an algorithm takes 1ms for input size 100. how long will it take for input size 1,000 if the running time is cubic?
Answers
In order to determine the time taken by an algorithm for an input size of 1,000 if the running time is cubic and the algorithm takes 1ms for input size 100, we can use the time complexity formula for cubic time, which is given by:T(n) = a*n^3 + b*n^2 + c*n + d, where a, b, c, and d are constants.Let T(100) = 1ms.
Substituting this into the formula, we get:1 = a*100^3 + b*100^2 + c*100 + dEquation 1Let's consider the time taken for an input size of 1,000. Substituting n = 1,000 in the formula, we get:T(1,000) = a*1,000^3 + b*1,000^2 + c*1,000 + dEquation 2Since the algorithm takes 1ms for input size 100,
the time taken by the algorithm for input size 1,000 is k * (a*10^3), where k is some constant. Since we don't have the value of constant k or a, we cannot determine the exact time taken. However, we can say that it will be more than 100ms, since it is cubic time and the input size has increased by a factor of 10.
To know more about time visit;
https://brainly.com/question/31732120
#SPJ11
Related Questions
What are 3 ways I plan to promote ethical use of technology when students use it your classroom?
Answers
For Technology, Ethics Utilize in Classroom- Maintain your technical equipment, Investigate suitable and secure websites for study and research, The Fair Use Act, Creative Commons, and copyright laws are important, assist in preventing cyberbullying, Self-image is significant, Use proper netiquette.
Simply said, ethical marketing refers to the practise of promoting a good, service, or brand in a way that is consistent with your beliefs and values. This can entail being completely transparent and upfront, as well as refraining from making exaggerated statements. Here are our top suggestions for setting higher standards and fostering an ethical workplace: Develop a code, Engage with both your staff and customers, Reiterate the advantages of the code, Set a positive example for others, Educate your staff, Promote your moral conduct, Encourage moral behavior, Take note of your errors, Adjective. ethical. ethical e-thi-kl.: of or connected to ethics.: adhering to recognised codes of conduct for professionals.
Learn more about ethical from
brainly.com/question/29552906
#SPJ4
In the decision-making process, after you have chosen the right solution, what is the next step?
Answers
Answer:
Implementing the right solution.
Explanation:
There is little point in taking decisions if it stays in the paper. If the best of the possible alternatives have been identified, it must be properly implemented to accomplish the aim it was chosen for. When a decision has been made, it should be implemented, i.e. enacted, into practice. Because of poor execution, a successful decision may become ineffective. A participatory approach can be an efficient way of enforcing such decisions successfully.
Maya has discovered that her computer is running slowly and not like it used to. She has decided to research why this might be. Which of the below is a good step for her to take in the research process?
A: Ask family and friends about their experiences.
B: Allow an unknown online person to remotely troubleshoot the problem.
C: Try every solution that can be found online.
D: Turn off your computer's firewall.
Answers
Answer:
The answer is A: Ask family and friends about their experiences.
Explanation:
B does not make sense, as if you were to let an unknown person online essentially take control of your computer, they might make the problem worse.
C might make sense at first, but if you read the question carefully, it says to try every solution available, and that's not always a good idea.
D does not make sense, as a firewall does not slow down your computer, it blocks unknown users that aren't yourself from accessing your computer, essentially another line of security on top of an anti-virus.
Therefore, the answer would be A, because, assuming her friends and family members have computers, might know how to help her fix her problem.
Keith needs to import data into an Access database from a text file. Which option is the most common delimiter and easiest to work with?
Answers
Answer:tab
Explanation:
Cause I got it right
Answer:
The answer is a comma.
Explanation:
This is the correct answer because space and tab are not delimiters. Therefore it has to be either comma or semicolon and a semicolon is bigger and harder to navigate around. So this gives you the answer of a comma.
more a poster appealing people to be aware
against bullying
Answers
Answer:
Cool
Explanation:
tle electrical instulation maintance
1.what is inventory 2. what is job order 3. what is barrow form 4. what is purchase request
Answers
Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. A job order is a document that contains all the information necessary to complete a specific maintenance task.
Definition of the aforementioned questions1) Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. This includes maintaining a list of all the items in stock, monitoring their usage, and ensuring that there are enough supplies to meet the demands of the job.
2) A job order is a document that contains all the information necessary to complete a specific maintenance task. This includes details about the task, such as the materials and tools required, the location of the work, and any safety considerations.
3) A barrow form is a document used to request materials or equipment from the inventory. It contains details about the requested item, including the quantity, the purpose of the request, and the name of the person or team making the request. The form is usually signed by an authorized person and submitted to the inventory manager or other appropriate personnel.
4) A purchase request is a document used to initiate the process of purchasing new materials or equipment for the electrical insulation maintenance program. It contains details about the item to be purchased, including the quantity, the cost, and the vendor or supplier. The purchase request is typically reviewed and approved by a supervisor or manager before the purchase is made.
learn more about electrical insulation maintenance at https://brainly.com/question/28631676
#SPJ1
you plan to use the language service to detect the language of reviews. you need to route the reviews that contain multi-lingual text to a human translator. which field in the json response should you use to filter records?
Answers
Where you plan to use the language service to detect the language of reviews, and you need to route the reviews that contain multi-lingual text to a human translator, the field in the JSON response should you use to filter records is: "Score" (Option A)
What is a Score?The "score" field in text analytics refers to a confidence score that shows the possibility that a particular analysis result is true. For example, if you're utilizing text analytics to determine the language of a review, the "score" column would reflect your level of confidence in the discovered language.
This parameter might be used to filter records and send evaluations with low confidence scores to a human translator for additional review.
Learn more about JSON:
https://brainly.com/question/28250382?
#SPJ1
Full Question:
You plan to use Text Analytics to detect the language of reviews. You need to route the reviews that are multi-lingual to a human translator. Which field in the JSON response should you use to filter records?
Select only one answer.
A. score
B. errors
C. statistics
D. name
choose the command option that would set the archive bit to indicate a file that will be backe up
Answers
The command option to set the archive bit to indicate a file that will be backed up depends on the operating system or backup software being used. Here is some of the common options:
attrib +a filename
What is archive bit?The archive bit is a file attribute used in some operating systems, such as Windows, to indicate whether a file has been modified since the last backup.
Linux or Unix (using chattr command):
chattr +a filename
The chattr command with the +a option sets the archive attribute for the specified file.
Backup software: Many backup software solutions have their own mechanisms to track files that need to be backed up. These programs often provide options to mark files for backup or enable automatic backup based on file attributes or other criteria.
Learn more about archive bit at:
https://brainly.com/question/28275416
#SPJ4
use the machine learning algorithms: k-nn and logistic regression to classify multiphase flow patterns, using the database and evaluate the performance.
Answers
Machine learning algorithms such as k-nn and logistic regression can be used to classify multiphase flow patterns.
These algorithms can be trained using a database of labeled data and their performance can be evaluated using various metrics.K-nn algorithm is a type of supervised machine learning algorithm. This algorithm works by modeling the probability of the output variable given the input variables. In the case of multiphase flow patterns, logistic regression can be used to classify the flow patterns into two classes based on their characteristics. For example, the flow patterns can be classified as either stratified or slug flow based on the liquid holdup, interfacial tension, and other relevant parameters.To evaluate the performance of these algorithms, various metrics such as accuracy, precision, recall, and F1 score can be used. These metrics can provide insights into the strengths and weaknesses of the algorithms and help in improving their performance.
Learn more about Machine learning algorithms here:
https://brainly.com/question/23496127
#SPJ11
The successful addition of a new entry in a dictionary occurs
after a search for a given key succeeds
after a search for a given key fails
after linear probing
after quadratic probing
Answers
The successful addition of a new entry in a dictionary occurs after a search for a given key fails allowing you to add the new entry with the given key.
When a new entry is added to a dictionary, the first step is to search for the given key. If the search is successful, it means that the key already exists in the dictionary, and the new entry cannot be added. However, if the search for the given key fails, it means that the key does not exist in the dictionary, and the new entry can be added. This process is known as open addressing, where the new entry is inserted in the next available slot after the failed search.
Linear probing and quadratic probing are both methods of resolving collisions that may occur when adding new entries to a dictionary. Linear probing involves checking the next slot in the dictionary when a collision occurs, while quadratic probing involves checking slots that are further away from the original slot in a non-linear way. However, these methods are only used after a search for a given key has failed and a new entry needs to be added to the dictionary.
To know more about key visit:
https://brainly.com/question/31937643
#SPJ11
Decimal numbers are based on __________.
letters (a and b)
16 digits
10 digits
two digits (1s and 0s)
Answers
I’m not sure.
Answer:
They are based on 10 digits.
Explanation:
I just did the test and got the answer right.
Discussion Topic
How does social media affect the process of globalization? Give examples. In what
ways does social media help in creating global communities? Discuss other positive
influences of social media. What might be the adverse effects of excessive use of social
media?
Answers
Answer:
Social media positively affects and impacts the process of globalization. ... Global communities is a social infrastructure tool and as social media helps in strengthening social relationships and bringing people and communities together it leads to creating a string global community.
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
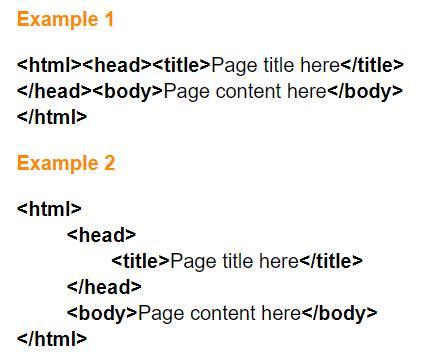
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
What is the output results of Artificial Neurons, electrical signals, chemical signals, numbers or letters?
Answers
Answer:
Neurons communicate via both electrical signals and chemical signals. The electrical signals are action potentials, which transmit the information from one of a neuron to the other; the chemical signals are neurotransmitters, which transmit the information from one neuron to the next.
Explanation:
Edhisive 4.9 lesson practice what variable is used to track the amount of loops that have been executed
Answers
Your question does not make clear which programming language you are interested in learning about, and the solution to a query about keeping track of loop iterations varies depending on the programming language and type of loop being used.
Define for loops.
A for-loop or for-loop in computer science is a control flow statement that specifies iteration. A for loop works specifically by constantly running a portion of code up until a predetermined condition is met. A header and a body are the two components of a for-loop.
A "For" Loop is employed to repeatedly run a given block of code a certain number of times. We loop from 1 to that number, for instance, if we wish to verify the grades of each student in the class. We utilize a "While" loop when the number of repetitions is unknown in advance.
To learn more about for-loop, use the link given
https://brainly.com/question/19706610
#SPJ1
Accessibility is the degree to which a product or service is readily available and usable by _____.
A - as many people as possible
B - anyone who is disabled
C - anyone who is disabled
D - employees
Answers
Answer:
A-As many people as possible
what are patch cables used for? (select two.)
Answers
Patch cables are commonly used in networking and audio applications.
Patch cables are frequently employed in audio and networking applications. These are two particular applications for patch cables: Networking: In networking, patch cables are frequently used to link network components, such as PCs, switches, and routers, to one another or to a network socket. These cables typically have a short length with two connectors on each end, such as RJ-45 or RJ-11. Patch cables are also used in audio applications to link together various audio equipment, including amplifiers, mixers, and speakers. These cables can be used to carry audio signals over small distances and are typically made with 1/4-inch or RCA connectors on each end.
Learn more about networking here:
https://brainly.com/question/13102717
#SPJ4
what type of attack could be exploited in an unencrypted public wireless environment to reroute network traffic to a new default gateway?
Answers
The vulnerability can be used in a man-in-the-middle attack to steal sensitive data delivered over a wireless networks that is WPA protected. If the WPA defect.
What types of assaults could occur on wireless networks?Assaults on wireless networks can be divided into three categories: passive, active, and attacks against specific wireless network elements. When an attacker is in close proximity to a wireless network and has access to wireless communications, passive attacks can occur. Packet sniffing is the most typical passive attack.
What type of assault on wireless networks is most typical? Why?One of the most prevalent wireless attacks is packet sniffing. Older routers, such as those that use WEP encryption, are simple targets for these widespread wireless network attacks.
To know more about wireless networks visit:-
https://brainly.com/question/14329857
#SPJ4
2. stadium seating there are three seating categories at a stadium. for a softball game, class a seats cost $15, class b seats cost $12, and class c seats cost $9. write a program that asks how many tickets for each class of seats were sold, then displays the amount of income generated. solving the stadium seating problem from ticket sales. format your dollar amount in a fixed-point notation with two decimal points and make sure the decimal point is always displayed.
Answers
When I was researching this online, I read that the total cost should be presented as $30.00 something rather than $300.00 if you enter (ticketsA = 10, ticketsB = 8, ticketsC = 6).
The decimal point is the dot that appears between the parts of a whole number and a fraction. The second place to the right of the decimal point, or the hundredths place, is used to round a decimal value to two decimal places.
#include <iostream>
#include <iomanip>
using namespace std;
int main()
{
float A, B, C, ticketsA, ticketsB, ticketsC, total;
A = 15;
B = 12;
C = 9;
cout << "Enter how many class A tickets were sold" << endl;
cin >> ticketsA;
cout << "Enter how many class B tickets were sold" << endl;
cin >> ticketsB;
cout << "Enter how many class C tickets were sold" << endl;
cin >> ticketsC;
total = (A * ticketsA) + (B * ticketsB) + (C * ticketsC);
cout << setprecision(2) << fixed;
cout << "The total amount of income generated is $" << total << endl;
return 0;
}
Learn more about ticket here-
https://brainly.com/question/14001767
#SPJ4
you are a cloud administrator, and you are asked to configure a vpc such that backend servers are not publicly accessible. what should you do to achieve this goal? deploy backend servers in different availability zones deploy the backend servers on premises use private subnets for backend servers implement audit logging on backend servers
Answers
To configure a VPC such that backend servers are not publicly accessible, I would Backend servers can be configured with a private subnet to restrict public access.
What VPC?A virtual private cloud (VPC) is a shared resource pool that can be configured on-demand and is assigned within a public cloud environment. It offers some degree of isolation between the various organizations (referred to as users below) using the resources. A private IP subnet and a virtual communication construct (like a VLAN or a collection of encrypted communication channels) are typically assigned to each user of a VPC in order to provide that user with isolation from all other users of the same cloud, including both other VPC users and other public cloud users.In a VPC, the previously discussed method that offers cloud isolation is combined with a virtual private network (VPN) function (again, allotted per VPC user) to secure an organization's remote access to its VPC resources through authentication and encryption. A company using this service is effectively functioning on a "virtually private" cloud with the adoption of the mentioned isolation levels (i.e., as if the cloud infrastructure is not shared with other customers), hence the name "VPC."To learn more about VPC, refer to
https://brainly.com/question/28085922
#SPJ4
match the image-editing tools with their features.
Answers
The main tools with which a user may manage, improve, and change images are graphic software programmes, which can be roughly categorised as vector graphics editors, raster graphics editors.
What kinds of features exist in images?In computer vision and image processing, a feature is a piece of information about an image's content. It often pertains to whether a certain section of the image possesses particular characteristics.
What is a sample photo feature?A feature image is a news image that provides more in-depth coverage for a news story or recent news story but has no compelling reason to appear alongside the top stories.
To know more about software visit:-
https://brainly.com/question/985406
#SPJ1
To make the first day on the job easier, you can
Answers
Answer:
How To Prepare For Your First Day At A Job
Research, Research, Research.
Make Contact With Your Manager.
Confirm Your Schedule.
Do A Test Run Of Everything.
Introduce Yourself To The Team Virtually.
Find A Buddy.
Practice Extra Self-Care.
Arrive Early.
Explanation:
In Python create the following functions:
1. MRT èUse Miller-Rabin Primality Test to choose prime number with s=512 bits and
check the primality test.
2. EA èUse Euclidean Algorithm to evaluate gcd
3. EEA èUse Extended Euclidean Algorithm to find modular inverse of the value
4. powmod_smè Square and multiply algorithm to evaluate exponentiation.
Now write the code for
I. RSA Key Generation (use above functions 1., 2., 3. ) should be
a. Choose two primes p and q of s bits using MRT where p is not equal to q.
b. Calculate = p ∗ , and phi() = (p − 1) ∗ ( − 1)
c. Chose randomly e from the set of {1,..., phi() − 1} and check using EA if
c(, phi()) = 1 if not chose again until it full fills the condition.
d. Calculate = 12 mo phi() using EEA. Note that should be at least 0.3 ∗
bits
e. Output :;< = (, ) and := = ()
II. RSA Encryption with input :;< = (, ) and random plaintext x and output should be
ciphertext y, evaluate exponentiation using the function powmod_sm
III. RSA Decryption with input := = () and ciphertext y and output should be plaintext x,
evaluate exponentiation using the function powmod_sm. Please make sure to check that you get the same plaintext value before the encryption.
Answers
The solution to the RSA key generation, encryption and decryption in Python is given below:I. RSA Key GenerationPython code to implement RSA key generation is as follows:```
import random
import math
# Miller-Rabin Primality Test
def MRT(n,s):
d = n-1
r = 0
while(d % 2 == 0):
r += 1
d = d // 2
for i in range(s):
a = random.randint(2, n-1)
x = pow(a, d, n)
if (x == 1 or x == n-1):
continue
for j in range(r-1):
x = pow(x, 2, n)
if (x == n-1):
break
else:
return False
return True
# Euclidean Algorithm to evaluate gcd
def EA(a, b):
if b == 0:
return a
else:
return EA(b, a % b)
To know more about implement visit:
https://brainly.com/question/32093242
#SPJ11
The Impacts of Technology: the Good, the Bad, and Everything In-Between Summarize the findings that you gather from the interview with the older adult and the local business professional. Through your response, also discuss how modern information technology has affected society.
Answers
Technology affects almost every aspect of modern life, including productivity, social interaction, access to food and healthcare, as well as the effectiveness and safety of transportation.
Explain about the impacted by technology?Social media and mobile devices can cause mental and physical health problems, such as eyestrain and difficulties focusing on demanding tasks. They might also aggravate more severe medical issues like depression. Teenagers and young children, who are still developing, may be particularly affected by excessive technology use.
Impact technology, which aims to solve a significant social or environmental issue, is the deliberate use of responsible science and technology to the benefit of people and the environment.
Artificial intelligence, or AI, and machine learning are terms used to describe a computer's capacity for learning and acting intelligently, which enables it to make decisions, perform tasks, and even forecast the future based on what it learns from data.
To learn more about impacted by technology refer to:
https://brainly.com/question/14573463
#SPJ1
Witch icon allows you to see paragraph formatting feature
Answers
What happens when you leave a tablet charging for two days?
Answers
I am sure it will get 100% on the tablet. Maybe if you leave it charging for 2 days it might overheat and cause a fire.
Explanation:
Left the tablet charging for 2 days.
B. Direction: Choose the letter of the correct answer.
11. Filler comes from silex, raw linseed oil, and turpentine.
A. Shellac
b paste filler C. Varnish
d. paint
12. A kind of varnish that is not waterproof.
A Paint
b. Shellac c. Enamel
d. Lacquer
13. What kind of varnish that dries up easily and is not waterproof? It comes from lac gum
diluted in alcohol
A Varnish
b. stains c. Enamel d. Shellac
14. A kind of stain that is easiest to apply on wood.
a. Spirit stain b. fillers c Oil stain
d. paint
15. It prevents moisture on the wood that causes decay.
a. Enamel
b. paint
c. Varnish
d. lacquer
Answers
Where are MAC addresses stored for future reference?
a. MAC cache
b. Ethernet cache
c. ARP cache
d. NIC
Answers
The MAC addresses are stored for future reference in the (C) ARP cache.
This cache is a table that maps the IP addresses to the corresponding MAC addresses on a network.
Whenever a device needs to communicate with another device on the network, it first checks the ARP cache to see if it already has the MAC address of the destination device.
If the MAC address is not found in the cache, the device sends out an ARP request to obtain the MAC address from the device with the corresponding IP address.
Once the MAC address is obtained, it is stored in the ARP cache for future reference.
This process helps to improve the efficiency of network communication by reducing the number of ARP requests that need to be sent out.
Know more about MAC addresses here:
https://brainly.com/question/13267309
#SPJ11
a. Why are the data known as raw facts? Explain.
Answers
Answer:
The word raw means that the facts have not yet been processed to get their exact meaning. Data is collected from different sources. ... The result of data processing is Information.
Answer:
The Raw Facts and Figures are Called Data.
The word raw means that the facts have not yet been processed to get their exact meaning. Data is collected from different sources. It is collected for different purposes. ... The process of sorting or calculating data is called Data Processing
Hope you got it
If you have any question just ask me
If you think this is the best answer please mark me as branliest
Which element is represented by the electron configuration in example B? Example B: 1s22s22p63s23p64s1 Aluminum Cesium Potassium Arsenic
Answers
Answer:
Potassium
Explanation:
potassium because all of the others are being used and potassium is not being used in example b
Answer:
It is potassium.
Explanation:
I just took the quiz and it was right.