.
Step 1: Input a positive integer A and let B = 1
Step 2: Let C = A/B. If C is an Integer print B
Step 3: If B
otherwise go to step 4.
Step 4: Stop
.
Let's try this algorithm for A = 6
Answers
Answer:
The value of B (which is 1) will be printed
Explanation:
Given
The above algorithm
A = 6
Required
Determine the outcome
Step 1: A = 6, B = 1
Step 2: C = A/B = 6/1 = 6
Step 3: If C is an integer print B.
Is 6 an integer? Yes.
So, the value of B (which is 1) will be printed
Related Questions
website is a collection of (a)audio files(b) image files (c) video files (d)HTML files
Answers
Website is a collection of (b) image files (c) video files and (d)HTML files
What is websiteMany websites feature a variety of pictures to improve aesthetic appeal and provide visual substance. The formats available for these image files may include JPEG, PNG, GIF, or SVG.
To enhance user engagement, websites can also introduce video content in their files. Web pages have the capability to display video files either by embedding them or by providing links, thereby enabling viewers to watch videos without leaving the site. Various formats such as MP4, AVI and WebM can be utilized for video files.
Learn more about website from
https://brainly.com/question/28431103
#SPJ1
in Programming in C, if
int p[2] [3] [4] = {
{{7, 4}, {0, -3}, {23, 12}},
{{13, 4}, {5, 9}, {3, 1}}};
Address of P= 10245 and assume that the address is increment by 2 bytes.
Find the output for the following:
printf ("%d\n",p);
printf ("%d\n",**p);
printf ("%d\n",*(*(*(p+1)+2)));
printf ("%d\n",*(*(p+2)));
printf ("%d\n",*(*(p+1)+1));
printf("%d",sizeof(int));
Answers
Using the knowledge in computational language in C++ it is possible to write a code that operator takes precedence over the * operator, and the () operators take precedence over everything else.
Writting the code:#include "stdio.h"
int main() {
static int x = 5;
static int *p = &x;
printf("(int) p => %d\n",(int) p);
printf("(int) p++ => %d\n",(int) p++);
x = 5; p = &x;
printf("(int) ++p => %d\n",(int) ++p);
x = 5; p = &x;
printf("++*p => %d\n",++*p);
x = 5; p = &x;
printf("++(*p) => %d\n",++(*p));
x = 5; p = &x;
printf("++*(p) => %d\n",++*(p));
x = 5; p = &x;
printf("*p++ => %d\n",*p++);
x = 5; p = &x;
printf("(*p)++ => %d\n",(*p)++);
x = 5; p = &x;
printf("*(p)++ => %d\n",*(p)++);
x = 5; p = &x;
printf("*++p => %d\n",*++p);
x = 5; p = &x;
printf("*(++p) => %d\n",*(++p));
return 0;
}
See more about C++ at brainly.com/question/19705654
#SPJ1
![in Programming in C, if int p[2] [3] [4] = { {{7, 4}, {0, -3}, {23, 12}}, {{13, 4}, {5, 9}, {3, 1}}};Address](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/AJYOLfu4Ex5sKQRwEmxKTawrGrLCtP1h.png)
1. State three modules in HansaWorld and briefly describe what each is used for. (6)
2. With an example, explain what settings are used for. (3)
3. What is Personal Desktop and why is it good to use? Mention two ways in which an
entry can be deleted from the personal desktop. (6)
Describe how you invalidate a record in HansaWorld (3)
Briefly explain what specification, paste special and report windows are used for. (6)
How many reports can you have on the screen at once? How many reports does
HansaWorld have? (4)
4.
5.
6.
7.
8.
9.
Describe any two views of the Calendar and how you can open them (4)
Describe three (3) ways in which records can be attached to Mails. (6)
Describe the basic SALES PROCESS where there is no stock involved and how the
same is implemented in HansaWorld. (12)
Answers
Financials: this module is used for accounting and financial management, including accounts receivable, accounts payable, general ledger, and budgeting.
Logistics: this module is used for managing inventory and supply chain, including purchase orders, sales orders, stock control, and manufacturing.
CRM: this module is used for managing customer relationships, including sales and marketing activities, customer service, and support.
Settings are used to configure various aspects of the system, such as user preferences, system defaults, and module settings. For example, a user can set their default currency, language, and font size. Settings can be accessed and modified through the "Settings" menu or through the relevant module's settings window.
Personal Desktop is a customizable dashboard that displays relevant information and provides quick access to frequently used functions. It is good to use because it can increase productivity and efficiency by allowing users to access important data and functions quickly. Two ways to delete an entry from the personal desktop are by right-clicking on the entry and selecting "Delete" or by dragging the entry to the trash can icon.
To invalidate a record in HansaWorld, the user can either delete the record or mark it as inactive. To mark a record as inactive, the user can go to the "General" tab of the relevant record and uncheck the "Active" checkbox.
Specification windows are used to define criteria for filtering data or generating reports. Paste Special windows are used to copy and paste data between different parts of the system or to import data from external sources. Report windows are used to view and print reports generated by the system.
The number of reports that can be on the screen at once depends on the user's screen size and resolution. HansaWorld has a large number of built-in reports for each module, but users can also create custom reports using the Report Designer.
Two views of the Calendar in HansaWorld are the Day view and the Month view. The Day view displays a detailed view of the events for a single day, while the Month view displays a calendar grid for a whole month. To open the Day view, the user can click on a specific date in the Month view, or they can select "Day" from the View menu. To open the Month view, the user can select "Month" from the View menu.
Three ways in which records can be attached to Mails are:
Drag and drop: the user can drag a record from the relevant module and drop it onto the Mail window.
Copy and paste: the user can copy a record from the relevant module and paste it into the Mail window.
Link: the user can insert a hyperlink to the record in the Mail window.
The basic sales process where there is no stock involved typically involves the following steps:
The customer requests a quote or makes a purchase order.
The salesperson creates a sales order based on the quote or purchase order.
The salesperson generates an invoice based on the sales order and sends it to the customer.
The customer pays the invoice.
The salesperson records the payment and closes the transaction.
In HansaWorld, this process is implemented through the Sales module. The salesperson can create a quote, sales order, and invoice in the relevant windows, and record the payment in the Payments window. The system can also generate reports and provide real-time updates on inventory levels, pricing, and other relevant data.
working with the tkinter(python) library
make the window you create always appear on top of other windows. You can do this with lift() or root.attributes('-topmost', ...), but this does not apply to full-screen windows. What can i do?
Answers
To make a tkinter window always appear on top of other windows, including full-screen windows, you must use the wm_attributes method with the topmost attribute set to True.
How can I make a tkinter window always appear on top of other windows?By using the wm_attributes method in tkinter and setting the topmost attribute to True, you can ensure that your tkinter window stays on top of other windows, even when they are in full-screen mode.
This attribute allows you to maintain the window's visibility and prominence regardless of the current state of other windows on your screen.
Read more about python
brainly.com/question/26497128
#SPJ1
In Coral Code Language - A half-life is the amount of time it takes for a substance or entity to fall to half its original value. Caffeine has a half-life of about 6 hours in humans. Given the caffeine amount (in mg) as input, output the caffeine level after 6, 12, and 18 hours.
Ex: If the input is 100, the output is:
After 6 hours: 50.0 mg
After 12 hours: 25.0 mg
After 18 hours: 12.5 mg
Note: A cup of coffee has about 100 mg. A soda has about 40 mg. An "energy" drink (a misnomer) has between 100 mg and 200 mg.
Answers
To calculate the caffeine level after 6, 12, and 18 hours using the half-life of 6 hours, you can use the formula:
Caffeine level = Initial caffeine amount * (0.5 ^ (time elapsed / half-life))
Here's the Coral Code to calculate the caffeine level:
function calculateCaffeineLevel(initialCaffeineAmount) {
const halfLife = 6; // Half-life of caffeine in hours
const levelAfter6Hours = initialCaffeineAmount * Math.pow(0.5, 6 / halfLife);
const levelAfter12Hours = initialCaffeineAmount * Math.pow(0.5, 12 / halfLife);
const levelAfter18Hours = initialCaffeineAmount * Math.pow(0.5, 18/ halfLife);
return {
'After 6 hours': levelAfter6Hours.toFixed(1),
'After 12 hours': levelAfter12Hours.toFixed(1),
'After 18 hours': levelAfter18Hours.toFixed(1)
};
}
// Example usage:
const initialCaffeineAmount = 100;
const caffeineLevels = calculateCaffeineLevel(initialCaffeineAmount);
console.log('After 6 hours:', caffeineLevels['After 6 hours'], 'mg');
console.log('After 12 hours:', caffeineLevels['After 12 hours'], 'mg');
console.log('After 18 hours:', caffeineLevels['After 18 hours'], 'mg');
When you run this code with an initial caffeine amount of 100 mg, it will output the caffeine levels after 6, 12, and 18 hours:
After 6 hours: 50.0 mg
After 12 hours: 25.0 mg
After 18 hours: 12.5 mg
You can replace the initialCaffeineAmount variable with any other value to calculate the caffeine levels for different initial amounts.
for similar questions on Coral Code Language.
https://brainly.com/question/31161819
#SPJ8
Look at the attached photos! I need urgent help! Please answer each of the questions. If you have any, I will take them!


Answers
The greatest challenge the analyst is likely to face in solving this problem is A. Making sure the price and volume numbers are accurate
The skill practiced is Consensus building.
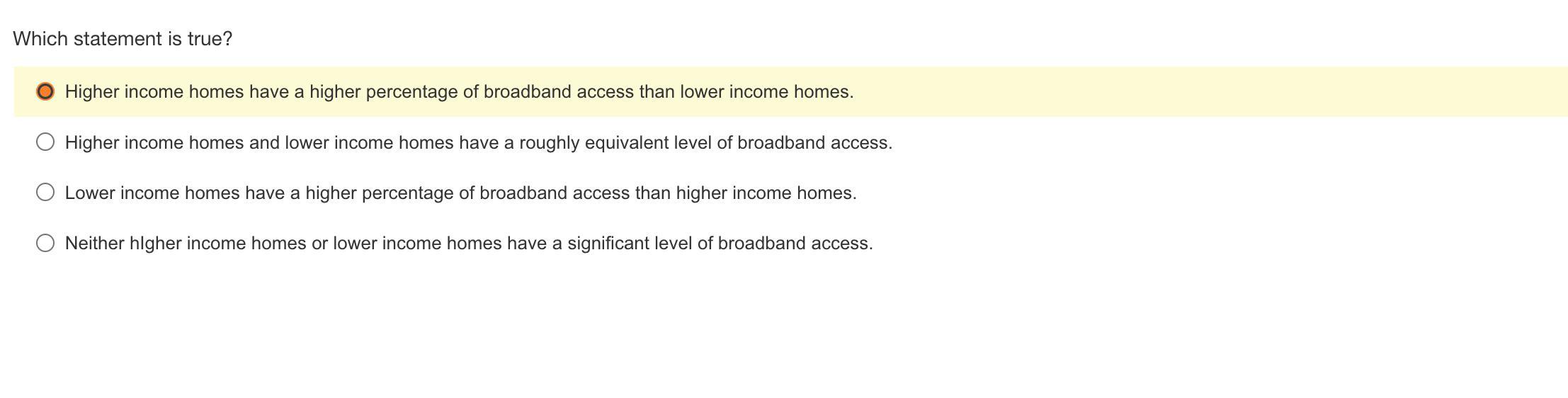
The true statement is that A. Higher income homes have a higher percentage of broadband access than lower income homes
How to convey the informationThe greatest challenge the analyst is likely to face in solving this problem is likely to be finding meaningful patterns in the stock market data that can accurately predict future behavior.
Higher income homes have a higher percentage of broadband access than lower income homes. This disparity in broadband access is commonly referred to as the "digital divide".
Learn more about market on:
https://brainly.com/question/25369230
#SPJ1
general requirements for tools and equipment maintenance
Answers
Explanation:
Clean, Inspect and Care for Tools. Make it a habit to clean tools after each use before you return them to storage. Wipe them down with a rag or old towel and be sure they are free of dust, grease and debris before you put them into their proper places.
What does the following code print?
s = 'theodore'
print(s[:4])
Answers
Answer:
The code prints "theo".
Explanation:
Select the recommended design practice that applies to a website using images for main site navigation.
a. provide alternative text for the images
b. place text links at the bottom of the page
c. both a and b
d. no special considerations are needed
Answers
The recommended design practice that applies to a website using images for main site navigation are both a and b.
What would be a wise design suggestion for text hyperlinks?Good hyperlinks should stand out on a web page from other sorts of content. Dr. Nielsen, a usability researcher, found that underlining hyperlinks to indicate that the text is clickable and making them a distinct colour from other forms of text on a web page both increase their effectiveness.There are three different types of organisational structures: matrix, sequential, and hierarchical.The suggested design strategy for a website that uses photos for the primary site navigation.
a. provide alternative text for the images
b. place text links at the bottom of the page
To learn more about alternative text refer to:
https://brainly.com/question/28580148
#SPJ4
Looking at the data in the spreasheet above, what is the user trying to keep track of? Who might this person be?
pls help I'll give you 50 brainlist if it's correct

Answers
Answer:
The user is trying to keep track of prices of fruits. The person might be a fruit saler
ProjectSTEM CS Python Fundamentals - Lesson 3.3 Question 2 - RGB Value:
Test 6: Using 256 for all inputs, this test case checks that your program has no output. / Examine the upper condition for each color.
Test 10: This test case sets the input for blue beyond the limit, while red and green are below. It checks if your program's output contains “Blue number is not correct”, but not “Red number is not correct”, or “Green number is not correct” / Check that you output the correct phrase when the number is outside the range. Make sure that only the incorrect color phrases are output.

Answers
While CMYK is frequently used to print out colors, RGB is utilized when the colors need to be presented on a computer monitor (such as a website).Make the variable "alien color" and give it the values "green," "yellow," or "red." To determine whether the alien is green, create an if statement.
How does Python find the RGB color?Colors can only be stored in Python as 3-Tuples of (Red, Green, Blue). 255,0,0 for red, 0 for green, and 255,0 for blue (0,0,255) Numerous libraries use them. Of course, you may also create your own functions to use with them.The rgb to hex() function, which takes three RGB values, is defined in line 1.The ":X" formatter, which automatically converts decimal data to hex values, is used in line 2 to construct the hex values. The outcome is then returned.Line 4 is where we finally call the function and supply the RGB values.Verify the accuracy of the RGB color code provided. While CMYK is frequently used to print out colors, RGB is utilized when the colors need to be presented on a computer monitor (such as a website).To learn more about Python refer to:
https://brainly.com/question/26497128
#SPJ1
true or false. Two of the main differences between storage and memory is that storage is usually very expensive, but very fast to access.
Answers
Answer:
False. in fact, the two main differences would have to be that memory is violate, meaning that data is lost when the power is turned off and also memory is faster to access than storage.
6n^3+n-2 C++ code using Dev
i need only the code
Answers
Answer:
A = 6*pow(n,3) +n - 2
Explanation:
I'm not sure if this what you need but that's what I can help you with :)
Please have a look at the screenshot below

Answers
Because of the network and recovery time
Plz give brainliest
Which of the following statements is true when you use MySQL Workbench to run INSERT, UPDATE, and DELETE statements?
If autocommit mode is on you can rollback the changes by clicking on the Rollback button.
By default, the changes are automatically committed to the database.
By default, the changes are rolled back when you exit MySQL Workbench unless you commit them.
If autocommit mode is on you can commit the changes by clicking on the Commit button.
Answers
All of the following statements are true when you use MySQL Workbench to run INSERT, UPDATE, and DELETE statements:
Explanation in Detail:
In MySQL Workbench, autocommit mode determines whether changes made to the database are automatically committed or rolled back when you execute an INSERT, UPDATE, or DELETE statement. By default, autocommit mode is turned on, which means that changes are automatically committed to the database as soon as they are made.
If you want to be able to roll back changes made to the database, you can turn off autocommit mode by clicking on the "Autocommit" button in the MySQL Workbench toolbar. This will allow you to execute multiple statements without committing them to the database until you are ready. You can then commit or roll back the changes as needed by clicking on the "Commit" or "Rollback" button in the toolbar.
To know more about MySQL Workbench, visit: https://brainly.com/question/29326730
#SPJ4
What are some good things when using technology on social media?
Answers
Answer:
Well first thing is communication because on many platforms such as IG or any other media, they have places where you can chat with other people or comment on their stuff
Next is information sharing where you can see what is happening in our world or the area you live like the news basically
Learning purposes: Some people like professional teachers make videos for those who are struggling in certain subjects so that they can understand how to do better. Also not only that, other people can go ahead in learning.
Creativity: Yes, this one is probably one of the greatest things because it is where people express themselves and showcase their talents, such as music, art, singing, writing, or even excelling in sports.
Business opportunities: This is where people would find jobs of their interest promoting services and building their personal brand.
write a recirsive function named productsof odds that accepts a tuple
Answers
Answer:
def productOfOdds(t):
if len(t) == 1:
if t[0] % 2 == 1:
return t[0]
else:
return 1
else:
if t[0] % 2 == 1:
return t[0] * productOfOdds(t[1:])
else:
return productOfOdds(t[1:])
t = (1, 2, 3, 4, 5, 6, 7, 8, 9)
print("Product of odd elements:", productOfOdds(t)
program a macro on excel with the values: c=0 is equivalent to A=0 but if b is different from C , A takes these values
Answers
The followng program is capable or configuring a macro in excel
Sub MacroExample()
Dim A As Integer
Dim B As Integer
Dim C As Integer
' Set initial values
C = 0
A = 0
' Check if B is different from C
If B <> C Then
' Assign values to A
A = B
End If
' Display the values of A and C in the immediate window
Debug.Print "A = " & A
Debug.Print "C = " & C
End Sub
How does this work ?In this macro, we declare three integer variables: A, B, and C. We set the initial value of C to 0 and A to 0.Then, we check if B is different from C using the <> operator.
If B is indeed different from C, we assign the value of B to A. Finally, the values of A and C are displayed in the immediate window using the Debug.Print statements.
Learn more about Excel:
https://brainly.com/question/24749457
#SPJ1
What kind of variable is measured using 2 different values
Answers
A variable that is measured using two different values can be classified as a categorical variable or a binary variable.
Depending on the nature of the values, a variable can be classified as:
1)Categorical Variable: If the two different values represent distinct categories or groups, the variable is considered categorical. In this case, the variable can take on only one of two possible values.
Examples include gender (male/female), presence/absence of a certain trait, yes/no responses, or any other classification with mutually exclusive categories.
2)Binary Variable: If the two different values represent two distinct outcomes or states, the variable can be classified as a binary variable. Binary variables are often used in statistics, machine learning, and hypothesis testing.
Examples include success/failure, true/false, 1/0, or positive/negative results.
It's important to note that the distinction between categorical and binary variables lies in the nature of the values and the underlying meaning they convey.
Categorical variables can have more than two categories, while binary variables specifically refer to variables with only two possible values.
For more questions on variable
https://brainly.com/question/28248724
#SPJ8
Creating ________ means creating awareness and a sense of anticipation about a company and its offerings.
A) ruckus
B) noise
C) clatter
D) clamor
E) buzz
Answers
1. A network administrator was to implement a solution that will allow authorized traffic, deny unauthorized traffic and ensure that appropriate ports are being used for a number of TCP and UDP protocols.
Which of the following network controls would meet these requirements?
a) Stateful Firewall
b) Web Security Gateway
c) URL Filter
d) Proxy Server
e) Web Application Firewall
Answer:
Why:
2. The security administrator has noticed cars parking just outside of the building fence line.
Which of the following security measures can the administrator use to help protect the company's WiFi network against war driving? (Select TWO)
a) Create a honeynet
b) Reduce beacon rate
c) Add false SSIDs
d) Change antenna placement
e) Adjust power level controls
f) Implement a warning banner
Answer:
Why:
3. A wireless network consists of an _____ or router that receives, forwards and transmits data, and one or more devices, called_____, such as computers or printers, that communicate with the access point.
a) Stations, Access Point
b) Access Point, Stations
c) Stations, SSID
d) Access Point, SSID
Answer:
Why:
4. A technician suspects that a system has been compromised. The technician reviews the following log entry:
WARNING- hash mismatch: C:\Window\SysWOW64\user32.dll
WARNING- hash mismatch: C:\Window\SysWOW64\kernel32.dll
Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
a) Rootkit
b) Ransomware
c) Trojan
d) Backdoor
Answer:
Why:
5. An instructor is teaching a hands-on wireless security class and needs to configure a test access point to show students an attack on a weak protocol.
Which of the following configurations should the instructor implement?
a) WPA2
b) WPA
c) EAP
d) WEP
Answer:
Why:
Answers
Network controls that would meet the requirements is option a) Stateful Firewall
Security measures to protect against war driving: b) Reduce beacon rate and e) Adjust power level controlsComponents of a wireless network option b) Access Point, StationsType of malware most likely installed based on log entry option a) RootkitConfiguration to demonstrate an attack on a weak protocol optio d) WEPWhat is the statement about?A stateful firewall authorizes established connections and blocks suspicious traffic, while enforcing appropriate TCP and UDP ports.
A log entry with hash mismatch for system files suggest a rootkit is installed. To show a weak protocol attack, use WEP on the access point as it is an outdated and weak wireless network security protocol.
Learn more about network administrator from
https://brainly.com/question/28729189
#SPJ1
It is not really important to organize your photos because you know that they are on your computer. (TRUE/FALSE)
Answers
Answer:
It is important
Explanation:
if not it'll be hard to find them in a cluttered mess of scattered photos
Answer: FALSE
Explanation: it is false because you can lose all those photos or even just misplace some photos that are gonna be lost.
Which is an example of correct HTML?
<h1>This is a heading </h1>
</h1>This is a heading<h2>
</h1>This is a title</h1>
<p/>This is a title</p>
please help! god bless you all

Answers
Answer: The first option
Explanation: In HTML, tags are used to classify the format of text between them. The correct usage of a tag is shown in the first option, with the first tag, <h1>, proclaiming that the following text is a part of the first header (hence h1), and the second tag proclaiming the conclusion of the first (the forward slash before the h1 in the second tag shows that the first tag is being concluded, and no text past that point pertains to the tags).
Answer:
a is the answer i took same quiz
Explanation:
Consider the two lists A and B. List A is an anagram of list B if the following two conditions are true: 1.list A and list B have the same number of elements 2.each element of list A occurs the same number of times in list A and list BFor example, [3, 2, 4, 1, 2] and [2, 2, 3, 1, 4] are anagram of each other, but [2, 3, 1, 2] and [1, 3, 1, 2] are not. Write a function named isAnagram that takes two lists of integers as parameters: lstA and lstB. The function isAnagram should return the bool value True if lstA is an anagram of lstB and False otherwise. The following is an example of correct output: >>> print(isAnagram([14, 10, 19], [10, 14, 19]))True
Answers
Answer:
cdacaddacdbbbbbacddebb
Explanation:
How many ways can we write a list of 6 numbers from (1, 2, 3, 4, 5, 6, 7, 8) without repeating any?
Answers
Explanation:
\( \binom{n}{\\ k} = \binom{6}{8} = \frac{8 \times 7 \times 6 \times 5 \times 4 \times 3}{6 \times 5 \times 4 \times 3 \times 2} = 28\)
We divide by factorial of 6 (!6) what is 6×5×4×3×2×1 so that there is no repetition.
Answer:
Explanation:
Number of combinations:
\(C_{8}^6 = \frac{8!}{(8-6)!*6! } = \frac{6!*7*8}{2!*6! } = \frac{7*8}{1*2} = \frac{56}{2}=28\)
Write a function that reads from a file the name and the weight of each person in pounds and calculates the equivalent weight in kilograms. Output the Name, weightLB, and weightKG in that order. Format your output to two decimal places. (1 kilogram
Answers
Answer:
#include <iostream>
#include <fstream>
#include <iomanip>
using namespace std;
int main(){
string name;
double weightKg, weightPd;
cout<< fixed << setprecision(2);
fstream myFile("filename.txt");
while (getline( myFlie, name, weightPd)){
weightKg = weight * 0.453592;
cout<< name << weightPd <<weightKg;
}
myFile.close();
}
Explanation:
The C++ source code reads in the content of a file that has a name and weight value in pounds and outputs the name, weight in pounds and the weight in kilograms.
Please don't answer if you don't know Type the correct answer in the box
. Spell all words correctly. How does SQA differ from SQC? SQA involves activities to evaluate software processes, and SQC involves activities that ensure quality software.
Answers
Software Quality Assurance (SQA) and Software Quality Control (SQC) are two distinct aspects of quality management in software development, each with its own focus and activities.
How different are they?SQA encompasses efforts directed toward assessing and enhancing the procedures of software development at every stage. The main emphasis is on guaranteeing that appropriate techniques, norms, and protocols are adhered to in order to create software of superior quality. SQA encompasses various tasks, including scrutinizing requirements, conducting process audits, and administering quality control procedures.
Conversely, SQC pertains to actions that prioritize assuring the quality of the actual software product. This involves employing methods such as testing, inspections, and reviews in order to detect flaws and guarantee that the software satisfies the stated demands and standards. The goal of SQC is to identify and rectify any shortcomings or irregularities within the software product.
To put it succinctly, SQA focuses on assessing and enhancing the manner in which software is developed, while SQC is primarily focused on verifying the excellence of the resulting software product. SQC and SQA both play a vital role in attaining an optimum level of software quality.
Read more about software here:
https://brainly.com/question/28224061
#SPJ1
when analyzing threats, which of the following would be classified a low threat? A. A flood in a Florida data center B. A terrorist attack on a buildinh in california c. Hurricane damage to an electrical generatinh facility in lowa D. RA social engineering attack on a centers for Disease Control and Prevention
Answers
When analyzing threats, the following occurrence would be classified as a low threat: C. hurricane damage to an electrical generating facility in lowa.
What is a low threat?A low threat can be defined as a type of threat that is not likely to cause failure, harm, or severe injury, especially because it is characterized by minimal (low) risk.
In this context, we can infer and logically deduce that hurricane damage to an electrical generating facility in lowa would be classified as a low threat when analyzing threats.
Read more on low threat here: https://brainly.com/question/8066984
#SPJ1
Programming style refers to the way a programmer uses elements such as identifiers, spaces, and blank lines
Answers
Answer
Absolutely true.
Explanation
i.e:
bool test = false;
bool test=false;
bool bTest=false;
bool bTest = false;
if(test) {
}
if (test) {
}
if(test)
{
}
if (test)
{
}
if ( test )
{
}
Style can refer to quite a bit of things but that statement is true.
Which of the following is the keyboard command for "paste"?This question is required. *
A
Ctrl + V / Command + V
B
Ctrl + P / Command + P
C
Ctrl + C / Command + C
D
Ctrl + A / Command + A
Answers
Answer:A: Ctrl + V / Command + V
Explanation: