C++ 11 introduced an alternative way to define variables, using the template key word and an initialization value. True or false
Answers
False. C++11 did introduce a new way to initialize variables using braces ({}) called "uniform initialization" or "list initialization", but it did not involve the use of templates.
How are variables defined?Instead, the syntax for using uniform initialization to initialize a variable with a value in C++11 is as follows:
int x{42}; // variable x is initialized with the value 42
This syntax is also valid for initializing variables of other types, such as arrays or objects. Additionally, C++11 introduced a feature called "initializer lists" that allows objects to be constructed with a list of values, which can also be used with the uniform initialization syntax.
The use of templates, on the other hand, is a separate language feature in C++ that allows for generic programming by defining functions and classes that can operate on different types.
Templates are typically defined using the "template" keyword followed by one or more type parameter declarations. They are not related to the initialization of variables in C++.
Read more about variables here:
https://brainly.com/question/25223322
#SPJ1
Related Questions
True or false objects that are not moving process no energy
Answers
They produce potential energy, and when moving they have kinetic energy
Have a great day! :)
which of the following is not the correct definition of an operating system
A.
it controls all other execution in a computer
B.
interface between hardware and application programs
C.
its a platform for ensuring that other executions has taken place
D.
maintains consistency of data loss during execution
Answers
The correct answer is C. An operating system is not a platform for ensuring that other executions have taken place. An operating system is a software program that manages the hardware and software resources of a computer and provides common services for computer programs. It acts as an interface between the hardware and application programs and controls all other execution in a computer. It also maintains consistency of data during execution.
TCP is a more dependable protocol than UDP because TCP is_____ latent/connectionless/connection-oriented/encapsulated
Answers
Answer:
connection-oriented
Explanation:
Answer:
TCP is a more dependable protocol than UDP because TCP is
connection-oriented
Explanation:
Because I took a guess and that was the
The ethical and appropriate use of a computer includes_____. Select 4 options.
Answers
The ethical and appropriate use of a computer encompasses several key principles that promote responsible and respectful behavior in the digital realm.
Four important options include:
1. Always ensuring that the information you use is correct: It is essential to verify the accuracy and reliability of the information we use and share to avoid spreading false or misleading content.
Critical evaluation of sources and fact-checking are vital in maintaining integrity.
2. Never interfering with other people's devices: Respecting the privacy and property rights of others is crucial. Unauthorized access, hacking, or tampering with someone else's computer or devices without their consent is unethical and a violation of their privacy.
3. Always ensuring that the programs you write are ethical: When developing software or coding, it is important to consider the potential impact of your creations.
Ethical programming involves avoiding harmful or malicious intent, ensuring user safety, respecting user privacy, and adhering to legal and ethical standards.
4. Never interfering with other people's work: It is essential to respect the intellectual property and work of others. Plagiarism, unauthorized use, or copying of someone else's work without proper attribution or permission is unethical and undermines the original creator's rights and efforts.
In summary, the ethical and appropriate use of a computer involves verifying information accuracy, respecting privacy and property rights, developing ethical programs, and avoiding interference with other people's work.
These principles promote a responsible and respectful digital environment that benefits all users.
For more such questions on ethical,click on
https://brainly.com/question/30018288
#SPJ8
The probable question may be:
The ethical and appropriate use of a computer includes_____.
Select 4 options.
-always ensuring that the information you use is correct
-never interfering with other people's devices
-always ensuring that the programs you write are ethical
-never interfering with other people's work
What is an advantage of storing data in a data lake without applying a specific schema to it initially?
Answers
An advantage of storing data in a Data Lake, without applying a specific schema to it initially is that: It makes working with the data faster as data lakes are more efficient.
What is a data lake?A data lake can be defined as a centralized data storage repository that avails all end users an ability to store, process and secure all of their structured and unstructured data at any scale, until they are needed for analytic software applications.
What is DBMS?DBMS is an abbreviation for database management system and it can be defined as a collection of software applications that enable various computer users to create, store, modify, migrate or transfer, retrieve and manage data in a relational database.
In this context, we can reasonably infer and logically deduce that data lakes makes working with data more faster because they are designed and developed to be efficient.
Read more on data lake here: https://brainly.com/question/26207955
#SPJ1
Complete Question:
What is an advantage of storing data in a Data Lake, without applying a specific schema to it initially?
It allows more flexibility to use the data in various innovative ways.
It saves both developer time and company money by never having to design a schema.
It avoids corrupting the data by working with it before there is a clearly defined need,
It makes working with the data faster as data lakes are more efficient.
I don't know this yet.
ASAP NEED HELP ASAP NEED HELP ASAP NEED HELP ASAP NEED HELP ASAP NEED HELP ASAP NEED HELP ASAP NEED HELP ASAP NEED HELP

Answers
Answer:
10.b
11.c
12.c
13.a
14.d
15.b
16.c
Explanation:
please brainleist please ♨️❤☺️☻
what is computer hardware
Answers
Computer hardware refers to the physical components of a computer system that can be seen and touched. It encompasses all the tangible parts that make up a computer, enabling it to function and perform various tasks. Hardware includes devices such as the central processing unit (CPU), memory (RAM), storage devices (hard drives, solid-state drives), input devices (keyboard, mouse), output devices (monitor, printer), and other peripheral devices (speakers, scanners, etc.).
These hardware components work together to execute and manage data and instructions within a computer system. The CPU acts as the brain of the computer, performing calculations and executing instructions. Memory provides temporary storage for data and instructions that the CPU can quickly access. Storage devices store data in a more permanent manner, allowing it to be retained even when the computer is turned off.
Input devices enable users to input data and commands into the computer, while output devices display or present processed information to the user. Peripheral devices expand the capabilities of the computer system, providing additional functionalities and connectivity options.
Computer hardware is essential for the functioning of a computer and determines its processing power, storage capacity, and overall performance. It is complemented by software, which provides the instructions and programs necessary to utilize the hardware effectively. Together, hardware and software form the foundation of modern computer systems.
For more such questions on components, click on:
https://brainly.com/question/28351472
#SPJ11
1. Identify two real-world examples of problems whose solutions do scale well.
2. Identify two real-world examples of problems whose solutions do not scale well.
3. Identify one problem that is so complex that there is no computational solution to feasibly solve the problem in a reasonable amount of time.
Answers
1. Identify two real-world examples of problems whose solutions do scale well.
ANSWER; Real word examples of
problems whose solutions do scale well are;
- To find the smallest/ largest element in a list of data.
This is used when there is trial to find from a table the person that posseses the largest attribute.examples are salary and age.
Or it is also used when finding the highest score on a test, however,this is scalable as it can be done by both humans and machines according to the problem size but in the same fashion.
- Solving simple arithmetic equations.
Solving a simple arithmetic problem is one of an easily scaled problem, however,this depends on the number of operations and the variables present in the equation and which corresponds to daily life situations like adding, finding mean and counting.
2. Identify two real-world examples of problems whose solutions do not scale well.
Real word examples of problems which do not scale well are;
- The sorting of a large list of numbers do not scale well,this is because as the steps required increases as square or increases as more by the increase in size.
- Multiplication of matrices for various applications.example of this is like solving equations.
3. Identify one problem that is so complex that there is no computational solution to feasibly solve the problem in a reasonable amount of time.
Example of a problem that is not feasible computer-wise would be to find the optimal way or best to play the game of Chess. Here, it is possible to tell a good move but to tell the best move is computationally not possible.
ABC Manufacturing Company is located in Hiroshima, Japan. Being prone to earthquakes, the company decided to implement a backup of their data on a Singapore server. The IT administrator contacted you to identify the optimal command interface protocol for this backup. Which command interface protocol should you advise?
Answers
The command interface protocol that I would suggest to the IT administrator is Secure Shell (SSH).
What is a command interface protocol?A command interface protocol can be defined as a standard protocol that is designed and developed to processes commands in the form of lines of text to a software program that is installed on a computer system.
The types of command interface protocol.In Computer technology, there are different types of command interface protocol and these include:
SSLTLSSSHSSH is an acronym for Secure Shell and it is a standard network protocol that gives a IT administrator a secure way to access data over an unsecured network, especially when backing up data.
Read more on SSH here: brainly.com/question/17147683
tip! if you want to not see notifications, just go to settings, go to notifications, and turn off notifications!
Answers
Answer:
thanks that helps
Explanation:
Answer:
okok
Explanation:
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Describe five examples of civil engineering projects.
Answers
Answer:
Hereare 5 types of civil engineering projects:
1 )Water engineering.
2)Construction and management engineering.
3)Structural engineering.
4)Geotechnical engineering.
5)Transport engineering.
Which of the following are advantages of automatic updates?

Answers
Answer:
a,b,d
Explanation:
a.they protect against viruses
b.they protect against hackers
d.they keep your computer running at peak performence
Answer:
They protect against viruses
Explanation:
How much data can a flash drive store?
Answers
Answer:
depends on which flash drive
Explanation:
32GB-1000 photos
Well, It just depends on which size you get. You could get a 512 MB or 10 GB. I prefer somewhere in the middle because I don't need to store a lot of stuff in my Flash drive.
Describe the basic internal operation of magnetic hard disc
Answers
Explanation:
Magnetic hard disks (HDDs) are a type of storage device used in computers to store data persistently. Here are the basic internal operations of magnetic hard disks:
Platters: The hard disk consists of several circular disks called platters that are made of a rigid material like aluminum or glass. These platters are coated with a thin layer of magnetic material.
Read/Write Heads: Read/Write Heads are small electromagnets that are positioned above and below each platter. The heads move in unison and are attached to a mechanical arm called the actuator. The actuator positions the heads over the appropriate tracks on the platters.
Spindle Motor: The spindle motor rotates the platters at high speed, typically between 5400 and 15000 revolutions per minute (RPM). The faster the RPM, the faster the hard disk can read and write data.
Magnetic Fields: When data is written to the hard disk, the read/write heads create a magnetic field that aligns the magnetic particles on the platters in a specific pattern, representing the data being written.
Reading Data: When data is read from the hard disk, the read/write heads detect the magnetic pattern on the platters and convert it back into digital data. The read/write heads move rapidly over the platters, reading data from multiple tracks simultaneously.
File System: To organize and manage data on the hard disk, a file system is used. A file system keeps track of the location of data on the hard disk, as well as other information such as file names, permissions, and timestamps.
leave a comment
What happens when QuickBooks Online doesn't find a rule that applies to a transaction?
Answers
QuickBooks employs the Uncategorized Income, Uncategorized Expense, or Uncategorized Asset accounts to hold transactions that it is unable to categorize. These accounts cannot be used to establish bank policies.
What is QuickBooks Online?A cloud-based financial management tool is QuickBooks Online. By assisting you with things like: Creating quotes and invoices, it is intended to reduce the amount of time you spend handling your company's money. monitoring the cash flow and sales.
While QuickBooks Online is a cloud-based accounting program you access online, QuickBooks Desktop is more conventional accounting software that you download and install on your computer.
QuickBooks is an accounting program created by Intuit whose products offer desktop, internet, and cloud-based accounting programs that can process invoices and business payments. The majority of QuickBooks' customers are medium-sized and small enterprises.
Thus, QuickBooks employs the Uncategorized Income.
For more information about QuickBooks Online, click here:
https://brainly.com/question/20734390
#SPJ1
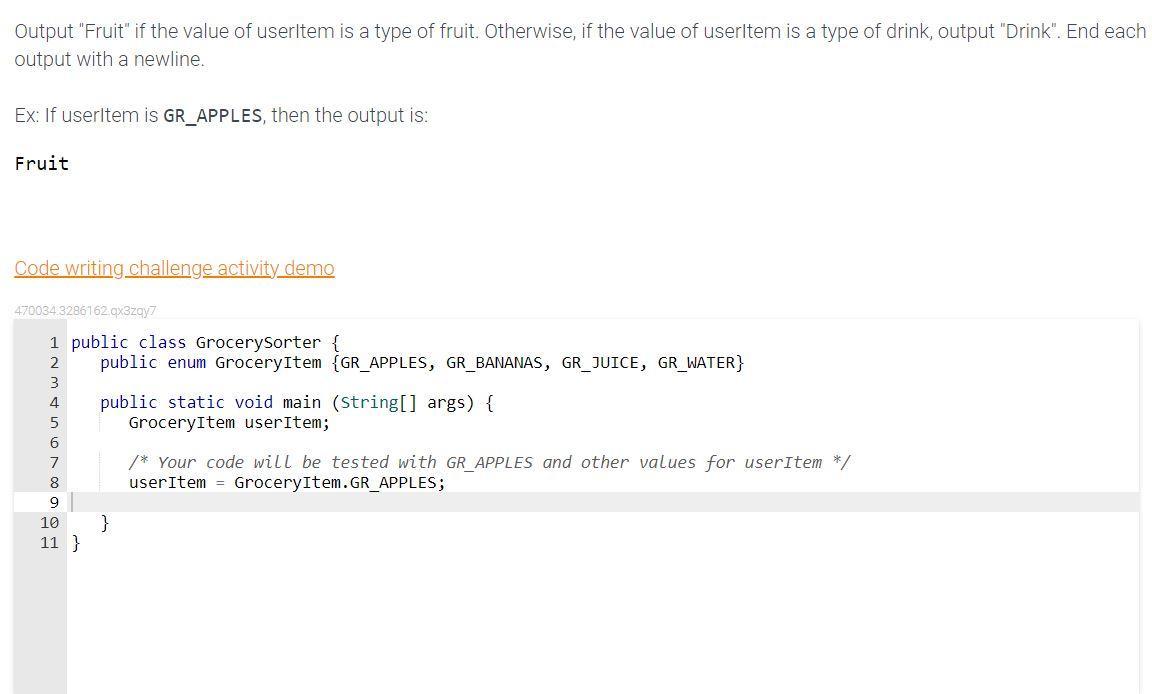
This is in Java.
Description:
Output "Fruit" if the value of userItem is a type of fruit. Otherwise, if the value of userItem is a type of drink, output "Drink". End each output with a newline.
Ex: If userItem is GR_APPLES, then the output is:
Fruit
Answers
Explanation:
public class GrocerySorter {
public static void main(String[] args) {
GroceryItem item = new GroceryItem("GR_APPLES", 1.99);
String itemName = item.getName();
if(itemName.startsWith("GR_")) {
System.out.println("Fruit\n");
} else {
System.out.println("Drink\n");
}
}
}
The program illustrates the use of conditional statements. Conditional statements in programming are statements that may or may not be executed. Their execution depends on the truth value of the condition.
What is program in Python?The program in Python, where comments are used to explain each line is as follows
#This gets input from the user
userItem = input("Item: ")
#This checks if user input is GR_APPLES or GR_BANANAS
if(userItem == "GR_APPLES" or userItem == "GR_BANANAS"):
#If yes, the program prints Fruit
print("Fruit")
#if otherwise, this checks if user input is GR_JUICE or GR_WATER
elif (userItem == "GR_JUICE" or userItem == "GR_WATER"):
#If yes, the program prints Drink
print("Drink")
#If otherwise
else:
#This prints Invalid
print("Invalid")
See attachment for sample run
Therefore, The program illustrates the use of conditional statements. Conditional statements in programming are statements that may or may not be executed. Their execution depends on the truth value of the condition.
Read more about conditional statements at:
brainly.com/question/4211780
#SPJ2
How are centralized computing and cloud computing similar?
Answers
The centralized computing and cloud computing similar because Cloud as well as they other both operates a centralized management system.
What are the similarities between cloud computing and grid computing?The Grid and Cloud are known to have similarities like both of them are known to be used to share recourses such as the computational power, storage, and others.
Hence, The centralized computing and cloud computing similar because Cloud as well as they other both operates a centralized management system.
Learn more about cloud computing from
https://brainly.com/question/19057393
#SPJ1
FILL IN THE BLANK ________ allows collaborators to access an online virtual meeting room where they can present PowerPoint slides, share files, demonstrate products, and interact with participants in real time.
Answers
"Web conferencing" allows participants to connect to a virtual conference space where they can share files, show off products, present PowerPoint slides, and communicate with one other in real time.
Define the term Web conferencing and its features?Any online gathering with at least two people who are in separate locations is considered a web conference.
Anywhere on the world could be one of these participants. They can see, hear, and speak to each other in real-time with conferencing software and a dependable internet connection. Although web conferencing may appear self-explanatory, it differs from standard conference calls. The primary distinction is that web conferencing tools, often known as web conferencing platforms as well as online meeting software, enable face-to-face remote conferences or video conversations over the Internet.With the free web conferencing package from Dialpad Meetings, you get:
endless video conferences10 people maximum per conference callfictitious backgroundsUnlimited recordings of audioNo downloads required for immediate participation through desktop or smartphone browserTo know more about the Web conferencing, here
https://brainly.com/question/3879633
#SPJ4
explain about your business and sales after covid 19 pandemic
Answers
The global economy has undergone tremendous disruption brought about by the pandemic, with some sectors being grievously hit while others have fresh openings.
What are the effects?Its aftermath has hastened the conversion to e-business, remote work, and digital remodeling as firms have poured significant capital into technological solutions in order to ameliorate compliance to the current state of affairs. Companies further evaluated their delivery strategies and diversified places from where they sourced materials so as to minimize any single nation's or region’s influence.
Altogether, the pandemic has showcased the indispensable value of pliancy, robustness, and novelty for business operations, and those entities that were able to adeptly conform to the existing condition are predicted to thrive in the post-COVID period.
Read more about business here:
https://brainly.com/question/24553900
#SPJ1
What symbol should you look for to determine who owns the intellectual property of a website?
Answers
Answer:
the logo of the company or corporation
Explanation:
Usually, the symbol that determines who owns the intellectual property is the logo of the company or corporation. The logo of a website is technically the logo of the brand which has the rights to all of the information represented on the site and ultimately the intellectual property of the site itself. Since there are various board members that usually make up the company that owns the intellectual property, the logo is a way of representing all of these members as a single entity.
Answer: D the copyright symbol
Explanation: I hope this helps you out
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
C/C++ does not allow arrays to be manipulated as a whole; each element must be set or accessed individually. To make operating on whole arrays or contiguous portions of arrays easier, write the following utility functions.
void arrayFill(int *p,int n,int v); // fill n elements starting a p with the value v
void arrayReverse(int *p,int n); // reverse the order of n elements starting a p
void arrayCopy(int *p,int n,int *q); // copy n consecutive elements from q to p
bool arrayEqual(int *p,int n,int *q); // iff n consecutive elements of p and q are equal
You will need to write your own test code to make sure your functions work correctly. The follow is an example of how to do this, but it is unlikely to find all errors.
#include
int main()
{
int a[20] = {1,2,3,4,5,6,7};
arrayReverse(a+2,3);
assert(a[2] == 5);
assert(a[4] == 3);
arrayCopy(a+7,6,a+1);
assert(a[12]==7);
arrayFill(a+13,6,-1);
int b[20] = {1,2,5,4,3,6,7,2,5,4,3,6,7,-1,-1,-1,-1,-1,-1};
assert(arrayEqual(a,20,b));
}
NOTE: Your submission may not use the array index operator ([]). You must use pointers.
Submit your functions without main().
Answers
Answer:
#include <assert.h>
void arrayFill(int *p, int n, int v)
{
for (int i = 0; i < n; i++)
{
*p = v;
p++;
}
}
void arrayReverse(int *p, int n)
{
int *q = p + n - 1;
while (p < q)
{
int temp = *p;
*p = *q;
*q = temp;
p++;
q--;
}
}
void arrayCopy(int *p, int n, int *q)
{
for (int i = 0; i < n; i++)
{
*p = *q;
p++;
q++;
}
}
bool arrayEqual(int *p, int n, int *q)
{
for (int i = 0; i < n; i++)
{
if (*p != *q)
{
return false;
}
p++;
q++;
}
return true;
}
Explanation:
The code includes 4 utility functions to make operating on arrays in C++ easier:
arrayFill: This function takes a pointer to an integer (p), the number of elements to be filled (n), and a value to fill the elements with (v). It uses a for loop to iterate through the n elements, starting from the pointer p, and sets each element to the value v.arrayReverse: This function takes a pointer to an integer (p) and the number of elements to be reversed (n). It initializes a pointer q to point to the last element of the array (p + n - 1). Then it uses a while loop to iterate through the elements, starting from the first (p) and last (q) elements, swapping the values of each pair of elements until the pointers meet in the middle.arrayCopy: This function takes two pointers to integers (p and q) and the number of elements to be copied (n). It uses a for loop to iterate through the n elements, starting from the pointer q, and copies each element to the corresponding location pointed to by p.arrayEqual: This function takes two pointers to integers (p and q) and the number of elements to be compared (n). It uses a for loop to iterate through the n elements, starting from the pointers p and q, and compares each pair of elements. If any pair of elements are not equal, the function returns false. If all pairs of elements are equal, the function returns true.program a macro on excel with the values: c=0 is equivalent to A=0 but if b is different from C , A takes these values
Answers
The followng program is capable or configuring a macro in excel
Sub MacroExample()
Dim A As Integer
Dim B As Integer
Dim C As Integer
' Set initial values
C = 0
A = 0
' Check if B is different from C
If B <> C Then
' Assign values to A
A = B
End If
' Display the values of A and C in the immediate window
Debug.Print "A = " & A
Debug.Print "C = " & C
End Sub
How does this work ?In this macro, we declare three integer variables: A, B, and C. We set the initial value of C to 0 and A to 0.Then, we check if B is different from C using the <> operator.
If B is indeed different from C, we assign the value of B to A. Finally, the values of A and C are displayed in the immediate window using the Debug.Print statements.
Learn more about Excel:
https://brainly.com/question/24749457
#SPJ1
Is the use of technology to control human behavior a necessary evil or an
unethical breach of privacy and freedom?
Answers
Answer:
The use of technology to control human behavior is a very contentious topic and the answer to this question depends on the individual's opinion and values. Some may argue that technology can be used to limit freedom, however, it can also be used to protect people from harm, such as in the case of automated speed cameras limiting the speed of drivers to prevent accidents. Others may argue that the use of technology to control behavior is an unethical breach of privacy and freedom as it can be used to monitor and restrict people's actions. Ultimately, it is up to the individual to decide whether the use of technology to control human behavior is a necessary evil or an unethical breach of privacy and freedom.
Is this right? I’m not sure

Answers
what specific Philippine law discusses copyright? elaborate?
Answers
Answer: Republic Act No. 8293 "Intellectual Property Code of the Philippines".
Explanation:
The Republic Act No. 8293 is the Intellectual Property Code of the Philippines. It is the Philippine law that discusses copyright. This law protects copyrights, intellectual property, trademarks, and patents.
Examples of copyright that are protected under the law are photographic works, drawings, audiovisual works, and cinematographic works.
Can someone answer the question s please

Answers
Answer:
1. it the point of art and they do it for fun
2. Yes I done that a couple of time and the reason why is because it fun and it u that is acknowledging your own work that u done for later memories even tho you know it wont last long.
3. I would love to create a sand castle I think or something about kpop
3. Consider the organization you are currently working in and explain this organization from systems characteristics perspectives particularly consider objective, components (at least three) and interrelationships among these components with specific examples.
Answers
The organization i worked for from systems characteristics perspectives is based on
Sales and OperationsMarketing and Customer RelationsWhat is the systems characteristics perspectivesIn terms of Sales and Operations: This part involves tasks connected to managing inventory, moving goods, organizing transportation, and selling products. This means getting things, storing them, sending them out, and bringing them to people.
Lastly In terms of Marketing and Customer Relations: This part is all about finding and keeping customers by making plans for how to sell products or services.
Read more about systems characteristics perspectives here:
https://brainly.com/question/24522060
#SPJ1
(d) Assume charArray is a character array with 20 elements stored in memory and its starting memory address is in $t5. What is the memory address for element charArray[5]?
Answers
Answer:
$t5 + 5
Explanation:
Given that ;
A character array defines as :
charArray
Number of elements in charArray = 20
Starting memory address is in $t5
The memory address for element charArray[5]
Memory address for charArray[5] will be :
Starting memory address + 5 :
$t5 + 5