B3 is an example of what in spreadsheet?
Answers
Answer:
B3 would be the third row and second column.
Explanation:
pls mark me the brainliest...thank uu
Related Questions
Describe what test presentation and conclusion are necessary for specific tests in IT testing such as
-resource availability
-environment legislation and regulations (e.g. disposal of materials)
- work sign off and reporting
Answers
For specific tests in IT testing, the following elements are necessary.
What are the elements?1. Test Presentation - This involves presenting the resources required for the test, ensuring their availability and readiness.
2. Conclusion - After conducting the test, a conclusion is drawn based on the results obtained and whether the objectives of the test were met.
3. Resource Availability - This test focuses on assessing the availability and adequacy of resources required for the IT system or project.
4. Environment Legislation and Regulations - This test evaluates compliance with legal and regulatory requirements related to environmental concerns, such as proper disposal of materials.
5. Work Sign Off and Reporting - This includes obtaining formal approval or sign off on the completed work and preparing reports documenting the test outcomes and findings.
Learn more about IT testing at:
https://brainly.com/question/13262403
#SPJ1
Blocks that allows you to repeat scripts multiple times are
Answers
Answer:
here are several methods to make a script perform an action for a set amount of ... Technically, this may not work if you have wait blocks or other blocks that take up time. ... This script uses the timer and the Repeat Until block.
Explanation:
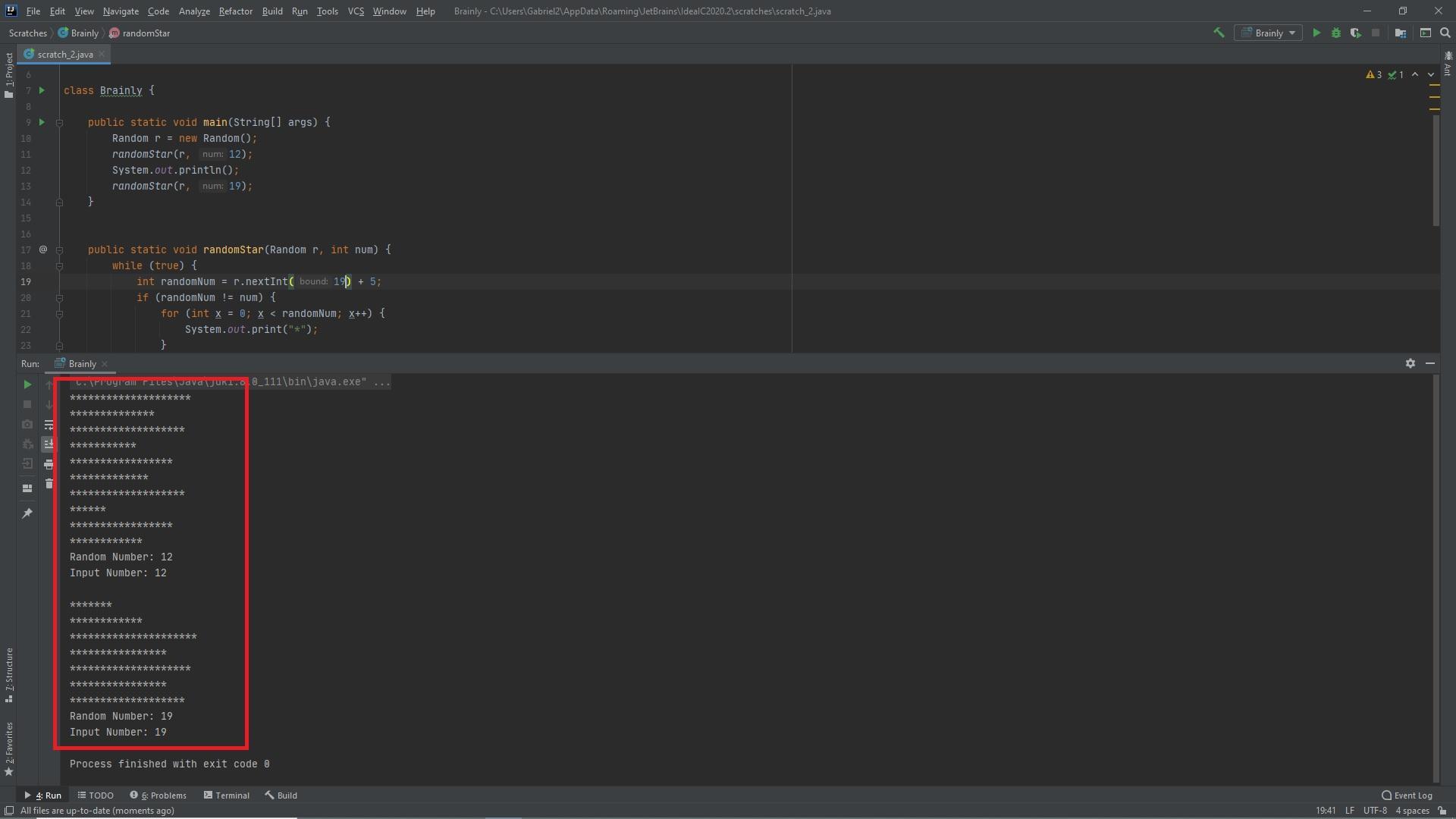
Random Star
Write a method named randomStar that takes two parameters, a Random object r and an integer num. The method should keep printing lines of * characters, where each line has between 5 and 19 * characters inclusive, until it prints a line with greater than or equal to num characters. num is guaranteed to be between 5 and 19. For example, the method call randomStar(14) will print:
import java.util.*;
public class RandomStar {
public static void main(String[] args) {
Random r = new Random(2063064142); // ignore the 2063064142
randomStar(r, 12);
System.out.println();
randomStar(r, 19);
}
public static void randomStar(Random r, int num) {
}
}
Answers
Answer:
Explanation:
The following code is written in Java. The function takes in the random object and creates a random number where it generates a random number and prints out the * characters, if the random number and the input num are the same it prints out both values and ends the function.
import java.util.Random;
class Brainly {
public static void main(String[] args) {
Random r = new Random();
randomStar(r, 12);
System.out.println();
randomStar(r, 19);
}
public static void randomStar(Random r, int num) {
while (true) {
int randomNum = r.nextInt(19) + 5;
if (randomNum != num) {
for (int x = 0; x < randomNum; x++) {
System.out.print("*");
}
System.out.print("\n");
} else {
for (int x = 0; x < randomNum; x++) {
System.out.print("*");
}
System.out.print("\n");
System.out.println("Random Number: " + randomNum);
System.out.println("Input Number: " + num);
break;
}
}
}
}
Rizwan, a data analyst, is generating a report by pulling data from multiple databases and analyzing it. The data processing application is resource-intensive, so Rizwan wants to ensure that other applications do not consume resources that this application needs.How can Rizwan boost the performance of the data processing application?
Answers
Reduce the actual memory while increasing the virtual memory Rizwan boost the performance of the data processing application.
What is a data analyst?
To find the solution to a problem or provide an answer to a question, a data analyst gathers, purifies, and analyses data sets. They work in a variety of fields, including as government, business, finance, law enforcement, and science.
What types of clients ought a company to focus on in its upcoming advertising campaign? Which age range is most susceptible to a specific disease? What behavioural trends are associated with financial fraud?
As a data analyst, you might have to respond to inquiries like these. Learn more about what a data analyst does, what skills you'll need, and how to get started on your path to becoming one by reading on.
Read more about data analyst:
https://brainly.com/question/28375055
#SPJ4
What are vSphere Clusters and how are they utilized in vSphere?
Answers
A group of ESXi hosts set up as a vSphere cluster to share resources like processor, memory, network, and storage In vSphere environments, each cluster can hold up to 32 ESXi hosts, each of which can run up to 1024 virtual machines.
What is vSphere Clusters?The Clusters page in the vSphere Infrastructure view lets you see how many more virtual machines (VMs) can be added to each cluster, how many resources are totaled up in each cluster, and how many resources are currently available in each cluster. It also lets you manage the resources of each host that is part of the cluster.
According to the spare cluster capacity, the page shows information about the number of additional VMs that can be added to each cluster, as well as information about the powered-on and running VMs, their CPU and memory utilization, and other information. By changing the settings for the spare VM basis on this page, you can change how the spare VM basis for an average VM is calculated.
The information on this page helps to address important subsystem-related questions like the following by giving a comprehensive picture of cluster memory usage and contention using Memory metrics:
Is my environment's vSphere memory management functioning properly?In my environment, is the vSphere page sharing mechanism being used effectively? What amount of memory is shared?How much memory can you overcommit?Learn more about vSphere
https://brainly.com/question/28787607
#SPJ1
True or false question :)
Handware can be tracked back to ancient times. Over six centuries ago.
°true
°false
Answers
Answer:
false and it's a recent technology
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
who here has a crush on jk from bts but feels more mature than him
Answers
Answer:
Nope not K-pop fan
Explanation:
I Previous
C Reset
2/40 (ID: 34700)
E AA
Examine the following code:
Mark For Review
def area (width, height)
area = width * height
return area
boxlarea = area (5,2)
box2area = area (6)
What needs to change in order for the height in the area function to be 12 if a height is not specified when calling the function?
0 0 0 0
Add a height variable setting height =12 inside the function
Change the box2area line to box 2area = area (6,12)
Add a height variable setting height =12 before the function is declared
Change the def to def area (width, height = 12)
Answers
Answer:
D. Change the def to def area (width, height = 12)
Explanation:
Required
Update the function to set height to 12 when height is not passed
To do this, we simply update the def function to:
def area (width, height = 12)
So:
In boxlarea = area (5,2), the area will be calculated as:
\(area = 5 * 2 = 10\)
In box2area = area (6), where height is not passed, the area will be calculated as:
\(area = 6 * 12 = 72\)
Write code in MinutesToHours that assigns totalHours with totalMins divided by 60
Given the following code:
Function MinutesToHours(float totalMins) returns float totalHours
totalHours = MinutesToHours(totalMins / 60)
// Calculate totalHours:
totalHours = 0
Function Main() returns nothing
float userMins
float totalHours
userMins = Get next input
totalHours = MinutesToHours(userMins)
Put userMins to output
Put " minutes are " to output
Put totalHours to output
Put " hours." to output
Answers
Answer:
Function MinutesToHours(float totalMins) returns float totalHours
// Calculate totalHours:
totalHours = totalMins / 60
return totalHours
End Function
9. How can you sum up the rows and
Column number quickly in the excel
Sheet?
Answers
Answer:
you can just search it on bing
Explanation:
You can sum up entire columns or rows in Microsoft Excel using the AutoSum feature.
The AutoSum tool automatically selects a column or row of numbers, but you can select any set of numbers by clicking and dragging with the mouse.
You can also manually sum a series of numbers in Excel by typing in a simple SUM formula.
You can view the details of your calculation by clicking the sum cell and looking at the formula bar at the top of the screen.
Answer:
highlight the entire row then go to the taskbar at top, click auto sum or highlight everything and press (alt +=)
Explanation:i am an accountant
In java Please
3.28 LAB: Name format
Many documents use a specific format for a person's name. Write a program whose input is:
firstName middleName lastName
and whose output is:
lastName, firstInitial.middleInitial.
Ex: If the input is:
Pat Silly Doe
the output is:
Doe, P.S.
If the input has the form:
firstName lastName
the output is:
lastName, firstInitial.
Ex: If the input is:
Julia Clark
the output is:
Clark, J.
Answers
Answer:
Explanation:
import java.util.Scanner;
public class NameFormat {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("Enter a name: ");
String firstName = input.next();
String middleName = input.next();
String lastName = input.next();
if (middleName.equals("")) {
System.out.println(lastName + ", " + firstName.charAt(0) + ".");
} else {
System.out.println(lastName + ", " + firstName.charAt(0) + "." + middleName.charAt(0) + ".");
}
}
}
In this program, we use Scanner to read the input name consisting of the first name, middle name, and last name. Based on the presence or absence of the middle name, we format the output accordingly using if-else statements and string concatenation.
Make sure to save the program with the filename "NameFormat.java" and compile and run it using a Java compiler or IDE.
John wants to view Sarah’s assignment files on his computer. But he cannot open them because of version problems. Which upgrade should he perform to solve the problem?
Answers
Since John wants to view Sarah’s assignment files on his computer. The upgrade that John need to perform to solve the problem is option E. Software upgrade
What is the Software upgrade about?It is likely that John will need to perform a software upgrade to be able to view Sarah's assignment files.
This is because a software upgrade involves installing a newer version of the software that is capable of opening the files. A RAM upgrade, motherboard upgrade, and optical drive upgrade would not likely resolve the issue with John being unable to open the files.
Learn More about upgrade from
https://brainly.com/question/3638683
#SPJ1
See full question below
John wants to view Sarah's assignment files on his computer. But he cannot open them because of version problems. Which upgrade should he perform to solve the problem.
A. Software update
B. RAM upgrade
C. Motherboard upgrade
D. Optical drive upgrade
E. Software upgrade
A data___is usually a smaller version of a data warehouse used by a single department
Answers
Answer:
mart
Explanation:
These were created in order to provide an easier access to a certain subject or department. It is important because it allows one to refrain from wasting time searching for something in a data warehouse and it provides organization.
Packet-switching was advanced by which of the following people?
Sergey Brin
Leonard Kleinrock
Tim Berners Lee
Bill Gates
DONE
Answers
Answer:
Leonard Kleinrock
Explanation:
numStudents is read from input as the size of the vector. Then, numStudents elements are read from input into the vector idLogs. Use a loop to access each element in the vector and if the element is equal to 4, output the element followed by a newline.
Ex: If the input is 6 68 4 4 4 183 104, then the output is:
4
4
4
Answers
Here's an example solution that uses a loop to access each element in the vector idLogs and outputs the elements equal to 4
How to write the output#include <iostream>
#include <vector>
int main() {
int numStudents;
std::cin >> numStudents;
std::vector<int> idLogs(numStudents);
for (int i = 0; i < numStudents; i++) {
std::cin >> idLogs[i];
}
for (int i = 0; i < numStudents; i++) {
if (idLogs[i] == 4) {
std::cout << idLogs[i] << std::endl;
}
}
return 0;
}
Read more on Computer code here https://brainly.com/question/30130277
#SPJ1
Which type of photographer documents plants and weather in their natural habitat?
a
Portrait
b
Nature
c
Product
d
Scientific
Answers
What help in executing commands quickly
Answers
Answer:99
Explanation: Last summer, my family and I took a trip to Jamaica. My favorite part of the trip was when we went to a place called the Luminous Lagoon. We ate dinner and waited for the sun to go down. Then we boarded a boat and went out into the lagoon. That’s when the magic started.
At first we could not see very much in the darkness except for the stars in the sky. After a few minutes, however, I noticed some fish swimming in the water. They didn’t look like ordinary fish. These fish were glowing! Our guide explained that the glow came from tiny creatures in the water called dinoflagellates. These little animals are not visible to us, but their bodies produce light using something called bioluminescence, just like fireflies. There are so many of these creatures in Luminous Lagoon that the water around them seems to glow.
After our guide explained these facts to us, he told us to put our hands in the water. I was not sure if it would work, but I tried it. When I did, my hand looked like it belonged to a superhero! It was glowing bright blue. I hope someday I get to return to the Luminous Lagoon. The lights in the water were much more entertaining than the ones in the sky.
Problem:
audio
The Greek prefix dinos- means “whirling” and the Latin root word flagellum means “whip”. What does dinoflagellate most likely mean as it is used in the passage?
audio
the production of light from an organism’s body
audio
the study of creatures that live in the ocean
audio
to move around underwater water like a fish
audio
an organism with a whip-like part it uses to move around in the water
visit three websites to learn more about agile system development. prepare a list of the sites you visited and a summary of the results.
Answers
The three websites to learn more about agile system development are Agile Alliance (https://www.agilealliance.org/),
Scrum Alliance (https://www.scrumalliance.org/) and Agile Manifesto (http://agilemanifesto.org/).
1. Agile Alliance (https://www.agilealliance.org/)
This website offers a comprehensive overview of agile system development, including the principles and values of agile, as well as resources for implementing agile in a team or organization. It also features a community section where users can discuss and ask questions about agile.
2. Scrum Alliance (https://www.scrumalliance.org/)
This website focuses on the Scrum framework, one of the most popular agile methodologies. It offers resources and training for becoming a Scrum Master, Product Owner, or Developer, as well as articles and case studies about implementing Scrum in a variety of industries.
3. Agile Manifesto (http://agilemanifesto.org/)
This website is the home of the Agile Manifesto, a document that outlines the values and principles of agile system development. It also includes a list of the original signatories of the manifesto, as well as a section for individuals to sign and show their support for the agile approach.
Learn more about agile system development here: https://brainly.com/question/30881801
#SPJ11
fine the average of 5,2,3
Answers
Answer:
3 1/3
Explanation:
I need help solving this. Understanding Arithmetic and Assignment Summary In this lab, you complete a partially written Python program that is provided along with the data files for this book. The program, which was written for a furniture company, prints the name of the furniture item, its retail price, its wholesale price, the profit made on the piece of furniture, a sale price, and the profit made when the sale price is used. Instructions The file named Furniture.py should be displayed. The file includes output statements. Read them carefully before you proceed to the next step. Design the logic that will use assignment statements to: Calculate the profit (profit) as the retail price minus the wholesale price Calculate the sale price (salePrice) as 25 percent deducted from the retail price Calculate the profit when the sale price is used (saleProfit) as the sale price minus the wholesale price Execute the program. Your output should be as follows: Item Name: TV Stand Retail Price: $325.0 Wholesale Price: $200.0 Profit: $125.0 Sale Price: $243.75 Sale Profit: $43.75
Answers
It seems that you need help completing a partially written Python program that calculates and prints the profit, sale price, and sale profit of a furniture item.
What are the steps needed for completing a partially written Python program?
Open the "Furniture.py" file and read the output statements provided in the file. Declare variables to hold the necessary information about the furniture item. You will need to declare variables for the item name, retail price, and wholesale price. For example:itemName = "TV Stand"
retailPrice = 325.0
wholesalePrice = 200.0
Calculate the profit made on the furniture item using the formula profit = retailPrice - wholesalePrice. Assign the result to a variable called profit. For example:profit = retailPrice - wholesalePrice
Calculate the sale price of the furniture item by deducting 25 percent from the retail price. Use the formula salePrice = retailPrice - (0.25 * retailPrice). Assign the result to a variable called salePrice. For Example:salePrice = retailPrice - (0.25 * retailPrice)
Calculate the profit made on the furniture item when it is sold at the sale price. Use the formula saleProfit = salePrice - wholesalePrice. Assign the result to a variable called saleProfit. For example:saleProfit = salePrice - wholesalePrice
Print the information about the furniture item, including the item name, retail price, wholesale price, profit, sale price, and sale profit. Use the output statements provided in the file and format the output to include the values of the variables. For example:print("Item Name:", itemName)
print("Retail Price: ${:.2f}".format(retailPrice))
print("Wholesale Price: ${:.2f}".format(wholesalePrice))
print("Profit: ${:.2f}".format(profit))
print("Sale Price: ${:.2f}".format(salePrice))
print("Sale Profit: ${:.2f}".format(saleProfit))
Save the changes to the file and run the program. The output should be as follows:Item Name: TV Stand
Retail Price: $325.00
Wholesale Price: $200.00
Profit: $125.00
Sale Price: $243.75
Sale Profit: $43.75
To learn more about Python program, visit: https://brainly.com/question/26497128
#SPJ1
Which of the following terms describes an attacker walking or driving through business areas and neighborhoods to identify unprotected wireless networks from the street using a laptop or a handheld computer?
A. Wi-Fi stealing.
B. Wi-Fi trolling.
C. Wi-Fi jacking.
D. Wi-Fi hacking.
Answers
Answer:
C. Wi-Fi jacking
Explanation:
Answer: yessir b
Explanation:
Transactions done through desktop or mobile personal computers are known as a
Answers
E-commerce can be done on a desktop computer, laptop, smartphone, or tablet. However, e-commerce is usually associated with computers that require users to find a location with an internet connection. Conversely, mcommerce refers specifically to transactions made via smartphones and mobile devices.
What are ecommerce transaction types?
types of e-commerce
Business-to-business (B2B)
Business to Consumer (B2C)
Consumer to Consumer (C2C)
From Consumer to Business (C2B)
Business to Administration (B2A)
From consumer to government (C2A)
What is debit card e-commerce?
E-commerce transactions make it easy and profitable for debit cardholders to purchase goods/services online via the Internet that accepts Visa/RuPay as a payment method. Our debit cardholders can buy flight/train/bus tickets, movie tickets and pay mobile and utility bills online.
To know more about E-commerce visit;
https://brainly.com/question/29732698
#SPJ4
8) Prime numbers. Write a program that prompts the user for an integer and then prints out
all prime numbers up to that integer. For example, when the user enters 20, the program
should print
2
2357
3
5
7
11
13
17
19
Recall that a number is a prime number if it is not divisible by any number except 1 and
itself.
Notes: Use do-while loop.
Answers
Here's a Python program that prompts the user for an integer and then prints out all prime numbers up to that integer:
python
# Prompt the user for an integer
n = int(input("Enter an integer: "))
# Initialize variables
i = 2
is_prime = True
# Loop through numbers from 2 to n
while i <= n:
# Check if i is prime
j = 2
while j < i:
if i % j == 0:
is_prime = False
break
j += 1
# Print i if it is prime
if is_prime:
print(i)
# Increment i and reset is_prime
i += 1
is_prime = True
What are the Prime numbers?Below is how the program works:
The program prompts the user to enter an integer using the input() function and converts the input to an integer using the int() function.
The program initializes a variable i to 2, which is the first prime number.
The program uses a while loop to loop through all the numbers from 2 to n.
For each number i, the program uses a nested while loop to check if it is prime. The nested while loop checks if i is divisible by any number from 2 to i-1. If it is divisible by any of these numbers, is_prime is set to False, and the nested while loop breaks.
If is_prime is still True after the nested while loop, i is a prime number and the program prints it using the print() function.
The program increments i and resets is_prime to True before looping back to step 4.
Once all the numbers from 2 to n have been checked, the program terminates.
Read more about Prime numbers here:
https://brainly.com/question/145452
#SPJ1
explain 3 advantages and 3 disadvantages of computers
Answers
Answer:
advantage
1: finish tedious tasks faster (writing an essay)
2: the internet (you can learn anything)
3: reduces the use of paper
disadvantage
1: social media (being addictive toxic)
2: decreasing jobs
3: less time for people to interact in person
Explanation:
advantages:
1. computers make information more accessible
2. they help pass time
3. they store documents and data
disadvantages:
1. information can get leaked
2. costly
3. uses up electricity
Why a commerce student must learn about SDLC (Software Development Life Cycle) and its phases?
How SDLC could help a commerce graduate in career growth and success?
Answers
Answer:
The description of the given question is described throughout the explanation segment below.
Explanation:
A method that delivers the best reliability as well as cheapest possible applications throughout the specified timeframe, is termed SDLC. A business student could perhaps read about such a life cycle and its stages when individuals not only relate to scientific issues and mean effective pressure.
Whenever a successful entrepreneur does an inventory of an enterprise, people are useful. SDLC demonstrates the capacity for decision-making or judgments.Brainly account. How to open?
Answers
what is the differences between INTEL and AMD processors
Answers
Is it possible to beat the final level of Halo Reach?
Answers
How does CSS relate to HTML
Answers
Answer:
CSS stands for Cascading Style Sheets with an emphasis placed on “Style.” While HTML is used to structure a web document (defining things like headlines and paragraphs, and allowing you to embed images, video, and other media), CSS comes through and specifies your document's style—page layouts, colors, and fonts are
Explanation: