Assignment 3 chatbot edhesive
Answers
Answer:
name1=input("What is your first name? ")
name2=input("What is your last name? ")
print("Hi there, "+ name1+" "+name2 +" ,nice to meet you!")
print("How old are you?")
age = int(input(" "))
print(str(age) + " is a good age.")
if(age >= 16):
print("You are old enough to drive. \n")
else:
print("Still taking the bus, I see. \n")
print("So, " + name1 + ", how are you today?")
feel=input("")
print("You are " + feel),
if(feel== "Happy"):
print("That is good to hear.")
elif(feel == "Sad"):
print("I'm sorry to hear that. ")
else:
print("Oh my!")
print("Tell me more. \n")
next=input("")
import random
r = random.randint(1, 3)
if(r==1):
print("Sounds interesting. \n")
elif(r==2):
print("That's good to hear. \n")
else:
print("How unusual. \n")
print("Well, " + name1 + ", it has been nice chatting with you.")
Explanation:
Related Questions
Statistics on Cybersecurity Issues??
Answers
According to the statistics on the Cybersecurity issue, it is found that the cost of cybercrime has risen by 10% in the past year.
What is Cybersecurity?Cybersecurity may be characterized as the significant and consistent practice or method of protecting critical systems and sensitive information from digital attacks. It is generally categorized into five distinct types.
According to the context of this question, the average cost of a data breach that generally holds the reason or concern of cybercrime in the United States in 2022 was $9.44 million, according to IBM data. Cybersecurity Ventures predicts cybercrime will cost $10,5 trillion annually by 2025.
Therefore, according to the statistics on the Cybersecurity issue, it is found that the cost of cybercrime has risen by 10% in the past year.
To learn more about Cybersecurity, refer to the link:
https://brainly.com/question/28004913
#SPJ9
hi, please help me, solution.
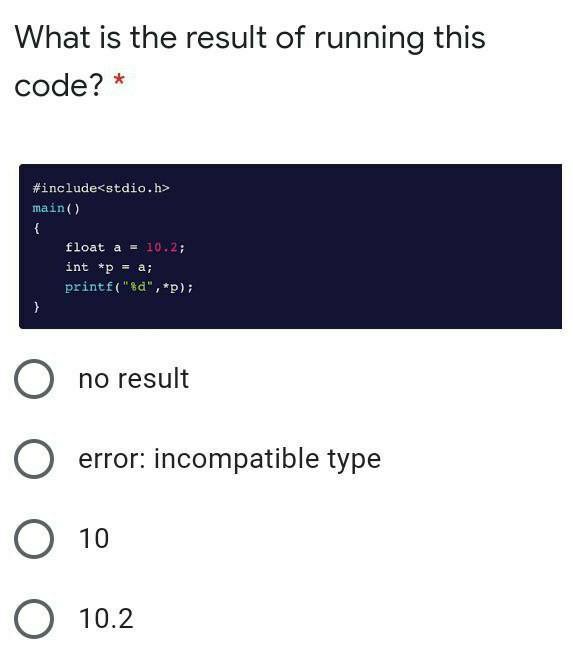
Answers
Answer:
error: incompatible types
Explanation:
Given
The attached code
Required
The output
Variable "a" is declared as float
While p is declared as a pointer to an integer variable
An error of incompatible types will be returned on line 3, int *p = a;
Because the variables are not the same.
To assign a to p*, we have to use type casting.
Hence, (b) is correct
Explain how loops can be utilized in list processing. Please provide Python examples in your response.
Answers
Answer:
data = [0,1,2,3,4]
for i in range(4):
print(data[i])
i+=1
Explanation:
Loops can be utilized in a listing process by looping back to a list with a variable while the loop increases that variable to give a different response from the list.
Assistive technology has gained currency in the 21st century since it facilitates the inclusion agenda in the country.Give four reasons to justify your point.
Answers
Answer:
Assistive technology has gained currency in the 21st century because it provides various benefits that support inclusion. These include:
Increased accessibility: Assistive technology can make it easier for individuals with disabilities to access and interact with technology and digital content. This can increase their independence and enable them to participate more fully in society.Improved communication: Assistive technology can facilitate communication for individuals with speech or hearing impairments, enabling them to express themselves and connect with others.Enhanced learning opportunities: Assistive technology can provide students with disabilities with access to educational materials and resources, enabling them to learn and succeed in school.Greater employment opportunities: Assistive technology can provide individuals with disabilities with the tools they need to perform job tasks and participate in the workforce, increasing their opportunities for employment and economic independence.Explanation:
Assistive technology refers to tools, devices, and software that are designed to support individuals with disabilities. In recent years, assistive technology has become increasingly important in promoting inclusion and accessibility for people with disabilities. The four reasons mentioned above provide a brief overview of the key benefits that assistive technology can offer, including increased accessibility, improved communication, enhanced learning opportunities, and greater employment opportunities. These benefits can help individuals with disabilities to participate more fully in society, achieve greater independence, and improve their quality of life.
We would like the set of points given in the following figure into 1D space. The set of points has been
generated using this instruction [X, y = make_moons(n_samples = 100)], where X are the 2D features
and y are the labels(blue or red).
How to do that while keeping separable data point with linear classification? Give the
mathematics and the full algorithm.
How to apply the SVM algorithm on this data without dimension reduction? Give the
mathematics and full algorithm.
Answers
One way to project the 2D data points onto a 1D space while preserving linear separability is through the use of a linear discriminant analysis (LDA) technique. LDA finds the linear combination of the original features that maximizes the separation between the different classes.
What is the mathematics in SVM algorithm?The mathematics behind LDA involve finding the eigenvectors of the within-class scatter matrix and the between-class scatter matrix and selecting the eigenvector that corresponds to the largest eigenvalue. The full algorithm for LDA can be outlined as follows:
Compute the mean vectors for each class
Compute the within-class scatter matrix (SW) and the between-class scatter matrix (SB)Compute the eigenvectors and eigenvalues of the matrix (SW⁻¹SB)Select the eigenvector that corresponds to the largest eigenvalue as the linear discriminantProject the original data onto the new 1D space using the linear discriminantRegarding the SVM algorithm, it can be applied directly to the original 2D data without the need for dimension reduction. The mathematics behind SVM involve finding the hyperplane that maximizes the margin, or the distance between the closest data points of each class, while also ensuring that the data points are correctly classified.
The full algorithm for SVM can be outlined as follows:
Select a kernel function (e.g. linear, polynomial, radial basis function)Train the model by solving the optimization problem that maximizes the marginUse the trained model to classify new data points by finding the hyperplane that separates the different classesIt is important to note that, in case of non-linearly separable data, SVM algorithm uses the kernel trick to map the original data into a higher dimensional space, where the data is linearly separable.Learn more about algorithm from
https://brainly.com/question/24953880
#SPJ1
What is output by the following line of code?
print(mystery("hello"))
Group of answer choices
Answers
Answer:int x = 5;
if(x < 5)
cout << "line 1 ";
cout << "line 2";
A. line 1 line 2 B. line 1 C. line 2
D. line 1 E. line 1line 2
line 2
2. What would be output by the following code? _______
int x = 0;
while(x < 5)
{
cout << x << " ";
x++;
}
A. 0 1 2 3 4 5 B. 1 2 3 4 5 C. 0 1 2 3 4
D. 0 E. 0 0 0 0 0
3. After execution of the following code, what will be the value of input_value if the value 3 is entered at the keyboard at run time? ________
cin >> input_value;
if (input_value > 5)
input_value = input_value + 5;
else if (input_value > 2)
input_value = input_value + 10;
else
input_value = input_value + 15;
a. A. 8
b. B. 13
c. C. 18
d. D. 0
e. E. 5
4. What would the user see displayed on the screen after the following lines of code are executed?¬¬________
int i = 6;
if (i == 10)
cout << “value: “ << i;
else
cout << "hmmm";
A. value: i B. value: 10
C. hmmm D. value: ihmmm
E. value: 10
Hmmm
5. What is the output of the following lines of code? ______
for(int i=0; i<4; i++)
cout << (i * 3) << " ";
A. 0 1 2 3 4 B. 0 3 6 9
C. 0 3 6 9 12 D. 0 1 2 3 E. 0 0 0 0
Explanation:
You are working with a client who wants customers to be able to tap an image and see pricing and availability. As you are building the code in Java, what will you be using?
graphical user interface
icon public use
graphical public use
icon user interface
Answers
Answer:
A. Graphical user interface
Explanation:
In Java the graphical user interface is what manages interaction with images.
Answer: A.)
Explanation:
The answer is A because
I was born to rule the world
And I almost achieved that goal
(Giovanni!)
But my Pokémon, the mighty Mewtwo,
Had more power than I could control
(Giovanni!)
Still he inspired this mechanical marvel,
Which learns and returns each attack
(Giovanni!)
My MechaMew2, the ultimate weapon,
Will tell them Giovanni is back!
There'll be world domination,
Complete obliteration
Of all who now defy me.
Let the universe prepare,
Good Pokémon beware,
You fools shall not deny me!
Now go, go, go, go!
It will all be mine,
Power so divine
I'll tell the sun to shine
On only me!
It will all be mine,
Till the end of time
When this perfect crime
Makes history
Team Rocket! This is our destiny!
Listen up, you scheming fools,
No excuses, and no more lies.
(Giovanni!)
You've heard my most ingenious plan,
I demand the ultimate prize
(Giovanni!)
Now bring me the yellow Pokémon
And bear witness as I speak
(Giovanni!)
I shall possess the awesome power
In Pikachu's rosy cheeks!
There'll be world domination,
Complete obliteration
Of all who now defy me.
Let the universe prepare,
Good Pokémon beware,
You fools shall not deny me!
Now go, go, go, go!
It will all be mine,
Power so divine
I'll tell the sun to shine
On only me!
It will all be mine,
Till the end of time
When this perfect crime
Makes history
Team Rocket! This is our destiny!
To protect the world from devastation
To unite all peoples within our nation
To denounce the evils of truth and love
To extend our reach to the stars above
Jessie!
James!
There'll be total devastation,
Pure annihilation
Or absolute surrender.
I'll have limitless power,
This is our finest hour
Now go, go, go, go!
Which part of the Result block should you evaluate to determine the needs met rating for that result
Answers
To know the "Needs Met" rating for a specific result in the Result block, you should evaluate the metadata section of that result.
What is the Result blockThe assessment of the metadata section is necessary to determine the rating of "Needs Met" for a particular outcome listed in the Result block.
The metadata includes a field called needs_met, which evaluates the level of satisfaction with the result in terms of meeting the user's requirements. The needs_met category usually has a score between zero and ten, with ten implying that the outcome entirely fulfills the user's demands.
Learn more about Result block from
https://brainly.com/question/14510310
#SPJ1
Discuss in details the difference among programmed I/O, Interrupt Driven I/O
and Direct Memory access over the processor
Answers
Answer:
Programmed I/O, Interrupt Driven I/O, and Direct Memory Access (DMA) are three methods of transferring data between input/output (I/O) devices and the central processing unit (CPU) of a computer system.
Programmed I/O:
In programmed I/O, the CPU executes instructions to transfer data between the I/O device and memory. The CPU continuously polls the I/O device to check if it is ready to send or receive data. This method is simple and easy to implement, but it is also inefficient since the CPU has to wait for the I/O device to be ready before it can perform any other task.
Interrupt Driven I/O:
In interrupt-driven I/O, the CPU sends a command to the I/O device to start the data transfer, and then continues to perform other tasks. When the I/O device has completed the data transfer, it interrupts the CPU to signal that the data is ready. The CPU then stops its current task and processes the interrupt by executing an interrupt service routine (ISR) to transfer the data between the I/O device and memory. This method is more efficient than programmed I/O since the CPU can perform other tasks while waiting for the I/O device to complete the data transfer.
Direct Memory Access (DMA):
In Direct Memory Access (DMA), the I/O device can access the system memory directly without the intervention of the CPU. The I/O device sends a request to the DMA controller to initiate the data transfer, and the DMA controller transfers the data between the I/O device and memory without any involvement of the CPU. The CPU can continue to perform other tasks while the DMA controller performs the data transfer. This method is the most efficient of the three since it frees up the CPU to perform other tasks while the data transfer is being performed.
In summary, the main differences among programmed I/O, interrupt-driven I/O, and DMA are:
Programmed I/O is the simplest method of data transfer, but it is also the least efficient since the CPU has to continuously poll the I/O device to transfer data.
Interrupt-driven I/O is more efficient than programmed I/O since the CPU can perform other tasks while waiting for the I/O device to complete the data transfer.
DMA is the most efficient method of data transfer since it frees up the CPU to perform other tasks while the DMA controller performs the data transfer directly between the I/O device and memory.
Why are cyber security professionals also expected to have some degree of relational skills
Answers
Answer:
Answered below
Explanation:
Relational skills are necessary for cybersecurity professionals in order to enable them interact and relate to other professionals in the fields. Cyber threats are always evolving and changing, therefore cybersecurity professionals need to communicate more with each other and share ideas and notifications about changes in the field.
Relational skills also help a professional understand their clients and what they want and therefore ensures client satisfaction and safety.
2. The population of New York City in 2010 was 8,175,133 people. Assuming that the population doubled every 40 years, create a Java program to calculate in which year the population of NYC was about 10,000 people. (Use printf to format output.)
Answers
```
public class PopulationCalculator {
public static void main(String[] args) {
int population = 8175133; // Population of NYC in 2010
int year = 2010;
while (population >= 10000) {
population /= 2; // Divide population by 2 every 40 years
year += 40; // Add 40 years to the current year
}
System.out.printf("The population of NYC was about 10,000 people in the year %d.", year);
}
}
```
In this program, we start with the population of NYC in 2010 and the current year (2010). Then we use a `while` loop to divide the population by 2 every 40 years and add 40 years to the current year until the population is less than 10,000 people.
Once the loop ends, we use `printf` to output the year when the population was about 10,000 people. The `%d` format specifier is used to insert the year value into the output string.
Note: This program assumes that the population doubles exactly every 40 years, which may not be entirely accurate.
You have just installed a new USB card reader into Wenders computer every time you perform a certain action using the card reader, you get your message that you’ve never seen before. What should you do first?
a.Replace the card read with a new one
b.Install the device on another computer
c.Uninstall the device, then reinstall it
d.Check the manufacturers website for more information about the error
Answers
Answer:
Check the manufacturers website for more information about the error
Why would you not restore a Domain Controller that was last backed up twelve months ago
Answers
Answer:
All the data and information that was updated or added since then will be lost so it is useless to restore a Domain Controller that was backedup twelve months ago.
Explanation:
A domain conttoller back-up must be prepared on regular basis else if DC breaks, restoration of most recent database will be impossible.
What strategy would best help someone manage their feelings of frustration after being cut from a team?
A
Criticizing the other team members, but only when you aren't in front of them
B
Talking to a trusted friend about their feelings
с
Confronting the coach for not giving them a chance
D
Both B and C
Answers
Explanation:
B.talking to a trusted friend about their feeling.
Both B and C
In which two areas do organizations need to excel if they are to perform and grow over a long timeframe
Answers
The two areas do organizations need to excel is by creating or building strategic partnerships, and also making strategic business decisions.
What is growth/development in business?In business development, one needs great ideas, initiatives, and activities that can aid or help one to make a business good.
Conclusively, This growth involves increasing revenues, business expansion, increasing profits etc.
Learn more about development in business from
https://brainly.com/question/1621812
From 1995 to 1997, the number of web users
Doubled
Tripled
Quadrupled
Remained the same
Answers
Where in PowerPoint should a user navigate to complete the tasks listed below?
Save a presentation:
Add a table to a slide:
Repeat or undo an action:
Expand the options for a command group:
Answers
Answer:Add a table to a slide. ribbon. Repeat or undo an action. Quick Access Toolbar. Expand the options for a command group: ribbon. Which feature helps a user
Answer:
Where in PowerPoint should a user navigate to complete the tasks listed below?
Save a presentation:
✔ Quick Access toolbar
Add a table to a slide:
✔ ribbon
Repeat or undo an action:
✔ Quick Access toolbar
Expand the options for a command group:
✔ ribbon
Explanation:
Yeah
Suggest
three ways in which hardware can be prevented from everyday wear and tear
Answers
The three ways in which hardware can be prevented from everyday wear and tear are:
Regular maintenanceProtective measuresProper handling and storageCare of hardwareRoutine maintenance can effectively prevent hardware deterioration by adhering to a scheduled maintenance plan. This encompasses duties like tidying up, eliminating dust, and applying lubrication to the components that are movable to maintain their peak state.
Precautionary steps, such as employing cases, envelope, or screen guards, may act as a barrier against hardware harm, scratches, and unintended spills. These accessories have the ability to soak up shock and reduce the likelihood of damage and deterioration.
Educating individuals on appropriate methods of handling and storing gadgets, such as refraining from dropping or mistreating them, can markedly limit deterioration. To extend the longevity of hardware, it is advisable to keep it in a secure and suitable setting, free from excessive heat, dampness, and dirt.
Read more about hardware here:
https://brainly.com/question/24370161
#SPJ1
Write a program that creates a login name for a user, given the user's first name, last name, and a four-digit integer as input. Output the login name, which is made up of the first five letters of the last name, followed by the first letter of the first name, and then the last two digits of the number (use the % operator). If the last name has less than five letters, then use all letters of the last name. Hint: Use the to_string() function to convert numerical data to a string.
Answers
Answer:
In C++:
#include <iostream>
#include <string>
#include <sstream>
using namespace std;
int main(){
string lname, fname,stringnum; int num; string login, pwd;
cout<<"Last Name: "; cin>>lname;
cout<<"First Name: "; cin>>fname;
cout<<"Four-digit integer: "; cin>>num;
stringnum = to_string(num).substr(0,4);
stringstream geek(stringnum); geek>>num;
num = num%100;
pwd = to_string(num);
if(lname.length()<5){ login = lname+fname.substr(0,1); }
else{ login = lname.substr(0,5)+fname.substr(0,1); }
cout<<"Login Name: "<<login<<endl;
cout<<"Password: "<<pwd<<endl;
return 0;
}
Explanation:
This declares all necessary variables
string lname, fname,stringnum; int num; string login, pwd;
This prompts the user for last name
cout<<"Last Name: "; cin>>lname;
This prompts the user for first name
cout<<"First Name: "; cin>>fname;
This prompts the user for a four digit integer
cout<<"Four-digit integer: "; cin>>num;
This converts the input number to string and gets only the first four integer
stringnum = to_string(num).substr(0,4);
This converts the string back to an integer
stringstream geek(stringnum); geek>>num;
This gets the last two of the four digit integer
num = num%100;
This gets the password of the user
pwd = to_string(num);
This gets the login name of the user.
This is executed if the length of the first name is less than 5
if(lname.length()<5){ login = lname+fname.substr(0,1); }
This is executed if otherwise
else{ login = lname.substr(0,5)+fname.substr(0,1); }
This prints the login name
cout<<"Login Name: "<<login<<endl;
This prints the password
cout<<"Password: "<<pwd<<endl;
HELP ASAP PLZ PLZ PLZTegan is playing a computer game on her smartphone and the battery is getting low. When she goes to charge her phone, she notices that the cord is broken. What can Tegan do to solve her problem?
Plug in the smartphone to charge.
Put tape around the broken part of the cord.
Ask a trusted adult for help replacing the cord.
Use the laptop charger instead.
Answers
Answer:
3rd choice
Explanation:
Select the correct answer.
Which section of a research paper contains all the sources that are cited in the paper?
ОА.
abstract
OB.
bibliography
OC.
review of literature
OD
analysis
thing
Reset
Next
Answers
Answer:
abstract
Explanation:
as it includes the main finding of the work, usually in research papers References cited is where that information would be.
Define a method named orderOfAppearance() that takes the name of a role as an argument and returns that role's order of appearance. If the role is not found, the method returns 0. Ex: orderOfAppearance("Forrest Gump") returns 1. Hint: A method may access the object's properties using the keyword this. Ex: this.title accesses the object's title property.
// Code will be tested with different roles and movies
let movie = {
title: "Forrest Gump",
director: "Robert Zemeckis",
composer: "Alan Silvestri",
roles: [ // Roles are stored in order of appearance
"Forrest Gump",
"Young Forrest Gump",
"Jenny Curran",
"Lieutenant Dan Taylor"
],
orderOfAppearance: function(role) {
}
};
Answers
The method named orderOfAppearance() that takes the name of a role as an argument is; Written as below
How to write a Program in Java?The steps to write this Java program is as follows;
1) Initialize the movie JSON (JavaScript Object Notation) having the name, director, composer and title properties.2) Define a roleOf: function that has a name parameter.3) Check whether the selected is not equal to undefined and then return that name.4) Otherwise display this message: "0".let movie = {
name: "Forrest Gump",
director: "Robert Zemeckis",
composer: "Alan Silvestri",
title: {
"Forrest Gump",
"Young Forrest Gump"
"Jenny Curran"
"Lieutenant Dan Taylor"
},
orderOfAppearance: function (role) {
if (typeof (this.title[role]) !== 'undefined') {
return this.title[role];
} else {
return "0";
}
}
};
Read more about java programming at; https://brainly.com/question/16397886
Compilers can have a profound impact on the performance of an application. Assume that for a program, compiler A results in a dynamic instruction count of 1.0E9 and has an execution time of 1.1 s, while compiler B results in a dynamic instruction count of 1.2E9 and an execution time of 1.5 s. a. Find the average CPI for each program given that the processor has a clock cycle time of 1 ns.
Answers
Answer:
The answer is "1.25"
Explanation:
\({CPU \ time}= {instructions \times CPI \times cycle\ time}\)
\(\therefore\\\CPI= \frac{CPU \ time}{instructions \times cycle \ time} \\\\cycle \ time = 1 \\\\ns = 10^{-9} s \\\)
Also for this context, it executes the time = CPU time. So, the compiler A, we has
\(CPI_{A}= \frac{CPU \ time_{A}} {instructions_{A} \times cycle \ time}= \frac{1.1 s}{10^{9} \times 10^{-9} s}= 1.1\)
For compiler B, we have
\(CPI_{B}= \frac{CPU \ times_{B}} {instructions_{B} \times cycle \ time}\)
\(= \frac{1.5\ s}{ 1.2 \times 10^{9} \times 10^{-9} \ s}\\\\= \frac{1.5}{ 1.2 }\\\\= 1.25\)
The average CPI for each program given that the processor has a clock cycle time of 1 ns is : 1.1, 1.25.
Average CPI for each programCPI (Complier A)=CPU time/Instruction×Cycle time
Where:
Cycle time=1ns=10^-9s
Hence:
CPI (Complier A)=1.1s/10^9×10^-9s
CPI (Complier A)=1.1
CPI (Complier B)=CPU time/Instruction×Cycle time
CPI (Complier B)=1.5s/1.2×10^9×10^-9s
CPI (Complier B)=1.25
Inconclusion the average CPI for each program given that the processor has a clock cycle time of 1 ns is : 1.1, 1.25.
Learn more about average CPI here:https://brainly.com/question/24723238
e. Define the following terms: i. BIT ii. Nibble iii. Byte
Answers
ii. A nibble is a group of four bits or half a byte. It can represent 16 possible values, ranging from 0000 to 1111 in binary.
iii. A byte is a unit of digital information that consists of eight bits. It can represent 256 possible values, ranging from 00000000 to 11111111 in binary. Bytes are used to represent characters, numbers, and other types of data in computer systems.
How to solve everything in Kotlin??
A) create a method that takes a string as a parameter and inverts it.
C) Create a car class that contains Brand, model, year of release and current speed. Use the primary constructor
B) create the main function, and create 4 objects of class car and store them in a vector and print them.
Answers
Answer:
crreate a method that takes a string as a perimeter and inverts it
Write an expression that will print "in high school" if the value of user_grade is between 9 and 12 (inclusive).
Answers
Answer:
C#
if(user_grade >=9 && user_grade <=12)
{
Console.WriteLine("In Highschool");
}
Python
if user_grade >= 9 & user_grade <= 12:
print("In Highschool")
Java
if(user_grade >=9 && user_grade <=12)
{
System.println("In Highschool");
}
Explanation:
Check
Which of these tasks can be accomplished when the drop-down menu of the Bullets icon is clicked? Check all that
apply.
Answers
Which of these tasks can be accomplished when the drop-down menu of the Bullets icon is clicked? Check all that
apply.
Indent the ideas in the bulleted list.
Change the number level of the list.
Choose the bullet to be used in the list.
Define the new bullet to be used in the list.
Pick the number format to be used in the list.
Answer:
Choose the bullet to be used in the list.
Define the new bullet to be used in the list.
Explanation:
When using Microsoft Word text editor, when the drop-down menu of the bullet icon is clicked, the following tasks can be accomplished which are to choose the bullet to be used in the list and define the new bullet to be used in the list.
A bullet is used to identify or list out important items, sometimes in ascending order, and are used to organize information to make the important points easy to pick out.
Answer:
Choose the bullet to be used in the list.
Define the new bullet to be used in the list.
Explanation:
.
Giving reasons for your answer based on the type of system being developed, suggest the most appropriate generic software process model that might be used as a basis for managing the development of the following systems: • A system to control anti-lock braking in a car • A virtual reality system to support software maintenance • A university accounting system that replaces an existing system • An interactive travel planning system that helps users plan journeys with the lowest environmental impac
Answers
There are different kinds of systems. the answers to the questions is given below;
Anti-lock braking system: Is simply known as a safety-critical system that helps drivers to have a lot of stability and hinder the spinning of car out of control. This requires a lot of implementation. The rights generic software process model to use in the control of the anti-lock braking in a car is Waterfall model. Virtual reality system: This is regarded as the use of computer modeling and simulation that helps an individual to to be able to communicate with an artificial three-dimensional (3-D) visual etc. the most appropriate generic software process model to use is the use of Incremental development along with some UI prototyping. One can also use an agile process.University accounting system: This is a system is known to have different kinds of requirements as it differs. The right appropriate generic software process model too use is the reuse-based approach.
Interactive travel planning system: This is known to be a kind of System that has a lot of complex user interface. The most appropriate generic software process model is the use of an incremental development approach because with this, the system needs will be altered as real user experience gain more with the system.
Learn more about software development from
https://brainly.com/question/25310031
after you submit the answer to this question, webassign will show correct answers with green check marks and wrong answers with red x marks. you will sometimes want to use the e-format for exponentials. for example, 2.53x104 or 25310 would be entered as 2.53e4. 3.567x10-3 or 0.003567 would be entered as 3.57e-3 express the following numbers to three significant digits in the e-format. use one number to the left of the decimal and two to the right. 0.001397 webassign will check your answer for the correct number of significant figures. 1.39e-3 correct: your answer is correct. 0.000013125 webassign will check your answer for the correct number of significant figures. 13.125e-6 partial credit: your answer received partial credit. check the number of significant figures. 35116
Answers
When more items like points or segments are added to your graph, such as in WebAssign's graphing tool, the score can become incorrect.
What do the red numbers mean in WebAssign?Observe the information defining your response by clicking Submission Data to verify this. To make sure no additional objects are drawn, clear the picture and begin again.Assignments The majority of WebAssign questions use randomized values, which are typically shown in red. By allowing for the practice of several versions of the question if enabled, randomizing question values aids in ensuring that every student has an equal opportunity to succeed on coursework.Log files can be compared side by side to look for similarities. When further research is required, you can examine student answer data to determine whether correct/incorrect responses match in ways that seem to suggest student cheating.If enabled, clicking Practice Another at the top of a question in an assignment will allow you to practice on an alternative, randomized version of the question. Practice questions are not graded, but they can be used to gauge how well you comprehend the issue.To Learn more About WebAssign's, refer TO:
https://brainly.com/question/14550245
#SPJ4
What is Machine Learning (ML)?
Answers
Answer:
its where you learn about machines