes[i];
numBuckets++;
}
// Update the minimum number of buckets if needed
if (remainingPebbles == 0 && numBuckets < minBuckets) {
minBuckets = numBuckets;
}
}
// If the minimum number of buckets is still the maximum integer value, return -1
if (minBuckets == Integer.MAX_VALUE) {
return -1;
}
return minBuckets;
}
public static void main(String[] args) {
// Test the minBuckets function
int numOfPebbles = 5;
int[] bucketSizes = {3, 5};
int minBuckets = minBuckets(numOfPebbles, bucketSizes);
System.out.println("Minimum number of buckets: " + minBuckets);
}
}
Learn more about java code from
https://brainly.com/question/18554491
#SPJ1
See full question below
Write a java code for the following Kelly is fond of pebbles. During summer, her favorite past-time is to collect pebbles of same shape and size. To collect these pebbles, she has buckets of different sizes. Every bucket can hold a certain number of pebbles. Given the number of pebbles and a list of bucket sizes, determine the minimum number of buckets required to collect exactly the number of pebbles given, and no more. If there is no combination that covers exactly that number of pebbles, return -1. Example numOfPebbles = 5 bucketSizes = [3, 5] One bucket can cover exactly 5 pebbles, so the function should return 1.
a new layer 3 switch is connected to a router and is being
Answers
A Layer 3 switch is a device that combines the functions of a switch and a router. It can connect devices on the same subnet or VLAN at high speeds and also support routing protocols and quality of service specifications. When configuring a new Layer 3 switch for interVLAN routing, some of the steps required for the configuration include: enabling IP routing, assigning ports to VLANs, and installing a static route.
Connecting a Layer 3 switch to a router involves configuration of the switch's interfaces, setting up VLANs, and configuring routing protocols for improved network performance.
When a new Layer 3 switch is connected to a router, it involves configuring the switch's interfaces, setting up VLANs (Virtual Local Area Networks), and configuring routing protocols. The Layer 3 switch can perform routing tasks as well as switching tasks. The goal is to optimize the network's overall performance. For example, if there's a lot of inter-VLAN traffic, a Layer 3 switch can handle that locally without having to involve the router. This frees up the router to handle other tasks and reduces overall network traffic. Therefore, when connecting a Layer 3 switch to a router, it's important to plan the configuration carefully according to specific network requirements and architecture.
Learn more about Layer 3 switch here:https://brainly.com/question/31563411
Allan needs to ensure that an object is in a very precise location on a slide. He decides to use the Ruler option to achieve this. On which tab is the Ruler option found?
choose *View got a 100%


Answers
Answer:
view
Explanation: post protected
Tier 1 networks form the internet ____.
Answers
Answer:
Internet Backbone
Explanation:
The internet is a network of networks, no single tier 1 network (ISP companies like Sprint, IBM, Verizon, AT&T for example, they provide the cables and routers that connect the networks) can reach the entire internet on its own, so they merge together to form the Internet Backbone, a backbone network enables all users and companies to connect with each other.
identify the oracle database objects used by attackers for enumeration . mysql.user, mysql.db, mysql.tables_priv sysobjects, syscolumns, sysdatabases MsysObjects, MsysQueries, MsysRelationships SYS.USER_OBJECTS, SYS.USER_VIEWS, SYS.ALL_TABLES Question 21 10 5 noint Which of the following types of honeypot emulates the real production network of a target organization and causes attackers to devote their time and resources toward attacking the critical production system of the company? Malware honeypots Honeynet Pure honeypots Spider honeypots
Answers
The type of honeypot that emulates the real production network of a target organization and causes attackers to devote their time and resources toward attacking the critical production system of the company is called a Honeynet.
Honeynets are designed to emulate a real network with various operating systems, services, and applications to attract attackers and study their behavior. They can be used to detect new or unknown attacks, gather intelligence on attackers, and study the techniques and tools used by attackers.
Unlike other types of honeypots, Honeynets require significant resources and expertise to set up and maintain, and should only be used in controlled environments by experienced security professionals.
Learn more about honeypot here:
https://brainly.com/question/24182844
#SPJ11
The type of honeypot that emulates the real production network of a target organization and causes attackers to devote their time and resources toward attacking the critical production system of the company is called a honeynet.
A honeynet is a high-interaction honeypot that is designed to simulate a full network with multiple hosts and services. It allows researchers to monitor attackers' behavior on a larger scale and gain a better understanding of their motives, tactics, and tools. Unlike other types of honeypots, which are designed to attract and trap attackers, honeynets are designed to gather intelligence and enable researchers to analyze attacker behavior in a safe and controlled environment.
For such more question on honeypot
https://brainly.com/question/17004996
#SPJ11
The best way to handle a problem is to ______.
a.
wait for someone to notice the problem
b.
avoid the problem so you don’t get blamed
c.
take care of the problem as soon as someone asks you
d.
take care of the problem as soon as you notice it
Answers
Answer:
D. take care of the problem ad soon as you notice it
which of the following best represents a field within a data base? a. a data base record. b. a database mine. c. records within customer names. d. customer names within a record.
Answers
To answer your question, the best representation of a field within a database would be option D, which is customer names within a record.
A field refers to a specific piece of information within a record, and in this case, the customer name would be the field within a record that contains other pieces of information such as the customer's address, phone number, and email. Option A, a database record, refers to a collection of fields, while option B, a database mine, is not a term commonly used in database management. Option C, records within customer names, does not make sense as records are not typically nested within a field. In conclusion, a field within a database is a specific piece of information within a record, such as customer names within a record.
To know more about database visit:
brainly.com/question/30163202
#SPJ11
Gina is using Outlook in the default cached mode and is connected to an Exchange server. What is the default file type used to store a cached version of Gina’s mailbox?
PST
OST
MSG
XML
Answers
Answer:
Its C. MSG
Explanation:
On edg
Answer:
c
Explanation:
took the test
refer to the exhibit. what description matches the function of the packet tracer devices shown?
Answers
A microarray like the Axiom array is a powerful tool that is used in the field of genomics for the detection of specific genetic variants.
It works by using a large number of probes that are specific to particular genetic variants. When a sample is applied to the microarray, the probes on the array will bind to any genetic material in the sample that matches their specific sequence. By examining which probes on the microarray have bound to the sample, it is possible to determine which genetic variants are present in the sample. This information can be used for a wide range of applications, from studying genetic disorders to identifying specific markers for drug response.
To learn more about Axiom click on the link below:
brainly.com/question/31491153
#SPJ11
Discuss the limitations of computer.
Answers
Answer:
Computer System doesn't think by itself.It needs continuous instructions by user.It takes limited number of input at a time.It cannot take its own decision.It doesn't have imagination.It is not creative.four example of computer software?
Answers
answer= safari, ms-word, moviemaker, ms-paint, firefox,etc...
at what layer of the osi model does a network switch normally operate? a. layer 5 b. layer 3 c. layer 4 d. layer 2
Answers
Answer:
D. Layer 2
Explanation:
It is layer 2.
To learn more:
https://brainly.com/question/26299918?referrer=searchResults
Hope this helps!
What does the CIA do ?
Answers
To protect national security, the Central Intelligence Agency (CIA) gathers, assesses, and disseminates critical information on foreign military, political, economic, scientific, and other developments.
What is CIA?The Central Intelligence Agency (CIA) is the main foreign intelligence and counterintelligence organization of the United States government. The Office of Strategic Services (OSS) from World War II gave rise to the Central Intelligence Agency (CIA), which was officially founded in 1947.
Duplication, competition, and a lack of coordination plagued earlier U.S. intelligence and counterintelligence efforts, which were carried out by the military and the Federal Bureau of Investigation (FBI). These issues persisted, in part, into the twenty-first century.
The establishment of a civilian intelligence agency by the United States, the last of the major powers, was charged with gathering top-secret data for decision-makers.
Learn more about CIA
https://brainly.com/question/29789414
#SPJ4
3. discuss the trade-offs between bus-based and switched ethernet. state the various conditions under which one or the other would be preferred and explain why.
Answers
Smaller networks favor bus-based Ethernet because it is simpler, cheaper, and prioritizes simplicity above performance and security. On the other hand, switched Ethernet is recommended in bigger networks.
What distinguishes switched Ethernet from Ethernet?The "Type" field in traditional Ethernet is what tells the receiver which process to give the frame to. The 'Length' field in switched Ethernet is where the number of bytes in the data field are stored.
What two things separate an Ethernet switch from an Ethernet bridge?A bridge only has two ports. Several ports can be handled by a switch. A device called a bridge joins two LANs and manages data flow.
To know more about Ethernet visit:-
https://brainly.com/question/13441312
#SPJ1
Need help plz 100 POINTS





Answers
Answer:
1. 12 anything below that looks like a slideshow presentation lol
2. False I dont think so.
3. Length X Width
4. Almost all news programs are close up.
5. True
Most operating systems include security features, such as an integrated ____, to protect against unauthorized access via the Internet.
Answers
The answer would be: firewall.
I hope that this helps you!
Lael is also planning for student groups that the office will be working with in the coming year. She decides to create a PivotTable to better manipulate and filter the student group data. Switch to the Academic Pivot Table worksheet, then create a PivotTable in cell A1 based on the AcademicGroups table. Update the PivotTable as follows so that it matches Final Figure 2:a. Change the PivotTable name to: AcademicPivotTable b. Add the Activities field and the Group Name field (in that order) to the Rows area.c. Add the 2021, 2022, and 2023 fields (in that order) to the Values area. d. Change the display of subtotals to Show all Subtotals at Top of Group. e. Change the report layout to Show in Outline Form. f. Update the Sum of 2021 field in the values area to display the name 2021 Membership with the Number number format with o decimal places. Ug. pdate the Sum of 2022 field in the Values area to display the name 2022 Membership with the Number number format with o decimal places. h. Update the Sum of 2023 field in the values area to display the name 2023 Membership with the Number number format with o decimal places. e. f. g. h.Previous question
Answers
I apologize, but as a text-based AI, I don't have access to specific worksheets or the ability to create PivotTables in spreadsheets.
I can provide guidance on how to create a PivotTable in general, but I can't perform specific actions on a specific worksheet.To create a PivotTable based on the AcademicGroups table and make the requested updates, you can follow these general steps using Microsoft Excel:Open the worksheet containing the AcademicGroups table.Select any cell within the table or the entire table.Go to the "Insert" tab in the Excel ribbon.Click on the "PivotTable" button. This will open the "Create PivotTable" dialog box.In the dialog box, ensure that the range or table reference is correctly selected.Choose the location for the PivotTable (e.g., "New Worksheet" or "Existing Worksheet").Click "OK" to create the PivotTable.Ine PivotTable Field List pane on the right, you will see the field names from the AcademicGroups table.Drag the "Activities"
learn more about spreadsheets here:
https://brainly.com/question/11452070
#SPJ11
This programming language adds functionality to web pages.
JavaScript
SQL
Python
HTML
Answers
Among the programming languages listed, JavaScript is the language that adds functionality to web pages.
The correct answer to the given question is option A.
JavaScript is a client-side scripting language that enables interactivity and dynamic effects on web pages. It allows developers to create responsive and engaging web pages that can change in real-time based on user input or other events. It is widely used for front-end development along with HTML and CSS, and is supported by all modern web browsers.
SQL, on the other hand, is a database language used for managing and manipulating data in relational databases. It is not used for adding functionality to web pages, but rather for handling data on the server-side. Python is a general-purpose programming language that can be used for various applications, including web development, but it is not specifically designed for web pages. HTML, on the other hand, is a markup language used for creating the structure and content of web pages, but it does not add functionality.
In summary, JavaScript is the programming language that adds functionality to web pages, while SQL is used for database management, Python is a general-purpose programming language, and HTML is used for creating the structure and content of web pages.
For more such questions on JavaScript, click on:
https://brainly.com/question/16698901
#SPJ8
anyone can help me answer this puzzle i really need it right now. thanks!
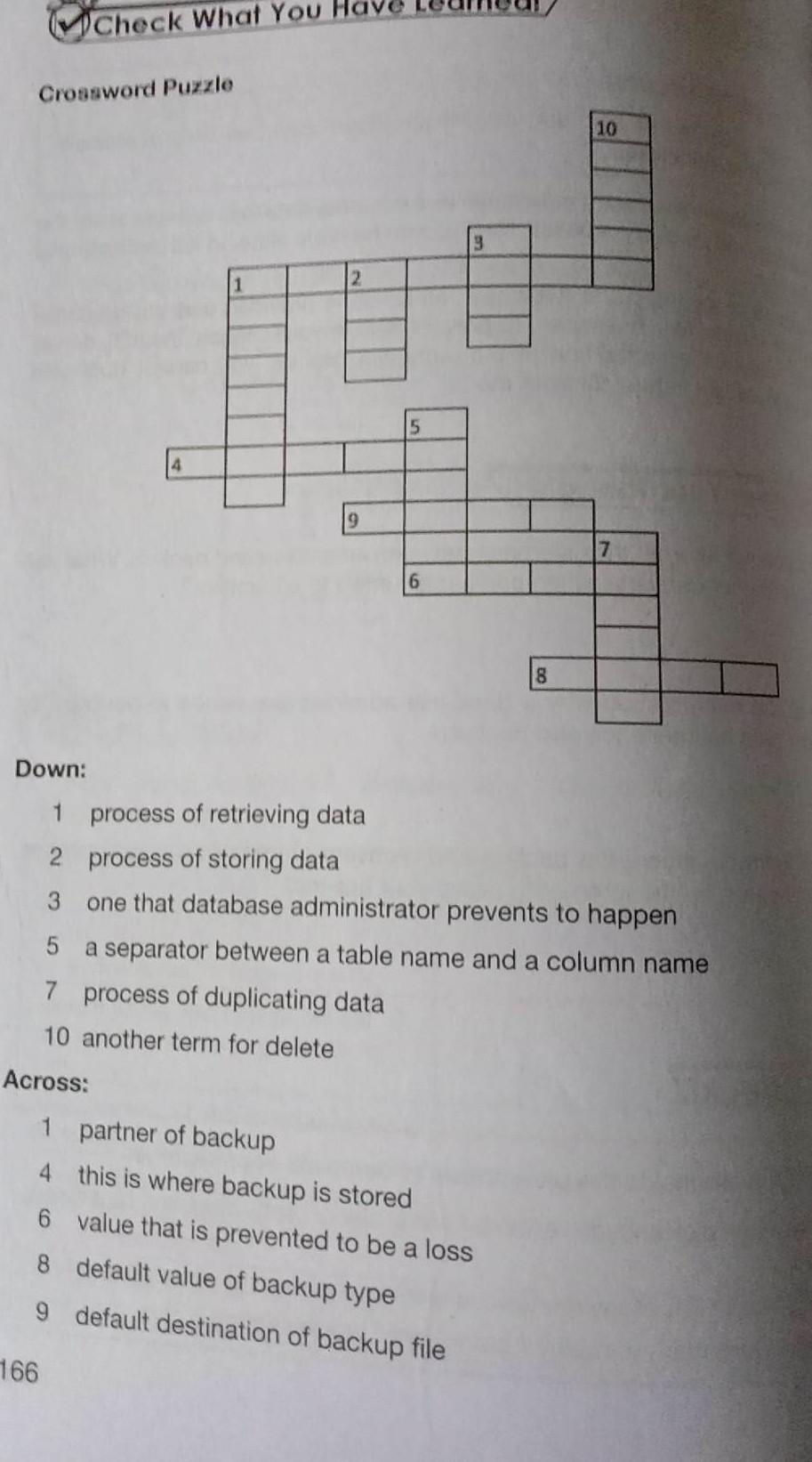
Answers
The right words that can be used to fill up the blank spaces in the puzzle are as follows:
data is fetching. data storagebreachperiodredundancydelete is remove or dropHow to fill up the blanksTo insert the correct words in the puzzles, we need to understand certain terms that are used in computer science.
For example, a data breach occurs when there is a compromise in the systems and it is the duty of the database administrator to avoid any such breaches. Also, data fetching is another jargon that means retrieving data.
Learn more about data fetching here:
https://brainly.com/question/14939418
#SPJ1
You are the IT administrator for a small corporate network. You have decided to upgrade your network adapter to a Gigabit Ethernet adapter on the Support workstation. You have already installed the network card in a free PCIe slot and downloaded the latest drivers from the manufacturer's website.
Currently, your computer has two network adapters, the new one you just added, and the original one you are replacing. Rather than remove the first network adapter, you decide to leave it in your computer. However, you do not want Windows to use the network adapter.
In this lab, your task is to complete the device configuration using Device Manager as follows:
Update the device driver for the Broadcom network adapter using the driver in the D:\drivers folder.
Disable the Realtek network adapter.
Answers
To complete the device configuration using Device Manager, you would need to follow the steps below: Open Device Manager by right-clicking on the Windows icon in the taskbar and selecting "Device Manager" from the menu.
Locate the two network adapters under the "Network adapters" category in the list of devices. Right-click on the Broadcom network adapter and select "Update driver" from the context menu. In the pop-up window, select "Browse my computer for driver software" and navigate to the D:\drivers folder where you have saved the latest drivers for the adapter. Click "Next" and let Windows install the driver. Once the driver installation is complete, right-click on the Realtek network adapter and select "Disable device" from the context menu. Confirm the action by clicking "Yes" on the pop-up window.
you will have successfully updated the device driver for the Broadcom network adapter and disabled the Realtek network adapter. This will ensure that Windows does not use the Realtek adapter and instead uses the Gigabit Ethernet adapter you have installed for better network performance. To complete the device configuration using Device Manager to update the Broadcom network adapter driver and disable the Realtek network adapter, please follow these steps: Press the Windows key + X to open the Quick Link menu and select "Device Manager" from the list. In the Device Manager window, expand the "Network adapters" category to see the list of network adapters on your computer. Locate the Broadcom network adapter in the list. Right-click on it and select "Update driver." In the Update driver window, select "Browse my computer for driver software. Now you have successfully updated the device driver for the Broadcom network adapter and disabled the Realtek network adapter in your computer.
To know more about Device Manager visit:
https://brainly.com/question/869693
#SPJ11
what are some ways to better secure your installation of the above noted linksys model e4200 wireless router access point?
Answers
1. Change the default login credentials: The default login credentials for the Linksys E4200 router are well-known and easily accessible online, making it easier for unauthorized users to access your network. Therefore, it is recommended to change the default login credentials right after setting up the router.
2. Enable WPA2 encryption: WPA2 is a security protocol that encrypts the data transmitted over your wireless network. It is recommended to enable WPA2 encryption on your router and to use a strong and unique passphrase.
3. Change the default SSID: The SSID (Service Set Identifier) is the name of your wireless network. It is recommended to change the default SSID to a unique name that does not reveal any personal information.
4. Disable WPS: Wi-Fi Protected Setup (WPS) is a feature that allows easy connection of devices