An organization wants to prevent SQL and script injection attacks on its Internet web application. The organization should implement a/an:
a. Intrusion detection system
b. Firewall
c. Application firewall
d. SSL certificate
Answers
The organization should implement an application firewall to prevent SQL and script injection attacks on its Internet web application.
An application firewall is a type of firewall that is specifically designed to protect web applications from attacks such as SQL injection, cross-site scripting (XSS), and other common web application vulnerabilities. An application firewall sits between the web server and the Internet, analyzing incoming web traffic and filtering out malicious requests that could exploit vulnerabilities in the web application. An application firewall can be configured to block specific types of attacks, such as SQL injection and script injection, by examining the content of incoming requests and blocking those that contain suspicious or malicious code. While intrusion detection systems and SSL certificates are important security measures, they do not provide the same level of protection against web application attacks as an application firewall.
To learn more about organization click on the link below:
brainly.com/question/29979715
#SPJ11
Related Questions
list any six area where computer used
Answers
Answer:
I. Banking and finance.
II. Hospitals.
III. Schools.
IV. Defense and military.
V. Office.
VI. e-commerce.
Explanation:
A computer can be defined as an electronic device that is capable of receiving of data in its raw form as input and processes these data into information that could be used by an end user.
The central processing unit (CPU) is typically considered to be the brain of a computer system. It is the system unit where all of the processing and logical control of a computer system takes place.
Additionally, the component of the central processing unit (CPU) that controls the overall operation of a computer is the control unit. It comprises circuitry that makes use of electrical signals to direct the operations of all parts of the computer system. Also, it instructs the input and output device (I/O devices) and the arithmetic logic unit on how to respond to informations sent to the processor.
The six (6) areas in which a computer can be used are;
I. Banking and finance.
II. Hospitals.
III. Schools.
IV. Defense and military.
V. Office.
VI. e-commerce.
Select the correct answer
Which filter enhances the color contrast around the edges of an image?
A. Texture filters
B.Sharpen filters
C.Blur filters
D.Noise filters
Answers
Answer: C. Blur filters
Explanation:
The unsharp mask filters or blur filters can be used for professional color correction. This will adjust the contrast of the image. Edge details and may produce a darker and lighter line on all side of the edges. This helps in creating illusion or blur image giving a sharp contrast and sharper image.
So, the color answer C. Blur filters
Answer:
B, Sharpen Filters
Explanation:
i got it right lol
What is humanity’s greatest invention?
Answers
design and write a program that asks the user to enter a series of 20 numbers. the program should store the numbers in a list then display the following data:
Answers
To design and write a program that asks the user to enter a series of 20 numbers and display the required data, you can follow these steps.
Initialize an empty list to store the numbers .Use a loop to prompt the user for input 20 times. Within each iteration, ask the user to enter a number and append it to the list. After collecting all the numbers, calculate the following data using the list. Display the calculated data to the user.
By running this program, the user will be able to enter 20 numbers, and then the program will display the sum, average, maximum, and minimum of those numbers.
To know more about program visit:
https://brainly.com/question/30613605
SPJ11
when looking over an iscsi configuration, you see the string iqn.1991-05.microsoft:san.domain1.local. what are you looking at?
Answers
When looking over an iscsi configuration, you see the string iqn.1991-05.microsoft:san.domain1.local. That is iSCSI qualified name
A configuration is typically the arrangement of the elements that make up a whole, or the act of doing so.
1) When referring to computers and computer networks, a configuration frequently refers to the precise hardware and software details in terms of the devices connected, the capacity or capabilities, and the components that make up the system.
2) A configuration in a network frequently refers to the network topology.
3) Configuration is occasionally the meticulous process of establishing options that are offered during the installation of hardware and software.
Here you can learn more about configuration in the link brainly.com/question/13410673
#SPJ4
Assume that you want to click on a link to obtain a Web page. The IP address for this link is not cached in your local host, so a DNS lookup is necessary to obtain the IP address corresponding to that link. Suppose that n DNS servers are visited before your host receives the IP address from DNS. The successive visits incur an RTT of RTT1 ,..., RTTn. Further suppose that the Web page contains one object(e.g. base file) but referencing 10 other objects on the same server, like images, audio, etc. Let RTT0 denote the RTT between the local host and the server containing objects above. Assuming zero transmission time of the objects, how much time elapses when the client clicks on the link until the client receives all the objects with:
(1) Non-persistent connection without parallel TCP connection
(2) Non-persistent connection with 4 parallel TCP connections
(3) Persistent connection without pipelining
(4) Persistent connection with pipelining
Answers
Answer:
3
Explanation:
because I just got a new phone I looked up the awaner it is 3
The Quick Access Toolbar is typically
located in the top-right corner of the
window, above the ribbon.
True
False
Answers
Answer:
False
Explanation:
It is on the left
is a type of data encryption that enables users of the internet to securely and privately exchange data through the use of a pair of keys that is obtained from a trusted authority and shared through that authority. a. a private key infrastructure b. secret key encryption c. a public key infrastructure
Answers
PKI enables users of insecure public networks such as the Internet to safely and discreetly exchange data and conduct financial transactions by utilizing a public and private cryptographic key pair obtained and supplied by a trusted authority (Certifying Authority).
This appears to be a programmed that lets an individual to send an encrypted message or file using a public key that the intended receiver may unlock using another key or code, usually always a private or personal key.
This is a set of functions, rules, equipment, applications, and procedures needed to create, manage, deliver, use, preserve, and withdraw digital credentials, as well as handle encryption with the public key.
This protects against hacking or tampering with client information or data. A public key infrastructure (PKI) is a collection of roles, rules, hardware, software, and processes that are required to produce, manage, distribute, utilize, store, and revoke digital certificates as well as handle public-key encryption.
Learn more about hacking from here;
https://brainly.com/question/30295442
#SPJ4
assignment 2: room area CS python fundamentals project stem
Answers
Answer:
side1 = float(input("Enter side A: "))
side2 = float(input("Enter side B: "))
side3 = float(input("Enter side C: "))
side4 = float(input("Enter side D: "))
side5 = float(input("Enter side E: "))
rect1 = (side1 * side2)
rect2 = (side4 - side2 - side5) * (side1 - side3)
tri = (side1 - side3) * side5 * 0.5
print("Room Area: " + str(rect1+ rect2+tri))
Explanation:
My teacher helped me and I got 100 so just copy and pate this
For each item, identify the way it is usually addressed in the software industry. Applying a bug fix: Addressing a security flaw: Improving ease of use: Adding new features:
Answers
Answer:
(patch)
(patch)
(new version)
(new version)
Explanation:
gimme my 5 stars
Answer:
patch patch new new
Explanation:
i did it on edge
When registering a new domain name, either the registrar's servers or self-owned servers can be used as name servers. What function will the name servers provide for the domain?
Answers
Answer:
Authoritative
Dig Into DNS
Explanation:
In the above question that which function will the domain receive from the name server is an Authoritative functions because it is the server that issues command to the domain
The full meaning of Dig in this context is Domain Information Groper which is refer to the administration command line instrument which is use in the navigating and querying of the Domain Name System,and which is also used for verifying and troubleshooting any Domain Name System issues.
What is the difference between planks and boards?
Answers
Answer:
Planks are often used as a work surface on elevated scaffolding and need to be wide enough to provide strength without breaking when walked on. The wood is categorized as a board if its width is less than 21⁄2 in (64 mm), and its thickness is less than 11⁄2 in (38 mm).
If a computer file will not open, what should you do? A. Make sure you have the correct software to open it. B. Change the name of the file. C. Keep clicking until it will open. D. Press the F1 key to open it.
Answers
Answer:
A. Make sure you have the correct software to open it.
Explanation:
If a computer file will not open, what you should do is to make sure you have the correct software to open it.
Sometimes, computer users make the mistake of opening files with the wrong software application or program, this often leads to an error due to the incompatibility of the software application with the particular file.
Basically, all software applications are designed and developed for use with specific file extensions or formats and as such, when used to open a file it isn't developed for, it result in an error.
For instance, you cannot use Microsoft Word to open a Coreldraw file or to play music and video files.
Hence, it is necessary and important to ensure that you have the right software associated with a file format before opening any file.
Additionally, actions such as changing the name of the file, continually clicking or opening the file and pressing F1 would never open the file because of the incompatibility issue.
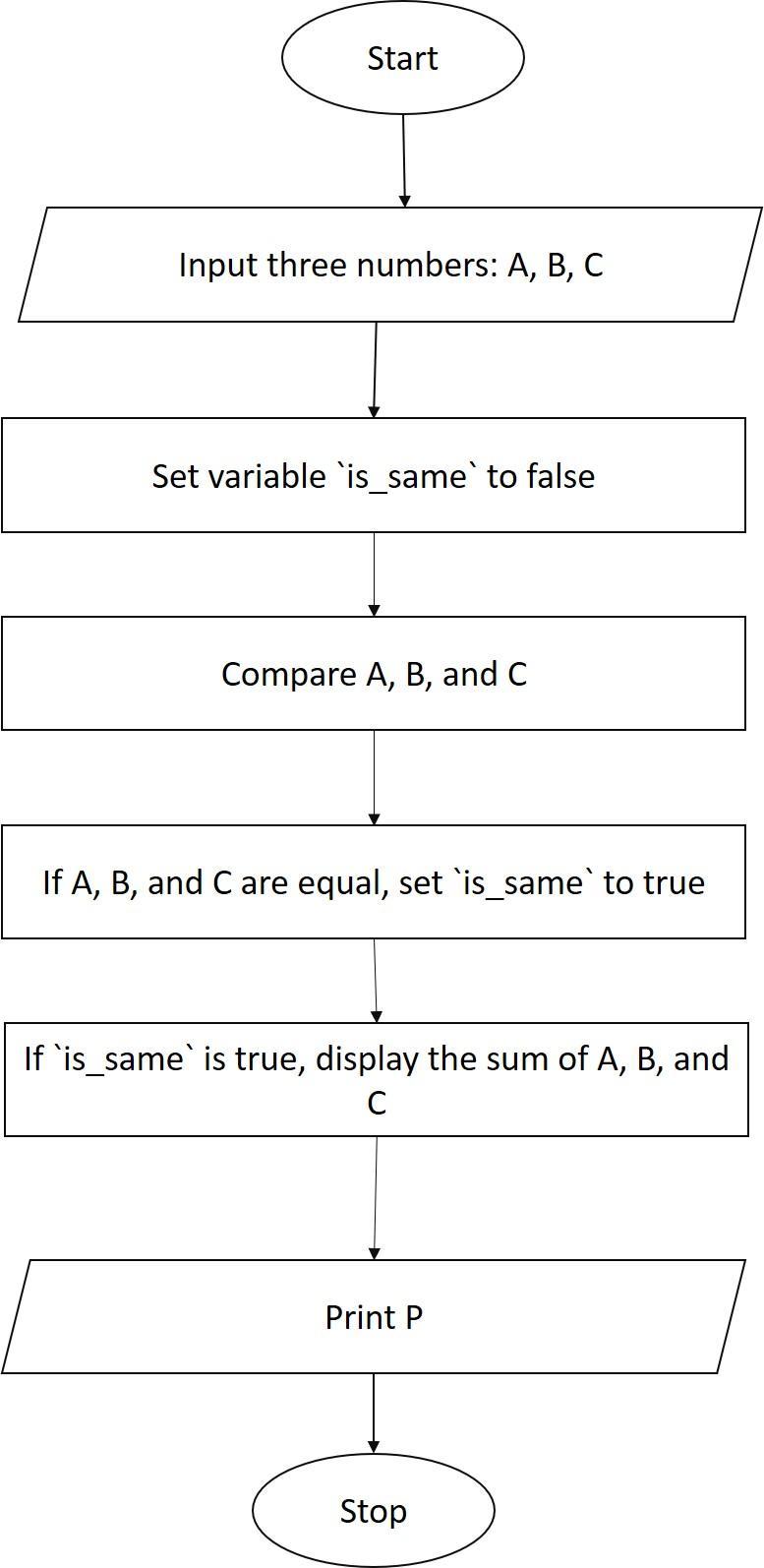
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
how many compares could it take, in the worst case, to insert n keys into an initially empty table, using linear probing with array resizing?
Answers
In the worst case, when inserting n keys into an initially empty table using linear probing with array resizing, it could take up to O(n^2) compares.
Linear probing is a collision resolution technique used in hash tables where, upon a collision, the next available slot in the table is checked linearly until an empty slot is found. However, when the table becomes full, resizing is necessary to accommodate additional keys. During the resizing process, all the keys from the old table are rehashed and inserted into the new, larger table. This operation can potentially result in many collisions, leading to additional compares for each key being inserted.
Learn more about Linear probing here:
https://brainly.com/question/30694795
#SPJ11
como se llama este icono de word

Answers
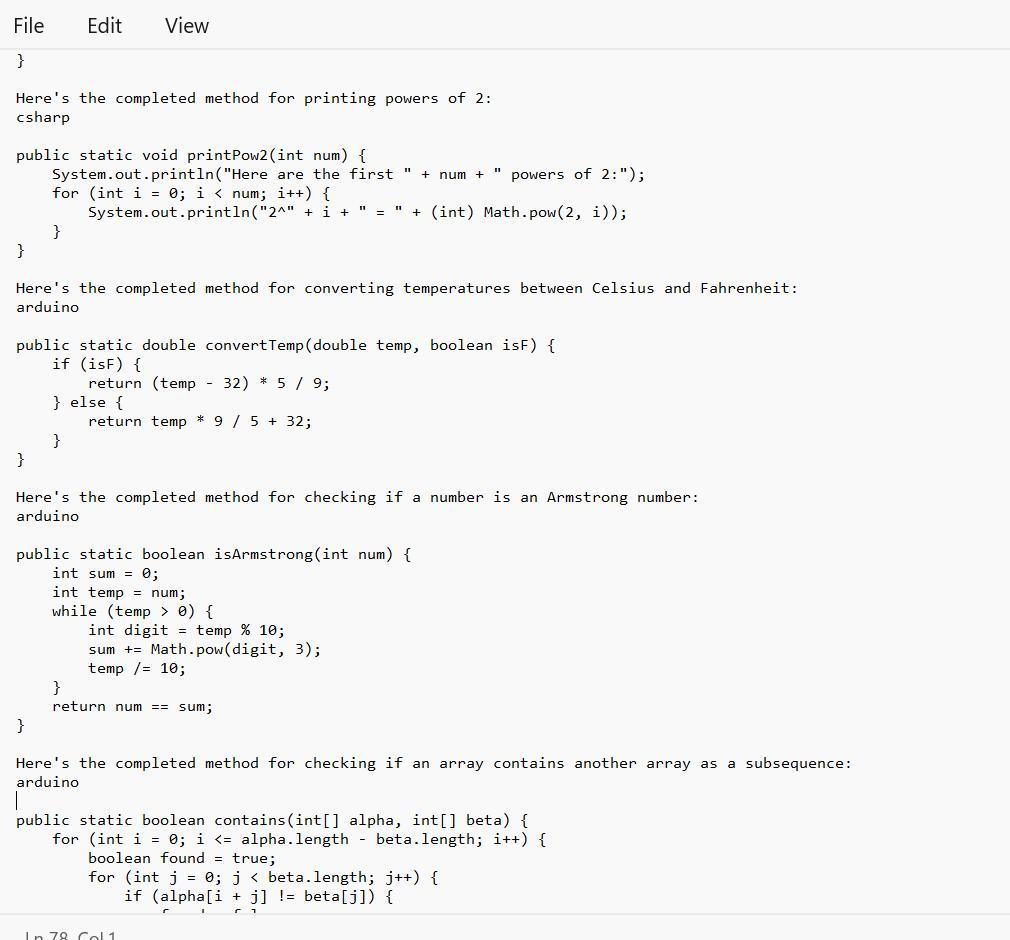
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


Create a program that ask the user to enter the number of switches and calculates the
possible outcomes that can come from those many number of switches (on / off).
Follow the steps given below to achieve the desired result:
● Step 1: Get the number of switches from the user and store it in a variable (lets
say switches).
● Step 2: Initialize 3 variables max_poss = 2, i = 1 and power = 1, where,
○ max_poss = 2 denotes the maximum possibile outcome of 1 switch (i.e. on
and off),
○ i is used to set the condition in while loop and it will keep incrementing
unless all the switches are over.
○ power variable is further used to store the result.
● Step 3: Define a while loop with a condition to execute till the value of i is less
than or equal to switches.
● Step 4: Inside the while loop,
○ Multiply the value stored in max_poss with power and store the result in
power.
○ Increment the value of i by 1.
For eg: When switches = 2, In the
1st iteration, power = 2 and in the 2nd iteration, power = 2 * 2 i.e. 4. This indicates that, the
number of possible outcomes = 2switches, where switches denotes the number of
switches.
● Step 5: Print the total number of possible outcomes stored in variable power.
plss help me with this
Answers
In python:
switches = int(input("How many switches? "))
max_pos = 2
power = 1
i = 1
while i < switches:
power = max_pos * power
i += 1
print(f"The total number of outcomes is {power}")
I hope this helps!
Give 3 reasons why it is believed that smart phones precent us from communicating face to face.give three reasons why it is believed that smartphones prevent us from communicating face to face
Answers
Answer:
yes
Explanation:
because the people will be lazy to go and talk to that person instead They will call each other and discuss
Vincent is attempting to remotely log into the system using openssh without success. he asks you what he can do to troubleshoot this problem. what should you recommend first?
Answers
In the case above, the command that i need to recommend first is option B. Add the -vvv option on to Vincent's ssh command.
What is SSH command?The Secure Shell (SSH) Protocol is known to be one that allows a user to be able to link up to a remotely located computer from the use of a single computer.
Note that this communication is one that often occurs via a secured encryption process. This kind of connection is one that is often used in file transfer and giving other remote commands.
Note that option B. is one that can enlist Vincent's help, and it is also one that can help him to be able to add the -vvv option on to his ssh command. This will help to give a great amount of information that will assist the person to you track down the issue.
Therefore, In the case above, the command that i need to recommend first is option B. Add the -vvv option on to Vincent's ssh command.
Learn more about open ssh from
https://brainly.com/question/17352088
#SPJ1
Choose the words that complete the sentences.
A_______
is used to edit raster images.
A_______
is used to edit vector images.
A_______
is used to control a scanner or digital camera.
Answers
Answer:
A paint application
is used to edit raster images.
A drawing application
is used to edit vector images.
A digitizing application
is used to control a scanner or digital camera.
Explanation:
got it right on edg
plants absorb water through root hairs.How do you think this water is used by the plants?
Answers
Harriet needs to move an 85-pound laser printer off of a table to get to a UPS. She should:
A. Use a hand truck.
B. Lift with her knees.
C. Get help to move it.
D. Call her supervisor.
Answers
Harriet should get help to move the 85-pound laser printer off of the table . Therefore, option (C) is correct.
If the lifting of big objects is not done correctly, it might result in serious injuries. It's possible that using a hand truck or lifting on her knees won't be enough to keep her from getting hurt.
In order to avoid harm during lifting, it is essential to employ safe lifting techniques and to ask for assistance when necessary. Therefore, Harriet should get help to move the 85-pound laser printer off of the table .
Learn more about laser printer, here:
https://brainly.com/question/29619585
#SPJ1
In the video game Animal Crossing: New Horizons, villagers are organized by Personality and Hobby.
The 8 Personalities are:
Normal
Lazy
Sisterly
Snooty
Cranky
Jock
Peppy
Smug
The 6 Hobbies are:
Education
Fashion
Fitness
Music
Nature
Playing
Create a program that allows the user to create their own Animal Crossing villager. The user should be able to enter a name, after which the program will choose a random Hobby and Personality for the villager:
"Please enter a Villager Name:
>> Betsy
Betsy is Snooty and into Nature"
The program should store both the Hobbies and Personalities in lists, and when creating a villager it should randomly choose from each list for the personality.
Requirements:
· Both Personalities and Hobbies must be stored in lists
· You must generate a different random number to determine the hobby and personality (that is, don't generate 1 random number and use it for both lists, as that prevents many combinations)
· In randomizing, you should make sure that all combinations are possible (that is, make sure you don't accidentally leave out a personality or hobby from random generation)
· The program shouldn't crash
Answers
The video game program is an illustration of randomization and lists
Randomization involves generating random numbers or selecting random optionsLists are variables that hold multiple valuesThe video game programThe video game program written in Python, where comments are used to explain each action is as follows:
#This imports the random package
import random
#This creates a list for personalities
Personality = ["Normal","Lazy","Sisterly","Snooty","Cranky","Jock","Peppy","Smug"]
#This creates a list for hobbies
Hobbies = ["Education","Fashion","Fitness","Music","Nature","Playing"]
#This gets input for name
name = input("Please enter a Villager Name: ")
#This generates a random number for personality
personalityNum = random.randint(0, 7)
#This generates a random number for hobbies
hobbiesNum = random.randint(0, 5)
#This prints the the required output
print(name,"is",Personality[personalityNum],"and into",Hobbies[hobbiesNum])
Read more about Python programs at:
https://brainly.com/question/16397886
Why do politically-powerful groups get bigger positive impacts of externalities?
- 1. GOVERNMENT CORRECTION FAVORS THEM
- 2. MORE POWERFUL GROUPS BECAME POWERFUL BECAUSE OF THESE EXTERNALITIES
- 3. BECAUSE OF CORRUPTION AND BRIBERY
- 4. BECAUSE THE POSITIVE IMPACTS ALWAYS OUTWEIGH THE NEGATIVE TO EVERYONE ELSE
Answers
There are a few reasons why politically-powerful groups get bigger positive impacts of externalities. One reason is that government correction favors them. Another reason is that more powerful groups became powerful because of these externalities.
What is government?
An organised community is governed by a system or group of people, typically a state. Government typically consists of the legislative, executive, and judicial branches in the case of its broad associative definition. Government is a mechanism for making policy decisions as well as a way to enforce organisational policies. A declaration of the government's guiding principles and philosophy is the equivalent of a kind of constitution in many nations. The term "government" is frequently used more specifically to refer to the roughly 200 independent national governments as well as subsidiary organisations, even though all organisations have governance. Modern democracies, monarchies, as well as authoritarian as well as totalitarian regimes are the main varieties of political systems.
Yet another reason is because of corruption and bribery. Finally, because the positive impacts always outweigh the negative to everyone else.
To learn more about government
https://brainly.com/question/1078669
#SPJ1
Calvin needs to design a simple yet professional interface for his users. Which option should he implement?
Answers
Answer:
switchboard
Explanation:
The option that he should implement would be a switchboard interface design. These design structures for graphic user interfaces use a single main page, large icons/buttons, a fixed navigation menu, and all the necessary functionality right in front of the user. This design is made with simplicity in mind in order to make it as easy as possible for a new user to pick up and efficiently and intuitively navigate the user interface. Therefore, since Calvin needs a simple yet professional design, this would be the best implementation.
Answer:
switchboards is the correct answer
Explanation:
just did the test
When designing a laptop, which three things should designers think about?
A. The balance between space, cost, and speed when processing
data
B. How increasing the computer's speed increases its power
consumption
C. Whether the laptop is going to be sold in stores or online
D. Whether to include a hard drive with greater storage capacity
Answers
Answer: A
Explanation:
nit 3 Quiz
Deshawn wants to buy a Chromebook that includes the Chrome OS because it is cheaper and has more freedom from software contracts and
icenses. Since it is an open-source software, where will he MOST LIKELY get technical support when he needs it?
OA
online communities that offer free or paid support
OB. the instruction manual that comes with the OS
OC. there is no assistance since it is an open-source software
OD. the company's 24/7 help line
Reset
Next
Answers
Since it is an open-source software, Deshawn would most likely get technical support when he needs it through the following medium: A. online communities that offer free or paid support.
What are the types of software license?In Computer technology, there are four (4) main types of software programs based on usage rights and these include the following:
Freeware softwarePurchased licenseShareware softwareOpen source softwareWhat is an open source software?In Computer technology, an open source software can be defined as a terminology which is used to describe a type of software that all end users can use and adapt it for any purpose or modify it for free without paying any license fee (money).
In conclusion, some technical support for an open source software can be gotten through online communities.
Read more on software here: brainly.com/question/25703767
#SPJ1
The traffic department is trying out a new system of traffic lights based on a busy vs. quiet intersection traffic model. we have to design a digital circuit which operates this new type of traffic light. traffic states for busy times red green red yellow red red green red yellow red red red traffic states for quiet times red green red yellow green red yellow red there are six lights to operate. the red, yellow, and green lights in the north-south direction will be designated as r1, y1, g1. similarly, the lights in the east-west direction will be called r2, y2, and g2. when the digital signals are 1 they turn their respective lights on, otherwise the lights are off. an additional input signal will designate whether it is a busy or quiet time. a digital clock signal will be supplied and at each clock pulse the lights should change according to the schedule given. the design of the circuit that produces the clock pulses at appropriate times will not be considered here. looking at the original specification, we see that there are 6 states (light patterns) for the busy period and 4 states for the quiet period . two states (3 and 6) have exactly the same traffic light outputs. could they be merged as one state
Answers
Yes, one can say that the states 3 and 6, which have the same traffic light outputs, can be merged into a single state.
What is the traffic lights?It is possible to combine states 3 and 6 into one state as they share identical outputs for traffic lights. Given that they generate identical light patterns, it is unnecessary to allocate distinct entities for them in the digital circuit layout.
Using the finite state machine (FSM) technique would be an effective means to create a digital circuit for the novel traffic signal in accordance with the provided requirements. The FSM will consist of a pair of states, one to signify busy times and another for calm periods.
Learn more about traffic lights from
https://brainly.com/question/10786180
#SPJ4
Given two objects represented by the tuples (22, 1, 42, 10) and (20, 0, 36, 8):
(a) compute the euclidean distance between the two objects.
(b) compute the manhattan distance between the two objects.
(c) compute the minkowski distance between the two objects, using q = 3.
(d) compute the supremum distance between the two objects.
Answers
Answer:
Given,
P = (22, 1, 42, 10)
Q = (20, 0, 36, 8)
a. Formula for Euclidean Distance :
distance = ((p1-q1)^2 + (p2-q2)^2 + ... + (pn-qn)^2)^(1/2)
Now,
distance = ( (22-20)^2 + (1-0)^2 + (42 - 36)^2 + (10-8)^2) ) ^(1/2)
=( (2)^2 + (1)^2 + (6)^2 + (2)^2 ) ) ^(1/2)
=(4+1+36+4)^(1/2)
=45^(1/2)
Distance = 6.7082
b.Manhattan distance :
d = |x1 - x2| + |y1 - y2|
d = |22- 20| + |1 - 0|
d = |2| + |1|
Explanation: