________________ are virtual machines that already contain an operating system, are sometimes preloaded with application software, and are used to create new virtual machines.
Answers
Template virtual machines are pre-built virtual machines that serve as a starting point for creating new virtual machines.
They contain an operating system and may also come preloaded with application software.
These templates help to streamline the process of creating new virtual machines by providing a pre-configured environment that can be customized as needed.
As a result, these virtual appliances save time, reduce errors, and improve consistency in managing virtual infrastructure.
They are widely used in cloud computing, data centers, and network management to optimize resource utilization, scalability, and flexibility.
Therefore, the right answer is Template.
To know more about virtual machines visit:
brainly.com/question/30774282
#SPJ11
Related Questions
Java
Write a program Checkerboard that takes an integer command-line argu-
ment n and uses a loop nested within a loop to print out a two-dimensional n-by-n
checkerboard pattern with alternating spaces and asterisks.
Answers
public static void main(String[] args) {
int n = Integer.parseInt(args[0]);
for (int i = 0; i < n; i++) {
for (int j = 0; j < n; j++) {
if ((i + j) % 2 == 0) {
System.out.print("*");
} else {
System.out.print(" ");
}
}
System.out.println();
}
}
}
The program takes an integer command-line argument n and uses two nested loops to print out an n-by-n checkerboard pattern. The if statement inside the inner loop checks if the sum of the current row index i and column index j is even, and if so, it prints an asterisk. Otherwise, it prints a space.
This is a subjective question, hence you have to write your answer in the Text-Field given below. hisht74528 77008 Assume you are the Quality Head of a mid-sized IT Services organizati
Answers
As the Quality Head of a mid-sized IT Services organization, your primary responsibility is to ensure the delivery of high-quality services and products to clients.
This involves establishing and implementing quality management systems, monitoring processes, and driving continuous improvement initiatives. Your role includes overseeing quality assurance processes, such as defining quality standards, conducting audits, and implementing corrective actions to address any deviations or non-compliance. You are also responsible for assessing customer satisfaction, gathering feedback, and incorporating customer requirements into the quality management system. Additionally, you play a crucial role in fostering a culture of quality within the organization by promoting awareness, providing training, and encouraging employee engagement in quality initiatives. Collaboration with other departments, such as development, testing, and project management, is essential to ensure quality is embedded throughout the organization's processes and practices.
Learn more about Quality Management Systems here:
https://brainly.com/question/30452330
#SPJ11
when describing blocks of ip addresses, what does cidr do?
Answers
Classless inter-domain routing is known as CIDR. It is an approach to IP address distribution and packet routing. An IP address's network prefix is specified via CIDR.
CIDR (Classless Inter-Domain Routing) is a more effective and adaptable method of allocating and routing Internet Protocol (IP) packets than the conventional IP address classes. A variable-length subnet mask (VLSM) is used by CIDR to distribute IP addresses, enabling more accurate distribution and greater address space use. Routing is made easier and subnets may be easily created thanks to the CIDR notation, which specifies the amount of bits in the network portion of the address. Internet Service Providers (ISPs) and network administrators manage IP addresses and routing tables using CIDR, which has evolved into the industry standard for IP address allocation and routing.
Learn more about CIDR here:
https://brainly.com/question/30775427
#SPJ4
2. INFERENCE (a) The tabular version of Bayes theorem: You are listening to the statistics podcasts of two groups. Let us call them group Cool og group Clever. i. Prior: Let prior probabilities be proportional to the number of podcasts each group has made. Cool made 7 podcasts, Clever made 4. What are the respective prior probabilities? ii. In both groups they draw lots to decide which group member should do the podcast intro. Cool consists of 4 boys and 2 girls, whereas Clever has 2 boys and 4 girls. The podcast you are listening to is introduced by a girl. Update the probabilities for which of the groups you are currently listening to. iii. Group Cool does a toast to statistics within 5 minutes after the intro, on 70% of their podcasts. Group Clever doesn't toast. What is the probability that they will be toasting to statistics within the first 5 minutes of the podcast you are currently listening to? Digits in your answer Unless otherwise specified, give your answers with 4 digits. This means xyzw, xy.zw, x.yzw, 0.xyzw, 0.0xyzw, 0.00xyzw, etc. You will not get a point deduction for using more digits than indicated. If w=0, zw=00, or yzw = 000, then the zeroes may be dropped, ex: 0.1040 is 0.104, and 9.000 is 9. Use all available digits without rounding for intermediate calculations. Diagrams Diagrams may be drawn both by hand and by suitable software. What matters is that the diagram is clear and unambiguous. R/MatLab/Wolfram: Feel free to utilize these software packages. The end product shall nonetheless be neat and tidy and not a printout of program code. Intermediate values must also be made visible. Code + final answer is not sufficient. Colours Use of colours is permitted if the colours are visible on the finished product, and is recommended if it clarifies the contents.
Answers
(i) Prior probabilities: The respective prior probabilities can be calculated by dividing the number of podcasts made by each group by the total number of podcasts made.
(ii) Updating probabilities based on the gender of the podcast intro: Since the podcast intro is done by a girl, we need to calculate the conditional probabilities of the group given that the intro is done by a girl.
(iii) Probability of toasting to statistics within the first 5 minutes: Since Group Cool toasts on 70% of their podcasts and Group Clever doesn't toast, we can directly use the conditional probabilities.
Group Cool: 7 podcasts
Group Clever: 4 podcasts
Total podcasts: 7 + 4 = 11
Prior probability of Group Cool: 7/11 ≈ 0.6364 (rounded to four decimal places)
Prior probability of Group Clever: 4/11 ≈ 0.3636 (rounded to four decimal places)
(ii) Updating probabilities based on the gender of the podcast intro: Since the podcast intro is done by a girl, we need to calculate the conditional probabilities of the group given that the intro is done by a girl.
Group Cool: 4 girls out of 6 members
Group Clever: 4 girls out of 6 members
Conditional probability of Group Cool given a girl intro: P(Group Cool | Girl intro) = (4/6) * 0.6364 ≈ 0.4242 (rounded to four decimal places)
Conditional probability of Group Clever given a girl intro: P(Group Clever | Girl intro) = (4/6) * 0.3636 ≈ 0.2424 (rounded to four decimal places)
(iii) Probability of toasting to statistics within the first 5 minutes: Since Group Cool toasts on 70% of their podcasts and Group Clever doesn't toast, we can directly use the conditional probabilities.
Probability of toasting within the first 5 minutes given Group Cool: P(Toasting | Group Cool) = 0.70
Probability of toasting within the first 5 minutes given Group Clever: P(Toasting | Group Clever) = 0
The overall probability of toasting within the first 5 minutes of the podcast you are currently listening to can be calculated using the updated probabilities from step (ii):
P(Toasting) = P(Toasting | Group Cool) * P(Group Cool | Girl intro) + P(Toasting | Group Clever) * P(Group Clever | Girl intro)
= 0.70 * 0.4242 + 0 * 0.2424
≈ 0.2969 (rounded to four decimal places)
The prior probabilities of Group Cool and Group Clever were calculated based on the number of podcasts each group made. Then, the probabilities were updated based on the gender of the podcast intro. Finally, the probability of toasting to statistics within the first 5 minutes of the current podcast was estimated using the conditional probabilities.
To know more about Prior Probabilities, visit
https://brainly.com/question/29381779
#SPJ11
Have you watched, or listened to, a documentary on your computer, smartphone, or on demand? Do you think these new distribution choices help or hurt future opportunities for video journalists? Support your answer.
Answers
Answer:
Yes, and No it does not hurt their opportunities
Explanation:
The main goal of video journalism is to get their work in front of as many people as possible so they can share their stories with the entire world. These platforms allow for this to happen. Smartphones, Computers, On-demand video platforms, etc. all allow Video Journalists to publish their work in various different platforms and formats in order to get their work seen by hundreds, thousands, or even millions of individuals. Therefore, It does not hurt video journalists, but instead encourages them and helps them further their work by creating more opportunities.
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


What is the definition of a flowchart? *
Answers
Answer:
A flowchart is simply a graphical representation of steps. It shows steps in sequential order and is widely used in presenting the flow of algorithms, workflow or processes. Typically, a flowchart shows the steps as boxes of various kinds, and their order by connecting them with arrows.
Explanation:
Modify the above program to let the Red and Blue led blink at the same time.Use an Keil uVision5 IDE.
/* Toggling LED in C using Keil header file register definitions. * This program toggles green LED for 0.5 second ON and 0.5 second OFF.
* The green LED is connected to PTB19.
* The LEDs are low active (a '0' turns ON the LED).
*/
#include
/* Function Prototype */
void delayMs(int n);
int main (void) {
SIM->SCGC5 |= 0x400; /* enable clock to Port B */
PORTB->PCR[19] = 0x100; /* make PTB19 pin as GPIO */
PTB->PDDR |= 0x80000; /* make PTB19 as output pin */
while (1) {
PTB->PDOR &= ~(0x80000U); /* turn on green LED */
delayMs(500);
PTB->PDOR |= (0x80000U); /* turn off green LED */
delayMs(500);
}
}
/* Delay n milliseconds
* The CPU core clock is set to MCGFLLCLK at 41.94 MHz in SystemInit().
*/
void delayMs(int n) {
int i;
int j;
for(i = 0 ; i < n; i++)
for (j = 0; j < 7000; j++) {}
}
Answers
Modify the above program to let the Red and Blue led blink at the same time, using an Keil uVision5 IDE.
Modifying the previous program to enable the Red and Blue LED to flash simultaneously in C using Keil header file register definitions involves the following steps:Replace the header files with the ones that support the Red and Blue LED. The header files below work for the Red and Blue LED. #include #include Add a few lines of code to turn the red and blue LEDs on and off.
{ PTB->PDOR &= ~(0x10000U); //turn ON Red LED PTB->PDOR &= ~(0x20000U); //turn ON Blue LED delayMs(500); PTB->PDOR |= (0x10000U); //turn OFF Red LED PTB->PDOR |= (0x20000U); //turn OFF Blue LED delayMs(500); }
To know more about led blink visit:
https://brainly.com/question/33463931
#SPJ11
Harry is the cloud administrator for a company that stores object-based data in a public cloud. Because of regulatory restrictions on user access to sensitive security data, what type of access control would you suggest he implement to meet his company's security policies?
Answers
Answer:
The correct answer will be "Mandatory access control".
Explanation:
MAC seems to be a security standard protocols limited by the designation, initialization including verification of the systems. These policies and configurations are implemented through one centralized controller and therefore are accessible to the system admin.MAC establishes and maintains a centralized implementation of sensitive requirements in information security.why is what you say in business as important as how you say it
Answers
Answer:
Because the things you say and how you say it can determine whether or not you sell an item, make a deal with another company and things of that nature. Hope this helps!!
on circuit switched portions of a pstn, what set of standards established by the itu is used to handle call signaling?
Answers
On circuit switched portions of a PSTN, the set of standards that are established by the ITU which is used to handle call signaling is: D. SS7
What is a modem?In Computer technology, a modem can be defined as a type of networking device that is designed and developed to convert the signals from the wire such as a telephone line, so that data can be sent and received by a computer.
In Computer networking, a modem simply refers to a network connectivity device that must be used by an end user to access the Internet through an internet service provider (ISP) or the Public Telephone Service Network (PSTN).
In conclusion, SS7 is an abbreviation for Signaling System 7 and it can be defined as a set of standards that is established by the International Telecommunication Union (ITU) in order to effectively and efficiently handle call signaling on circuit switched portions of a Public Telephone Service Network (PSTN).
Read more on modem here: brainly.com/question/7320816
#SPJ1
Complete Question:
On circuit switched portions of a PSTN, what set of standards established by the ITU is used to handle call signaling? (A) MCU (B) H.323 (C) H.225 D. SS7
Choose all items that represent features of the job application process.
Answers
Answer:we need some options or we can’t help you
Explanation:
A person buys a product from XYZ shop. You have to input quantity of a product and price of one product. Provide 10 percent discount on bill, display bill before discount, amount discounted and bill after discount. Write pseudo code algorithm to process the requirement.
Answers
Answer:
The pseudocode algorithm is as follows:
StartInput QuantityInput PriceBill = Quantity * PriceDiscount = 0.10 * BillDisplay "Before Discount: "+billDisplay "Discount: "+discountDisplay "After Discount: "+(bill - discount)StopExplanation:
This begins the algorithm
Start
First, get input for quantity
Input Quantity
Then, get input for price
Input Price
Calculate the total bill (before discount)
Bill = Quantity * Price
Calculate discount
Discount = 0.10 * Bill
Print the total bill (before discount)
Display "Before Discount: "+bill
Print the discounted amount
Display "Discount: "+discount
Print the total bill (after discount)
Display "After Discount: "+(bill - discount)
End of algorithm
Stop
What are the best steps to learn a 2d animation software?
Answers
Answer:
this is the correct answer
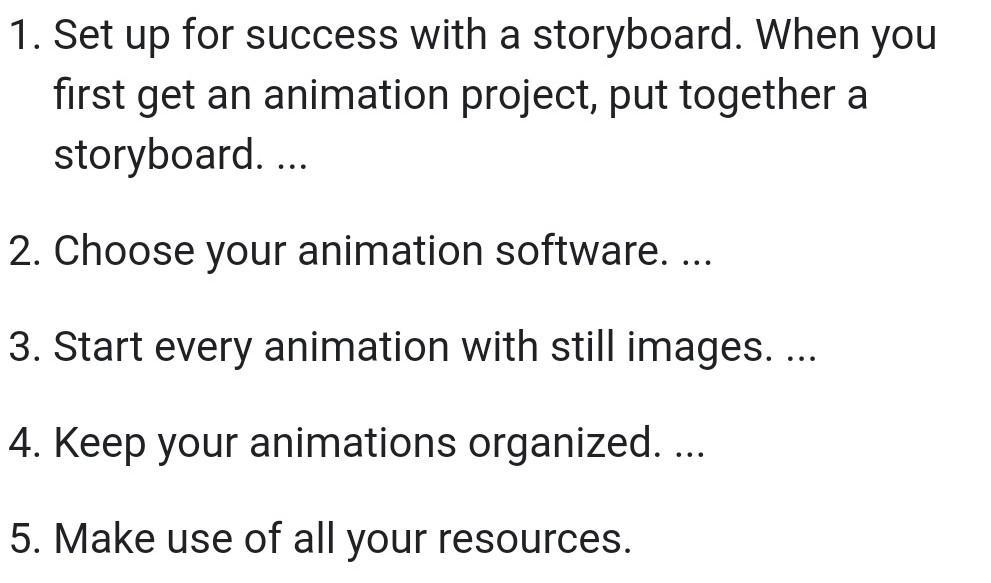
1. Familiarize yourself with the user interface of the software.
2. Read tutorials and watch videos from experts on how to use the software.
3. Practice with simple projects like animations, short films, or motion graphics.
4. Get feedback on your projects from other professionals in the field.
5. Attend online workshops or classes to learn more advanced techniques.
6. Experiment and try different approaches to create unique pieces.
the stringbuilder class's insert method allows you to insert into the calling object's stringa. trueb. false
Answers
The statement is true. The insert method of the StringBuilder class allows you to insert characters or strings into the calling object's string.
The StringBuilder class in Java provides methods for efficient manipulation of strings. One of the methods is insert, which allows you to insert characters or strings at a specified position within the StringBuilder object's string. The insert method takes two arguments: the index at which the insertion should occur and the value to be inserted. This method modifies the original StringBuilder object by adding the specified value at the desired position, shifting the existing characters to accommodate the insertion. This enables dynamic and efficient string manipulation, making it a useful feature in scenarios where you need to modify a string in a mutable manner.
Learn more about StringBuilder class here: brainly.com/question/18521991
#SPJ11
____ allow us to store a binary image in code. (1 point)
Bitmaps
Classes
Arrays
Unions
Answers
Answer:
A. Bitmaps
Explanation:
hey guys just dropped some hot beats so go and follow me my user is the beats and comment if you would do that that would be grate
Answers
Write an expression that will cause the following code to print "I am a teenager" if the value of userAge is less than 20.
import java. Util. Scanner;
public class AgeChecker {
public static void main (String [] args) {
int userAge;
scanner scnr = new Scanner(System. In);
userAge = scnr. NextInt(); // Program will be tested with values: 18, 19, 20, 21.
if (/ *Your solution goes here*/ ) {
System. Out. Println("I am an adult");
}
else {
System. Out. Println("I am a teenager");
}
}
}
Answers
Replace if userAge > 20 with userAge > 19 so "I am a teenager" if the value of userAge is less than 20.
if userAge > 20 checks if age is 21, 22, 23, 24........
The else condition which prints "I am a teenager" checks if age is 20, 19, 18....
Notice that 20 is inclusive of the else condition; this shouldn't be because for userAge to be less than 20, 20 isn't inclusive
To solve this,
Replace if userAge > 20 with userAge > 19
So that, the else
The else condition which prints "I am a teenager" checks if age is 19, 18, 17, 16....
Learn more about userAge here:
https://brainly.com/question/17119319
#SPJ4
Need help on Assignment 4: Evens and Odds

Answers
n = int(input("How many numbers do you need to check? "))
even = 0
odd = 0
for x in range(n):
num = int(input("Enter number: "))
if num % 2 == 0:
even += 1
print(str(num) + " is an even number.")
else:
odd += 1
print(str(num) + " is an odd number.")
print("You entered " + str(even) + " even number(s).")
print("You entered " + str(odd) + " odd number(s).")
This works for me. Best of luck.
"
Describe the framework of Green Operations in Information technology"
Answers
Green operations (GO) is a comprehensive concept that seeks to achieve environmental and social responsibility in IT companies' operations. The Green Operations framework was developed to assist IT companies in integrating environmental and social sustainability into their daily operations.
Green Operations in Information Technology (IT) refer to the creation of a digital environment that ensures environmental and social sustainability by increasing energy efficiency, reducing e-waste, and conserving natural resources. This system has been implemented to reduce IT's negative environmental impact and boost its economic and social sustainability. The Green Operations framework of IT consists of four stages:
Measure, analyze, and identify environmental and social risks and opportunitiesRedesign IT systems and procedures to meet environmental and social sustainability standardsImplement green operations programs and best practicesMonitor, assess, and report environmental and social sustainabilityIn conclusion, Green Operations are critical in enhancing environmental and social sustainability in IT companies. GO helps organizations decrease their environmental impact while also increasing economic efficiency. Companies are able to conduct environmentally sustainable operations through the Green Operations framework by integrating environmental and social considerations into daily business operations.
To learn more about Green operations, visit:
https://brainly.com/question/31232761
#SPJ11
Write a program that takes a date as input and outputs the date's season in the northern hemisphere. The input is a string to represent the month and an int to represent the day. Note: End with a newline.
Answers
A program that takes a date as input and outputs the date's season in the northern hemisphere will bear this order
cout << "Winter"
cout << "Spring"
cout << "Summer"
cout << "Autumn"
Complete Code below.
A program that takes a date as input and outputs the date's season in the northern hemisphereGenerally, The dates for each season in the northern hemisphere are:
Spring: March 20 - June 20Summer: June 21 - September 21Autumn: September 22 - December 20Winter: December 21 - March 19And are to be taken into consideration whilst writing the code
Hence
int main() {
string mth;
int dy;
cin >> mth >> dy;
if ((mth == "January" && dy >= 1 && dy <= 31) || (mth == "February" && dy >= 1 && dy <= 29) || (mth == "March" && dy >= 1 && dy <= 19) || (mth == "December" && dy >= 21 && dy <= 30))
cout << "Winter" ;
else if ((mth == "April" && dy >= 1 && dy <= 30) || (mth == "May" && dy >= 1 && dy <= 30) || (mth == "March" && dy >= 20 && dy <= 31) || (mth == "June" && dy >= 1 && dy <= 20))
cout << "Spring" ;
else if ((mth == "July" && dy >= 1 && dy <= 31) || (mth == "August" && dy >= 1 && dy <= 31) || (mth == "June" && dy >= 21 && dy <= 30) || (mth == "September" && dy >= 1 && dy <= 21))
cout << "Summer" ;
else if ((mth == "October" && dy >= 1 && dy <= 31) || (mth == "November" && dy >= 1 && dy <= 30) || (mth == "September" && dy >= 22 && dy <= 30) || (mth == "December" && dy >= 0 && dy <= 20))
cout << "Autumn" ;
else
cout << "Invalid" ;
return 0;
}
For more information on Programming
https://brainly.com/question/13940523
Which guideline should an employee use when taking notes for a report?
O A. Create long, accurate notes by copying and pasting
B. Stick to key points, uncluttered with the name of the source
OC. Include information about unrelated topics in case he or she
expands the report
D. Write ideas briefly in his or her own words, and give the source
Answers
When taking notes for a report, an employee should write ideas briefly in his or her own words, and give the source.
The correct andswer is option D.
This involves writing ideas briefly in their own words and providing the source of the information. By doing so, the employee can effectively summarize and synthesize key points, making the report concise and easily understandable. This approach ensures that the report is focused on relevant information while acknowledging the original source of the information.
Including long, accurate notes by copying and pasting (option A) can lead to excessive detail and potential plagiarism issues. Sticking to key points without mentioning the source (option B) is not recommended as it omits important context and may lead to credibility issues. Including information about unrelated topics (option C) can make the report unfocused and difficult to follow.
Therefore, option D is correct.
For more such questions on plagiarism, click on:
https://brainly.com/question/11946294
#SPJ11
What tag is used to contain information about a web page, such as the title and related pages?
Answers
Answer:
<head>
Explanation:
correct on edge 2021
The tag that has been used for the headings and titles and the information contained in a web page is <head>.
What is a tag?A tag is given as the label that has been attached to someone or something in order to add identification to the particular thing. The tag in the HTML or any other language has been used for the conversion of the HTML document into web pages. The tags are braced in the < >.
The headings and the subheadings or titles stand for the analysis of the topic and the concern of the particular topic or subject. There was the presence of the tag such as head, meta, footer, and header.
The title and the heading to a particular subject have been the representation of the topic that has been covered in the meta description part. Thereby, the title and important information are given in the <head> tag.
Learn more about the tag, here:
https://brainly.com/question/8441225
#SPJ5
Which of the following types of copyright license is most appropriate if you create a graphic and would like to share it with anyone for any purpose as long as you receive credit?
A. All Rights Reserved
B. Public Domain
C. Some Rights Reserved: Attribution
D. Some Rights Reserved: Share Alike
Can someone help me out with this? Thanks!
Answers
Answer:
C is the correct answer:)
Explanation:
The most appropriate type of copyright license for the described scenario would be Some Rights Reserved: Attribution. The correct option is C.
What is copyright license?A copyright license is a legal agreement between the copyright holder and someone who wants to use the copyrighted material.
This licence allows others to use and distribute the graphic as long as the original creator is credited. It is a type of Creative Commons licence in which some rights are granted to others while others are reserved for the original creator.
This option is ideal if you want to share your work with others while maintaining control and receiving credit for it.
Option B, Public Domain, allows anyone to use the graphic for any purpose without attribution, whereas Option D, Some Rights Reserved: Share Alike, requires others to share derivative works under the same licence terms.
Option A, All Rights Reserved, would prohibit others from using the graphic without the creator's explicit permission.
Thus, the correct option is C.
For more details regarding copyright license, visit:
https://brainly.com/question/30696317
#SPJ2
Python please help.
Why I’m i getting this error

Answers
So, age is a of type string when it should be of type int.
def main():
age = int(input("How old are you? "))
if age >= 13:
#the rest of your code.
Strings cannot be greater than another string only integers and other number based data types. Also, you should change the list variable as I mentioned on the earlier question. Best of luck.
in this project, you work for a large corporation it security department. your duties include conducting internal digital investigations and forensics examinations on company computing systems
Answers
Remember, conducting internal digital investigations and forensic examinations requires a careful and methodical approach to ensure accurate findings and maintain the integrity of the evidence collected. In this project, you work for a large corporation's IT security department.
Your duties involve conducting internal digital investigations and forensic examinations on the company's computing systems. To perform these tasks effectively, you should follow a step-by-step process:
1. Identify the Incident: Begin by identifying any potential security incidents or suspicious activities on the company's computing systems
2. Secure the Affected System: Once an incident is identified, take immediate action to secure the affected system.
3. Gather Evidence: Collect and preserve digital evidence related to the incident. This may include log files, system snapshots, network traffic captures, and any other relevant data.
4. Analyze the Evidence: Examine the collected evidence to understand the scope and impact of the incident. This can involve analyzing log files, examining system configurations, reviewing user activity, and conducting memory and disk forensics.
5. Document Findings: Document all findings, including the evidence collected, analysis performed, and any conclusions drawn.
6. Report and Remediate: Report your findings to the appropriate stakeholders, such as management or legal teams.
7. Prevent Future Incidents: Identify any weaknesses or gaps in the company's security posture that contributed to the incident.
To know more about investigations visit:
https://brainly.com/question/1191670
#SPJ11
To begin with this lab, first replace the "Hello World!" portion of the code, with the following:
"UGETGV UQWR KU DGUV"
This is a shift-cipher, that was encrypted by shifting every letter two values to the RIGHT (for example, ‘A’ would become ‘C’, ‘B’ would become ‘D’, and so on.) Please adjust the Assembly code used in the original "Hello World!" program so that it shifts every letter BACK two values, to display the decrypted message. Remember, you’ll want to look at the ASCII encoding values discussed in the lecture for help on how to shift the values, and as one final hint you’ll likely be looking to add additional code to the ".loop" function to perform the shift.
IN ADDITION: You’ll need to compensate for the spaces between the words, and use a conditional jump to avoid decrypting if the current character you’re looking at is a SPACE. Remember, the ASCII reference has a very specific value for a blank space. So in your final decrypted message, the blank spaces between the words should still be blank spaces.
Answers
Modify the assembly code to shift each letter in "UGETGV UQWR KU DGUV" two values back and preserve spaces.
How to decrypt the shift-cipher message and handle spaces?To decrypt the given shift-cipher message and adjust the assembly code, we can modify the code inside the ".loop" function. Here's an example of how the modified assembly code would look like:
section .data
message db "UGETGV UQWR KU DGUV", 0
section .text
global _start
_start:
mov ecx, message
jmp .loop
.loop:
cmp byte [ecx], 0
je .exit
cmp byte [ecx], ' ' ; Check if the current character is a space
je .next
sub byte [ecx], 2 ; Shift the character two values back
jmp .next
.next:
inc ecx
jmp .loop
.exit:
mov eax, 4
mov ebx, 1
mov edx, 16
int 0x80
mov eax, 1
xor ebx, ebx
int 0x80
In this modified code, we start by replacing the "Hello World!" portion with the encrypted message "UGETGV UQWR KU DGUV". We then enter the .loop function, which compares the current character with zero to check for the end of the string.
If the character is a space, we skip the shifting operation by jumping to .next. Otherwise, we subtract 2 from the ASCII value of the character to shift it back two positions. Finally, we increment the pointer to the next character and jump back to .loop to continue decrypting until the end of the string.
The decrypted message will be displayed with the blank spaces preserved.
Learn more about function
brainly.com/question/30241605
#SPJ11
Silas develops this algorithm to compute the calories burned for an activity for a given number of minutes and body weight: If the activity is running, compute caloriesPerMin by dividing weight by 10.5 If the activity is walking, compute caloriesPerMin by dividing weight by 15.5 Compute numCalories by multiplying caloriesPerMin by numMinutes He implements the algorithm in an app, and users soon ask for the ability to compute the total calories for multiple sessions of walking or running. What structure must be added to the original algorithm so that it can compute the total across multiple sessions
Answers
Answer:
Explanation:
This change can be accomplished in one of two ways. The first being creating a global variable that adds to it and saves the total calories burned at the end of every session. This global variable can then be called at any time to show the total number of calories burned in all previous sessions combined. The other option would be to create a list of Session objects. Each object would hold all the information regarding each session including calories burned. Then create a function that loops through this list, adding the total calories burned in each session and outputting the total.
What is the mode? 47 42 47 42 42 47 47 49 42 49 49 47 49 49 49 47 42 42 47 52
Answers
The mode of the given dataset is 47.
How can we determine the mode of a dataset?The mode is a statistical measure that represents the most frequently occurring value in a dataset. In the given dataset, the value 47 appears the most number of times, making it the mode.
The mode is a useful measure to identify the central tendency or the most common value in a set of data. It is especially helpful when dealing with categorical or discrete data, where finding the most frequent value provides valuable insights.
Learn more about mode
brainly.com/question/28566521
#SPJ11
Create a scenario and show it on flowchart that incorporates GIS
(spatial analysis) and MIS analytics. Please keep in mind that
MIS/GIS might share a database.
Answers
A GIS can integrate maps and database data with queries True(Option A).
A Geographic Information System (GIS) is a powerful tool that can integrate various types of spatial data, including maps and database data. GIS allows users to store, analyze, and visualize geographically referenced information.
With GIS, users can perform queries and spatial analysis to extract meaningful insights from the data. This integration of maps and database data, along with the ability to perform queries, is one of the core functionalities of a GIS. It enables users to explore relationships, make informed decisions, and solve complex spatial problems.
for further information on the Database visit:
brainly.com/question/31941873
#SPJ4
The complete question on:
Create a scenario and show it on flowchart that incorporates GIS
(spatial analysis) and MIS analytics. Please keep in mind that
MIS/GIS might share a database.