_____ agents usually track and report on computer equipment and network systems to predict when a system crash or failure might occur.
Answers
Monitoring agents usually track and report on computer equipment and network systems to predict when a system crash or failure might occur. Monitoring agents provide real-time visibility into the health and performance of computer equipment and network systems.
Monitoring agents are software elements created to monitor and report on the performance and status of computer hardware and network systems. Their main goal is to anticipate and identify probable system failures or breakdowns before they occur, enabling administrators or operators to take proactive action to stop or lessen the effects of such incidents.
Learn more about Monitoring agents here:
https://brainly.com/question/32322678
#SPJ4
Related Questions
Which two statements show cultural effects of computers and the Internet?
O A. Melissa says "LOL" instead of laughing at a joke her friend told.
B. Jake uses the Internet to meet people from other countries online,
C. A city's traffic lights are controlled by a computer algorithm to
help improve traffic
D. A company uses servers instead of paper databases to store
sales data
Answers
Answer:
I think it is A, Melissa says "LOL" instead of laughing at a joke her friend told.
Jake uses the Internet to meet people from other countries online, and a city's traffic lights are controlled by a computer algorithm to help improve traffic are the statements that show cultural effects of computers and the Internet. The correct options are B and C.
What is internet?The internet is a worldwide network of interconnected computers and servers that allows users to share, exchange, and communicate with one another.
Jake uses the Internet to connect with people from other countries: The internet has facilitated communication and the exchange of ideas between people from various cultures, leading to a greater understanding and appreciation of different cultures.
A computer algorithm controls traffic lights in a city to help improve traffic flow: This is an example of how technology is being used to make daily life more efficient and sustainable.
Thus, the correct options are B and C.
For more details regarding internet, visit:
https://brainly.com/question/13308791
#SPJ7
Before she applies for an internship with a local engineering company, what type of letter might zaynab ask one of her teachers to write for her? question 3 options: resignation letter complaint letter thank-you letter recommendation letter
Answers
An internship is a period of supervised work experience offered by an employer to a student or recent graduate in a specific field of study.
Zaynab may request a recommendation letter from one of her teachers to strengthen her internship application to a local engineering company. A recommendation letter is a formal document that assesses Zaynab's abilities, academic achievements, skills, and personal qualities. It also endorses her as a candidate for the position she is applying for. This letter provides the employer with an understanding of Zaynab's qualities and how she can contribute to the company. It can also add weight to Zaynab's application, as a recommendation letter from a credible source can increase the likelihood of her being selected for the position. A well-written recommendation letter may provide Zaynab with an advantage over other applicants, as it highlights her potential and vouches for her suitability for the role.
To learn more about internship visit;
https://brainly.com/question/27290320
#SPJ4
At which of the capability maturity model integration maturity levels, are processes well defined, understood, and consistent across the organization?.
Answers
At defined (quantitatively managed), the capability maturity model integration maturity levels, are processes well defined, understood, and consistent across the organization.
An organization's software development process can be developed and improved using the Capability Maturity Model (CMM). The model outlines a five-level evolutionary path of processes that get more ordered and systematic as they mature.
The Software Engineering Institute (SEI), a research and development facility supported by the U.S. Department of Defense (DOD) and now a part of Carnegie Mellon University, developed and promotes CMM. In order to address software engineering difficulties and, generally speaking, develop software engineering approaches, SEI was established in 1984.
More specifically, SEI was created to streamline the DOD's software-intensive system development, acquisition, and maintenance processes. SEI supports the widespread industrial use of CMM Integration (CMMI), a development of CMM. Additionally, the capability maturity model is still commonly employed.
CMM is comparable to ISO 9001, one of the International Organization for Standardization's ISO 9000 set of standards. The ISO 9000 standards outline an efficient quality system for the manufacturing and service sectors; ISO 9001 explicitly addresses the creation and upkeep of software.
To know more about Capability Maturity Model click on the link:
https://brainly.com/question/14595603
#SPJ4
If you want to stop a loop before it goes through all of its iterations, the break statement may be used. Group of answer choices True False
Answers
Answer:
Answer is true
Explanation:
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
When water changes from a solid to a liquid, a chemical change occurs.
TrueFalse
Answers
Explanation:
TRUE is the answer
What is 3g,4g, and 5g.
Answers
..........................................
Please help me please
Answers
Answer:
what are the choices
Explanation:
Give at lesat 3 examples of how is NLG (Natural Language Generation) beneficial and unbeneficial (pls support your points)
Answers
NLG (Natural Language Generation) is beneficial isuch as automating content creation, personalizing user experiences, and generating insights from data but have limitations including potential biases in generated content and difficulties in capturing nuanced human language.
How is NLG beneficial and unbeneficial?NLG offers numerous benefits including the ability to automate the generation of content across different domains, such as news articles, product descriptions, and weather reports. This helps save time and resources by eliminating the need for manual content creation.
NLG systems may have limitations. One concern is the potential for biased content generation as the models are trained on existing data that may contain biases. This can lead to the generation of discriminatory or misleading content.
Read more about Natural Language
brainly.com/question/14222695
#SPJ1
NLG is beneficial in generating content quickly and accurately, maintaining consistency, and providing a personalized user experience
NLG, or Natural Language Generation, is the method of generating natural language text using computer algorithms. It is a subfield of artificial intelligence that focuses on creating human-like texts, thereby making it easier for humans to interact with machines. Natural Language Generation is beneficial in many ways, but it also has its limitations. In this response, we will discuss the benefits and drawbacks of NLG in detail. Benefits of Natural Language Generation (NLG):
1. Efficient content creation: NLG algorithms can generate content faster than human writers, making it easier for businesses and publishers to create large amounts of content in less time. This is particularly beneficial for news and sports articles, where quick updates are required.
2. Consistent quality and tone: NLG can ensure that the content is written in a consistent tone and style, maintaining the brand's voice and values. In contrast, human writers can experience mood changes, which may influence the quality of their writing.
3. Personalization: NLG algorithms can create personalized messages and content, providing a better user experience for customers and clients. It can also be used for chatbots to provide human-like interactions with customers, improving customer satisfaction.
Unbeneficial of Natural Language Generation (NLG):1. Limited creativity: NLG algorithms can generate text based on the data it is fed. However, it lacks creativity and may fail to produce the same level of creativity as human writers. NLG cannot replace human writers' creativity, which is required in fields such as literature and poetry.
2. Dependence on data quality: NLG requires high-quality data to generate effective texts. Low-quality data may result in incorrect information and errors in the generated text.
3. Lack of empathy: NLG algorithms lack human empathy and understanding of social and emotional contexts. This may cause problems in situations that require a high level of emotional intelligence, such as counseling, medical diagnosis, and human resources. Therefore, NLG is beneficial in generating content quickly and accurately, maintaining consistency, and providing a personalized user experience. However, it has its limitations and cannot replace human creativity, empathy, and emotional intelligence.
For more questions on articles
https://brainly.com/question/25276233
#SPJ8
Write a program that: Takes the list lotsOfNumbers and uses a loop to find the sum of all of the odd numbers in the list (hint: use Mod). Displays the sum.
Answers
Answer:
Following are the code to this question:
#include <iostream>//defining header file
using namespace std;
int main()//defining main method
{
int x[]={2,3,4,6,7,8,9,1,11,12};//defining 1-D array and assign value
int i,sum=0;//defining integer variable
for(i=0;i<10;i++)//defining loop for count value
{
if(x[i]%2==1)//defining if block to check odd value
{
sum=sum+x[i];//add value in sum variable
}
}
cout<<sum;//print sum
return 0;
}
Output:
31
Explanation:
In the above-given program, an integer array "x" is declared that holds some integer values, and in the next line two integer variable "i and sum" is defined which is used to calculate the value.
In the next line, a for loop is declared, that counts all array value, and it uses the if block to check the odd value and add all the value into the sum variable.
The code is in Java.
It uses for loop, if-else structure, and mod to calculate the sum of odd numbers in a list.
Comments are used to explain each line of code.
You may see the output in the attachment.
//Main.java
import java.util.*;
public class Main
{
public static void main(String[] args) {
//create a list with some numbers
List<Integer> lotsOfNumbers = Arrays.asList(7, 20, 1002, 55, 406, 99);
//initialize the sum as 0
int sumOfOdds = 0;
//create a for each loop to iterate over the lotsOfNumbers list
//check each number, if it is odd or not using the mod
//if it is odd, add the number to the sum (cumulative sum)
for (int number : lotsOfNumbers){
if(number % 2 == 1)
sumOfOdds += number;
}
//print the sum
System.out.println("The sum of odd numbers: " + sumOfOdds);
}
}
You may check out another question at:
https://brainly.com/question/24914609

what is the main task of the project manager
Answers
Answer:
to handle day to day operations of a project
Explanation:
Answer: to handle the day to day operations of the project
Explanation:
What is the class width? what are the approximate lower and upper class limits of the first class?
Answers
The distance between the bottom bounds of succeeding classes is known as the "class width." The range is the number of data entries between the maximum and minimum. 1. Choose how many classes to use if the number is not specified.
Set the smallest number as the lower class limit for the first class to determine the class limits. Next, multiply the lower class limit by the class width to arrive at the next lower class limit. Continue until you have taken every lesson. A class's upper limit is one less than the next-lowest class's upper limit.
The class interval's maximum value is known as the upper limit. Similar to the upper limit, the lower limit is the class interval's smallest value. Making the upper limit of one class and the lower limit of the following class equal and the same for the lower limit is necessary to determine the actual upper limits and lower limits.
Learn more about class width:
https://brainly.com/question/14378469
#SPJ4
mr. abbot is recording requirements for the new orchestration tool. he needs the tool to automatically deploy and replicate any containers that have crashed. what is this called?
Answers
The functionality that automatically deploys and replicates containers that have crashed in an orchestration tool is commonly referred to as "autohealing."
Autohealing is a critical feature in container orchestration tools that ensures the continuous availability and reliability of containerized applications. When a container crashes or becomes unresponsive, the autohealing mechanism detects the failure and automatically takes action to restore the desired state.
This typically involves deploying a new instance of the container to replace the crashed one, or replicating the container across multiple nodes to maintain the desired level of redundancy and fault tolerance. Autohealing minimizes downtime and manual intervention, improving the overall resilience and performance of the orchestration environment.
Learn more about environment click here:
brainly.com/question/5511643
#SPJ11
An organisation creates a scope/statement of work
before designs are complete and some contract details are vague.
What is a risk if the organisation is using fixed price
contracts?a) The contractor m
Answers
Using fixed-price contracts when the scope and contract details are unclear poses a risk to contractors. Changes in scope can lead to financial losses.
When an organization creates a scope/statement of work before designs are complete and some contract details are vague, there is a risk associated with using fixed-price contracts. The main concern is that if the scope or requirements change significantly after the contract is signed, the contractor may face financial losses. This is because fixed-price contracts establish a predetermined price that does not account for any additional work or changes that may be required. If the project scope expands or if there are unforeseen circumstances, the contractor may need to invest additional resources without receiving additional compensation. This poses a financial risk to the contractor and can lead to disputes or project delays if the parties involved cannot agree on the necessary adjustments to the contract terms. Therefore, it is essential for organizations and contractors to carefully assess and address any ambiguities or uncertainties in the contract and consider alternative contract types, such as cost-plus or time and materials contracts, when the project requirements are not fully defined or subject to potential changes.
know more about fixed-price contracts here: brainly.com/question/29534898
#SPJ11
Which range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE?
A. 10.120.160.0 to 10.120.168.0
B. 10.120.160.0 to 10.127.255.255
C. 10.120.160.0 to 10.120.191.255
D. 10.120.160.0 to 10.120.167.255
Answers
10.120.160.0 to 10.120.167.255 is the range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE.
Thus option D is correct.
What is IP addresses?An Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification and location addressing.
Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s.
IP addresses are written and displayed in human-readable notations, such as 192.0.2.1 in IPv4, and 2001:db8:0:1234:0:567:8:1 in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., 192.0.2.1/24, which is equivalent to the historically used subnet mask 255.255.255.0.
Learn more about IP addresses
https://brainly.com/question/16011753
#SPJ4
T/F: a homegroup offers better security than workgroup sharing
Answers
True, a homegroup offers better security than workgroup sharing.
A homegroup is a feature in Windows that allows devices on a home network to easily share files and printers. It provides better security than workgroup sharing because it uses a password to control access to shared resources. Only those with the homegroup password can access the shared files and printers, ensuring that unauthorized users cannot access your shared resources. Additionally, homegroups make it easier to manage permissions and user access, further enhancing security.
Learn more about Windows here:
https://brainly.com/question/31252564
#SPJ11
Write the technical terms for each of the following:
a. The use of the Internet to buy and sell goods and services.
b. Voice communication through the Internet. C. A program that allows the user to log into a remote computer on the Internet as a user on that system.
d. High speed digital communication network evolving from existing telephony.
e. Software that is used for surfing information through the Internet.
Answers
Explanation:
network" (and any subsequent words) was ignored because we limit queries to 32 words.
what is a major difference between cyber vandalism and online priacy
Answers
Answer:
There really isn't a significant difference; two terms for the same things. B. Vandals want to disrupt and show off a viewpoint; the goal of online piracy is to steal money.
Answer:
Vandals want to disrupt and show off a viewpoint; the goal of online piracy is to steal money.
Explanation:
a p e x
is often conducted by phone with a hacker imitating someone in a position of authority and attempting to gradually draw information out of a user.
Answers
This type of attack is commonly known as "social engineering" or "voice phishing," where a hacker impersonates an authoritative figure to manipulate and extract information from a user.
In social engineering attacks conducted over the phone, the hacker typically adopts a persona of someone in a position of authority, such as a company executive, IT support personnel, or a trusted individual. By leveraging this false identity, the hacker aims to gain the victim's trust and exploit their willingness to comply with requests.
The attacker uses various psychological tactics to gradually draw out sensitive information from the user. They may employ techniques such as building rapport, creating a sense of urgency or fear, and exploiting human vulnerabilities like trust and helpfulness. The ultimate goal is to obtain confidential data, such as passwords, account details, or personal information that can be used for malicious purposes like identity theft or unauthorized access.
It is important to remain vigilant and cautious when receiving unsolicited phone calls, especially from individuals requesting sensitive information. Verifying the identity of the caller by using trusted contact information or reaching out to the supposed authority figure independently can help mitigate the risk of falling victim to social engineering attacks. Additionally, organizations can implement awareness programs and security measures to educate employees and protect against these types of threats.
Learn more about hacker here:
brainly.com/question/32413644
#SPJ11
Define bit, nibble, byte, binary
Answers
Answer: , a group of 4 bits is called a nibble
Explanation:
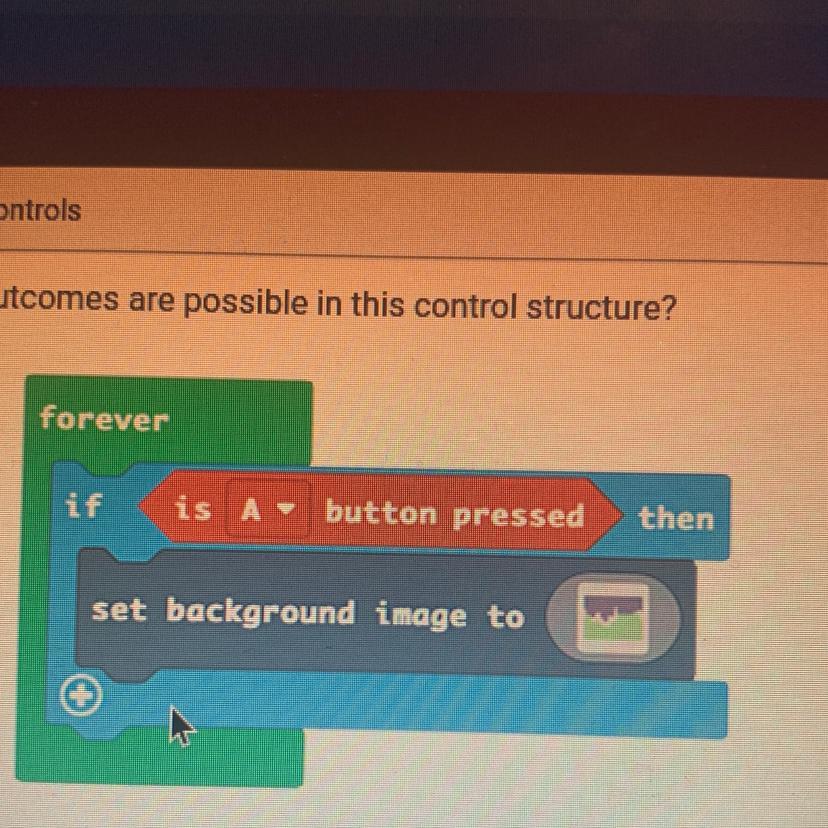
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
The full meaning of QWERTY
Answers
Answer:
A keyboard layout for Latin-script alphabets
what is the relationship between the processing time at a resource and its capacity?
a. They are the same
b. They are reciprocals of each other
c. They are multiples of each other
d. They are not related
Answers
The relationship between a resource's processing time and its capacity is reciprocal.
At a given resource, what distinguishes capacity from utilization?The difference between capacity and utilization is that capacity refers to the maximum amount that can be used for something or someone, while utilization refers to how well that something or someone is used.
What is the relationship between a system's constraint, also known as a bottleneck, and its capacity?Simply put, a resource with more demand than capacity to deliver is a bottleneck. A constraint is the system bottleneck with the least capacity; it can only be considered the "constraint" once you decide how to manage it.
To know more about processing time visit :-
https://brainly.com/question/29307330
#SPJ4
How do cell phones negatively affect students in the classroom?
Answers
Cell phones negatively affect students with a divert attention and have a detrimental effect on cognitive ability, reaction times, performance, and enjoyment of focused tasks.
What is cognitive ability?Any task, no matter how simple or difficult, requires cognitive abilities, which are brain-based skills. They are less concerned with actual knowledge and more with the processes by which we learn, remember, solve problems, and pay attention.
For instance, picking up the phone requires motor skills (lifting the receiver), language skills (talking and understanding language), perception (hearing the ring tone), decision-making (answering or not), and social skills.
Particular neuronal networks provide support for cognitive abilities or skills. For instance, the temporal lobes and some parts of the frontal lobes are primarily responsible for memory functions. Due to damaged neuronal regions and networks, people with traumatic brain injuries may have lower cognitive function.
Learn more about cognitive abilities
https://brainly.com/question/9741540
#SPJ4
explain methods that describe how to make forensically sound copies of the digital information.
Answers
Creating forensically sound copies of digital information is crucial in the field of digital forensics to ensure the preservation and integrity of evidence.
Several methods can be employed to achieve this:
1)Bitstream Imaging: This method involves creating an exact sector-by-sector copy of the original digital media, including all data and metadata.
Tools like dd or FTK Imager can be used to capture a bitstream image, which ensures that the copy is an exact replica of the original.
Hash values such as MD5 or SHA-256 can be computed for verification purposes.
2)Write-Blocking: Before making a copy, it is essential to use hardware or software write-blocking techniques to prevent any accidental modification of the original data.
Write-blockers, like Tableau or WiebeTech devices, intercept write commands, allowing read-only access during the imaging process.
3)Validation and Verification: Once the copy is created, it is crucial to validate its integrity.
Hash values generated during the imaging process can be compared with the hash values of the original media to ensure their match.
Additionally, tools like EnCase or Autopsy can perform file-level validation to verify the integrity of individual files within the copy.
4)Chain of Custody: Maintaining a proper chain of custody is essential to establish the integrity and admissibility of digital evidence.
Documenting each step of the imaging process, including who performed the copy, the date and time, and any changes made, ensures that the evidence is legally defensible.
5)Preservation: The forensically sound copy should be stored in a secure and controlled environment to prevent tampering or accidental modification.
Access to the copy should be restricted, and measures like write-protecting or storing it on write-once media, such as write-once DVDs or read-only drives, can enhance its preservation.
For more questions on digital information
https://brainly.com/question/12620232
#SPJ8
On what day did redhat push out a patch to address cve-2017-6074 for their rhel linux 7 kernel?
Answers
The CVE-2017-6074 vulnerability refers to a use-after-free flaw in the Linux kernel's DCCP protocol implementation, which could allow a local attacker to escalate their privileges on the affected system.
According to the Red Hat Security Advisory (RHSA-2017:0294), the patch for CVE-2017-6074 was released on February 22, 2017, for Red Hat Enterprise Linux (RHEL) 7. This means that the patch was pushed out on that same day to address the vulnerability in the RHEL 7 kernel.
It's worth noting that CVE-2017-6074 affected multiple Linux distributions, and each vendor may have their own timeline for releasing patches to address the vulnerability.
Learn more about Linux kernel here:
https://brainly.com/question/31309972
#SPJ11
in the function =sum(b2:b6), which part of the function is the argument?
Answers
In the function =sum(b2:b6), b2:b6 is the argument in the function.
What is an argument?
A way for you to give a function more information is with an argument. The data can then be used like a variable by the function while it executes. To put it another way, you can enter information as a parameter or argument when you build a function.
Arguments are variables that are only used in that particular function.When calling the function, you must specify the argument's value.Your applications can use more information by using function arguments.To learn more about an argument, use the link given
https://brainly.com/question/12947158
#SPJ1
Show transcribed data
This assignment helps to learn how to use generics in Java effectively. The focus of this assignment is on the relationships between classes and the generic definitions applied that sets all classes into context. Implement an application that handles different kinds of trucks. All trucks share the same behavior of a regular truck but they provide different purposes in terms of the load they transport, such as a car carrier trailer carries cars, a logging truck carries logs, or refrigerator truck carries refrigerated items. Each truck only distinguishes itself from other trucks by its load. Inheritance is not applicable because all functionality is the same and there is no specialized behavior. The property of every truck is also the same and only differs by its data type. That is the load of a truck is defined by an instance variable in the truck class. This instance variable is defined by a generic parameter that must have the Load interface as an upper bound. The Load interface represents any load a truck can carry. It is implemented by three different classes. Create the following types . Load: Create an interface called Load. The interface is empty. • Car. Create a class named Car that implements the tood intertace. This class is empty but you may add properties. Treelog: Create a class named Treelog that implements the Lord interface. This class is empty but you may add properties. • Refrigerated Storage: Create a class named Refrigerated Storage that implements the cous interface. This class is empty but you may add properties. • Truck: A final public class named truck Instances (not the class itself:) of this Truck class should be specialized in the way they handle freight transport. The specialized freight is accomplished by the class using a generic type parameter in the class definition. The generic parameter on the class definition must have the Load interface as its upper bound. Each truck carries a freight which is defined by an instance variable of praylist with elements of the generic type parameter, Do not use the type toad interface for the elements. The exact type of the load instance variable is determined at instantiation time when the variable of the truck class is declared. The class has the following members • A member variable of type arrayList named freignt. The ArrayList stores objects of the generic type defined in the class definition • A method named 1006.) that loads one object onto the truck and adds it to the releit list. The object is passed in as an argument and must be of the generic type defined in the class definition • A method named unicooker) which expects an index of the element in the predprt list to be removed. The removed element is returned by the method. The return type must match the generic type defined in the class signature. Solution: Implement the program yourself first and test your solution. Once it works, fill in the missing parts in the partial solution provided below. Download Truck.java interface Load } class } class Tree Log } class Refrigerated Storage } public final class Truck private ArrayList freight = new ArrayList 0: public void load(T item) { this.freight.add(item); } public unloadint index) { return this.freight.get(index); } }
Answers
The solution to the given problem regarding Java program is as follows:
class Car implements Load { }
class Treelog implements Load { }
class RefrigeratedStorage implements Load { }
interface Load { }
public final class Truck {
private ArrayList<Load> freight = new ArrayList<>();
public void load(Load item) {
this.freight.add(item);
}
public Load unload(int index) {
return this.freight.get(index);
}
}
The provided Java program deals with different types of trucks. Each truck carries a freight, which is defined as an instance variable named `freight` of type `ArrayList` with elements of the generic type parameter.
The class `Truck` has the following members:
A member variable named `freight` of type `ArrayList<Load>`. This `ArrayList` stores objects of the generic type `Load`.A method named `load` that takes an object of type `Load` as an argument and adds it to the freight list.A method named `unload` that expects an index of the element in the `freight` list to be removed. It returns the removed element, and the return type matches the generic type defined in the class signature.Note that the Load interface is implemented by the classes Car, Treelog, and RefrigeratedStorage, which allows objects of these classes to be added to the freight list. The specific type of the Load instance variable is determined at instantiation time when the variable of the Truck class is declared.
Learn more about Java program: https://brainly.com/question/17250218
#SPJ11
Help me pls!!! last question
Tori needs to turn her Turtle to the left 90 pixels. Which line of code should Tori use?
tina(90)
tina.back(90)
tina.left(90)
tina.right(90)
Answers
Answer:
tina.left(90)
Explanation:
In code if you want your character to turn left you put "left" in your code and if you want your character to go right type "right" and so on and so on so your answer is tina.left(90)
Answer: Option C is the correct line of code Tori should use.
tina.left(90)
Explanation:
I took the test and got it correct, you can trust me.
, Hope this helps :)
Have a great day!!
Why don’t many cyber criminals ever go to jail?
Answers
Answer: Most laws are national in their implementation, despite cybercrime conventions, where the Internet is borderless and international by definition. Countries do not agree, which makes this area exceptionally challenging from a legal perspective.