An attacker captures packets as they travel from one host to another with the intent of altering the contents of the packets. Which type of attack is being executed
Answers
An attacker captures packets as they travel from one host to another with the intent of altering the contents of the packets . The type of attack being executed is known as a "packet manipulation attack."
In a packet manipulation attack, an attacker intercepts network traffic between two hosts and modifies the content of the packets before allowing them to reach their intended destination. This attack aims to manipulate the data within the packets, potentially altering the information being transmitted or introducing malicious code or instructions.
Packet manipulation attacks can have severe consequences, as they can lead to data corruption, unauthorized access, or the injection of malware into the network. Attackers can modify various aspects of the packets, including the payload, headers, or routing information. By tampering with the packets, they may attempt to gain unauthorized access, perform man-in-the-middle attacks, or disrupt the communication between the two hosts.
To mitigate the risk of packet manipulation attacks, it is essential to implement security measures such as encryption, authentication, and integrity checks. Additionally, monitoring network traffic and using intrusion detection systems can help identify and prevent such attacks.
LEARN MORE ABOUT packets here: brainly.com/question/20038618
#SPJ11
Related Questions
please help thank u!!!!!

Answers
Answer:
i believe you can change slides with the arrow keys not entirely sure though
Explanation:
Answer:
using the arrows
pressing space
and clicking the mouse
Explanation:
Danielle wants to record a voice-over to add to a presentation. Other than a microphone, what does danielle need to record the audio?.
Answers
Answer:
Sound recorder software
Explanation:
A single computer on a network is called a____________.
Answers
Answer: A single computer on a network is called a node. pls brainliest
explain the look of a document which contains several different font sizes and font colors
Answers
Answer:
Colorful and dynamic?
Explanation:
The look of a document that has several different font sizes and font colors is one that has undergone editing to give it a kind of uniqueness.
What is name of the document?A document file name is said to be the name that is given to an electronic file copy of a document.
The document file name is one that can be written in different ways. The HTML style is known to be an element that is often used to add a lot of styles to an element, such as color, font of a document.
Learn more about document from
https://brainly.com/question/16650739
Beth wants to add information to her powerpoint presentation that is hidden from her audience and only she will see. which feature should she use? a. notes pane b. title slide c. normal view d. slide sorter view
Answers
For information that Beth wants to keep private from her audience and only see, she should add it to her PowerPoint presentation using the Notes pane.
Microsoft's PowerPoint presentation software enables users to design and deliver captivating presentations. It provides a selection of tools and features to assist users in producing presentations with a professional appearance using a range of material kinds, including text, photos, videos, and charts. PowerPoint is frequently used in a variety of contexts, including business meetings, academic lectures, and individual presentations, thanks to its user-friendly interface and customizable templates. In order to improve the presenting experience, it also provides elements like animations, transitions, and speaker notes. PowerPoint presentations can be given live, online, or via email, and they can be stored in a variety of file formats. Ultimately, PowerPoint is a flexible tool that may assist users in engaging their audience and effectively communicating ideas.
Learn more about PowerPoint here:
https://brainly.com/question/30038509
#SPJ4
This high-level programming language is similar to Java and useful for newer programmers.
HTML
Python
PHP
CSS
Answers
High-level programming languages like Python are frequently suggested for beginning programmers.
What level of programming language is CSS?The primary justification for why HTML and CSS aren't regarded as programming languages is that they solely affect the design of the webpage you're creating. In contrast to other front-end languages, they don't have any instructions. Python is an interpreted, object-oriented, high-level, dynamically semantic programming language.
Are Python and Java high-level languages?The two most used programming languages are Python and Java. Both languages are high-level, all-purpose, and widely utilized. Java is currently the programming language of choice for creating desktop and web apps.
To know more about Python visit:-
https://brainly.com/question/30427047
#SPJ1
Jill is interested in a career as a paramedic. She is trained to use medical equipment, she remains calm under pressure, and she has good bedside manner. Which career pathway would best fit Jill's interests and skills?
Answers
Answer:
Emergency and Fire management services
Explanation:
Paramedics are trained to respond to emergency situations faced by the public. These could include, fire incidents, accidents, or other emergency situations. Paramedics are trained to be calm under pressure, to use medical equipment, as well as to have good bedside manners as their jobs might require taking care of victims of various incidents at the spot of crisis, or in ambulances before they arrive the hospitals.
So, Jill is likely interested in a career in Emergency and Fire Management Services because she would require these skills to succeed in this field.
Answer:
Emergency and Fire management services
Explanation:
Do you think employers are impressed with someone who knows how to use Excel? Why or Why not?
Answers
Answer:
Explanation:
Yes, but it depends on who your applying your job for. If it's a computer based job than they will be impressed.
Each row in an Access table datasheet displays which of the following? A. a query. B. a record. C. a field. D. a data type.
Answers
The correct answer is B. Each row in an Access table datasheet displays a record. Records represent individual entries or instances in a table, containing specific data values organized into fields.
In Microsoft Access, and indeed in most relational databases, data is organized into tables composed of rows and columns. Each row, also known as a record or tuple, represents a single instance of the entity described by the table. Each column, on the other hand, is called a field, attribute, or property and corresponds to a particular piece of data within the record. So, in the context of a table datasheet, each row displays a complete record, with each cell in the row holding the value of a specific field for that record. Therefore, each row provides a complete set of related data for a specific instance or entity.
Learn more about data organization here:
https://brainly.com/question/14310152
#SPJ11
How does the Problem-solving Process help us to solve everyday Problems?
Answers
Answer:
Problem-solving gives us a mechanism for identifying these things, figuring out why they are broken and determining a course of action to fix them. Also Problem-solving helps us understand relationships and implement the changes and improvements needed to compete and survive in a continually changing environment.
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
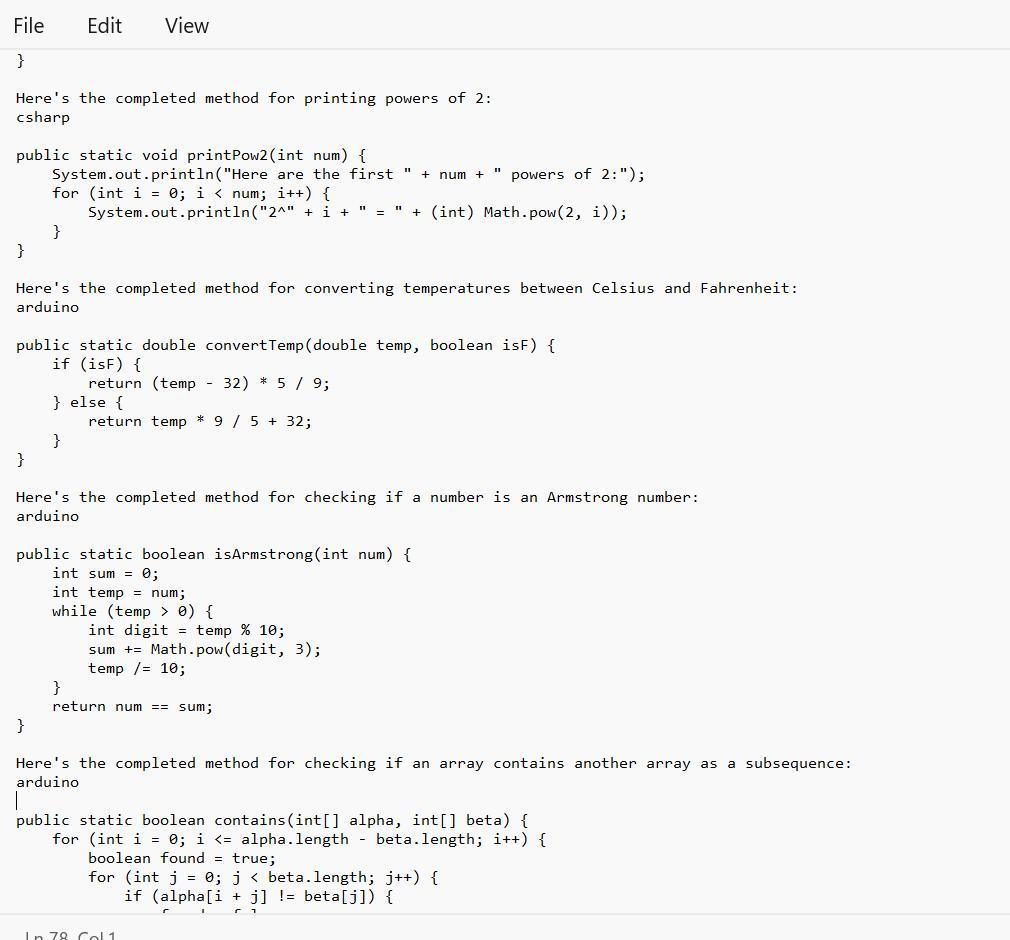
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


Given a 10-bit Binary Code determine the user or human input if bits in the 1st and 4th positions are on. 8. A user types the "Tilde - using QWERTY keyboard. Determine the machine language equivalent for the user input.
Answers
The machine language equivalent for the user input is 126.
1. The 10-bit binary code for the user input is 0100000111.
2. The 1st and 4th positions in the binary code are both on.
3. The machine language equivalent for the user input is 01111100.
1. The 10-bit binary code representation of the user input "Tilde" is 0100000111.
2. In binary, the positions are numbered from right to left, starting from 1. So, the 1st and 4th positions correspond to the bits in the binary code.
3. Both the 1st and 4th bits are on (1), indicating that the "Tilde" key was pressed.
4. The machine language equivalent for the user input "Tilde" is represented by the binary code 01111100. Machine language instructions vary depending on the specific system architecture and instruction set being used.
Learn more about binary code here:
https://brainly.com/question/29792509
#SPJ11
Write a code in python that guesses a hardcoded answer and keeps on asking the user until the user gets the answer correct. The cmputer should be telling the user if the number they are guessing is too low or too high.
Answers
import random
#You can change the range.
answer = random.randint(1,1000)
counter = 0
while(True):
guess = int(input("Make a guess: "))
message = "Too high!" if guess>answer else "Too low!" if guess<answer else "You won!"
print(message)
if(message=="You won!"):
print("It took",counter,"times.")
break
else:
counter+=1

What is the system of computers, routers, wires, cables,etc. that allow computers to communicate called?
Answers
Not 100% sure though
Ignore this it a temporary note for me: SPSstudents
Answers
Answer:
okk
Explanation:
which computer is used in hospital for ultrasound?
Answers
Answer:
Pentium Powered Computer
Explanation:
Pentium powered computer
A ______ lookup table has data organized into columns.
Answers
A Vertical lookup table has data organized into columns. In computer science, a lookup table (LUT) is an array that replaces run-time computations with simpler array indexing operations.
This process is called "direct addressing", a LUT is different from a hash table, a hash table that takes a value v with key k stores the value v in slot h(k). where h is the hash function. that is k. is used to compute the slot, but in the case of the LUT the value v is stored in slot k and can be addressed directly. :
466 Saving processing time is important because retrieving a value from memory is often faster than performing an "expensive" computation or I/O operation.
Tables can be precomputed and stored in static program memory, computed (or "prefetched") as part of the initialization (memorization) phase of the program, or stored in the hardware of an application-specific platform.
Lookup tables are also commonly used to validate input values against a list of valid (or invalid) elements in an array. Some programming languages may include pointer functions (or offsets to labels) to handle matched input. FPGAs also make extensive use of hardware-implemented reconfigurable lookup tables to provide programmable hardware functionality.
Know more about lookup table here:
https://brainly.com/question/22603459
#SPJ4
what is a characteristic of hash structure in a key-value database?
Answers
A characteristic of hash structure in a key-value database is the ability to efficiently store and retrieve data. Hashing is a process of converting a key into a unique index that represents the location of the corresponding value in the database. This means that when a key is used to retrieve data, the hash function can quickly calculate the index where the value is stored, without having to search through the entire database.
One advantage of hash structures in key-value databases is their ability to handle large amounts of data. Hashing ensures that data can be quickly accessed and processed, even in databases with millions or billions of entries. Additionally, hash structures support fast insertions and deletions, since the hash function can quickly calculate the new location of the value being inserted or deleted.
Another characteristic of hash structures in key-value databases is their ability to handle collisions. Collisions occur when two or more keys map to the same index in the hash table. To handle collisions, hash structures use collision resolution techniques such as chaining or open addressing. Chaining involves creating a linked list at each index in the hash table, while open addressing involves probing for the next available slot when a collision occurs.
In summary, hash structures in key-value databases provide efficient storage and retrieval of data, can handle large amounts of data, and provide collision resolution techniques for handling collisions.
To know more about hash structure visit:
https://brainly.com/question/30790467
#SPJ11
Why do cooler substances have a tendency to sink?
Answers
Answer:
Explanation:
the molecules to slow down and they get closer to together.
:)
Convection happens in fluids (liquids & gases). The heat energy moves through the material as the particles in the material move through the material.
Hot liquids and gases rise because when they are heated they expand and become less dense. The less dense warm liquid or gas then floats up through the more dense cold liquids and gases.
Cold liquids and gases sink because when cooled they contract and become more dense. The more dense cold liquids and gases sink down through the less dense warm liquids and gases.
These changes in density cause the convection currents in the liquid or gas.

have you gone/done into things that you forget to close/settle?
Answers
Answer: AT SOME CIRCUMSTANCES YES
Explanation: WELL ONE EXAMPLE WAS OUR GAMING GROUP WHICH WAS MADE OF ABOUT 2 YEARS AGO AND THERE ARE STILL TO PEOPLE IN THE GROUP WHEN WE DON'T EVEN USE ANYMORE , CAN YOU BELIEVE IT ?
Miss Tanaka regularly runs review sessions for her students before exams, as her students forget what topics have been covered and where they can access the resources used in class. How should she use Blogger effectively to reduce the amount of review sessions she needs to run? She can embed a Sheet containing the class topics and links to resources, and update it after each class. She can create a video giving students a quick overview of the semester, and upload it to Blogger at the end of the semester. She can upload all her lesson plans and notes into the File Cabinet in Blogger so students can only access them at school. She can create a new blog post after every class with the lesson overview, notes and links to resources.
Answers
Answer:
She can create a new blog post after every class with the lesson overview, notes and links to resources.
Explanation:
In order to help her students out, Miss Tanaka can simply create a blog post after every class - her students will know to expect it every week and can easily locate it whenever they need it. This way, Miss Tanaka will also avoid having to repeat the same lesson over and over again if the students can find the summaries themselves and read whenever they want. These blogs will be found on the main page so everything is neat and well-organized.
She can create a new blog post after every class with the lesson overview, notes and links to resources.
What is a blog?A blog is an online platform that allows an an individual, group or industry presents a record of their activities, teachings or beliefs.
An individual can login to a blog website and can view all the activities or event posted.
Therefore, Mrs Tanaka can create a new blog post after every class with the lesson overview, notes and links to resources.
Learn more on links to resources here,
https://brainly.com/question/16595058
besides protecting a computer from under-voltages, a typical ups also performs which other actions?(select two.)
Answers
The other actions a typical ups performs, besides protecting a computer from low voltages, is:
Protects from over-voltagesConditions the power signalIn addition to protecting a computer from low voltages, a typical Uninterruptible Power Supply (UPS) can also protect against over-voltages, brownouts, blackouts, and power surges. It also conditions the power signal by filtering out any noise or spikes in the power signal before it reaches the computer.
The UPS also helps to provide a consistent stream of clean power to the computer, which can help to improve its performance and reliability.
Learn more about computers:
https://brainly.com/question/24540334
#SPJ4
Besides protecting a computer from under- voltages, a typical UPS also performs which two actions? (Select two.)
A. Prevents electric shock
B. Prevents ESD
C. Protects from over-voltages
D. Conditions the power signal
E. Protects network cabling from EMI
will give brainliest
Which of the following best characterizes how Evan, a computer programmer, might
benefit with regard to upward mobility?
Computer programmers can become highly specialized.
Computer programmers consistently reach the top of their field.
Computer programmers may advance as project leaders or software developers.
Computer programmers typically start in entry-level positions.
Answers
Answer:
Computer programmers may advance as project leaders or software developers.
Order the steps to record a macro in word

Answers
Answer:
Select record Marco...
Explanation:
because
You’ve been stuck in bumper-to-bumper traffic for nearly an hour on a hot summer day. The temperature warning light has just come on. How will you handle this situation? What safety precautions will you take?
Answers
Answer:
In a bumper-to-bumper traffic, when the engine starts overheating the situation can be handled by tapping the accelator which will revive the engine.
Explanation:
Overheating of engine can be due to many reasons. But one should know what to do when an engine overheats in a traffic. Bumper-to-bumper traffic is when the cars are so close in traffic that they touch each other. This usually happens when there's a traffic for a long time or on very busy lane. During summer times, it is important to keep checking the engine temperature to avoid any problem.
When one is stuck in bumper-to-bumper traffic with overheating engine, then there are some meausres that one can take. They are:
To put the car on park or neutral mode of driving and tap the accelator which will revive the engine. The heat can be disperse by rolling down the window and turn the heater up. It will disperse the heat.true or false? structured query language (sql) is a front-end, object-oriented interface for databases
Answers
The statement is false. A database's front-end, object-oriented interface is called Structured Query Language (SQL). Finding patterns and links in vast amounts of detailed data is a process known as data mining.
Designed for managing data stored in a relational database management system, SQL is a database language. IBM created SQL for the first time in the early 1970s (Date 1986). The original SEQUEL (Structured English Query Language) version was created to access and manipulate data held in IBM's System R quasi-relational database management system. The first SQL implementation to be made commercially available was Oracle V2, which was released for VAX computers in the late 1970s by Relational Software Inc., later to become Oracle Corporation.
Learn more about database here-
https://brainly.com/question/14885760
#SPJ4
which is known as accurate processing of computer
Answers
Answer:
GIGO is the considered as the accurate processing in computers. In the field of computer science, the word GIGO stands for " garbage in, garbage out". It is a concept that refers that if bad input is provided to the computers, the output will also be bad and useless. It is the inability of the program to any bad data providing incorrect results.
Explanation:
Hey i need some help with code.org practice. I was doing a code for finding the mean median and range. the code is supposed to be including a conditional , parameter and loop. I'm suppose to make a library out of it and then use the library to test the code? please help!
here is the link to the code.
https://studio.code.org/projects/applab/YGZyNfVPTnCullQsVFijy6blqJPMBOgh5tQ5osNhq5c
P.S. you cant just type on the link i shared you have to click view code and then remix to edit it. thanks
Answers
Answer:
https://studio.code.org/projects/applab/YGZyNfVPTnCullQsVfijy6blqJPMBOgh5tQ5osNhq5c
Explanation:
Discuss the idea of managing users by group membership. How does this help you manage network resources. (250 words)
Answers
The management of users through group membership refers to the creation of groups in the directory that manage access permissions to a specific network resource. This is a type of user management that enables administrators to make a large number of changes quickly to the permissions granted to various groups of users.
It simplifies management by grouping together users with similar roles or requirements, as well as provides better control over access to network resources.The idea of managing users through group membership helps to manage network resources in a number of ways, including:
1. Improved security: Groups permit administrators to apply access controls in a granular manner to specific users and system resources. Administrators may give read-only access, for example, to some resources while granting complete access to other resources to groups that require it.
2. Efficient allocation of resources: Network resources can be a limited resource, hence, the creation of groups enables the efficient allocation of resources, in that, resources are assigned to only those users that need it.
3. Reduced management complexity: As the number of users increases, it becomes increasingly difficult for administrators to manually assign privileges to each user. However, with the creation of groups, administrators can manage users and their permissions more efficiently. Administrators can add or delete users from groups quickly and easily and thereby ensure that permissions are consistent across users.
4. Compliance: Security compliance regulations require organizations to maintain strict controls over user access to network resources. With the help of groups, administrators can keep a better control over user access and permissions, and ensure that the organization's security requirements are met.
In conclusion, group membership offers a way to better manage users and network resources. It simplifies management, improves security, allows for efficient allocation of resources and ensures compliance with security regulations.
To know more about specific network resource.visit:
https://brainly.com/question/15102743
#SPJ11
What are the two most common input and output devices?
Answers
Answer:
Keyboard and mouse are the most common input devices.
Monitor and the printer are the common output devices.