After the information that needs to be protected has been identified, what step should be completed next
Answers
After identifying the information that needs to be protected, the next step that should be completed is conducting a risk assessment. This step involves evaluating the potential threats and vulnerabilities to the identified information, as well as assessing the potential impact and likelihood of those risks.
A risk assessment helps determine the level of protection needed and guides the development of an effective security strategy. A risk assessment involves analyzing the value and sensitivity of the identified information, identifying potential threats such as unauthorized access, data breaches, or physical damage, and evaluating the vulnerabilities and weaknesses in the systems or processes that handle the information. By understanding the risks, their potential impact, and the likelihood of occurrence, organizations can prioritize their security efforts and allocate resources effectively.
During the risk assessment process, organizations may employ various methodologies and frameworks, such as risk matrices or qualitative and quantitative analysis techniques, to assess and quantify the risks. This assessment provides valuable insights into the specific areas that require security measures and helps in determining the appropriate security controls and safeguards to mitigate the identified risks effectively.
Overall, conducting a risk assessment is a crucial step in the information security lifecycle, as it enables organizations to make informed decisions regarding the implementation of security measures and allocate resources appropriately to protect the identified information.
To learn more about risk assessment, click here:
brainly.com/question/32694936
#SPJ11
Related Questions
Computer networks can consist of as few as computers.
Options are: 5, 10, 2, & 3
Answers
Answer: 2
Explanation:A computer network is a set of computers that are connected together.
Select the strategies below that are likely to increase audience attention. Vary the use of transitions for each slide. Avoid the use of animations. Use similar animation styles on each slide. Use consistent transitions. Use lots of different animation styles on each slide. Match special effects to content.
Answers
The strategies below that are likely to increase audience attention is vary the use of transitions for each slide. Thus, option A is correct.
Why effective attention is important?An effective attention getter should always relate the topic to the audience and pique the audience's interest in the topic. In addition, for a speech to persuade, the attention getter should engage an audience beginning, for example, by asking a rhetorical question.
Use an interesting quote and ask a question that provokes thought in the reader, they could be rhetorical questions or just questions and answers. Humor if handled well, can be a wonderful attention getter.
Therefore, The strategies below that are likely to increase audience attention is vary the use of transitions for each slide. Thus, option A is correct.
Therefore, The strategies below that are likely to increase audience attention is vary the use of transitions for each slide. Thus, option A is correct.
Learn more about strategies on:
https://brainly.com/question/15860574
#SPJ1
How to fix the number you are trying to reach is not reachable?
Answers
Answer:
It means that the person didn't pay their phone bill and their phone got shut off. I know someone who lets this happen often and whenever it does, this is the automated message i hear.
This might not be the only thing it means, but i definitely know that it is at least one.
Explanation:
The way a student prepares for a test or reviews academic material is referred to as
a study environment.
study habits.
study hall.
a study schedule.The way a student prepares for a test or reviews academic material is referred to as
Answers
Answer:
study habits
Explanation:
Answer:
The Answer is Study Habits
Explanation:
Just got it right on edge
why is entity relationship diagram or database schema necessary, even if you never design or build a database
Answers
Entity relationship diagrams or database schemas are necessary even if you never design or build a database because they provide a visual representation of the data structure and relationships, aiding in understanding and communication.
Entity relationship diagrams (ERDs) and database schemas serve as essential tools in the field of data management and analysis. They provide a systematic and organized way to represent the structure and relationships within a database, even if you are not directly involved in the design or construction of the database itself.
Firstly, ERDs and database schemas offer a visual representation of how data entities relate to one another. By illustrating entities (such as tables) and their attributes (such as columns), along with the relationships and connections between them, these diagrams enable a comprehensive overview of the data model. This visual representation facilitates understanding and clarity, allowing stakeholders to grasp the complex relationships between different entities and their attributes. It serves as a common language for discussing and documenting the structure and organization of data.
Secondly, ERDs and database schemas enhance communication and collaboration among various stakeholders involved in the data ecosystem. Whether you are a business analyst, project manager, software developer, or data scientist, having a shared understanding of the data structure is crucial. These diagrams serve as a reference point, providing a clear and concise representation of how data is organized and connected. They act as a blueprint for discussions, ensuring that everyone involved can align their understanding of the data model and make informed decisions based on accurate information.
Lastly, even if you are not directly involved in designing or building a database, understanding ERDs and database schemas can be beneficial in many ways. It allows you to analyze existing databases, identify potential improvements, and optimize data workflows. Furthermore, it helps in data integration tasks, where you may need to map and transform data from various sources into a unified structure.
Learn more about database schemas
brainly.com/question/13098366
#SPJ11
1. List deep NLP models
2. Explain concept of vanishing gradient over fitting
computational load
Answers
Deep NLP models are Recursive neural network (RNN), Convolutional neural network (CNN), Long-short-term memory (LSTM), Gated recurrent unit (GRU), Autoencoder (AE). The connection between vanishing gradient and overfitting lies in the ability of deep neural networks to learn complex representations.
a. Recursive Neural Network (RNN):
RNNs are a type of neural network that can process sequential data by maintaining hidden states that capture information from previous inputs.They are commonly used in tasks like natural language understanding, sentiment analysis, and machine translation.b. Convolutional Neural Network (CNN):
CNNs, originally designed for image processing, have been adapted for NLP tasks as well. In NLP, CNNs are often applied to tasks such as text classification and sentiment analysis, where they can capture local patterns and learn hierarchical representations of text.c. Long Short-Term Memory (LSTM):
LSTMs are a type of RNN that addresses the vanishing gradient problem by introducing memory cells. They are effective in capturing long-term dependencies in sequential data and have been widely used in various NLP tasks, including language modeling, machine translation, and named entity recognition.d. Gated Recurrent Unit (GRU):
GRUs are another type of RNN that simplifies the architecture compared to LSTM while still maintaining effectiveness. GRUs have gating mechanisms that control the flow of information, allowing them to capture dependencies over long sequences. They are commonly used in tasks like text generation and speech recognition.e. Autoencoder (AE):
Autoencoders are unsupervised learning models that aim to reconstruct their input data. In NLP, autoencoders have been used for tasks such as text generation, text summarization, and feature learning. By learning a compressed representation of the input, autoencoders can capture salient features and generate meaningful output.2.
If the gradients vanish too quickly, the network may struggle to learn meaningful representations, which can hinder its generalization ability. On the other hand, if the gradients explode, it may lead to unstable training and difficulty in finding an optimal solution.
Both vanishing gradient and overfitting can increase computational load during training.
To address these issues, techniques such as gradient clipping, weight initialization strategies, regularization (e.g., dropout, L1/L2 regularization), and architectural modifications (e.g., residual connections) are employed to stabilize training, encourage better generalization, and reduce computational load.
To learn more about overfititing: https://brainly.com/question/5008113
#SPJ11
what protocol simplifies multicast communications by removing the need for a router to direct network traffic?
Answers
The protocol that simplifies multicast communications by removing the need for a router to direct network traffic is the Internet Group Management Protocol (IGMP).
IGMP is a network-layer protocol that enables hosts to join and leave multicast groups on an IP network. It allows multicast traffic to be efficiently delivered to multiple recipients without burdening the network with unnecessary traffic.
Here's how IGMP simplifies multicast communications:
1. Host Membership: When a host wants to receive multicast traffic, it sends an IGMP join message to its local router. This message indicates that the host wants to join a specific multicast group.
2. Router Query: The local router periodically sends IGMP queries to all hosts on the network to determine which multicast groups they are interested in. The queries are sent to the multicast group address and require a response from the hosts.
3. Host Report: If a host is interested in a particular multicast group, it responds to the IGMP query with an IGMP report message. This report informs the router that the host wants to receive multicast traffic for that group.
4. Traffic Forwarding: Once the router receives IGMP reports from interested hosts, it knows which multicast groups to forward traffic to. The router then delivers the multicast traffic to the appropriate hosts without the need for additional routing decisions.
By using IGMP, multicast communications become more efficient and simplified. The protocol ensures that multicast traffic is only delivered to hosts that are interested in receiving it, reducing unnecessary network traffic and improving overall performance.
In summary, the Internet Group Management Protocol (IGMP) simplifies multicast communications by allowing hosts to join and leave multicast groups and by enabling routers to deliver multicast traffic directly to interested hosts without the need for additional routing decisions.
Read more about Multicast at https://brainly.com/question/33463764
#SPJ11
use the words from the list to complete the sentences about RAM and ROM..........( ROM, RAM and video cards) _______ are memory chips which run the software currently in use. _______loses its contents when the power is removed. ________stores info which needs to be permanent and does not lose its content when the power is removed
Answers
Answer:
RAM are memory chips which run the software currently in use.video cards loses its contents when the power is removed. ROM stores info which needs to be permanent and does not lose its content when the power is removed
Explanation:
Which MLA web source citations are formatted correctly? Check all that apply.
Wolfson, Elijah. “Newsweek Names a Mars Crater.” Newsweek. Newsweek, 28 Feb. 2014. Web. 1 Mar. 2014.
Herman, Barbara. “Where’s the Fire?” Newsweek. Newsweek, 24 Oct. 2013. Web. 25 Feb. 2014.
Niesen, Joan. “Learning to Cope: Disabled Vet Hunt Finds Freedom as Paralympic Skier.” Sports Illustrated. Web. 27 Feb. 2014.
A Mighty Girl. N.p., n.d. Web. 26 Feb. 2014.
Kloc, Joe. “Kepler Mission Finds Hundreds More Planets.” 2 Feb. 2014. Web. 25 Feb. 2014.
Answers
Answer:
Explanation:
A,B on exp.

The correct MLA web source citations are:
Wolfson, Elijah. “Newsweek Names a Mars Crater.” Newsweek. Newsweek, 28 Feb. 2014. Web. 1 Mar. 2014.Others are:
Herman, Barbara. “Where’s the Fire?” Newsweek. Newsweek, 24 Oct. 2013. Web. 25 Feb. 2014. What is MLA citation?MLA in-text citation style is known to be a citation method that is often used in citing authors. Her one often uses the author's last name and the page number from where the work is taken from.
A good example of this MLA web source citations is:
Wolfson, Elijah. “Newsweek Names a Mars Crater.” Newsweek. Newsweek, 28 Feb. 2014. Web. 1 Mar. 2014.Learn more about MLA web source from
https://brainly.com/question/26110488
#SPJ2
In a word processing document, describe the changes you think you need to make to your code. Then make these changes in your code and save your file to your computer again. Name it Rectangles 3.
Answers
Answer:
Open (and close) the writer application.
Open one or several documents.
Create a new document.
Save a document to a location on a drive.
Save a document to different formats.
Work with multiple documents.
Use available Help functions.
Close a document.
Do you like PC? Why? (I need your opinion for research)
Answers
Answer:
I do prefer a PC over a MacBook or other computers because you can customize the hardware and make it bette ring your own way unlike a MacBook where it’s all a secret and you can’t even try to pry it open and if you do the computer would stop working. You can customize your own features to make it better in your own way. A PC is pretty basic to use but the bad thing is that since the systems are most likely not protected, then many hackers/viruses could get in.
what type of data visualization technique allows analysts to extract information
Answers
The type of data visualization technique allows analysts to extract information is interactive dashboard
What is interactive dashboard?Data is presented visually in interactive dashboards using graphs, charts, and other visual elements, enabling analysts to explore and evaluate the data in a fluid and natural way.
Data can be filtered, details can be drilled down into, and different data transformations or calculations can be applied by analysts as they engage with the dashboard.
Through interaction, they can find patterns, trends, and links in the data, spot outliers or anomalies, and gain insightful knowledge that can guide decision-making.
Learn more about dashboard at: https://brainly.com/question/30167063
#SPJ4
Write a Python program for a calculator. Your program should present a calculator same as following picture in button arrangement and features.
It needs to be able to carry out addition, subtraction, division and multiplication.
It needs to be able to handle positive and negative numbers.
It needs to be able to accept integers and floating point numbers.
Clear button is to clear the screen during calculation or after the calculation. When this button is pressed, windows needs to be cleaned as in the above picture.
For all buttons (numbers and functions), you will need to use Lambda functions.
All buttons need to be placed exactly same as above picture.
Entire Calculator size and button size should be larger than the picture since it was reduced to display without taking up too much space.
You will need to use several functions.
Make sure to provide proper comments for the program.
Windows color needs to be different than button or frame color.
Frame color and button color needs to be different.
Only use tkinter package.
Do not create a class for it.
Only use functions for it.
Answers
The algorithm for the calculator program that would help you write the python program is:
The AlgorithmImport the tkinter package.
Define a function button_click to handle button clicks.
Create a window using tkinter.
Create a screen using tkinter and bind it to a StringVar.
Create a screen entry field in the window.
Create a frame for the buttons.
Define the texts for the buttons.
Iterate through the button texts and create buttons in the frame.
Bind the button_click function to the button clicks.
Run the window's event loop using tkinter.
This algorithm outlines the steps required to create a calculator program using tkinter.
Read more about algorithms here:
https://brainly.com/question/13902805
#SPJ4
Someone help please I really need help

Answers
Answer:
Smallest value;
\(f(x) = { \sf{MIN}}(value)\)
Largest value;
\(f(x) = { \sf{MAX}}(value)\)
Jairo is shopping for a new pair of shoes online and has found four online stores that sell the shoes. He opens them all up in different browser tabs and begins the checkout process so that he can find out what the final price (with shipping and taxes) will be and decide if any of the websites aren't legitimate.
Answers
Answer:
The store that asks for his name, drivers license number, credit card number, and address in the checkout form.
Explanation:
An online store should not need his drivers license number to charge his credit card and ship a product to him. It is suspicious that they are asking for that information, especially since that PII can be used for identity fraud.
Distributed Program Environment: We examine Centralized vs. Decentralized networks. The Centralized model perhaps exists in one ph al location, and perhaps on one physical hardware device. This isolation can damper sharing resources. Alternative, Decentralized network could perhaps expand physical locations, and perhaps separat, services such as network server, user devices, web server, database server, disk file storage, etc so that no one person no one machine would bring the environments down. True O False QUESTION 2 A Guest operating system is the hardware's primary bootup operating system, while the Host operating system is the application virtual machine emulation simulating an operating system True O False QUESTION 3 Possible Multiple Answer Question Pick all which apply The cornerstones of system programming in Linux The majority of Unix and Linux code is still written at the system level in C and C++ System Calls O C Library O Compiler Machine Language
Answers
Centralized vs. Decentralized networks Distributed Program Environment is a type of computing environment where resources and components are spread across different locations in a network or on the internet. In distributed programming, it is common to compare centralized vs. decentralized networks.
Centralized networks have their resources and components located at one physical location, and often times on one physical hardware device. In such an environment, sharing of resources may be limited because it is isolated. Decentralized networks, on the other hand, have their resources and components spread across different physical locations and separated services such as network server, user devices, web server, database server, disk file storage, etc.,
So that no one person or machine can bring the environment down. In such an environment, sharing of resources is enhanced and it is more resilient to component or resource failures.
To know more about Program visit:
https://brainly.com/question/18763374
#SPJ11
Choose the words that complete the sentences.
A_______
is used to edit raster images.
A_______
is used to edit vector images.
A_______
is used to control a scanner or digital camera.
Answers
Answer:
A paint application
is used to edit raster images.
A drawing application
is used to edit vector images.
A digitizing application
is used to control a scanner or digital camera.
Explanation:
got it right on edg
I need it completed in an excel file
3) Use Excel solver and Lingo to find the optimal solution and verify your answer.
3) Use Excel solver and Lingo to find the optimal solution and verify your answer.
A truck must travel from New Yor
Answers
A truck that is going from New York City to Los Angeles has to cross 4 loading stations, and the number of goods to be loaded at each station is provided.
The truck has a maximum carrying capacity of 4000 pounds. The objective is to determine the optimal solution for this scenario. To determine the optimal solution, we can use Excel solver and Lingo.To start with, we will set up an Excel spreadsheet with the available information in the following order:Loading Station (i) Pounds to be loaded (j) Shipping cost ($/lb) (cij)1 700 0.042 2 800 0.039 3 1100 0.047 4 600 0.040Using Excel solver, we can solve for the optimal solution. To do this, follow the below steps:In the Excel file, click on Data, then Solver, and add the following parameters:Set objective: MinimizeShipping Cost ($/lb)Change variable cells: Pounds to be loaded ($/lb)Subject to: Maximum carrying capacity of the truck = 4000 poundsEnsure that the "Simplex LP" algorithm is selected. Click OK. The solution can then be obtained and verified in the Excel Solver and Lingo.The optimal solution, according to the model, is to load 1100 pounds of goods at loading station 3 and 2900 pounds at loading station 4. The total cost of shipping will be $116.2. Therefore, the optimal solution has been found by using Excel Solver and Lingo.
Learn more about spreadsheet :
https://brainly.com/question/1022352
#SPJ11
How do you find the width and height of an Oval in coding? (cmu)
Answers
Explanation:
MU Graphics is a persistent-object graphics package, meaning that it allows you to draw shapes on the screen using Python, and those shapes will stay on the screen until they are removed.
Here is an example. Click the green run button to draw a rectangle and circle. You can also change the code and run again to see your changes!
Shapes can be changed or interacted with by using the built-in event functions, like so.
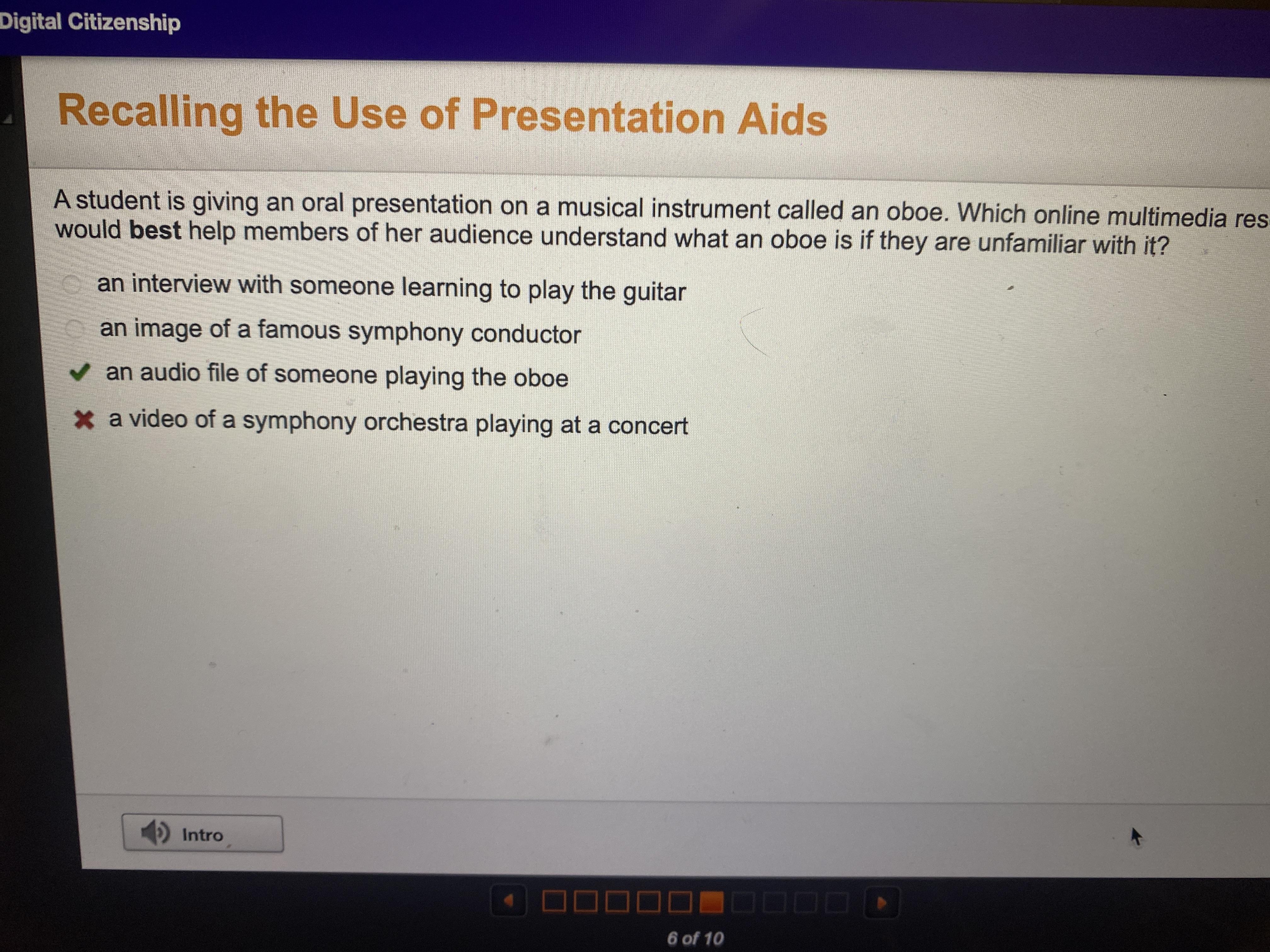
A student is giving an oral presentation on a musical instrument called an oboe. Which online multimedia resource would best help members of her audience understand what an oboe is if they are unfamiliar with it?.
Answers
The greatest way to explain an oboe to the audience is via an audio file of someone playing one.
What is Multimedia?
Contrary to traditional mass media, such as printouts or audio recordings, which contain little to no user participation, multimedia is a type of communication that combines several content formats, such as text, audio, photos, animations, or videos into a single interactive presentation. Audio slideshows, animated films, and video podcasts are a few common types of multimedia. The fundamentals of software, hardware, or other technologies, as well as their applications in interactive communication, are all included in multimedia.
To know more about multimedia
https://brainly.com/question/24138353
#SPJ4
Answer:
C!!!
Explanation:
I need help!
A standard is a:
A. normal way of addressing business letters.
B. level of quality or performance that people accept as normal.
C. a document with specific rules and regulations.
D. set unit of measurement for a particular purpose.
Answers
Explanation:
The answer is B. level of quality or performance that people accept as normal
Answer:
A standard is a: level of quality or performance that people accept as normal.
Explanation:
Just did this and got it correct.
A.What is the maximum core diameter for a fiber if it is to operate in single mode at a wavelength of 1550nm if the NA is 0.12?
B.A certain fiber has an Attenuation of 1.5dB/Km at 1300nm.if 0.5mW of Optical power is initially launched into the fiber, what is the power level in microwatts after 8km?
Answers
The maximum core diameter for the fiber to operate in single mode at a wavelength of 1550nm with an NA of 0.12 is approximately 0.0001548387.
To determine the maximum core diameter for a fiber operating in single mode at a wavelength of 1550nm with a given Numerical Aperture (NA), we can use the following formula:
Maximum Core Diameter = (2 * NA) / (wavelength)
Given:
Wavelength (λ) = 1550nm
Numerical Aperture (NA) = 0.12
Plugging these values into the formula, we get:
Maximum Core Diameter = (2 * 0.12) / 1550
Calculating the result:
Maximum Core Diameter = 0.24 / 1550
≈ 0.0001548387
Know more about Numerical Aperture here:
https://brainly.com/question/30389395
#SPJ11
Write a function that can find the largest item in the array and returns it. The function takes the array as an input. From the main function, send initial address, type and length of the array to the function. You can use registers to send the data to the function. Also return the largest item in the array using EAX register. You can use the following array for this problem. Array DWORD 10, 34, 2, 56, 67, -1, 9, 45, 0, 11
Answers
Answer:
var newArray = array.OrderByDescending(x => x).Take(n).ToArray();
Explanation:
Write the find_index_of_largest() function (which returns the index of the largest item in an array). Eg: a = [1 3 5 2 8 0]; largest = find_index_of_largest ( a ); largest = 5; Question: Write the
Where is a Pivot Table inserted?
a. Next to the last column of data in your worksheet
b. Below the last row of data in your worksheet
c. It depends on whether you select to insert the Pivot Table in the current worksheet or a new worksheet
d. Above the first row of data in your worksheet
Answers
The Create PivotTable dialog box will prompt you to create a Pivot Table on an Existing Worksheet if you insert one on a data-filled worksheet. One of the options in the Create PivotTable dialog box is this one.
Utilized in spreadsheet applications like Excel, OpenOffice.org Calc, and Ggle Sheets is a data summarization tool called a pivot table. Sorting, counting, and totaling data in a table are its primary uses. In order to create a report, you can summarize the data in a variety of ways using a pivot table.
The dialog box for "Create PivotTable":
In Excel, a new pivot table can be created using the dialog box labeled "Create PivotTable."
Learn more about PivotTable at
brainly.com/question/18410166
#SPJ4
what is this called?

Answers
Answer:
Fender Champion 40
Explanation:
....
..
What are three risks of developing a strategic role for information systems ?
Answers
Answer:
The strategic role of information systems is to enhance the image of information Services in an organization. ... Strategic information systems are developed in response to corporate business initiative and they are intended to give competitive advantage to the organization.
The risks of developing a strategic role for information systems are:
Hardware and software failure.Malware.Viruses.What are the threats to IT systems and data?Note that hardware and software failure can lead to power loss or it is one that can corrupt data corruption.
Note also that malware and viruses can disrupt computer operations and as such, they are the risks of developing a strategic role for information systems.
Learn more about malware from
https://brainly.com/question/399317
#SPJ2
An attacker installs trojan malware that can execute remote backdoor commands, such as the ability to upload files and install software to a victim pc. what type of trojan malware is this?
Answers
The attacker has installs trojan malware that can execute remote backdoor commands called the Remote Access Trojan (RAT).
What is Remote Access Trojan (RAT)?This is known to be a worm that is often written in VBS, and it is one that do makes it hard to see on Windows machines and it is one that makes the attacker to have total control over a machine and also they send data back to their server.
Hence, The attacker has installs trojan malware that can execute remote backdoor commands called the Remote Access Trojan (RAT).
Learn more about trojan malware from
https://brainly.com/question/11831402
#SPJ1
how many bits would be needed to count all the students in class today
Answers
Answer:
5 bits
Explanation:
Most classes have around 20 student with a 5-bit system goes up to 31 ( 1+2+4+8+16) and a 4-bit system(1+2+4+8) goes up to 15. Bits are the 1s and 0s and so a 5-bit system looks like this: 01001(18).
Spend some time exploring the components inside of a computer by performing online research into the topic. You can begin with this link, What does the inside of a computer look like?, and then continue to explore other websites of your own finding to answer the questions below, if needed.
How do you think the computer components would change if you were looking at a tablet computer or a smartphone?
What is one major component that would not be found in a tablet or phone, and how has modern computing made that component less important?
What component is in a tablet or phone that wouldn’t have been in a desktop (remember, you can search online for ideas)?
Answers
Answer:
1. Chassis (case)
Data cable: (IDE, SATA)
Disc drive: CD-ROM, CD-RW, DVD-ROM, or Blu-ray.
Expansion card (ISA, PCI, AGP, and PCI Express).
Fan (Heat sink)
Floppy drive
Hard drive: HDD, SSD
Memory (RAM)
Motherboard
Power cable (Molex)
Power supply (PSU)
Processor (CPU)
The expansion cards are often devices such as your video card, sound card, network card, etc.
It is common for a computer today to have these components built into the motherboard, also referred to as integrated components.
Network card
Sound card
Video card
What parts are needed for a computer to work?
CPU (processor)
Memory (RAM)
Motherboard
Storage device (e.g., hard drive)
2. Smartphones and tablets have less storage capacity than a computer, and their components cannot be modified like a desktop computer's can. Desktop and laptop computers can run more powerful software than a smartphone or tablet due to their size, components, and less restrictive power requirements.
3. A hard drive
Since tablets and phones are compact, they are better off not having a big, giant, bulky storage device like hard drives. Modern computing made hard drives less important by developing Solid-State Drives (SSDs) and extremely dense (512 bit) storage that can provide the same if not more storage than a traditional hard drive at the fraction of the size.
4. Since tablets and phones are mobile devices, they would be outfitted with a GPS (Global Positioning System) so that location services would work with them. Desktops do not usually have GPS components.
Explanation: / \
I already explained up above. |
The parts that are needed for a computer to work are:
CPU (processor)Memory (RAM)MotherboardStorage device (e.g., hard drive)What is a computer?A computer is an electronic device for storing and processing data according to instructions given to it in a variable program.
It is common for a computer today to have these components built into the motherboard, also referred to as integrated components.
Desktop and laptops can run more powerful software than a smartphone due to their size, components, and less restrictive power requirements.
Learn more about computer on:
https://brainly.com/question/24540334
#SPJ2
tiền tệ ra đời là kết quả
Answers
bruuh, wht is this man saying