Silicon Valley Killer robot case
From the Randy samuels perspective?
Why is my team's character not responsible for the death of Bart Matthews?
2. Suggest 2 possible actions that my character could have taken to prevent this tragedy:
a) Explain how each of these actions might have changed the final outcome.
b) Are there any sideeffects from implementing the 2 suggested actions?
3. Which character do you think is the most guilty? Only pick one character.
a) Give at least 2 reasons to justify your choice.
Answers
Why is my team not responsible for Bart Matthews' death?
Suggest 2 actions my character could have taken to prevent the tragedy and their possible outcomes.
Pick one character most guilty and give 2 reasons to justify the choice.
From Randy Samuels' perspective, your team's character is not responsible for the death of Bart Matthews because your team followed all the safety regulations and protocols during the design and development of the robot. It was the malfunctioning of the robot's software, which caused the accident.
Two possible actions that your character could have taken to prevent this tragedy are:
a) Implementing a failsafe mechanism in the robot's software to detect any abnormal behavior and shut down the robot automatically to avoid any potential danger. This could have changed the final outcome by preventing the robot from causing harm to Bart Matthews.
b) Conducting regular software maintenance and testing to ensure the robot's software is functioning correctly and is up to date with the latest safety standards. This could have prevented the malfunctioning of the robot's software, which caused the accident.
There could be some side-effects of implementing these suggested actions, such as additional cost and time required for software maintenance and testing, which may delay the delivery of the robot to the customer.
The most guilty character in this case is the CEO of the company that produced the robot, as they failed to ensure that the robot was safe for use and did not have any potential malfunctions. Two reasons to justify this choice are:
a) The CEO had the ultimate responsibility of ensuring the safety of the product and its users, and they failed to do so.
b) The CEO prioritized profits over safety by rushing the product to the market without proper testing and safety measures, which ultimately led to the tragedy.
Learn more about decision making here: brainly.com/question/13244895
#SPJ4
Related Questions
Which number is equivalent to 3e-2?
3
0.3
O 30
my
0.03
Answers
Answer:
0.03
Explanation:
Edge 2020
0.03 is equivalent to 3e-2. Therefore option D is correct.
The notation 3e-2 represents 3 times 10 raised to the power of -2.
In scientific notation, the "e" indicates the exponent, which represents the number of places the decimal point must be moved to obtain the original value.
In this case, the exponent is -2, so we move the decimal point two places to the left.
Thus, 3e-2 is equivalent to 0.03. Option D (0.03) is the correct choice, as it represents the same value as 3e-2, which is three hundredths or 3/100.
Therefore option D 0.03 is correct.
know more about decimal points:
https://brainly.com/question/28338004
#SPJ6
I need help with this question.

Answers
Explanation:
Whilst it is impractical to convert all the numbers to binary, I will explain how binary works to you.
Binary is usually composed of eight bits, each representing a different number.
0000 0000
Each 0 represents a column in an 8-bit binary number. The far-right column starts at 1 and doubles each time you change to the left column.
128 64 32 16 8 4 2 1
0 0 0 0 0 0 0 0
A number 1 means that there is a number in that column whereas a 0 means there isn't, like the normal "0 means off and 1 means on" system. When there is a 1 in every column:
1 1 1 1 1 1 1 1
There can be a maximum value of 255.
For example, the number 79 would be represented in binary as:
128 64 32 16 8 4 2 1
0 1 0 0 1 1 1 1
64 + 8 + 4 + 2 + 1 = 79
Hope this helps!
multichannel retailers struggle to provide an integrated shopping experience because:
Answers
Multichannel retailers face difficulties in providing an integrated shopping experience due to data silos, inconsistent branding, inventory management challenges, channel conflicts, and technological limitations.
How this this so?These obstacles hinder the ability to have a unified view of customer data, maintain consistent branding, manage inventory effectively, coordinate channels, and integrate systems seamlessly.
Overcoming these challenges requires strategic planning, investment in technology, and prioritizing a customer-centric approach for a cohesive shopping experience.
Learn more about multichannel retailers at:
https://brainly.com/question/15690065
#SPJ4
what serves a specific community with common business models, security requirements, and compliance considerations? multiple choice private cloud community cloud hybrid cloud utility computing
Answers
A community cloud serves a specific community with common business models, security requirements, and compliance considerations.
Among the given options, a community cloud is the most suitable choice for serving a specific community with common business models, security requirements, and compliance considerations. A community cloud is a type of cloud computing deployment model that is designed to meet the specific needs of a particular community or group of organizations.
In a community cloud, the infrastructure and resources are shared among organizations within the same community, allowing them to collaborate and benefit from shared services and capabilities. This type of cloud deployment is tailored to address the common requirements, business models, security concerns, and compliance considerations that are specific to that community.
By leveraging a community cloud, organizations within the community can achieve economies of scale, enhanced security measures, and regulatory compliance adherence that are tailored to their specific needs. The community cloud model allows for shared resources while maintaining a level of isolation and customization required by the community members.
In summary, a community cloud is the most suitable cloud deployment model for serving a specific community with common business models, security requirements, and compliance considerations. It provides a shared infrastructure that is customized to meet the specific needs of the community while maintaining security, compliance, and collaboration among its members.
Learn more about security here: https://brainly.com/question/29796699
#SPJ11
You learned in class how to use a named pipe (aka FIFO) and the netcat
(nc) program to turn mdb-lookup-cs3157 into a network server.
mkfifo mypipe
cat mypipe | nc -l some_port_num | /some_path/mdb-lookup-cs3157 > mypipe
Write a shell script that executes the pipeline.
- The name of the script is "mdb-lookup-server-nc.sh"
- A shell script starts with the following line (the '#' is the 1st
character without any leading space):
#!/bin/sh
And the line must be the VERY FIRST LINE in the script.
- You must make the file executable using "chmod" command.
- The script takes one parameter, port number, on which nc will
listen.
- The script should create a named pipe named mypipe-, where
indicates the process ID of the shell running the script. The
named pipe should be removed at the end of the script.
- See section 3.4 in the Bash Reference Manual
(http://www.gnu.org/software/bash/manual/bashref.html) for how to
refer to the arguments and the process ID from your script.
- Because the named pipe gets removed only at the end of the script, if you
quit out of the script by hitting Ctrl-C while it's running, the FIFO will
not get removed. This is ok. You can manually clean up the FIFOs in the
directory. If this annoys you, you can optionally add the following lines
to your script after the first line:
on_ctrl_c() {
echo "Ignoring Ctrl-C"
}
# Call on_ctrl_c() when the interrupt signal is received.
# The interrupt signal is sent when you press Ctrl-C.
trap on_ctrl_c INT
Answers
The script takes one parameter, which is the port number on which nc will listen. The script should create a named pipe named mypipe-, where indicates the process ID of the shell running the script. The named pipe should be removed at the end of the script. The script starts by defining an interrupt handler that ignores Ctrl-C.
To create a shell script called "mdb-lookup-server-nc.sh" that executes the pipeline with the given specifications, follow these steps:1. Open a text editor and add the following lines of code to create the shell script:
```bash
#!/bin/sh
on_ctrl_c() {
echo "Ignoring Ctrl-C"
}
# Call on_ctrl_c() when the interrupt signal is received.
# The interrupt signal is sent when you press Ctrl-C.
trap on_ctrl_c INT
port_number="$1"
pipe_name="mypipe-$$"
mkfifo "$pipe_name"
cat "$pipe_name" | nc -l "$port_number" | /some_path/mdb-lookup-cs3157 > "$pipe_name"
rm "$pipe_name"
```
2. Save the file as "mdb-lookup-server-nc.sh".
3. Open a terminal and navigate to the directory where the script is saved.
4. Make the file executable using the "chmod" command:
```bash
chmod +x mdb-lookup-server-nc.sh
```
Now you can run the script with the specified port number as its argument:
```bash
./mdb-lookup-server-nc.sh some_port_num
```
It then checks the number of arguments passed to the script. If there is not exactly one argument, the script prints an error message and exits.The script then sets the b variable to the first argument, creates a FIFO with a unique name, and starts the pipeline. When the pipeline exits, the script removes the FIFO.This script will create a named pipe called "mypipe-", execute the pipeline with netcat listening on the given port number, and remove the named pipe at the end. Additionally, it will ignore the interrupt signal (Ctrl-C) while running.
Learn more about FIFO: https://brainly.com/question/12948242
#SPJ11
Select the correct answers.
Which are the benefits of leveraging web technologies?
processing of large amounts of data
more manpower
better marketing and customer service
increased production costs
difficulty in handling customer complaints

Answers
Answer:
Explanation:
Select the correct answers.
Which are the benefits of leveraging web technologies?
1) Processing of large amounts of data
2) Better marketing and customer service
Section 1; DESIGN AND DEVELOPMENT PLAN (also called R&D)
A. Development Status and Tasks
B. Difficulties and Risks
C. Product Improvement and New Products
D. Projected Development Costs
E. Proprietary Issues/Intellectual Property (patents, licenses, copyrights, brand names, trade secrets)
Answers
A. Development Status and Tasks: The current development status of project involves these tasks are crucial for the successful completion of the project and will be prioritized and executed according to the established development plan.
B. Difficulties and Risks: While progressing with project, certain difficulties and risks have been identified. Mitigation strategies and contingency plans have been devised to address these difficulties and risks effectively. C. Product Improvement and New Products: As part of the development plan, continuous efforts will be made to improve the existing product based on user feedback and market demands.D. Projected Development Costs: The projected development costs for the project include various factors such as research and development expenses, equipment procurement, staffing, and testing.
A comprehensive budget has been formulated, outlining the estimated costs for each phase of the development process. E. Proprietary Issues /Intellectual Property: Intellectual property protection is a key consideration for the project. The company holds [mention relevant intellectual property assets such as patents, licenses, copyrights, brand names, or trade secrets] that safeguard the uniqueness and competitiveness of our products.
Learn more about design and development plan here:
https://brainly.com/question/33071329
#SPJ11
Create and run a query that displays all employees from the employee table who have the title Senior Sales Associate. This requires that you join related tables and select columns from all them but display only some of the columns. In the dynaset display each qualifying employee's last name, gender, and city, and state where they work (arrancge columns left to right in this way). Sort the dynaset in ascending order by state and then by last name within each state group. Assign aliases to the column as follows: Name, Gender, Work City, and Work State. Optimize the dynaset column widths. Print the resulting dynaset and write your name on the output.
Answers
Sure, I can help you create a query for this. However, to create an accurate SQL query, I need to know the exact table structures. In particular, I need to know:
1. The name of the employee table, and its column names.
2. The name of the related tables, and their column names.
3. The relationship between these tables (foreign keys).
4. Which tables contain the 'title', 'last name', 'gender', 'city', and 'state' data.
For the purpose of this answer, let's assume we have two tables: `employees` and `locations`.
The `employees` table has the following columns: `emp_id`, `first_name`, `last_name`, `gender`, `title`, and `location_id`.
The `locations` table has the following columns: `loc_id`, `city`, and `state`.
Here's an example of how your query might look:
```sql
SELECT
e.last_name AS 'Name',
e.gender AS 'Gender',
l.city AS 'Work City',
l.state AS 'Work State'
FROM
employees e
JOIN
locations l ON e.location_id = l.loc_id
WHERE
e.title = 'Senior Sales Associate'
ORDER BY
l.state ASC,
e.last_name ASC;
```
This query first selects the desired columns from the `employees` and `locations` tables, assigning them the requested aliases. It then joins the two tables on their shared `location_id`/`loc_id` column. The `WHERE` clause filters the results to only include rows where the title is 'Senior Sales Associate'. Finally, the `ORDER BY` clause sorts the results first by state in ascending order, and then by last name in ascending order within each state group.
As for optimizing the column widths, printing the resulting dynaset, and writing your name on the output, these are tasks typically handled by the application or tool you're using to run the SQL query, rather than within the SQL query itself. You'd need to check the documentation or help resources for that tool to see how to do this.
If your table structure is different, please provide the correct structure and I will adjust the query accordingly.
a honeypot is configured to entice attackers and allows administrators to get information about the attack techniques being used.
Answers
Using a honeypot, which is designed to lure attackers, administrators can learn more about the attack strategies being used.
A network honeypot has what purpose?A honeypot is a cybersecurity technology that simulates an attack target to direct hackers away from legitimate targets. They also gather details about the individuals, tactics, and goals of their adversaries.
Which of the following uses for a honeynet do you have in mind?Even though the primary objective of a honeynet is to gather information on the strategies and motivations of attackers, a phony network can be valuable to its operator in other ways, such as by diverting attackers from the real network and its resources.
To know more about honeypot visit:-
https://brainly.com/question/24182844
#SPJ4
Question is incomplete:
What is a honeypot? What is the main function of a honeypot?
When developing a new software package, logically, the software must be designed before the code is written, and the code must be written before it is tested. These activities are dependent on each other by _________ constraints.
Answers
Answer: Technical
Explanation: When making decisions, we may have to follow a certain pattern or order due to restrictions brought about by circumstances rules or conditions. These restrictions or limitations are regarded to as constraints. Technicality may be explained as the knowledge, expertise or initiative required for an operation, production or design. Therfore, we may view technical constraint as limitations or restrictions brought about by the technical guidelines or expertise required for a certain products. From a technical perspective, before a software package can be built, the engineer must know why and what he wants the software to be capable of doing, then he writes the code then tests the code. It is a sequence, a test cannot be performed without a written code and code cannot be written without a planned design.
Antivirus programs protect your computer system from viruses or malicious programs. This is an example of which type of software
Answers
Answer:
Utilities
Explanation:
Which answer below best describes IDS? Intuitive Detector System Incident Detection System
Integral Delay System none of the above
Answers
IDS stands for Intrusion Detection System. It is a security technology used to monitor network traffic and identify unauthorized access or malicious activities within a computer network. IDS works by analyzing network packets and comparing them to known patterns or signatures of malicious behavior.
Here is a step-by-step explanation of how IDS works:
1. Monitoring: IDS constantly monitors network traffic, looking for any abnormal or suspicious activities. It examines packets of data flowing through the network.
2. Signature-based Detection: IDS uses a database of known attack signatures to compare against the network traffic. If it finds a match, it raises an alarm indicating a potential intrusion.
3. Anomaly-based Detection: IDS also looks for deviations from normal behavior within the network. It establishes a baseline of what is considered normal and alerts when there is a significant deviation from that baseline.
4. Notification and Response: When IDS detects a potential intrusion, it generates alerts or notifications to system administrators or security personnel. These alerts provide information about the detected intrusion and allow for timely response and mitigation.
5. Prevention and Mitigation: IDS can also be configured to trigger automatic responses, such as blocking suspicious IP addresses or isolating compromised systems from the network. This helps prevent further damage and minimize the impact of an intrusion.
To know more about IDS visit:
https://brainly.com/question/32015055
#SPJ11
Of the 3 types of loops you learned about, which one is a loop where you specify the number of times it repeats
A) while loop
B) do until loop
C) for loop
Answers
Answer:
C
Explanation:
for loop
An online supermarket wants to update its item rates during the sales season. They want to show the earlier rates too but with a strikethrough effect so that the customer knows that the new rates are cheaper.
The ____ element gives a strikethrough appearance to the text.
Answers
Answer:
the <strike> element should do it
Explanation:
a wiki is a website made up entirely of content posted by users.
Answers
A wiki is a type of website that allows users to collaboratively create and edit its content.
What is wiki?It is true that the content is primarily created and edited by users, not all wikis are made up entirely of user-generated content. In fact, many wikis have moderators or administrators who oversee the content to ensure it meets certain quality standards or guidelines.
Additionally, some wikis have policies in place that dictate who can contribute, how content is created and edited, and how disputes are resolved. Overall, while user contributions are a significant part of wikis, the degree to which they make up the content can vary depending on the specific wiki and its policies.
Learn more about website:https://brainly.com/question/19459381
#SPJ1
hi what is full form of ugst
Answers
Answer:
UGST – Union Territory Goods & Services Tax.
Answer:
Explanation:
Hello friend
Here's your answer
The full form of UTGST is Union Territory Goods and Service Tax
Hope this helps
plz mark as brainiest!!!!!!
he attributes for an iframe are controlled by CSS. One of the iframe controls is "seamless." This means it _____. will blend the iframe to mimic all surrounding images will format the iframe to code all the surrounding text will blend the iframe to look like the surrounding page will blend the iframe to create a border around pages
Answers
Answer:
A. Will blend the iframe to look like the surrounding page
Drag each tile to the correct box.
Match the hardware to the function it performs.
-control unit
-read-only memory
-arithmetic logic unit
-random access memory

Answers
Answer:
Directs the flow of data → Control Unit
Holds data the CPU needs at the moment → Random Access Memory/RAM
Stores startup instructions → Read-Only Memory/RAM
Performs Calculations → Arithmetic Logic Unit/ALU
Explanation:
Answer:
control unit : holds the data CPU needs at the moment
read only memory : stores startup instructions
arithmetic logic unit : performs calculations
random access memory : direct the flow of data
Andrew is researching a new operating system for the computers at his workplace. His boss wants the computers to be able to connect to the cloud and thus have security in case the laptops are stolen. What version of Windows 10 does not have the ability to lock the hard drive so that it is unusable if removed from a laptop
Answers
The Windows 10 Home edition does not have the ability to lock the hard drive and render it unusable if removed from a laptop.
The feature of locking the hard drive to prevent usability if removed from a laptop is known as "Device Encryption" or "BitLocker." This feature is only available in the Pro and Enterprise editions of Windows 10.
Windows 10 Home does not include the BitLocker functionality, which means it does not have the ability to lock the hard drive for security purposes in case of theft or unauthorized access.
If Andrew's boss requires the computers to have the ability to lock the hard drive and render it unusable if removed, they would need to consider using Windows 10 Pro or Enterprise edition rather than the Home edition.
These higher-tier editions provide the necessary security features such as BitLocker encryption to protect data in case of theft or physical removal of the hard drive from the laptop.
Learn more about Windows 10 here:
brainly.com/question/31563198
#SPJ11
What is the drawback of the linear model?
A.
communication is only in one direction
B.
too much noise is created
C.
no feedback is sent on receiving the message
D.
long travel between the sender and the receiver
Answers
Answer:
long travel between the sender and the receiver
Explanation:
The drawback of linear model is long travel between the sender and the receiver. The correct option is D.
What is linear model?Depending on the context, the phrase "linear model" is used differently in statistics.
The word is frequently used interchangeably with a linear regression model since it occurs most frequently in relation to regression models.
The phrase has a different connotation when employed in time series analysis, though.
Something that is linear is related to a line. A line is built using all of the linear equations. A non-linear equation is one that cannot be represented by a straight line. It has a variable slope value and resembles a graphed curve.
The linear model's disadvantage is the distance between the transmitter and the receiver.
Thus, the correct option is D.
For more details regarding linear model, visit:
https://brainly.com/question/29757372
#SPJ2
6. Each sales person earns Bonus points for the sales of each product type based on the following criteria. 1 point for every sh. 50 for Faiba, 2 points for every sh. 60 for Gateway, 3 point for every sh. 50 for Vodafone, 2 point for every sh. 60 for SAF. Insert a column Bonus Points in row 3 and compute the points of each sales person [5]
Answers
The column Bonus Points in row 3 and compute the points of each sales person [5] are
What is bonus?
Bonus is a form of financial compensation given to an employee or contractor in addition to their regular wages or salary. Bonuses may be awarded to employees based on their performance or for meeting certain goals. Bonuses may be in the form of a cash payment, extra paid vacation, or other benefits such as a stock option or gift. Bonuses may also be awarded to employees for long-term service or loyalty. Bonuses are a way of rewarding employees for their hard work and dedication to the company. They can also be used as an incentive to encourage employees to stay with the company, or to motivate them to reach higher levels of performance.
In the third row of the table, the column ‘Bonus Points’ can be added.
For salesperson A, the bonus points earned can be calculated as follows:
For Faiba - A has sold Sh.600, so the bonus points earned are 600/50 = 12.
For Gateway - A has sold Sh.120, so the bonus points earned are 120/60 = 2.
For Vodafone - A has sold Sh.500, so the bonus points earned are 500/50 = 10.
For SAF - A has sold Sh.120, so the bonus points earned are 120/60 = 2.
Therefore, the total bonus points earned by salesperson A is 12 + 2 + 10 + 2 = 26.
Similarly, the bonus points earned by other salespersons can be calculated and the total bonus points earned by each salesperson can be inserted in the ‘Bonus Points’ column.
To learn more about bonus
https://brainly.com/question/29659552
#SPJ1
state the difference between IBM PC and apple machintosh computers
Answers
Answer:
a Mac is a PC because PC stands for personal computer. However, in everyday use, the term PC typically refers to a computer running the Windows operating system, not the operating system made by Apple.
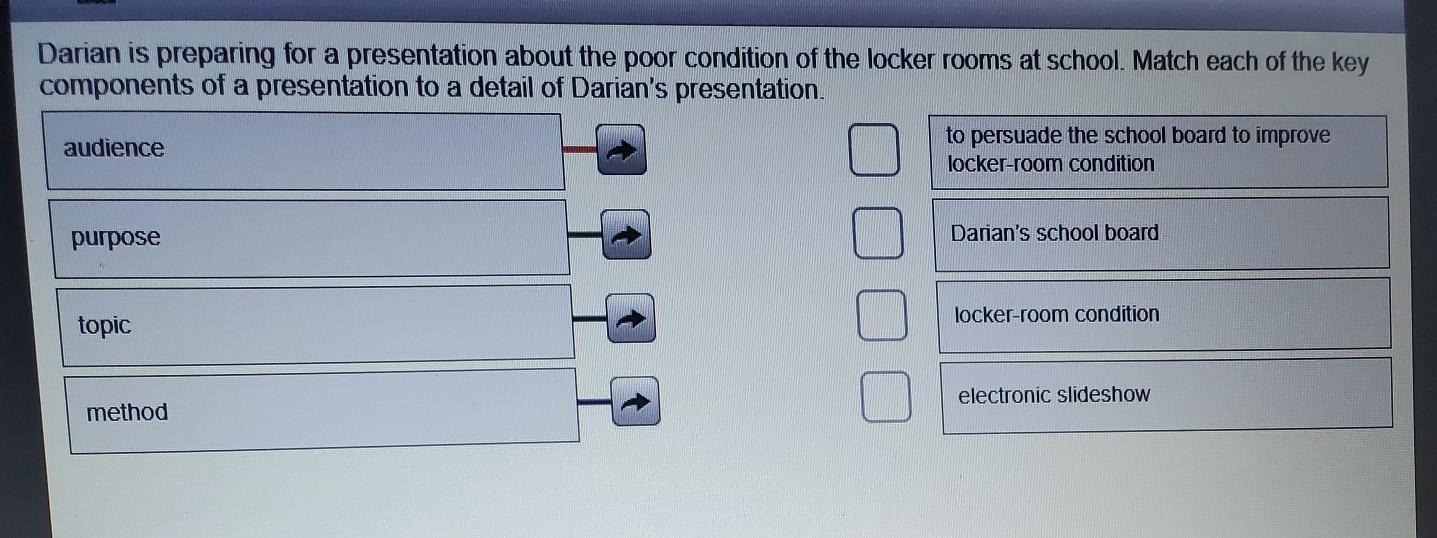
Darian is preparing for a presentation about the poor condition of the locker rooms at school. Match each of the key components of a presentation to a detail of Darian's presentation. audience to persuade the school board to improve locker-room condition purpose Darian's school board locker-room condition topic a electronic slideshow method can anyone
Answers
Answer:
Purpose - To paurswade the board to change the conditions of the locker room
Topic - Locker room condition
Method - Electronic Slideshow
Audience - School Board
A video conferencing application isn't working due to a Domain Name System (DNS) port error. Which record requires modification to fix the issue?
Answers
Answer:
Service record (SRV)
Explanation:
Service records (SRV record) are data records stipulating specifications of the DNS such as the port numbers, servers, hostname, priority and weight, and IP addresses of defined or cataloged services servers.
The SRV record is the source of information and the search site about the
location of particular services as such an application i need of such services will look for a related SRV record
A configured SRV is the source of the ports and personal settings for a new email client, without which the parameters set in the email client will be incorrect.
What is a presentation program? Name any
presentation programs.
Answers
Answer: A presentation program is a software program that helps create a slideshow that addresses a topic. Presentation programs can be used in businesses and schools for discussing a topic or for teaching. Many times, the presenter uses a projector to project the slideshow up on to screen that everyone can see. The most commonly used program is Power Point and Slides.
The contents of a data file are as shown.
dog, 30, 6
dog, 45, 2
cat, 12, 3
22, cat, 15
This data is
O abstract
O incorrect
O structured
O unstructured
Answers
The contents of a data file is Unstructured data.
What are data file?This is known to be a computer file that is said to store data that are often used by a computer application or system. They are made up of input and output data.
Conclusively, The Unstructured data is said to be a collection of different kinds of data that are said to not be stored organized or a well-defined form.
Learn more about data file from
https://brainly.com/question/26125959
which relational algebra command creates a new table where only certain columns are to be included?
Answers
The relational algebra command that creates a new table where only certain columns are to be included is the PROJECT operation.In relational algebra, the PROJECT operation is used to select specific columns from a relation (table) and create a new relation that contains only those selected columns. It projects a subset of attributes from a relation while eliminating duplicates.
The syntax for the PROJECT operation followsPROJECT<column_list>(relation_name)Here, column_list represents the list of columns to be included in the resulting table, and relation_name is the original table from which the columns are selectedBy applying the PROJECT operation, it is possible to create a new table that includes only the desired columns, facilitating data manipulation and analysis by focusing on the relevant attributes.
To learn more about eliminating click on the link below:
brainly.com/question/29560851
#SPJ11
what is the difference between word processing software and presentation software
Answers
Answer:
Word is a word processing program. PowerPoint is presentation software. MS Word is used for preparing documents which have higher quantum of text and tables. ... On the other hand, MS Powerpoint is used in cases where you want to give a presentation.
Word is a program for word processing. Presentation tools include PowerPoint. Documents with a greater amount of text and tables are created using MS Word. However, if you want to give a presentation, MS PowerPoint is what you use.
What word processing software and presentation software?Plain text is typed and edited in word processing, whereas presentation software is used to edit and create visual aids to assist your presentation.
Word processors are specialized pieces of software that are required to do word processing. Many individuals use various word processing tools in addition to Microsoft Word, which is only one example.
Therefore, In contrast to presentation software, which prevents you from doing so, word processing software allows you to create papers and keep your information privately
Learn more about software here:
https://brainly.com/question/12114624
#SPJ2
A good way to repeatedly perform an operation is to write the statements for the task once and then place the statements in a loop that will repeat as many times as necessary. true or false
Answers
The statement 'a good way to repeatedly perform an operation is to write the statements once and then place the statements in a loop that will repeat as many times as necessary' is TRUE. It is part of Phyton programming.
What do Phyton loops mean?
Phyton loops are specific loops used to execute a statement and/or group of statements many times.
The loops in Python programming include for loop, while loop (that allows to execute a block of statements repeatedly), and nested loop.
In Phyton programming, the loop statements are executed for each specific item of a given sequence.
Learn more about Phyton loops here:
https://brainly.com/question/26497128
Does each box at the fruit stand contain a different fruit?
In [164]:
# Set all_different to "Yes" if each box contains a different fruit or to "No" if multiple boxes contain the same
fruit all_different = "No" all_different
Out[164]: 'No' In [165]: _
= ok.grade('q6_3')
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ Running tests
Answers
Answer:
yes
Explanation:
The value of the variable all_different is: all_different = No
Complete questionDoes each box at the fruit stand contain a different fruit? Set all_different to True if each box contains a different fruit or to False if multiple boxes contain the same fruit.
Hint: You don't have to write code to calculate the True/False value for all_different. Just look at the inventory table and assign all_different to either True or False according to what you can see from the table in answering the question.
box ID fruit name count
53686 kiwi 45
57181 strawberry 123
25274 apple 20
48800 orange 35
26187 strawberry 255
57930 grape 517
52357 strawberry 102
43566 peach 40
all_different = ...
How to determine the true statement?From the hint given, we can see that writing a code is not necessary.
All we need to do is to scan through the table.
From the given table, we can see that there are several fruits on the table.
These include peach, kiwi, grape, strawberry, etc.
Since the fruits are different, then the value of the variable all_different is:
all_different = No
Read more about boolean variables at:
https://brainly.com/question/18089222
#SPJ2