Adele wants to extract a list of unique items in a database. Which of the following will she select in the series of clicks to do so: Select cell > Data tab > Advanced > Select option under Action (X) > Specify List range > Select a starting cell for copying to location > Check box beside Unique records only > OK
Answers
To extract a list of unique items in a database, Adele would select a cell, go to the Data tab, click Advanced, choose the action (X), specify the list range, select the destination, and check the Unique records only box.
To extract a list of unique items in a database, Adele would follow the series of clicks as outlined below:
a. Select a cell within the database.
b. Go to the "Data" tab in the toolbar.
c. Click on "Advanced" in the "Data Tools" group.
d. In the "Advanced Filter" dialog box that appears, select the option under the "Action" dropdown menu (X) that corresponds to "Copy to another location."
e. Specify the range of the list in the "List range" field. This would typically be the entire range of the database.
f. Select a starting cell for copying the unique records to in the "Copy to" field.
g. Check the box beside "Unique records only" to ensure that only unique items are extracted.
h. Click "OK" to initiate the extraction process.
By following these steps, Adele will be able to filter the database and create a new list that contains only the unique items from the original database.
To learn more about database visit :
https://brainly.com/question/31459706
#SPJ11
Related Questions
how to recall an email in outlook without recipient knowing
Answers
To recall an email in Outlook without the recipient knowing, follow these steps:
Open Outlook and navigate to the "Sent Items" folder.Locate and double-click on the email you wish to recall.Click on the "Actions" option in the top menu, and then select "Recall This Message."Choose either "Delete unread copies of this message" or "Delete unread copies and replace with a new message," depending on your preference.To avoid notifying the recipient, ensure the "Tell me if recall succeeds or fails for each recipient" option is unchecked.Click "OK" to initiate the recall process.Please note that the recall's success depends on several factors, such as the recipient's email settings and whether they have already read the email.
For more information about Outlook, visit:
https://brainly.com/question/24165533
#SPJ11
What is string literal in Java?
variable type that allows more than one character
group of printable characters enclosed within double quotation marks
group of printable characters enclosed within curly brackets
variable type that only allows for one character
Answers
Answer:
A string literal in Java is basically a sequence of characters from the source character set used by Java programmers to populate string objects or to display text to a user. These characters could be anything like letters, numbers or symbols which are enclosed within two quotation marks.
Explanation:
field value maximum storage size is defined by the field size property for the data types including short text, number, and ____________________ only.
Answers
The field value maximum storage size is defined by the field size property for the data types including short text, number, and date/time only.
In many database management systems, fields have a defined data type that specifies the kind of data that can be stored in that field. In addition to the data type, fields may also have a field size property that specifies the maximum number of characters, digits, or bytes that can be stored in that field.
The Date/Time data type also has a field size property that can be used to set the maximum storage size for date and time values, but the field size value has a slightly different meaning than it does for Short Text and Number fields. For Date/Time fields, the field size property determines the precision of the value that can be stored, rather than the maximum storage size.
To learn more about field size property visit : https://brainly.com/question/30454520
#SPJ11
Three of the following values could be stored as strings. When would you NOT use a
string command?
O To store a word.
O To store a list of colors.
O To store values NOT used for calculations.
O To store decimal values.
Answers
Answer:
To store decimal values
Explanation:
If values are not to be used for calculation, that is, they are not numerical data, therefore, some of them could be stored as strings. A string may contain any sequence of characters. The characters in a string may be repeated.
From the foregoing, decimals can not be stored as strings because in computer programming, a string is normally a sequence of characters, hence the answer above.
Using variable concepts, it is found that you would not use a string command to store decimal values.
---------------------------
Strings are used in programming to work with variables that are composed by text, which can include words, colors, and any variable that is not used for calculator.For decimal values, float and double variables are used, not strings, and thus, this is the option for which a string command would not be used.A similar problem is given at https://brainly.com/question/15583814
Write true or false:-
1. The start attribute always accept an integer value.
2. Description list is used to create a bulleted list.
3. The <DT> tag is used to create a table in HTML.
4. The <TR> tag is used to create cells in the table.
5. The VALIGN in attitude of the <TD> tag is used to Align the position of text in the cell vertically.
And please don't give only one answer, if you are giving, then please give all the answers.
Answers
Answer:
false
true
false
true
false
Explanation:
.
PLEASE HURRY 50 POINTS
Perform online research and find out the different types of spreadsheet software programs in use. Then, list their features, and identify the areas in which people use them.
Answers
Answer:
One part of Clare’s job at an environmental awareness organization is to answer the phone to collect donations. The table shows the number of hours she worked each week, , and the amount of donations in dollars, , that the organization collected each week for 10 weeks.
which computer belongs to the first generation?
Answers
when do you use an elif statement? group of answer choices to handle string values to check multiple expressions for true and execute a block of code as soon as one of the conditions evaluates to true. to end an if statement to input a variable
Answers
With the help of the Elif statement, you can test multiple expressions for true and have a block of code run whenever one of the conditions is true.
What is Elif statement?Multiple conditional expressions can be included after the if condition or in between the if and else conditions by using the Elif condition. If the provided condition evaluates to True, the Elif block is carried out.
Python uses the if-Elif-else statement to make decisions; that is, the program will assess a test expression and only run the remaining statements if the specified test expression is true. This makes it possible to validate numerous expressions.
Thus, with the help of the Elif statement, you can test multiple expressions for true and have a block of code run whenever one of the conditions is true.
To learn more about Elif statement, refer to the link below:
https://brainly.com/question/14994174
#SPJ1
there are methods that help measure application blank information by the degree to which the information differentiates between high- and low-performing individuals. this scoring methodology is called a(n
Answers
Answer: Weighted application blank
Explanation:
Which of the following statements is true regarding the relationship of engineers and technology? O a. None of these statements is true O b. Engineers must adopt the technological pessimism view Oc. Engineers must adopt a critical attitude toward technology O d. Engineers must adopt the technological optimism view
Answers
Technology read-ahead, technology free-ahead Sequential access is the process of accessing a collection of items in a predetermined, ordered manner, such as data stored on magnetic tape, in a disk file, or in a memory array.
None of the aforementioned technologies can optimize sequential access. It is the opposite of random access, which makes it possible to access any part of a sequence at any time and from any location with the same ease and efficiency.
For instance, sequential access may be the only means of accessing the data when it is stored on a tape. It could likewise be the favored admittance procedure, for example, assuming everything necessary is the deliberate handling of a progression of information pieces.
To know more about sequential access:
brainly.com/question/12950694
#SPJ4
Write a pseudocode to print the sum of first 10 terms in the series:
2, 4, 9, 16, 25…
Answers
Answer:
2,4,9,16,25,36,49,64,81, 110 , 121, 144
Please help for MAXIMUM POINTS!
Jarod’s boss sends him an e-mail about a task that she wants him to complete. In the email she asks that he collect the clothing size information of all 900 employees in his company and then place a branded clothing order with their supplier. After sending the email, his boss schedules a meeting with Jarod for the next day so that he can ask her any questions that he may have. What are four things that Jarod can do to ensure that he collects all the information he needs to do the task well?
Answers
How can you get to the Excel Function Reference information
Answers
Explanation:
To get detailed information about a function, click its name in the first column.
Note: Version markers indicate the version of Excel a function was introduced. These functions aren't available in earlier versions.
Answer:
Help tab
F1
searching in the tell me bar
A user doesn't want a website to know which of the website's webpages they visit. which action(s) can the user take to prevent the website from recording their browsing history along with any form of user identifier
Answers
Answer:
Take different forms of security.
Explanation:
These forms may be using a trusted VPN on a browser like Chromium, which is an open source version of chrome, using Operating systems like Linux, and using a search engine made for privacy, like duckduckgo.com. I hope this helps, although i think these are extreme measures.
what is computer generation
Answers
Answer:
Generation in computer terminology is a change in technology a computer is/was being used which includes hardware and software to make of an entire computer system .
HELP ME
what is the full form of BYE,AIDS,ASCC
Answers
50 points 3. Which of the following statements is true of phishing emails?
O A. They're important to keep.
B. They come from trusted sources.
C. They pretend to need information and use it for harm.
D. They're the same thing as junk mail.
Answers
Answer:
C. They pretend to need information and use it for harm
Explanation:
goog it
They pretend to need information and use it for harm. Therefore, the correct answer is option C.
Phishing is a form of cybercrime in which criminals use malicious emails and websites to try and extract sensitive information such as usernames, passwords, credit card numbers, and other personal information from unsuspecting victims. The criminals use this information for their own financial gain, either by stealing the victim's money or using the victim's identity to commit various other frauds. Phishing emails often appear to come from trusted sources and can use various tactics to try and convince the recipient to click on a malicious link or provide credentials. In contrast, junk mail or spam is just annoying and usually is not associated with malicious activities.
Therefore, the correct answer is option C.
Learn more about the Phishing here:
https://brainly.com/question/32858536.
#SPJ6
que significa DESFRAGMENTAR EL DISCO DURO?????
Answers
Answer:
DESFRAGMENTAR
Explanation:
es el proceso de reorganizar los datos almacenados en el disco duro para que los datos relacionados se vuelvan a juntar, todos alineados de manera continua.
5. What is bus? Explain its types
Answers
Answer:
A bus is a subsystem that is used to connect computer components and transfer data between them.
It's types are:-
•Address bus
Data bus.
Control bus.
Which Windows feature allows secure printing over the Internet?
Answers
Answer:
You need to install Windows 7 over an existing version of Windows.
Explanation:
Brainiest??
These icons cannot be removed from the Dock. Finder e-mail music player Trash
Answers
Answer:
Trash and Finder
Explanation:
There are, however, a couple of items that cannot be removed from the Dock–the Finder and the Trash.
What kind of computer are you most likely to find in
your home?
a. Mainframe
b. Supercomputer
c. Minicomputer
d. Microcomputer
Answers
The kind of computer that you are most likely to find in your home is a microcomputer. The correct option is D.
What are microcomputers?Microcomputers are computers that are small and easy to transport and use. So these computers can be used in houses and shops. They come with a box containing many other parts with a CPU. A keyboard and a mouse are also a part of the microcomputer.
Computers are of many sizes. They are huge, like a size of a room. They are called supercomputers. They are used for higher calculations, and they are used in factories and industries.
Mini computers are slightly smaller than supercomputers. They are cheaper than supercomputers and used for smaller works.
Thus, the computer used in homes are microcomputers. The correct option is D.
To learn more about microcomputers, refer to the link:
https://brainly.com/question/21219576
#SPJ2
when using the jira issue/filter macro to create multiple jira issues all at once, how must the issue names appear on a confluence page?
Answers
Select Insert > Jira Issue > Create new issue from the editor's menu. If you have more than one Jira site connected to Confluence, provide your server, project, issue type, summary, and description. Choose Insert.
Issue-specific dependencies should be displayed in your plan. Issues can be seen according to their current status as well as issues that you've made in your plan but haven't yet saved to Jira Software. Warnings — Only show problems with warnings. Select the "Issue Statistics" gadget from your dashboard by navigating there. Locate the stored filter, choose "Project" as the statistic type, and then save the filter. You should now have access to a list of all the projects' issues. Choose the first summary's text. Click the Jira symbol in the tiny menu that displays. Make sure the Jira project and ticket type are correct in the Create Task window, then select Create numerous problems from table.
To learn more about Jira site click the link below:
brainly.com/question/29987557
#SPJ4
"
Describe the framework of Green Operations in Information technology"
Answers
Green operations (GO) is a comprehensive concept that seeks to achieve environmental and social responsibility in IT companies' operations. The Green Operations framework was developed to assist IT companies in integrating environmental and social sustainability into their daily operations.
Green Operations in Information Technology (IT) refer to the creation of a digital environment that ensures environmental and social sustainability by increasing energy efficiency, reducing e-waste, and conserving natural resources. This system has been implemented to reduce IT's negative environmental impact and boost its economic and social sustainability. The Green Operations framework of IT consists of four stages:
Measure, analyze, and identify environmental and social risks and opportunitiesRedesign IT systems and procedures to meet environmental and social sustainability standardsImplement green operations programs and best practicesMonitor, assess, and report environmental and social sustainabilityIn conclusion, Green Operations are critical in enhancing environmental and social sustainability in IT companies. GO helps organizations decrease their environmental impact while also increasing economic efficiency. Companies are able to conduct environmentally sustainable operations through the Green Operations framework by integrating environmental and social considerations into daily business operations.
To learn more about Green operations, visit:
https://brainly.com/question/31232761
#SPJ11
Cuá es la relación entre la tecnología y la vida?
Answers
Answer:
La innovación tecnológica ha permitido que la humanidad avanzara sobre la base de disponer de unas prótesis más potentes en el divagar por la tierra
Explanation:
Hola! Dicho esto en el mundo en que vivimos hoy en día hemos podido con la tecnología inventar cosas que nos ayudan con nuestras vidas cotidianas como son los medios de comunicación, transporte, entre otros. Y para terminar de contestar la pregunta como tal pues sería algo como:
"La relación entre la tecnología y la vida es que la tecnología ayuda al ser humano en diferentes áreas tales como el transporte y la comunicación que hoy en día son un punto clave para poder vivir mejor."
¡Espero que te haya ayudado mucho!! ¡Bonito día!
What are three social
responsible as it relates to computer ethies
Answers
PLEASE HELP I DONT HAVE TME

Answers
9514 1404 393
Answer:
(d)
Explanation:
The cell reference to pi in D3 must be absolute ($D$3), and the value of the radius in A2 must be cubed (A2^3). The product of these must be multipied by 4/3. The only choice with these correct is the last choice.
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
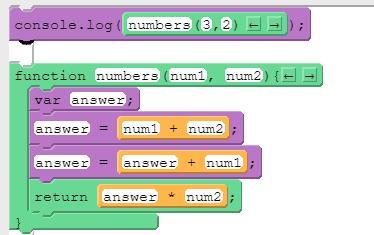
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
Which curve is mostly used to characterize technology growth process? A S-curve An exponential curve A 45 degree straight line A Bell curve
Answers
The S-curve is the curve that is most commonly used to characterize the technological growth process.
An S-curve is a curve that is characterized by a rapid increase in growth at the beginning, followed by a leveling off or saturation at a certain point. The rate of growth slows down as it approaches its limits. It is a common way to represent the growth of a variety of phenomena, including technological growth.A technological advancement can start slowly, then speed up as more researchers become interested in it and funding becomes more accessible. However, it will eventually reach its peak, at which point it will slow down. A few technological advancements may also experience a plateau in their growth before becoming obsolete.A Bell curve is used to represent the normal distribution of data, an exponential curve represents exponential growth, and a 45-degree straight line represents constant growth. Therefore, the curve that is most commonly used to represent the technological growth process is the S-curve.
Learn more about S-curve here :-
https://brainly.com/question/28333332
#SPJ11
When it is sunny, joe's ice cream truck generates a profit of $512 per day, when it is not sunny, the
profit is $227 per day, and when the truck is not out there selling ice cream, joe loses $134 per
day. suppose 8% of a year joe's truck is on vacation, and 82% of a year the truck is selling ice
cream on sunny days, what is the expected daily profit the truck generates over a year? enter your
answer as a decimal number rounded to two digits after the decimal point.
Answers
The expected daily profit of Joe's ice cream truck over a year is approximately $431.82.
To calculate the expected daily profit of Joe's ice cream truck over a year, we'll use the weighted average of profits for each scenario:
Expected daily profit = (percentage of sunny days * profit on sunny days) + (percentage of non-sunny days * profit on non-sunny days) + (percentage of vacation days * loss on vacation days)
First, we need to find the percentage of non-sunny days, which is the remaining percentage after subtracting sunny days and vacation days: 100% - 8% - 82% = 10%
Now, we can plug in the numbers:
Expected daily profit = (0.82 * $512) + (0.10 * $227) + (0.08 * -$134)
= ($419.84) + ($22.70) + (-$10.72)
= $431.82
To know more about profit visit:
brainly.com/question/27980758
#SPJ11