according to the zippo standard, websites that provide information but do not provide the opportunity to conduct online transactions are deemed to be passive and do not create personal jurisdiction over the defendant company that operates the site.
Answers
According to the zippo standard, websites that provide information but do not provide the opportunity to conduct online transactions are deemed to be passive and do not create personal jurisdiction over the defendant company that operates the site is false.
What does the Zippo case represent?A 1997 ruling with the iconic Internet case name Zippo Manufacturing Company v. Zippo Dot Com, Incorporated seemed to provide some solace in that environment. This choice created the categories of active, passive, and interactive Internet activity.
An "active" defendant is one who consciously uses the Internet extensively, such as when it signs contracts with citizens of another country that require frequent transmission of computer files over the Internet.
Therefore, the Zippo" Websites can be rated using Zippo's "continuum," or sliding scale, and are divided into one of three groups: either passively, actively, or as an inherent part of the defendant's enterprise.
Learn more about transactions from
https://brainly.com/question/1016861
#SPJ1
See full question below
according to the zippo standard, websites that provide information but do not provide the opportunity to conduct online transactions are deemed to be passive and do not create personal jurisdiction over the defendant company that operates the site. true or false
Related Questions
Which kind of file would be hurt most by lossy compression algorithm
Answers
Answer:
Answer is a text document
Explanation:
"Text document" is the file that would be hurt most by the lossy compression algorithm.
Audio, as well as picture data (text document), are compressed with crushing defeat to start taking benefit of the unique vision as well as listening or auditory shortcomings.More such documents including software should have been stored without any information leakage as well as corruption.
Thus the above answer is appropriate.
Learn more about the text document here:
https://brainly.com/question/18806025

To better align with Agile and DevOps principles, what type of system should be
used for code management?
O commercial systems
O source control systems
Oopen source systems
O cloud systems
O I don't know this yet.
Answers
The type of system that should be used for code management is cloud systems.
How does DevOps align with Agile?DevOps is known to be a method that is often used to software development that helps teams to create, test, and also be able to release software in a quick way and also in a more reliably way by incorporating agile principles and also their practices, e.g increased automation and better collaboration between development and that of operations teams.
Note that Agile and DevOps often uses Virtualization technology and this is one that can be used to run all areas of the enterprise IT environment.
Hence, The type of system that should be used for code management is cloud systems.
Learn more about DevOps principles from
https://brainly.com/question/24499667
#SPJ1
For each of these conditions— deadlock, race, and starvation—give at leasttwo “real life” examples (not related to a computer system environment) ofeach of these concepts. Then give your own opinion on how each of these sixconditions can be resolved.
Answers
Answer:
Explanation:
Deadlock:
Two cars are approaching an intersection from different directions, both needing to turn left but the traffic is too heavy, and neither can proceed until the other does.
Two friends borrow each other's books and refuse to return them until the other returns their book first.
To resolve deadlock, techniques such as detecting deadlock and breaking the circular wait by releasing resources can be used. For example, in the case of the intersection, a traffic management system can detect the deadlock and break the deadlock by directing one car to move first.
Race:
Two kids are competing to finish their homework first and get a reward.
Several runners in a marathon race are competing to reach the finish line first.
To resolve race conditions, techniques such as locking mechanisms, synchronization, and mutual exclusion can be used. For example, in the case of the homework, the teacher can use a timer to ensure that both kids finish their homework at the same time.
Starvation:
A busy restaurant has a limited number of tables, and some customers may have to wait for a long time to get a table.
In a large company, some employees may never get a promotion or a pay raise despite their hard work and dedication.
To resolve starvation, techniques such as fair scheduling, prioritization, and resource allocation can be used. For example, in the case of the restaurant, a reservation system can be implemented to ensure that customers are served in an orderly and timely manner.
In general, resolving these conditions requires careful planning, design, and implementation of systems and processes to ensure fairness, efficiency, and effectiveness. It is important to identify and address these conditions early on to avoid negative impacts on productivity, customer satisfaction, and organizational success.
