An example of a document that cannot be created with word processing software is:
A. A resume
B. A slide show
C. A report
D. A business letter
Answers
Answer: The actual answer is B. a slide show.
Explanation: I honestly didn't know this one either, but I just tried A. a resume, and the quiz then told me that it was B. a slide show.
So yes, it's B. a slide show.
An example of a document that cannot be created with word processing software is slide show.
What is word processing software?Word Processing is known to be the way one uses to make, edit, save and also print documents through the use of a computer.
Note that An example of a document that cannot be created with word processing software is slide show as that is the work of a presentation software.
Learn more about word processing from
https://brainly.com/question/985406
#SPJ2
Related Questions
An internet download speed is 4.2 MB/S (constant). How long will it take to download a 30 GB file?
And with 900 KB/S?
Answers
Answer:
(a) \(Time= 119.05 \ min\)
(b) \(Time= 9.26\ hr\)
Explanation:
Given
\(File = 30GB\)
Required
Download time
Solving (a): When Speed =4.2Mb/s
Speed is calculated as:
\(Speed = \frac{File\ Size}{Time}\)
Make Time the subject:
\(Time= \frac{File\ Size}{Speed }\)
Substitute values for File Size and Speed
\(Time= \frac{30Gb}{4.2Mb/s}\)
Convert Gb to Mb
\(Time= \frac{30*1000Mb}{4.2Mb/s}\)
\(Time= \frac{30000s}{4.2}\)
Convert to minutes
\(Time= \frac{30000}{4.2*60}\ min\)
\(Time= \frac{30000}{252}\ min\)
\(Time= 119.05 \ min\)
When converted, it is approximately 2 hours
Solving (a): When Speed =900Kb/s
\(Time= \frac{File\ Size}{Speed }\)
Substitute values for File Size and Speed
\(Time= \frac{30Gb}{900Kb/s}\)
Convert Gb to Kb
\(Time= \frac{30*1000000Kb}{900Kb/s}\)
\(Time= \frac{30*1000000s}{900}\)
\(Time= \frac{1000000s}{30}\)
\(Time= \frac{100000}{3}s\)
Convert to hours
\(Time= \frac{100000}{3*3600}hr\)
\(Time= \frac{1000}{3*36}hr\)
\(Time= \frac{1000}{108}hr\)
\(Time= 9.26\ hr\)
Answer:
(a)
(b)
Explanation:
Given
Required
Download time
Solving (a): When Speed =4.2Mb/s
Speed is calculated as:
Make Time the subject:
Substitute values for File Size and Speed
Convert Gb to Mb
Convert to minutes
When converted, it is approximately 2 hours
Solving (a): When Speed =900Kb/s
Substitute values for File Size and Speed
Convert Gb to Kb
Convert to hours
Which part of the Result block should you evaluate to determine the needs met rating for that result
Answers
To know the "Needs Met" rating for a specific result in the Result block, you should evaluate the metadata section of that result.
What is the Result blockThe assessment of the metadata section is necessary to determine the rating of "Needs Met" for a particular outcome listed in the Result block.
The metadata includes a field called needs_met, which evaluates the level of satisfaction with the result in terms of meeting the user's requirements. The needs_met category usually has a score between zero and ten, with ten implying that the outcome entirely fulfills the user's demands.
Learn more about Result block from
https://brainly.com/question/14510310
#SPJ1
When is using the Transmission Control Protocol (TCP) most appropriate?
Answers
Answer:
TCP is typically used when you need a connection-oriented, reliable communication channel.
Most internet protocols (like HTTP, POP, MQTT, ...) have TCP as their underlying protocol.
Only when speed is important and it is acceptable to lose some of the data, you would consider simpler protocols like UDP.
five real world objects with similar characteristics
Answers
Our current scientific knowledge in areas such as human visual perception, attention, and memory, is founded almost exclusively on experiments that rely upon 2D image presentations. However, the human visuomotor system has largely evolved to perceive and interact with real objects and environments, not images (Gibson, 1979; Norman, 2002).
Drag each label to the correct location on the table.
Match the correct features to virtualization and cloud computing.
allows multiple operating systems
to run on a single machine
consolidates hardware devices into
a physical server
allows users to access data from anywhere
includes services such as platform
as a service and desktop as a service
uses a hypervisor that can be type 1 or type 2
allows users to run software applications
on web browsers without installing
the application locally
Answers
Match the correct features to virtualization and cloud computing is allows multiple operating systems to consolidates hardware and uses a hypervisor to allows users to access
Divide the statement in virtualization and cloud computing ?
sing virtualization, different operating systems can operate on a single machine using a type 1 or type 2 hypervisor.
Users can access data from anywhere using cloud computing, which combines hardware devices into a physical server and offers services like platform as a service and desktop as a service. Users can execute software applications on web browsers without having to install them locally.
Know more about virtualization Visit:
brainly.com/question/31037702
#SPJ1
If the decimal value is 45, binary value is
Answers
The binary representation of the decimal 45 is 101101.
Features of database software
Answers
features
-stores data in one central location.
-allows data to be shared by many users.
-provides user interfaces to work with the data.
-creates backups.
-controls who can access and edit the data.
What will be the result from running the following program? print grades print 92 print 80print total print 92+80
Answers
Answer:
Grades
92
80
Total
92 + 80
Explanation:
When utilizing quotations, you enable to code to print what wrote, as it is. So, instead of adding the 92 + 80, it's printed out.
I hope this helped!
Good luck <3
9. In a 208-volt Y-connected system, what is the voltage drop between any phase wire and the grounded
neutral center tap of the windings?
A. 262 VAC
B. 180 VAC
C. 120 VAC
D. 240 VAC
Answers
How to send and receive same bits with the SDR in simulink????????
Answers
Answer:
SI QUERÉS SALIMOS
Como te amo te adoro
by using the Communications Toolbox
In C#
Please as soon as possible

Answers
Answer:
I'm not hundred percent sure but I believe it is going up by 100 the scale each number for the total quantity
Explanation:
Which of the following best explains how data is typically assembled in packets for transmission over the Internet?a. Each packet contains data to be transmitted, along with metadata containing information used for routing the data. b.Each packet contains an encrypted version of the data to be transmitted, along with metadata containing the key needed to decrypt the data. c.Each packet contains only the metadata used to establish a direct connection so that the data can be transmitted. d.Each packet contains multiple data files bundled together, along with metadata describing how to categorize each data file
Answers
This statement best explains how data is typically assembled in packets for transmission over the Internet is a. Each packet contains data to be transmitted as well as metadata containing information used for data routing.
What is Packet in data transmission?
In data transmission, a packet is a unit of data that is transmitted over a network. It consists of a header, which contains information about the packet, such as the source and destination addresses, and a payload, which contains the actual data being transmitted.
Packets are used to ensure that data is transmitted efficiently and reliably, as they can be broken down and transmitted individually, and can be reassembled at the receiving end.
To learn more about Packet, visit: https://brainly.com/question/13818790?referrer=searchResults
#SPJ1
I really need help with CSC 137 ASAP!!! but it's Due: Wednesday, April 12, 2023, 12:00 AM
Questions for chapter 8: EX8.1, EX8.4, EX8.6, EX8.7, EX8.8



Answers
The response to the following prompts on programming in relation to array objects and codes are given below.
What is the solution to the above prompts?A)
Valid declarations that instantiate an array object are:
boolean completed[J] = {true, true, false, false};
This declaration creates a boolean array named "completed" of length 4 with initial values {true, true, false, false}.
int powersOfTwo[] = {1, 2, 4, 8, 16, 32, 64, 128};
This declaration creates an integer array named "powersOfTwo" of length 8 with initial values {1, 2, 4, 8, 16, 32, 64, 128}.
char[] vowels = new char[5];
This declaration creates a character array named "vowels" of length 5 with default initial values (null for char).
float[] tLength = new float[100];
This declaration creates a float array named "tLength" of length 100 with default initial values (0.0f for float).
String[] names = new String[]{"Sam", "Frodo", "Merry"};
This declaration creates a String array named "names" of length 3 with initial values {"Sam", "Frodo", "Merry"}.
char[] vowels = {'a', 'e', 'i', 'o', 'u'};
This declaration creates a character array named "vowels" of length 5 with initial values {'a', 'e', 'i', 'o', 'u'}.
double[] standardDeviation = new double[1];
This declaration creates a double array named "standardDeviation" of length 1 with default initial value (0.0 for double).
In summary, arrays are objects in Java that store a fixed-size sequential collection of elements of the same type. The syntax for creating an array includes the type of the elements, the name of the array, and the number of elements to be stored in the array. An array can be initialized using curly braces ({}) to specify the initial values of the elements.
B) The problem with the code is that the loop condition in the for loop is incorrect. The index should start from 0 instead of 1, and the loop should run until index < masses.length instead of masses.length + 1. Also, the totalMass should be incremented by masses[index], not assigned to it.
Corrected code:
double[] masses = {123.6, 34.2, 765.87, 987.43, 90, 321, 5};
double totalMass = 0;
for (int index = 0; index < masses.length; index++) {
totalMass += masses[index];
}
The modifications made here are to correct the starting index of the loop, fix the loop condition, and increment the totalMass variable correctly.
C)
1)
Code to set each element of an array called nums to the value of the constant INITIAL:
const int INITIAL = 10; // or any other desired initial value
int nums[5]; // assuming nums is an array of size 5
for (int i = 0; i < 5; i++) {
nums[i] = INITIAL;
}
2) Code to print the values stored in an array called names backwards:
string names[4] = {"John", "Jane", "Bob", "Alice"}; // assuming names is an array of size 4
for (int i = 3; i >= 0; i--) {
cout << names[i] << " ".
}
3) Code to set each element of a boolean array called flags to alternating values (true at index 0, false at index 1, true at index 2, etc.):
bool flags[6]; // assuming flags is an array of size 6
for (int i = 0; i < 6; i++) {
flags[i] = (i % 2 == 0);
}
Learn more about array objects at:
https://brainly.com/question/16968729
#SPJ1
What is the name for the strip of frequently used icons on a computer? O App O Program O Toolbar O Utilities panel ILL MARK YOU BRAINEST
Answers
Answer: The name of the strip is the Toolbar.
Answer:
its quite obvious toolbar
Explanation:
Write a program that reads a list of integers into a list as long as the integers are greater than zero, then outputs the smallest and largest integers in the list.
Ex: If the input is:
10
5
3
21
2
-6
the output is:
2 and 21
Answers
n = 1
lst = []
while n > 0:
lst.append(n := int(input()))
lst.pop(-1)
print(str(min(lst)) +" and "+str(max(lst)))
I wrote this code in python 3.8. I hope this helps
Many individuals and organizations are choosing cloud storage for their important files. Discuss the pros and cons of cloud storage for both personal files and business files. Many individuals and organizations are choosing cloud storage for their important files. Discuss the pros and cons of cloud storage for both personal files and business files. What inputs and outputs are needed to support the storage environment
Answers
Answer:
Pros of cloud storage
Files can be accessed remotely without having to be connected to a company's intranetSecurity and file backups are managed by the cloud storage company, frees up employees time applying updates and other maintenance tasks.Usually billed monthly which allows for a lower initial startup costCons of cloud storage
File security relies upon trust in the cloud storage providerLong term cost could be higher than storing files yourselfRequires an internet connection to access files1. Why is data the most important asset an organization possesses? What other assets in the organization require protection?
2. What are the various types of malware? How do worms differ from viruses? Do Trojan horses carry viruses or worms?
Answers
Here are the key points:
Why data is important:
- Data contains the intellectual capital and knowledge of an organization. It includes information about customers, business processes, operations, finances, etc. This data drives decision making and performance.
- Loss of data can significantly impact an organization's ability to operate effectively and achieve its goals. It can also damage reputation and trust.
Other assets to protect:
- Intellectual property like patents, trademarks, copyrights
- Physical assets like facilities, equipment, inventory
- Human capital like employees and their knowledge/skills
Types of malware:
- Viruses - Self-replicating programs that attach to other programs and spread when those programs are executed. They can corrupt or delete data.
- Worms - Self-replicating programs that spread over networks and consume network bandwidth. They do not require host programs to replicate.
- Trojan horses - Malware that masquerades as legitimate programs. They do not replicate like viruses/worms but once activated, can give an attacker access and control of the infected system.
Relationship between worms, viruses and Trojans:
- Worms and viruses differ in their replication techniques. Worms spread on their own while viruses need host programs.
- Trojan horses do not replicate like viruses or worms. They simply provide unauthorized access to a system. However, they are sometimes used to deliver viruses or worms upon execution.
PLEASE I NEED HELP ASAP!! WILL MARK BRAINILEST

Answers
Some examples of HTML tags you might observe in the source code of a web page:
<html>: Represents the root element of an HTML document.<head>: Contains metadata and other non-visible information about the web page.<title>: Specifies the title of the web page that appears in the browser's title bar or tab.What is the act of using the tags?The tag serves as the fundamental element for an HTML file. This tag envelops all the remaining components of the webpage.
The element holds important information about the webpage such as metadata and other details that are not visible to the user. One of the components found in web pages is the <title> tag, which indicates the webpage's title.
The <title> element identifies the webpage's title. The information displayed in the title bar or tab of a browser is commonly utilized to offer a concise summary of the webpage's content.
Learn more about Web Page from
https://brainly.com/question/28431103
#SPJ1
Creating a Web Page Using HTML: Tutorial
An HTML File
This activity will help you meet these educational goals:
8 of 25
Save &
• Content Standards-You will perform an Investigation, in which you will make observations and communicate your results in written form. Inquiry-You will perform an Investigation, in which you will make observations and communicate your results in written form.
⚫ 21st Century Skills-You will use critical thinking and problem solving skills.
Directions
Read the instructions for this self-checked activity. Type in your response to each question, and check your answers. At the end of the activity, write a brief evaluation of your work.
Activity
Visit the About Us page of Edmentum's web site. Once the web page loads, view the source HTML file by right-clicking on the page and choosing View Source (in Internet Explorer) or View Page Source (in Firefox or Chrome). If you use Safari, you have to click on Develop | Show Page Source. (If Develop is not visible, go to Preferences and tick Show Develop in the Advanced menu bar.)
Part A
Observe the HTML code. You will see many instances of text enclosed in angle brackets . These instances of text are HTML tags. List some of the HTML tags you see.
Write a program that will add up the series of numbers: 99, 98, 97… 3, 2, 1. The program should print the running total as well as the total at the end. The program should use one for loop, the range() function and one print() command.
Answers
Answer:
isum = 0
for i in range(99,0,-1):
isum = isum + i
print(isum)
Explanation:
This line initializes isum to 0
isum = 0
The following iteration starts from 99 and ends at 1
for i in range(99,0,-1):
This line adds the series
isum = isum + i
This line prints the sum of the series
print(isum)
The program that will add up the series of numbers: 99, 98, 97… 3, 2, 1 is represented as follows using for loop, the range() function and one print() function.
sum = 0
for i in range(1, 100):
sum += i
print(sum)
The code is written in python.
The variable sum is initialise to zero.
For loop is used to loop through the range of number 1 to 100(excluding 100).
Then the numbers are added to the sum initialised to zero.
The total sum is then printed.
learn more on python here: https://brainly.com/question/22164565?referrer=searchResults

what number am i. i am less than 10 i am not a multiple of 2 i am a coposite
Answers
Answer: 9 is less than 10, it is odd (not a multiple of 2), and it is composite (since it has factors other than 1 and itself, namely 3). Therefore, the answer is 9.
Radio station wxyz takes a random survey of 300 morning drive-time listeners. The station determines that 85% of those surveyed enjoy listening to music more than a talk show. What can the radio station conclude from the survey?.
Answers
Based on the survey results, the radio station can conclude that 255 out of the 300 morning drive-time listeners surveyed prefer listening to music over talk shows. This information can help the station determine what type of programming to focus on during the morning drive-time slot, in order to better meet the preferences of their audience. However, it is important to keep in mind that this is just a survey of 300 listeners, and may not accurately represent the preferences of the entire listener base. Further research and surveys may be necessary to get a more comprehensive understanding of listener preferences.
For questions 5-8, consider the following code:
def mystery(a = 2, b = 1, c = 3):
return 2 * a + b + 3 * c
What is the output for mystery(4, 3, 7)?
What is the output for mystery(5, 8)?
What is the output for mystery(1)?
What is the output for mystery()?
Answers
Answer:
les go, it has optional parameters so...
Explanation:
output of 1 is 32
second 27
third 12
fourth 14
4.1 lesson practice
Answers
what is document formatting?
Answers
Answer:
Document formatting refers to the process of designing and arranging the content, layout, style, and structure of a document to make it more readable, visually appealing, and professional-looking. Document formatting involves applying different formatting techniques such as setting margins, adding page numbers, adjusting font size and style, indenting paragraphs, adding headings and subheadings, using bullet points and numbered lists, and incorporating images, tables, and charts to enhance the presentation of the document.
Explanation:
What will be the different if the syringes and tube are filled with air instead of water?Explain your answer
Answers
Answer:
If the syringes and tubes are filled with air instead of water, the difference would be mainly due to the difference in the properties of air and water. Air is a compressible gas, while water is an incompressible liquid. This would result in a different behavior of the fluid when being pushed through the system.
When the syringe plunger is pushed to force air through the tube, the air molecules will begin to compress, decreasing the distance between them. This will cause an increase in pressure within the tube that can be measured using the pressure gauge. However, this pressure will not remain constant as the air continues to compress, making the measured pressure unreliable.
On the other hand, when the syringe plunger is pushed to force water through the tube, the water molecules will not compress. Therefore, the increase in pressure within the tube will be directly proportional to the force applied to the syringe plunger, resulting in an accurate measurement of pressure.
In summary, if the syringes and tube are filled with air instead of water, the difference would be that the measured pressure would not be reliable due to the compressibility of air.
Recall your technology experience in the workplace or at home. When adopting a new technology, what specific problems were you or your employer trying to resolve?
Describe your biggest challenge in adopting new technologies based on your experience.
Share how you or your employer overcame these issues.
Answers
Answer:
Use of technology helps solve issues like file management, receipt tracking, report generation and growth tracking that often hamper employee productivity. Modern workplaces extensively rely on computer-aided tools for efficiency. These tools help cut down both the time and money needed for getting the job done.
How do you implement new technology in the workplace?
To help you streamline the process, here are steps for integrating new technology into your organization:
Identify Your Organization's Needs.
Investigate Technologies That Will Solve Problems for Your Organization.
Develop a Plan for Implementing Your New Technology.
Train Other Employees in Using the New Technology
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
Which of the following best describes an insider attack on a network?
OA. an attack by someone who uses fake emails to gather information related to user credentials
OB. an attack by someone who becomes an intermediary between two communication devices in an organizatio
OC. an attack by a current or former employee who misuses access to an organization's network
O D. an attack by an employee who tricks coworkers into divulging critical information to compromise a network
Answers
An attack by a current or former employee who misuses access to an organization's network ca be an insider attack on a network. The correct option is C.
An insider attack on a network refers to an attack carried out by a person who has authorized access to an organization's network infrastructure, either as a current or former employee.
This individual intentionally misuses their access privileges to compromise the network's security or to cause harm to the organization.
Option C best describes an insider attack as it specifically mentions the misuse of network access by a current or former employee.
The other options mentioned (A, B, and D) describe different types of attacks, but they do not specifically involve an insider with authorized access to the network.
Thus, the correct option is C.
For more details regarding network, visit:
https://brainly.com/question/29350844
#SPJ1
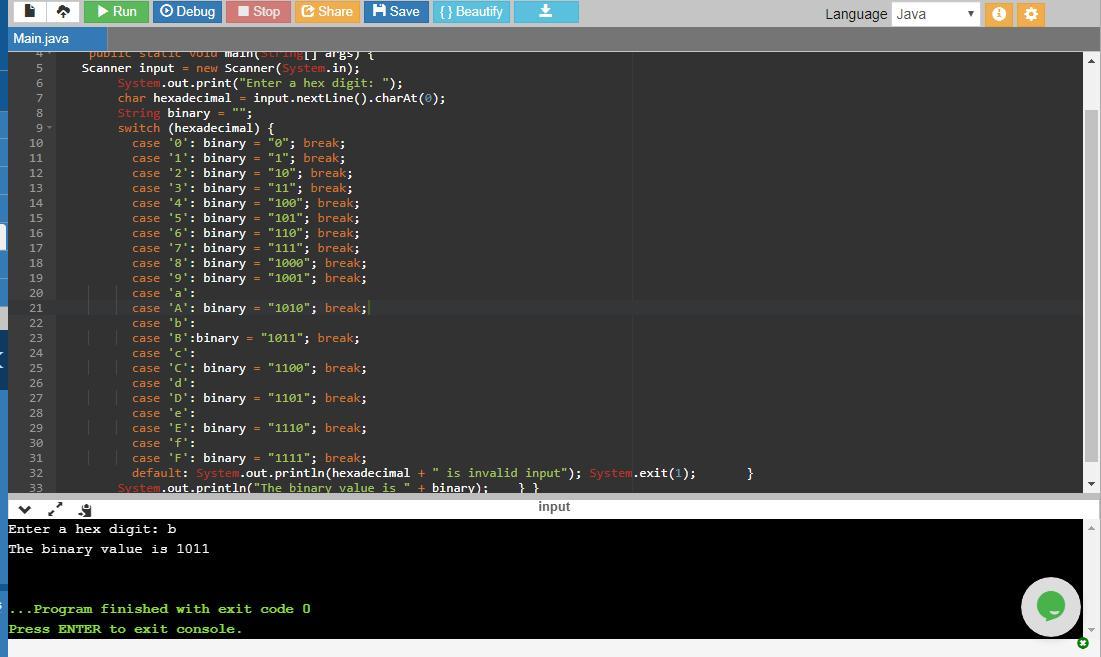
Write a program that prompts the user to enter a hex digit and displays its corresponding binary number. Sample Run 1 Enter a hex digit: B The binary value is 1011 Sample Run 2 Enter a hex digit: b The binary value is 1011 Sample Run 3 Enter a hex digit: T Invalid input
Answers
Answer:
I am writing a JAVA program. Let me know if you want the program in some other programming language.
import java.util.Scanner; //to take input from user
public class HexaToBinary{ //class to convert hexa to binary number
public static void main(String[] args) {// start of main() function body
//creates instance of Scanner class
Scanner input = new Scanner(System.in);
//prompts user to enter a hexadecimal number
System.out.print("Enter a hex digit: ");
char hexadecimal = input.nextLine().charAt(0);//reads input from user
String binary = ""; //variable to hold corresponding binary number
/*switch statement is used to convert hexadecimal input to corresponding binary number. the switch statement has cases. Each case has a hexa decimal number. The user's input is stored in hexadecimal variable which is given as a choice parameter to switch statement. If the input matches any of the cases in switch statement, the body of that case is executed which prints the corresponding binary number otherwise invalid input message is displayed in output */
switch (hexadecimal) {
case '0': binary = "0"; break;
case '1': binary = "1"; break;
case '2': binary = "10"; break;
case '3': binary = "11"; break;
case '4': binary = "100"; break;
case '5': binary = "101"; break;
case '6': binary = "110"; break;
case '7': binary = "111"; break;
case '8': binary = "1000"; break;
case '9': binary = "1001"; break;
//here both the upper and lower case letters are defined in case, so the user //can enter a hexadecimal in lowercase or uppercase
case 'a':
case 'A': binary = "1010"; break;
case 'b':
case 'B':binary = "1011"; break;
case 'c':
case 'C': binary = "1100"; break;
case 'd':
case 'D': binary = "1101"; break;
case 'e':
case 'E': binary = "1110"; break;
case 'f':
case 'F': binary = "1111"; break;
default: System.out.println(hexadecimal + " is invalid input"); System.exit(1); } //displays this message if user enters invalid input e.g T
System.out.println("The binary value is " + binary); } }
//prints the corresponding binary number of the hexadecimal input
Explanation:
The program is well explained in the comments mentioned with each line of the program. Lets take an example of user input.
For example if user enters b in input then the cases of the switch statement are searched for by the program to select the corresponding binary number of the input hexadecimal. So b is present in case 'b': case 'B':binary = "1011"; break; So the value of binary is 1011 and this value is displayed on the screen with this statement System.out.println("The binary value is " + binary); So the output is: The binary value is 1011
The screenshot of output and program are attached.
Select the correct answer from each drop-down menu.
Maria is preparing a slide show on procedural programming. She wants to define procedural programming in one of the slides. Help Maria complete
the definition.
Procedural-oriented programming is a programming paradigm that views a problem as a series of ____ to be performed in a _____ manner.
a series of (objects, tasks, statements)
to be preformed in a (sequential, random, logical)
Answers
Answer:
Procedural-oriented programming is a programming paradigm that views a problem as a series of tasks to be performed in a sequential manner. In procedural programming, a program is broken down into a series of steps or procedures that are executed in a particular order to achieve a desired outcome. Each procedure is designed to perform a specific task, and the program flows from one procedure to the next until the final task is completed. This approach to programming is often used for creating small to medium-sized programs and is known for its simplicity, modularity, and ease of debugging.
Explanation: