After a new technology is purchased, what are some additional costs that must be incorporated into an upgrade budget?
Answers
Answer:
Depends
Explanation:
If corprate then education,
if home then premium software,
if school educational software.
HOPE THIS ANWSERS YOUR QUESTION
IF NOT, MESSAGE ME!
Related Questions
How to unlock your iphone when you forgot the password?.
Answers
Answer:
go to customer service
Explanation:
1. Create a naive Bayes model for this data set.
2. What prediction will the naive Bayes model return for the query q=(1,0,0)?
Answers
Answer:
import the GaussianNB class from the scikit-learn naive bayes module using the import statement;
from sklearn.naivebayes import GaussianNB
create the classifier,
clf = GaussianNB()
Then train or fit a section of the dataset (the training set) with the classifier, then predict the label of the test section of the dataset with the provided query "q".
trained = clf.fit( train_features, train_label)
predict = clf.predict(q)
Explanation:
The scikit-learn is a machine learning package in python used to create machine models from datasets. It has several classifiers and regressions algorithms.
The naive baye algorithm is a machine learning class in python used in supervised machine learning to create models used to predict a label given a set of features using a classifier.
A convened IRB Committee approved a protocol as a more than minimal risk study on February 15, 2019. In 2020, the study remains open to enrollment with 14 subjects currently enrolled and receiving the intervention. Which of the following best describes IRB continuation review requirements for this study?
O The research must be re-reviewed by the convened IRB on or before February 14, 2020.O The research must be re-reviewed by the convened IRB on or before February 14, 2018.O The research must be re-reviewed by the convened IRB on or after February 14, 2020.
Answers
The right response is: The convened IRB must reevaluate the research on or before February 14, 2020.
When should IRB ongoing review take place? What is it?What does Ongoing Review entail? You must submit a study to the IRB for continuing review permission if you want to keep working on it after its expiration date. The IRB conducts a fresh evaluation of the trial to decide whether it should proceed unaltered or with changes.
What day did the IRB approve?The date of IRB approval is the day the requested revisions are confirmed by the Chair, Vice Chair, or his/her designee when the research study is approved subject to amendments at a convened meeting.
To know more about response visit:-
https://brainly.com/question/28563302
#SPJ1
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
in chapter 4, we learn about several types of loops. describe specifically with an explanation and code example when it is appropriate to use: a for loop a while loop a do-while loop
Answers
In chapter 4, we learn about several types of loops and each has its sever use case.
A for loop is appropriate when you know the number of iterations you want to perform. It's commonly used for iterating over arrays or several. The syntax of a for loop looks like this:
```
for (initialization; condition; update) {
// code block to be executed
}
```
Here's an example of a for loop that iterates through an array:
```
const myArray = ['apple', 'banana', 'orange'];
for (let i = 0; i < myArray.length; i++) {
console.log(myArray[i]);
}
```
A while loop is appropriate when you don't know how many iterations you'll need to perform, and the loop continues until a condition is met. The syntax of a while loop looks like this:
```
while (condition) {
// code block to be executed
}
```
Here's an example of a while loop that keeps generating random numbers until it reaches a number greater than 0.5:
```
let randomNumber = 0;
while (randomNumber <= 0.5) {
randomNumber = Math.random();
console.log(randomNumber);
}
```
A do-while loop is similar to a while loop, but it executes the code block at least once before checking the condition. It's appropriate when you want to ensure that the code block runs at least once. The syntax of a do-while loop looks like this:
```
do {
// code block to be executed
} while (condition);
```
Here's an example of a do-while loop that prompts the user for a number until they enter a valid number:
```
let userNumber;
do {
userNumber = prompt('Enter a number:');
} while (isNaN(userNumber));
```
In summary, a for loop is appropriate when you know the number of iterations, a while loop is appropriate when you don't know how many iterations, and a do-while loop is appropriate when you want to ensure that the code block runs at least once.
Learn more about initialization here:
https://brainly.com/question/15396694
#SPJ11
Select the correct answer.
Ben wants to keep similar items close to each other in the image he is working on. Which is the most effective technique for applying the gestalt
concept of proximity?
The BLANK technique is the most effective technique for applying the gestalt concept of proximity.
Answers
Gestalt Principles are principles/laws of human perception that describe how humans group similar elements, recognize patterns and simplify complex images when we perceive objects.
What are the Gestalt Principles?The tendency to view items as belonging to the same grouping when they are close to one another is known as the gestalt principle of
proximity
. It claims that regardless of how different the forms and sizes are from one another, if shapes are close to one another, you will perceive them as groups. One of Gestalt's principles, the concept of closeness focuses on how each stimulus would be seen in its most basic form. The
Law of Simplicity
or the Law of Pragnanz are other names for it. It is founded on the idea that the sum of a thing is worth more than the sum of its components.
To learn more about Gestalt Principles refers to;
https://brainly.com/question/4734596
#SPJ1
(HELP!!!) Which of the following is true about a low-level language?
Select two answers:
Difficult for machines and humans to parse
Relatively easy for humans to write
Less readable by humans than other languages
Guaranteed to be unambiguous
Answers
Answer:
d and b i think
Explanation:
sorry if im wrong :l
Answer:
A and B
Explanation: It's on google if you do your research.
the term that describes when an action is taken to a dataset that results in a new dataset being created is:
Answers
The term that describes when an action is taken to a dataset that results in a new dataset being created is "data transformation".
Data transformation refers to the process of converting data from one format, structure, or type to another. This process involves a range of activities such as cleaning, filtering, sorting, aggregating, and merging data to create a new dataset that is better suited for analysis, reporting, or visualization purposes. Data transformation is an essential step in data management and analysis as it helps to ensure that the dataset is accurate, complete, and consistent. It also helps to enhance the quality and usefulness of the dataset by making it easier to understand and interpret. For example, if you have a dataset containing sales data for a particular product, you may want to transform the data by aggregating it by month, year, or region to get a better understanding of sales trends over time or across different locations.
In conclusion, data transformation is a crucial process in data management and analysis, and it involves taking an action to a dataset that results in a new dataset being created. This process helps to improve the quality and usefulness of the dataset by converting it into a format that is better suited for analysis, reporting, or visualization purposes.
Learn more about visualization here: https://brainly.com/question/23995556
#SPJ11
What does this mean
Don't use such phrases here, not cool! It hurts our feelings :(
Answers
what type of software controls the internal operations of the computer’s hardware?
Answers
The type of software that controls the internal operations of a computer's hardware is known as the operating system (OS).
The operating system acts as an intermediary between the hardware and the software applications running on the computer.
The operating system is responsible for managing various hardware components, such as the central processing unit (CPU), memory, storage devices, input/output (I/O) devices, and network connections.
It provides the necessary services and functions to ensure efficient and coordinated operation of the hardware resources.
The OS performs several key functions:
1. Process Management: The OS manages the execution of processes or programs, allocating CPU time, scheduling tasks, and handling process synchronization and communication.
2. Memory Management: It oversees the allocation and deallocation of memory resources, ensuring that programs and data have the necessary memory space for execution.
3. File System Management: The OS manages the organization, storage, and retrieval of files and directories on storage devices, such as hard drives or solid-state drives.
4. Device Management: It controls the interaction with input and output devices, such as keyboards, mice, printers, and displays, by providing device drivers and handling device interrupts and communication.
5. User Interface: The operating system provides a user interface that allows users to interact with the computer, either through a command-line interface (CLI) or a graphical user interface (GUI).
Common examples of operating systems include Windows, macOS, Linux, and Unix. Each operating system has its own specific features, functionality, and compatibility with different hardware architectures.
In summary, the operating system is the crucial software component that controls and manages the internal operations of a computer's hardware, ensuring the efficient execution of software applications and providing an interface for users to interact with the system.
Learn more about software:
https://brainly.com/question/28224061
#SPJ11
(Maximum 400 words) Describe how this period of Coronavirus (COVID-19) will influence and affect the STEM (Science, Technology, Engineering, and Mathematics) fields.
Answers
The period of coronavirus will have both negative and positive impacts on STEM fields.
However, the STEM (Science, Technology, Engineering, and Mathematics) fields have shown significant changes and impacts.
Here is how this period of COVID-19 will affect the STEM fields.
1. Technology
The current situation has increased the use of technology in various fields. Remote work and online meetings are becoming more popular, and this has led to increased technology usage. Technological advancements are expected in the future, leading to new business models that are more efficient.
2. Biomedical research
The COVID-19 pandemic has sparked the need for more biomedical research and led to an increase in research funding. Scientists are researching vaccines, treatments, and diagnostic tools, which is expected to lead to a better understanding of viruses and other infectious diseases.
3. Education
The pandemic has affected the education system globally, with many institutions closing and students learning from home. Teachers and educators are now incorporating technology in teaching, and the pandemic has accelerated the adoption of e-learning platforms. This has led to the development of new ways to learn and teach, and new online learning platforms are expected to emerge in the future.
4. Engineering
The pandemic has led to an increase in demand for essential supplies such as ventilators, personal protective equipment (PPE), and other medical devices. This has led to the development of new designs and manufacturing processes that are more efficient. The need for innovation has also led to the development of new solutions, such as 3D printing of medical supplies.
5. Mathematics
Mathematical models are used to understand the transmission of diseases, and the COVID-19 pandemic has led to the development of new models to understand the spread of the virus. These models help policymakers and public health officials make decisions to control the pandemic.
In conclusion, the COVID-19 pandemic has impacted STEM fields significantly, leading to new developments and innovations. With increased technology adoption, biomedical research, e-learning platforms, and engineering, the STEM fields are expected to change and adapt to the new normal. It is crucial to keep up with these changes and find ways to take advantage of the opportunities presented by the pandemic.
learn more about STEM fields here:
https://brainly.com/question/30082530
#SPJ11
Why would a user want to resend a message? Check all that apply.
O to include new recipients
D to include a forgotten attachment
D to force recipients to read the message immediately
D to respond to a request from a recipient who accidentally deleted it
O to include missing information
O to require recipients to respond to a read receipt
Answers
Answer:
A
B
D
E
Explanation:
O to include new recipients
D to include a forgotten attachment
D to respond to a request from a recipient who accidentally deleted it
O to include missing information
Answer:
He's right its A, B, D and E
Explanation:
What underlying consept is edge computing based on?
Answers
Edge computing is based on the underlying concept of decentralization of data processing.
This means that instead of all data being processed in a centralized location, such as a cloud data center, the data is processed closer to the source or "edge" of the network. This allows for faster processing and decision-making, as well as reduced latency and bandwidth usage. Edge computing is often used in applications such as the Internet of Things (IoT), where devices and sensors collect and process data in real-time.
By decentralizing data processing, edge computing allows for more efficient and effective use of resources and improves overall system performance.
Learn more about edge computing:
https://brainly.com/question/23858023
#SPJ11
Edge computing is based on the underlying concept of decentralization of data processing.
This means that instead of all data being processed in a centralized location, such as a cloud data center, the data is processed closer to the source or "edge" of the network. This allows for faster processing and decision-making, as well as reduced latency and bandwidth usage. Edge computing is often used in applications such as the Internet of Things (IoT), where devices and sensors collect and process data in real-time.
By decentralizing data processing, edge computing allows for more efficient and effective use of resources and improves overall system performance.
Learn more about edge computing:
brainly.com/question/23858023
#SPJ11
PC Shopping Network may upgrade its modem pool. It last upgraded 2 years ago, when it spent $115 million on equipment with an assumed life of 5 years and an assumed salvage value of $15 million for tax purposes. The firm uses straight-line depreciation. The old equipment can be sold today for $80 million. A new modem pool can be installed today for $150 million. This will have a 3 -year life, and will be depreciated to zero using straight-line depreciation. The new equipment will enable the firm to increase sales by $25 million per year and decrease operating costs by $10 million per year. At the end of 3 years, the new equipment will be worthless. Assume the firm's tax rate is 35 percent and the discount rate for projects of this sort is 12 percent. What are the Free Cash Flows, the NPV and IRR of the replacement project? Note: There is double jeopardy on this problem. If you miss a free cash flow, you will miss the NPV and the IRR. (6 points) FCF 0
= FCF 1
= FCF 2
= FCF 3
= NPV= IRR=
Answers
The replacement project involves upgrading the modem pool of PC Shopping Network. The old equipment was purchased 2 years ago for $115 million, has a 5-year assumed life, and a salvage value of $15 million.
The old equipment can be sold today for $80 million. The new equipment can be installed for $150 million and has a 3-year life. The new equipment is expected to increase sales by $25 million per year and decrease operating costs by $10 million per year. The tax rate is 35% and the discount rate is 12%. We need to calculate the Free Cash Flows (FCFs), the Net Present Value (NPV), and the Internal Rate of Return (IRR) of the replacement project.
To calculate the FCFs, we need to determine the cash inflows and outflows associated with the project. In this case, the cash inflows are the increase in sales ($25 million) and the decrease in operating costs ($10 million) each year. The cash outflows include the initial investment in the new equipment ($150 million) and the tax savings resulting from depreciation expense. By subtracting the cash outflows from the cash inflows for each year, we can calculate the FCFs.
The NPV of the project is the present value of the FCFs, discounted at the given rate of 12%. By summing up the present values of the FCFs, we can calculate the NPV. If the NPV is positive, the project is considered financially viable.
The IRR is the discount rate at which the NPV of the project becomes zero. It represents the project's internal rate of return or the rate of return that the project is expected to generate. The IRR is calculated iteratively until the NPV reaches zero.
To obtain the specific values of FCF0, FCF1, FCF2, FCF3, NPV, and IRR, the calculations need to be performed based on the given information and formulas for each year.
learn more about salvage value here
https://brainly.com/question/28387066
#SPJ11
An office building has two floors. A computer program is used to control an elevator that travels between the two floors. Physical sensors are used to set the following Boolean variables.
The elevator moves when the door is closed and the elevator is called to the floor that it is not currently on.
Which of the following Boolean expressions can be used in a selection statement to cause the elevator to move?
answer choices
(onFloor1 AND callTo2) AND (onFloor2 AND callTo1)
(onFloor1 AND callTo2) OR (onFloor2 AND callTo1)
(onFloor1 OR callTo2) AND (onFloor2 OR callTo1)
(onFloor1 OR callTo2) OR (onFloor2 OR callTo1)
Answers
The following Boolean expressions, "onFloor1 AND callTo2" or "onFloor2 AND callTo1," can be used in a selection statement to move the elevator.
The commands to move the lift may be simply determined based on the other commands designed to be provided and received by the lift, which indicate what operation it is engaged in.
When the elevator is on the first floor and has to be taken to the second floor, the order "onFloor1 AND callTo2" can be used. The order "onFloor2 AND callTo1" would serve as the reverse of the previously given instruction and cause the lift to operate in the exact opposite manner.
To know more about elevator visit:-
https://brainly.com/question/2168570
#SPJ4
Which option below is not a hashing function used for validation checks? RC4 MD5 SHA-1. CRC32.
Answers
The option that is not a hashing function used for validation checks is RC4. So, the first option is correct.
a) RC4: RC4 (Rivest Cipher 4) is a symmetric encryption algorithm, not a hashing function. It is commonly used for encrypting data, particularly in protocols like SSL and WEP. However, it is not typically used for validation checks or integrity verification of data.
b) MD5: MD5 (Message Digest Algorithm 5) is a widely used cryptographic hash function. It generates a 128-bit hash value known as a message digest. MD5 was commonly used for data integrity checks and password hashing.
However, it is now considered weak for cryptographic purposes due to vulnerabilities and collision attacks.
c) SHA-1: SHA-1 (Secure Hash Algorithm 1) is another widely used cryptographic hash function. It produces a 160-bit hash value and was commonly used for integrity checks and digital signatures. However, similar to MD5, SHA-1 is now considered weak and vulnerable to collision attacks.
d) CRC32: CRC32 (Cyclic Redundancy Check 32) is a checksum algorithm commonly used for error detection, particularly in data transmission and storage. While it is not a cryptographic hash function, it is often used for verifying data integrity and detecting accidental changes or errors.
So, the first option is correct.
Learn more about hashing function:
https://brainly.com/question/13149862
#SPJ11
The implementation of register forwarding in pipelined CPUs may increase the clock cycle time. Assume the clock cycle time is (i) 250ps if we do not implement register forwarding at all, (ii) 290ps if we only implement the EX/MEM.register-to-ID/EX.register forwarding (i.e., the case #1 shown on slide 12 in lecture note Session12.pdf), and (iii) 300ps if implement the full register forwarding. Given the following instruction sequence:
or r1,r2,r3
or r2,r1,r4
or r1,r1,r2
a) Assume there is no forwarding in this pipelined processor. Indicate hazards and add nop instructions to eliminate them.
b) Assume there is full forwarding. Indicate hazards and add nop instructions to eliminate them.
c) What is the total execution time of this instruction sequence without forwarding and with full forwarding? What is the speedup achieved by adding full forwarding to a pipeline that had no forwarding?
d) Add nop instructions to this code to eliminate hazards if there is EX/MEM.register-toID/EX.register forwarding only.
Answers
The addition of nop instructions or forwarding is necessary to eliminate data hazards and improve execution time in a processor pipeline.
a) Without forwarding, there will be data hazards between instructions 1 and 2, and between instructions 2 and 3. To eliminate them, we need to add nop instructions as follows:
1. or r1, r2, r3 2. nop 3. nop 4. or r2, r1, r4 5. nop 6. nop 7. or r1, r1, r2
b) With full forwarding, there will be no data hazards, so no need to add any nop instructions.
1. or r1, r2, r3 2. or r2, r1, r4 3. or r1, r1, r2
c) The total execution time without forwarding is 7 cycles * 250ps = 1750ps. With full forwarding, the execution time is 3 cycles * 300ps = 900ps. The speedup achieved by adding full forwarding is 1750ps / 900ps = 1.94.
d) With EX/MEM.register-to-ID/EX.register forwarding only, there is still a data hazard between instructions 1 and 2, and between instructions 2 and 3. To eliminate them, add nop instructions as follows:
1. or r1, r2, r3 2. nop 3. or r2, r1, r4 4. nop 5. or r1, r1, r2
Learn more about data here;
https://brainly.com/question/10980404
#SPJ11
at which point in interphase are cells officially committed to reproduction
Answers
The primary growth phase, or G1, is where regular development and metabolism take place. Here is where the restriction point is, forcing the cell into mitosis.
If a cell has advanced past this stage, it enters the S Phase, during which DNA replication takes place and the cell decides to divide.
Which interphase stage helps the cell get ready for reproduction?
Cells are getting ready to divide at the G1 stage. It subsequently enters the S phase, where the cell duplicates all of the DNA, to accomplish this. S stands for DNA synthesis, then.The information molecule is DNA. It contains information needed to create proteins, which are other big molecules.
Learn more about DNA :
brainly.com/question/16099437
#SPJ4
How can Mario complete his task without leaving the word application?
Answers
Answer:Use the Thesaurus feature to find a synonym of the word.
Explanation:i just got the same question.
Answer:Use the Thesaurus feature to find a synonym of the word.
Explanation:
what is the minimum time needed to distribute the file from server to 6 peers using client-server model.
Answers
The minimum time needed to distribute a file from a server to 6 peers using a client-server model is determined by the slowest network connection between the server and the peers.
The minimum time required to distribute a file from a server to 6 peers using a client-server model depends on the size of the file and the speed of the network connection.
Assuming all network connections have the same speed, the minimum time can be calculated as the file size divided by the network speed multiplied by the number of peers:
Time = File size / (Network speed * Number of peers)
For example, if the file size is 1 GB and the network speed is 100 Mbps, the minimum time required to distribute the file to 6 peers would be:
Time = 1 GB / (100 Mbps * 6) = 27 seconds.
Learn more about server to 6 peers here:
https://brainly.com/question/20912835
#SPJ4
Assuming zero transmission time for the HTML object, how much time (in msec) elapses from when the client clicks on the link until the client receives the object? (hint Note that 2 RTTHTP are needed to fetch the HTML object and don't forget DNS delay)
Answers
Assuming zero transmission time for the HTML object, the time that elapses from when the client clicks on the link until the client receives the object is 2RTT + DNS delay.
The 2 RTT HTTP are needed to fetch the HTML object. Therefore, the answer is 2RTT + DNS delay (in msec). This means that it will take 2 Round Trip Times (RTT) and DNS delay to fetch the HTML object from the server. The RTT is the time it takes for a packet to travel from the client to the server and back again.
The DNS delay is the time it takes to look up the IP address of the server that hosts the HTML object, using the domain name in the URL.
Learn more about zero transmission: brainly.com/question/30574835
#SPJ11
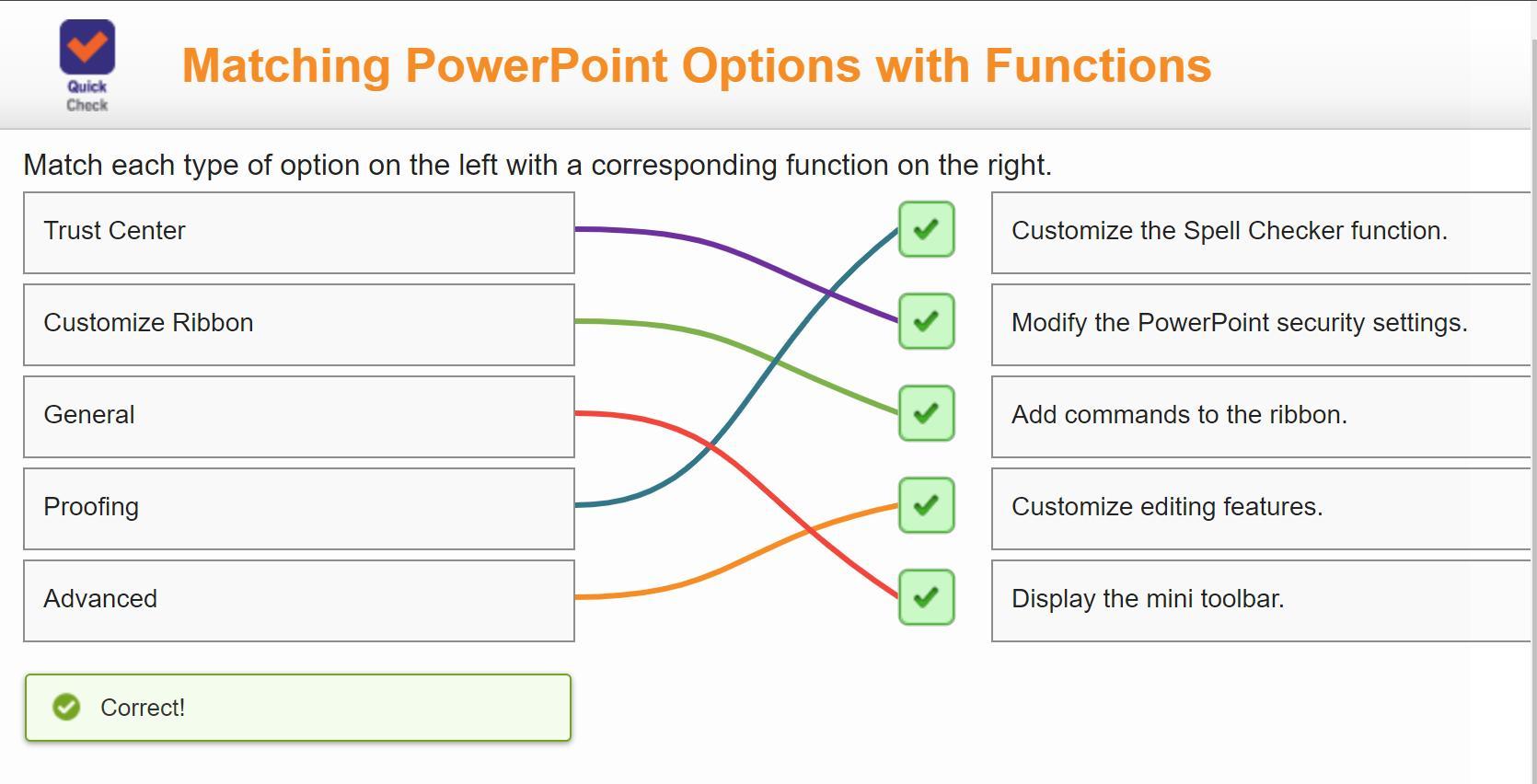
Match each type of option on the left with a corresponding function on the right.
Answers
Answer:
yes. the above is correct
Explanation: q posted
Answer: Anwer is correctly shown!!!!!!!!
Explanation:
HOPE IT HELPS Y'ALL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!

Write a function create_password() expects two parameters: pet_name (a string) and fav_number (an integer). The function returns a new password generated using the following pattern:
Answers
Answer:
Explanation:a
Symmetric encryption is also called secret key encryption. true or false?
Answers
Secret-key or single-key encryption are other names for symmetric encryption.
What is Symmetric Encryption?The easiest attack to counter is the ciphertext-only one. A brute-force strategy entails testing every key until the ciphertext can be deciphered and converted into plaintext.
Symmetric encryption is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic data. The entities communicating via symmetric encryption must exchange the key so that it can be used in the decryption process.
By using symmetric encryption algorithms, data is "scrambled" so that it can't be understood by anyone who does not possess the secret key to decrypt it.
Therefore, Secret-key or single-key encryption are other names for symmetric encryption.
To learn more about Symmetric encryption, refer to the link:
https://brainly.com/question/15187715
#SPJ1
Select the correct answer.
Nate is team lead at a firm. He uploads a file to a shared location. At the end of each week, all his team members update their tasks in this file.
What specific permission does each team member have?
OA View
ОВ.
read
OC change
OD
full control
Answers
Answer:
OC change i think..
Explanation:
EXPLAIN THE IMPORTANCE OF CREATING A POWERPOINT PRESENTATION AND HOW YOU COULD USE IT IN YOUR FUTURE CAREER
Answers
Answer: You could use this in real life because you might have a job and you might need to do a presentation for your work and presentations and powerpoints might help you remember things and stay organized.
Explanation:
There are many ways you can improve the performance of a website from an SEO perspective. When it comes to link building, which of the following statements is accurate?
a. The quantity of links is important, not the quality
b. The quality of links is important, not the quantity
c. Links hidden within code on sites improves your SEO performance
d. Links hidden within images on sites improves your SEO performance
Answers
The quality of links is important, not the quantity
Select the steps to use the Document Inspector.
1. Make sure you have saved your document.
2. Go to the
v tab on the ribbon.
3. Select
v in the Inspect Document section of the Backstage view.
4. From the drop-down menu, select
5. Check the boxes you want inspected and click OK.
6. If the Document Inspector finds issues, it will
Answers
Answer:
2. File
3. Check for issues
4. Inspect document
6.open a dialogue box with options
Explanation:
Answer on edge 2020
Answer:
the other guy is right!
Explanation:
Virtual teams _____.
Responses
that are cross-cultural, tend to produce better results than less diverse, single-location teams
that are cross-cultural, tend to produce better results than less diverse, single-location teams
are not suited to software development projects
are not suited to software development projects
are always cross-cultural, with a lot of diversity
are always cross-cultural, with a lot of diversity
can use asynchronous communication, but not synchronous communication
Answers
Virtual teams are always cross-cultural, with a lot of diversity.
Thus, A virtual team, sometimes referred to as a geographically dispersed team or a remote team, is a collection of individuals who communicate with one another online.
A virtual team typically consists of individuals from various locations. Since virtual teams communicate virtually, trust and effective communication are essential to their success.
A new product, information system, or organizational process may be developed by product development teams, which are made up of specialists from various regions of the world and diversity.
Thus, Virtual teams are always cross-cultural, with a lot of diversity.
Learn more about Virtual team, refer to the link:
https://brainly.com/question/31535713
#SPJ1
Approximately how many viewers watch the Super Bowl each year? How does the audience size compare to other television events?
Answers
Answer:
Ok
Explanation:
About 100 Million people watch the Super Bowl, both on tv and in stadium, most other events are watched by close to 20 Million is what Google says