Assume we need to implement the following sequence of Instructions with
forwarding by using a 5 stages pipeline.
sub x12, x11, x13
and x8 x12, x15
or x9,x16.x12
For clock cycle 5, what are the control values of A and B (the two outputs of
"Forwarding unit") respectively?
(The control values for the forwarding multiplexors
are shown in the following table)
MUX Control Source
A/B - 00
ID/EX
W/B - 10
EX/MEM
Answers
Answer:
0 0 1 0
Explanation:
sub X12, X11, X13 and x8, X12, X15 or X9, x16, x12 For clock cycle 5, what are the control values of A and B.
XYZ is a well-renowned company that pays its salespeople on a commission basis. The salespeople each receive 700 PKR per week plus 9% of their gross sales for that week. For example, a salesperson who sells 4000 PKR worth of chemicals in a week receives 700 plus 9% of 5000 PKR or a total of 1060 PKR. Develop a C++ program that uses a Repetitive Structure (while, for, do-while) to manipulate each salesperson’s gross sales for the week and calculate and displays that salesperson’s earnings.
Answers
Answer:
#include<iostream>
#include<conio.h>
using namespace std;
float calculateGross(float sale)
{
return (sale/100*9) + 700;
}
main()
{
float sale[3] = { 5000,7000,9000}, Totalsale =0;
for(int i=0; i<=2; i++)
{
cout<<"Sales Person "<<i+1<<" Gross Earnings: "<<calculateGross(sale[i])<<" PKR\n";
Totalsale += calculateGross(sale[i]);
}
cout<<"Total Gross Sales Earnings for week: "<<Totalsale<<" PKR\n";
return 0;
}
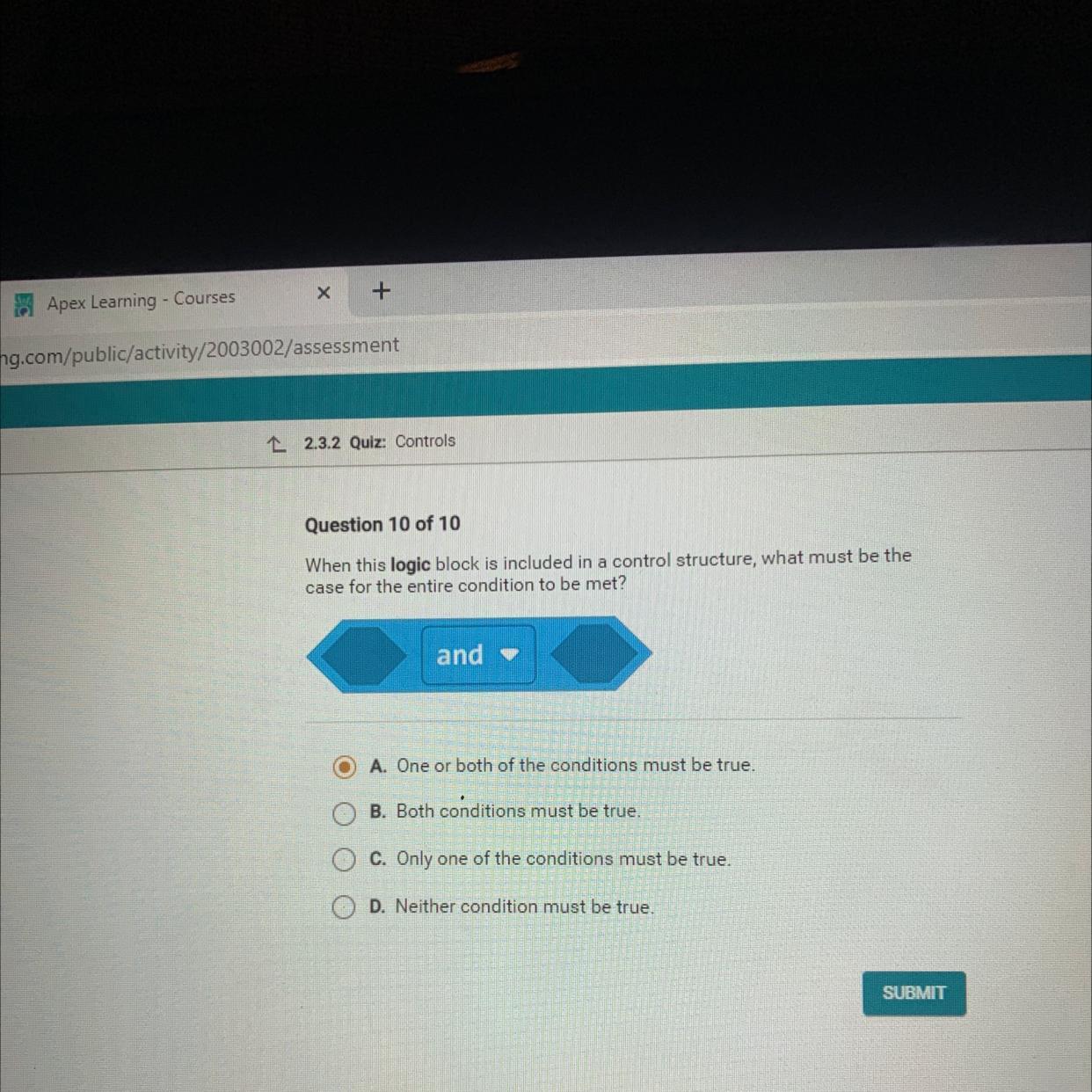
When this logic block is included in a control structure, what must be the
case for the entire condition to be met?
and -
A. One or both of the conditions must be true.
B. Both conditions must be true.
C. Only one of the conditions must be true.
D. Neither condition must be true.
Answers
Answer:
B
Explanation:
a AND b is only true if a is true and b is true.
5.30 LAB: Musical note frequencies
On a piano, a key has a frequency, say f0. Each higher key (black or white) has a frequency of f0 * rn, where n is the distance (number of keys) from that key, and r is 2(1/12). Given an initial key frequency, output that frequency and the next 4 higher key frequencies.
Output each floating-point value with two digits after the decimal point, which can be achieved as follows:
System.out.printf("%.2f", yourValue);
Ex: If the input is:
440.0
(which is the A key near the middle of a piano keyboard), the output is:
440.00 466.16 493.88 523.25 554.37
Note: Use one statement to compute r = 2(1.0/12.0) using the pow function. Then use that r in subsequent statements that use the formula fn = f0 * rn with n being 1, 2, 3, and finally 4.
Answers
Answer:
public static void main(String[] args) {
double f0 = 440.0;
double r = Math.pow(2, 1.0/12.0);
for(int n=0; n<=4; n++) {
double f = f0 * Math.pow(r,n);
System.out.printf("%.2f ", f);
}
}
Explanation:
You could also do it with a running variable, much shorter, but not using the formula as required:
public static void main(String[] args) {
double f = 440.0;
double r = Math.pow(2, 1.0/12.0);
for(int n=0; n<=4; n++) {
System.out.printf("%.2f ", f);
f *= r;
}
}
to group worksheets together press and hold the _____ key
Answers
5 ways in which academic library supports teaching learning and research
Answers
The academic library helps support teaching, learning, and research because it allows people to teach themselves and learn by doing their own research. When you go into an academic library, you are able to find the topic that you are struggling with and do your own research and learn more about it. By doing this you are teaching yourself more about the topic that you were struggling with. By allowing students to have an academic library they have more Independence to learn on their own, teach themselves, and do their own research rather than having to ask a teacher for the questions that they have or for the answer.
what seemingly useless item can be of social, ecological or commercial value?
Answers
Some seemingly useless item can be of social, ecological or commercial value is money, behavior, death etc.
What is something really useless?A useless item are known to be things that are said to be rubbish.
They are items that is useless, of no value. Some useless item can be of social, ecological or commercial value is money, behavior, vehicles etc.
Learn more about commercial value from
https://brainly.com/question/25528419
Explain how the entity relationship (ER) model helped produce a more structured
relational database design environment.
Answers
The way that the entity relationship (ER) model helped produce a more structured relational database design environment is that
A database's primary entities and their relationships can be determined with the aid of an entity relationship model, or ERM. The role of the ERM components is easier to comprehend because they are graphically portrayed.
It is simple to translate the ERM to the tables and attributes of the relational database model using the ER diagram. The full set of needed database structures is generated by this mapping procedure, follows a set of clearly defined processes which are:
uses clearly defined images and rules to represent reality.the theoretical basisbeneficial for communicationTranslate to any DBMS typeHow does the ER model aid in relational database design?A visual representation of relational databases is an entity relationship diagram (ERD). Relational databases are modeled and designed using ERDs.
The Entity Relationship Model (ERM), which enables designers to perceive entities and connections visually, contributed to the creation of a more structured relational database design environment.
Therefore, Instead of defining the structures in the text, it is easier to understand them graphically.
Learn more about entity relationship (ER) model from
https://brainly.com/question/14424264
#SPJ1
How do advertisers use data to know which products would most likely appeal to you
Answers
Answer:
it gives children or adults something to think about
Explanation:
Which of the following accurately describes a user persona? Select one.
Question 6 options:
A user persona is a story which explains how the user accomplishes a task when using a product.
A user persona should be based only on real research, not on the designer’s assumptions.
A user persona should include a lot of personal information and humor.
A user persona is a representation of a particular audience segment for a product or a service that you are designing.
Answers
A user persona is a fictionalized version of your ideal or present consumer. In order to boost your product marketing, personas can be formed by speaking with people and segmenting them according to various demographic and psychographic data and user.
Thus, User personas are very helpful in helping a business expand and improve because they reveal the various ways customers look for, purchase, and utilize products.
This allows you to concentrate your efforts on making the user experience better for actual customers and use cases.
Smallpdf made very broad assumptions about its users, and there were no obvious connections between a person's occupation and the features they were utilizing.
The team began a study initiative to determine their primary user demographics and their aims, even though they did not consider this to be "creating personas," which ultimately helped them better understand their users and improve their solutions.
Thus, A user persona is a fictionalized version of your ideal or present consumer. In order to boost your product marketing, personas can be formed by speaking with people and segmenting them according to various demographic and psychographic data and user.
Learn more about User persona, refer to the link:
https://brainly.com/question/28236904
#SPJ1
what is the best motivation that you can do/give to make your employees stay?
Answers
i'd give fringe benefits to them every month
Explanation:
to encourage them to work on the mission statement and the business goal
A good CRM should Integrate marketing, sales, and customer support activities measuring and evaluating the process of knowledge acquisition and sharing.
Answers
The correct answer to this open question is the following.
Unfortunately, you forgot to include a question. Here, we just have a statement.
What is your question? What do you want to know?
If this is a true or false question, the answer is "true."
It is true that a good CRM should integrate marketing, sales, and customer support activities measuring and evaluating the process of knowledge acquisition and sharing.
The reason is that effective investment in Customer Relationship Management (CRM) should be able to operate efficientñy with these management aspects in order to increase the productivity and efficiency of the company.
A good CRM has to facilitate the operations of a company, improving time management and people's activities that can produce better results accomplishing the companies goals and fulfilling the key performing indicators (KPI)
Universal Containers (UC) has a queue that is used for managing tasks that need to be worked by the UC customer support team. The same team will now be working some of UC's Cases. Which two options should the administrator use to help the support team?
a. Create a new queue and add Cases as an available object.
b. Configure a flow to assign the cases to the queue.
c. Add Cases to the existing queue as available object.
d. Use assignment rules to set the queue as the owner of the case.
Answers
We have that the two options should the administrator use to help the support team are
Configure a flow to assign the cases to the queueUse assignment rules to set the queue as the owner of the caseOption B and D
From the question we are told
Universal Containers (UC) has a queue that is used for managing tasks that need to be worked by the UC customer support team. The same team will now be working some of UC's Cases. Which two options should the administrator use to help the support team?Support team HelpGenerally the two options that will be taken
1)Configure a flow to assign the cases to the queue
The configuration of the waft is will be created in such a way that if any different venture comes then it computerized get managed and the uc client aid group will test the waft on that base they can sketch based totally on the assignment and assign to group and execution of the mission is being started.
2. Use assignment rules to set the queue as the owner of the case
The venture policies are used for the reason of getting assigned the challenge mechanically , in this case we have now the important points like the UC
Therefore
Configure a flow to assign the cases to the queue Use assignment rules to set the queue as the owner of the caseOption B and D
For more information on Support visit
https://brainly.com/question/18540902
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
What is nanotechnology?
Answers
Answer:
Nanotechnology is a field of research and innovation concerned with building 'things' - generally, materials and devices - on the scale of atoms and molecules.
Explanation:
The diameter of a human hair is, on average, 80,000 nanometres.A nanometre is one-billionth of a metre – ten times the diameter of a hydrogen atom.Answer:
Nanotechnology are the areas of science and engineering where phenomena that take place at dimensions in the nanometre scale are utilised in the design, characterisation, production and application of materials, structures, devices and systems.
What is the top anime shows? <3
Answers
Answer:
This is personally based on my opinion.
My top 10 favorites
Toradora
Darling in the franxx
Lucky Star
My Melody
Death note
Attack on titans
One piece
The Promise neverland
Kaguya-sama: love is war
Black cover
Answer:
This is just my opinions as of rn
Explanation:
Attack on Titan
Hunter x Hunter
Saiki K
Haikyu!!
The Promised Neverland
Toilet Bound Hanako-kun (The manga is amazing.)
Ouran High School Host Club
Given
Yuri on Ice!!!
Hetalia
some close runner ups were
Toradora
A Silent Voice
Anohana
Kakegurui
and Black Butler
The other anime i've seen were either movies and shows I watched as a kid or I just couldn't think of them right away
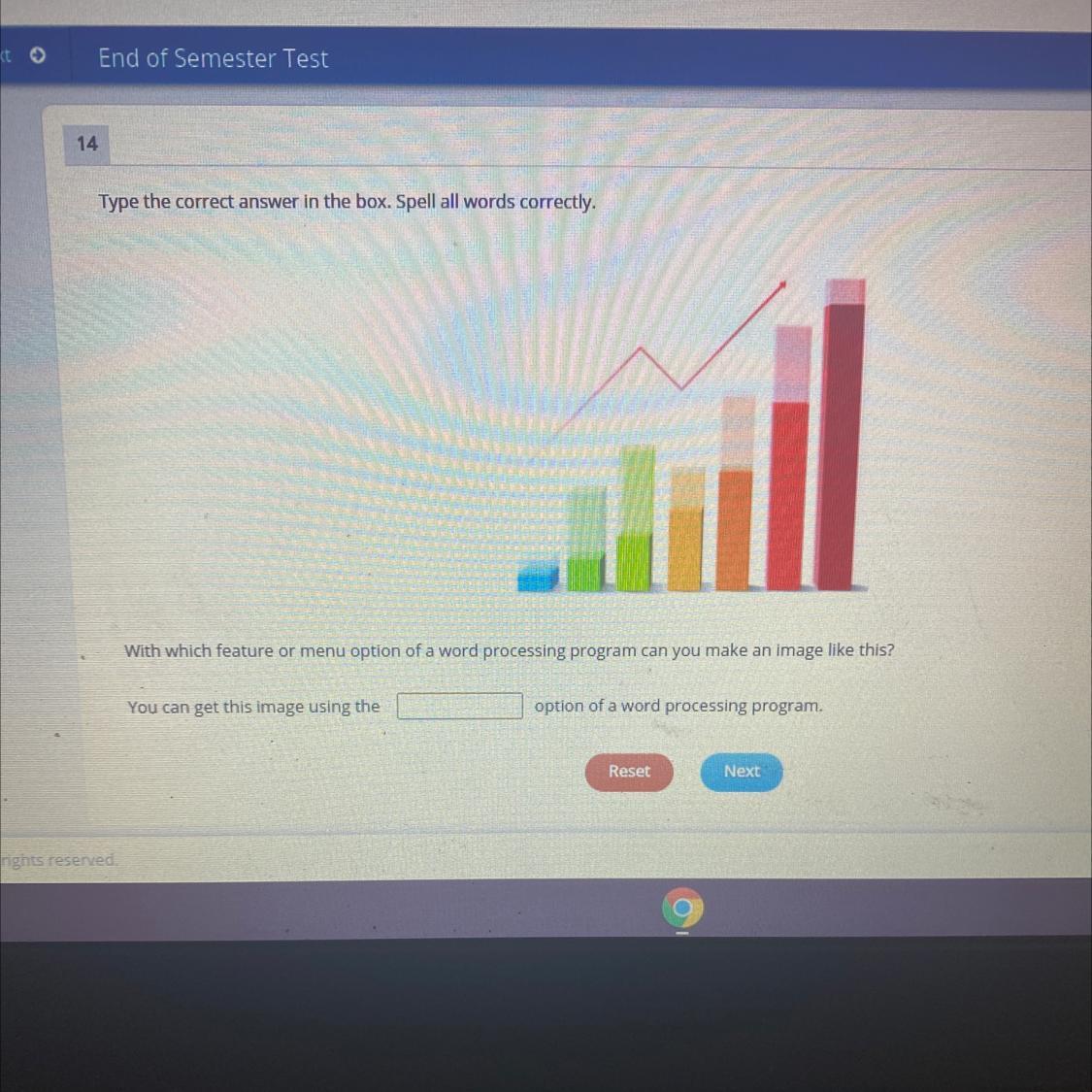
With which feature or menu option of a word processing program can you make an image like this?
You can get this image using the
option of a word processing program.
Reset
Next
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The correct answer to this question is Chart.
You can insert an image like as given in the question using the Chart feature in the word processing document. This image called the bar graph chart.
You can insert a chart in your word processing document going through the Insert tab, then find the chart option under the Illustrations group of the command.
As you click on the chart, different types of charts will be shown to you. You can click on the required chart and insert it into the document. The inserted chart can be customized while double-clicking on the inserted chart.
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1
Hi!
i want to ask how to create this matrix A=[-4 2 1;2 -4 1;1 2 -4] using only eye ones and zeros .Thanks in advance!!
Answers
The matrix A=[-4 2 1;2 -4 1;1 2 -4] can be created by using the following code in Matlab/Octave:
A = -4*eye(3) + 2*(eye(3,3) - eye(3)) + (eye(3,3) - 2*eye(3))
Here, eye(3) creates an identity matrix of size 3x3 with ones on the diagonal and zeros elsewhere.
eye(3,3) - eye(3) creates a matrix of size 3x3 with ones on the off-diagonal and zeros on the diagonal.
eye(3,3) - 2*eye(3) creates a matrix of size 3x3 with -1 on the off-diagonal and zeros on the diagonal.
The code above uses the properties of the identity matrix and the properties of matrix addition and scalar multiplication to create the desired matrix A.
You can also create the matrix A by using following code:
A = [-4 2 1; 2 -4 1; 1 2 -4]
It is not necessary to create the matrix A using only ones and zeroes but this is one of the way to create this matrix.
Write a Pandas program to import excel data (coalpublic2013.xlsx) into a dataframe and draw a bar plot where each bar will represent one of the top 10 production.
Answers
Answer:
import pandas as pd
import numpy as np
import matplotlib.pyplot as plt
df = pd.read_excel('coalpublic2013.xlsx')
sorted_by_production = df.sort_values(['Production'], ascending=False).head(10)
sorted_by_production['Production'].head(10).plot(kind="bar")
plt.show()
Explanation:
The python program plot a bar chart of the top ten productions in the excel worksheet. The excel file is read in as a pandas dataframe, sorted in descending order and the first ten of the dataframe is plotted as a bar plot.
Part 1 Develop a 2- to 3-page table in Microsoft® Word that lists the roles and responsibilities of each of the following with respect to security. Use the following column headings: Title Role Responsibilities Use the following row headings: Chief Executive Officer (CEO) Chief Operations Officer (COO) Chief Financial Officer (CFO) Chief Information Officer (CIO) Chief Information Security Officer (CISO) Senior Security Manager Information Security Architect Information Security Engineer Information Security Auditor Information Security Analyst Security Technician/Specialist
Answers
The roles and responsibilities of the below-listed person with respect to security are:
Chief Executive Officer (CEO)- This person is responsible for making major corporate decisions, managing the overall operations and resources of a company
Chief Operations Officer (COO)- He is usually the second-in-command at the firm and can stand in when the CEO is unavailable.
Chief Financial Officer (CFO)- He is responsible for tracking cash flow and financial planning and analyzing the company's financial strengths
Chief Information Officer (CIO)- This person is in charge of information technology initiatives and strategy.
Chief Information Security Officer (CISO)- individual primarily responsible for the assessment, management, and implementation of information security in the organization.
Senior Security Manager Information- This person is in charge of managing the day-to-day operations of their organization's security department
Security Architect Information- This person is responsible for assessing the organization's systems for weaknesses. They conduct penetration tests
Security Engineer Information- This person is in charge of building digital security protocols, operating a cyber security system and maintaining an IT security infrastructure
Security Auditor Information- This person looks at the safety and effectiveness of computer systems and their security components,
Security Analyst- This person protects computer networks from cyber attacks, creates cybersecurity policies and practices f
Security Technician/Specialist- This person has the main duty to maintain and repair security-related concerns in a company.
Read more about Senior Security Manager here:
https://brainly.com/question/14467050
#SPJ1
Write a recursive function is_pow2(n) that returns True if the positive integer n is an integer power of 2, and False otherwise. For example: function call return value is_pow2(1) True is_pow2(2) True is_pow2(3) False is_pow2(4) True is_pow2(5) False is_pow2(6) False is_pow2(7) False is_pow2(8) True is_pow2(9) False is_pow2(255) False is_pow2(256) True Hint: Consider using repeated floor division.
Answers
Answer:
In Python:
def is_power(n):
if n > 2:
n = n/2
return is_power(n)
elif n == 2:
return True
else:
return False
Explanation:
This defines the function
def is_power(n):
If n is greater than 0
if n > 2:
Divide n by 2
n = n/2
Call the function
return is_power(n)
If n equals 2
elif n == 2:
Return True
return True
If n is less than 2
else:
Then, return false
return False
You are tasked with designing the following 3bit counter using D flip flops. If the current state is represented as A B C, what are the simplified equations for each of the next state representations shown as AP BP CP?
The number sequence is : 0 - 1 - 2 - 4 - 3 - 5 - 7 - 6 - 0
Answers
In the given 3-bit counter, the next state of A, B, and C (represented as A', B', and C') depends on the current state ABC.
The sequence is 0-1-2-4-3-5-7-6 (in binary: 000, 001, 010, 100, 011, 101, 111, 110).
The simplified next state equations for D flip-flops are:
A' = A ⊕ B ⊕ C
B' = A · B ⊕ A · C ⊕ B · C
C' = A · B · C
This counter follows the mentioned sequence and recycles back to 0 after reaching the state 6 (110). These equations can be implemented using XOR and AND gates connected to D flip-flops.
Read more about XOR and AND gates here:
https://brainly.com/question/30890234
#SPJ1
You're the network administrator for a consulting firm. Your network consists of the following:
• 30 laptops in the sales department
10 computers for HR
• 5 laptops for management
• 20 computers in marketing
• 15 computers in IT
You're using Microsoft Intune to manage the company's devices. You've configured an update ring named Management and
enrolled the ring in the Semi-Annual Servicing Channel. You've also set updates to be delayed for 30 days, which gives you ample
time to test them before they're rolled out to the user machines. However, you want to make sure you can rollback a feature
update if a problem comes up after the update has been installed on the user machines.
What is the maximum number of days you can configure a feature update uninstallation period for?
Answers
Answer:
anytime
Explanation:
as far as i know you can manage in real time meaning add or remove any hardware or software anytime but im not sure once its rewritten each is considered version 1.0 but uninstallation happens each time you reinstall so uninstallation is actualy anytime
last i checked all tho trial activation is usualy one week or one month so 7 or 30 days till installation but uninstall is anytime unless it service or updates
Where do you get your news? Is it owned by a large conglomerate does it matter to you who own your local news outlets? why or why not?
Answers
Which practice indicates integrity? A. manipulating people for everyone’s benefit B. inflating product costs in accounting ledgers C. actively participating in team practices and team meetings D. indiscriminately providing company data to external parties
Answers
Answer:
The practice that indicates integrity is C. actively participating in team practices and team meetings.
Explanation:
onsider the below given table and write queries for
(i) & (ii) and output of
(iii) –(v):Table Name: Pet
i) Display name, owner and gender for all dogs.
ii) Display Name, owner and age of all pets whose age is more 2 years.
iii)select name, owner from pet where owner name like ‘%ya’;
iv) select name, age from pet where species = dog and age between 1 and 3;
v) select * from pets where species in (‘horse’,’parrot’)
Answers
Note that this is an SQL prompt. This is because we are asked to create queries. When you have information on tables are are asked to create queries that will result in a certain output, you are looking at a dataase query. Queries are created in SQL. Here are the queries below. The expected output are all attached.
(i) Display name, owner and gender for all dogs.
Query:
SELECT Name, Owner, Gender
FROM Pet
WHERE Species = 'Dog';
(ii) Display Name, owner and age of all pets whose age is more 2 years.
Query:
SELECT Name, Owner, Age
FROM Pet
WHERE Age > 2;
(iii) select name, owner from pet where owner name like ‘%ya’;
Query:
SELECT Name, Owner
FROM Pet
WHERE Owner LIKE '%ya';
(iv) select name, age from pet where species = dog and age between 1 and 3;
Query:
SELECT Name, Age
FROM Pet
WHERE Species = 'Dog' AND Age BETWEEN 1 AND 3;
(v) select * from pets where species in (‘horse’,’parrot’)
Query:
SELECT *
FROM Pet
WHERE Species IN ('Horse', 'Parrot');
What is an SQL Query and why is it important?
An SQL query is a command used to retrieve or manipulate data in a relational database. It is important because it allows users to extract specific data from large databases, make updates to existing data, and create new records.
SQL queries are essential in many industries that rely on large amounts of data, such as finance, healthcare, and e-commerce.
SQL queries are used to interact with data stored in relational databases, which are typically organized into tables. Queries allow users to extract, modify, and manage data within those tables.
See all output attached.
Learn more about SQL Query on:
https://brainly.com/question/30755095
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
Assuming this is a database, consider the above given table and write queries for:
(i) & (ii) and output of
(iii) –(v):Table Name: Pet
i) Display name, owner and gender for all dogs.
ii) Display Name, owner and age of all pets whose age is more 2 years.
iii)select name, owner from pet where owner name like ‘%ya’;
iv) select name, age from pet where species = dog and age between 1 and 3;
v) select * from pets where species in (‘horse’,’parrot’)
