A variation of the round-robin scheduler is the regressive round-robin scheduler. This scheduler assigns each process a time quantum and a priority. The initial value of a time quantum is 50 milliseconds. However, every time a process has been allocated the CPU and uses its entire time quantum (does not block for I/O), 10 milliseconds is added to its time quantum, and its priority level is boosted. (The time quantum for a process can be increased to a maximum of 100 milliseconds.) When a process blocks before using its entire time quantum, its time quantum is reduced by 5 milliseconds, but its priority remains the same. What type of process (CPU-bound or I/O-bound) does the regressive round-robin scheduler favor? Explain.
Answers
If the regressive round-robin scheduler's initial value of a time quantum is 50 milliseconds, if 10 milliseconds is added to its time quantum and its priority level is boosted every time a process has been allocated the CPU and uses its entire time quantum, and if its time quantum is reduced by 5 milliseconds, but its priority remains the same when a process blocks before using its entire time quantum, then the regressive round-robin scheduler favors CPU-bound processes.
The regressive round-robin scheduler favors CPU-bound processes because this scheduler favors processes that are very CPU intensive. This is because the scheduler increases the quantum time of a process that uses up its entire CPU quantum, so it can continue running on the CPU, while at the same time, it boosts the priority level of the process. As a result, a process that has been allocated the CPU will have a higher chance of being allocated the CPU again when it becomes available. Since a CPU-bound process takes up the CPU most of the time, it will use up its CPU quantum and receive a priority boost, allowing it to stay on the CPU for a longer period of time. As a result, CPU-bound processes are favored over I/O-bound processes, which would use up their quantum time much less frequently, if at all.
Hence, the regressive round-robin scheduler favors CPU-bound processes.
Learn more round-robin scheduler:
brainly.com/question/30023475
#SPJ11
Related Questions
Tier 1 networks form the internet ____.
Answers
Answer:
Internet Backbone
Explanation:
The internet is a network of networks, no single tier 1 network (ISP companies like Sprint, IBM, Verizon, AT&T for example, they provide the cables and routers that connect the networks) can reach the entire internet on its own, so they merge together to form the Internet Backbone, a backbone network enables all users and companies to connect with each other.
1.what are the ways on how to maintain you hand tools properly?
2.why is it important to have proper maintenance of hand tools?
3.why do you think 5s is important in the workplace?
help:(
Answers
There are several ways to maintain your hand tools properly. Store them in a safe and organized manner, and regularly inspect them for any damage or wear and tear. Cleaning your hand tools after use helps prevent rust and corrosion, which can lead to deterioration and eventually make them unusable.
Proper maintenance of hand tools is important for several reasons. It prolongs their lifespan and ensures they function properly, which saves you time and money in the long run. Explanation-wise, when hand tools are well-maintained, they are less likely to break or malfunction, which can cause delays or accidents in the workplace. Additionally, having to constantly replace broken or worn-out tools can be costly and time-consuming, so proper maintenance is a smart investment.
5S is important in the workplace for several reasons. It promotes safety, efficiency, and productivity by organizing the workplace and reducing waste. 5S involves five steps: sorting, straightening, shining, standardizing, and sustaining. By sorting through materials and equipment and getting rid of anything that is not necessary, the workplace becomes safer and more efficient. Straightening involves organizing everything in a logical and accessible manner, which makes it easier to find and use tools. Shining refers to keeping everything clean and in good condition, which helps prevent accidents and prolongs the lifespan of equipment.
To know more about inspect visit:-
https://brainly.com/question/30727643
#SPJ11
why are extensions necessary in scratch programming as a whole?
Answers
Scratch extensions are vital for scratch to interface with the external hardware and information.
Scratch simply means a free programming language where an individual can create their own interactive stories.
It's simply the world's largest coding community for children. Scratch extensions are vital for scratch to interface with the external hardware and information.
Read related link on:
https://brainly.com/question/15418798
Exercise 7.2.6: If You're Not First, You're Last
Write the function called end_of_word that takes a string and returns everything but the first character.
end_of_word ("boat")
="oat"
end_of_word ("mice")
="ice"
Answers
Answer:
end_of_word ("boat")
="oat"
end_of_word ("mice")
="ice"
Explanation:you need to call out your function in the best way possible
Answer:
def end_of_word(word):
return word[1:]
print(end_of_word("something"))
Explanation:
Your welcome :D
Activity Universal Usability Visit each of the following web pages and evaluate their usability. Describe components that show adaptability for different users and provide suggestions, if any, to improve the usability of the website. Part A
Answers
Users may easily locate and navigate through various sections of the website because to its simple and well-organized style.
What are the usability's five elements?Usability can be divided into five different aspects because it is not a single, one-dimensional characteristic of a user interface. These qualities are learnability, effectiveness, memorability, mistakes, and contentment.
What are the 4 usability levels?Any product, system, or website can generally be tested for usability using one of four different ways. Model/metrics based, inquiry, inspection, and testing methods are some categories for usability testing techniques.
To know more about website visit:-
https://brainly.com/question/19459381
#SPJ1
Question:-
Activity: Universal Usability
Visit each of the following web pages and evaluate their usability. Describe components that show adaptability for different users and provide suggestions, if any, to improve the usability of the website.
Part A:
Website: https://www.nytimes.com/
Website: https://www.bbc.com/
Part B:
Website: https://www.target.com/
Website: https://www.walmart.com/
Why should you use a server provider instead of a personal server?
Answers
One should use a service provider rather than a personal server because Dedicated Servers services may provide the power and control you need for network administration while also keeping your network secure and saving you time and money. You may designate servers to accomplish tasks such as maintaining several websites or coordinating all of your company's printing.
What is a dedicated Server?A dedicated hosting service, also known as a dedicated server or managed hosting service, is a form of Internet hosting in which the client rents a whole server that is not shared with anybody else.
If your website is having difficulty keeping up with increased traffic, it may be time to convert it to a dedicated server. This is essentially a server that exclusively hosts your site, and it may not only increase the speed of your site, but also improve page loading times and help you optimize security.
Learn more servers:
https://brainly.com/question/28320301
#SPJ1
. how can one assign a cost to a connection between two bridges or two routers
Answers
To assign a cost to a connection between two bridges or two routers, you can use a metric, which is a numerical value representing the "cost" of using a particular link. This cost can be based on factors like bandwidth, delay, or reliability. Network protocols, such as OSPF or EIGRP, use these metrics to determine the best path for data transmission between devices.
Connecting two bridges or two routersThe cost of a connection between two bridges or two routers can be assigned by considering several factors. These factors can include the distance between the two devices, the type of network being used, and any additional costs associated with maintaining the connection.
For example, if the two devices are connected using fiber-optic cable, the cost of the cable, installation, and maintenance should be considered.
Similarly, if the two devices are connected using a wireless network, the cost of the wireless access point and any additional hardware should be factored into the cost assignment process.It is also important to consider any ongoing costs associated with maintaining the connection.
These can include the cost of electricity or other utilities needed to maintain the connection, as well as any labor costs associated with ongoing maintenance tasks.
Learn more about router at
https://brainly.com/question/29869351
#SPJ11
Write a short note on Computer
impact on
our society?
Answers
well not a note but here are some few points
Explanation:
1 Computers can have the huge impact on employment of people like job and other stuff.
2 lots of human can be jobless or unemployed
3 it can cuz impact on the health of peoples
4 it also can make us lazy and and lack of self knowledge
Answer:
Everybody knows that the computer age is here, and most people use the computer. Science and technology development has a direct impact both on our everyday life and on our social lives. In seconds, computer technology has enabled communication between the two parts of the world. In one part of the world, you may see the transactions while in the other part. The development of computers is one of the 20th century's greatest scientific achievements.
Explanation:
Positive Impact of Computer:-
The work can be done very quickly.You can store more information in a small space.Multitasking and data multimedia capacity.Access to data is easy.Negative Impact of Computer:-
Very costly.Accidents.Pirating data. Enhanced joblessness.Sometimes enormous data and information can be lost.Computer technology is changing rapidly.Distribution of services.Computing and computer analphabetism.Which file attribute identifies the file as having been modified since the last backup?.
Answers
Archive File Definition
The meaning of the word Archive in the Online Computer Dictionary is used to make a copy of a backup file with the aim of protecting the original copy from damage.
How to Archive Files Into 1 File
If you want to send a large number of files, you can make the file into 1 archive file format with .zip, .tar, or .rar format first. This method is also quite easy and fast.
• First, make sure your computer has programs such as winzip, winrar. This program is needed to archive files.
• Second, you can select the file you want to archive, then right-click on the file. The example below shows 2 files to be archived
• The third step, you can directly select Add to “folder name.rar” to directly create archive files automatically. If you want to do some settings, it can be done by selecting the Add to archive option. The Add to archive option allows you to choose the save format of the file, divide or create the archive into several parts (part 1, part 2, etc.), to create a password. With the password, before the file can be extracted, it is necessary to enter the password first.
In addition to files, you can also archive folders directly along with the contents of the files in it. Keep in mind, how fast the process of archiving this file will depend on how many or large files to be archived.
Learn more about archive files athttps://brainly.com/question/15355917.
#SPJ4
The control panel contains the number of
Answers
A computer system's control panel often has a number of categories, which are groupings of related settings and functions that the user may access and alter.
What are the functions oft he Control Panel?The Control Panel is a Microsoft Windows component that allows you to see and alter system settings.
It is made up of a collection of applets that let you to install or remove hardware and software, control user accounts, change accessibility features, and access networking settings.
The control panel handles peripheral devices and interacts between them and the host computer.
Learn more about Control Panel at:
https://brainly.com/question/31921377
#SPJ1
Nadia wants to make changes to her Excel spreadsheet. She wants to keep her original file with its current file name, and save the changed document as a new file. What command should she use
Answers
Answer:
Save as.
Explanation:
A spreadsheet can be defined as a file or document which comprises of cells in a tabulated format (rows and columns) typically used for formatting, arranging, analyzing, storing, calculating and sorting data on computer software applications such as Microsoft Excel.
In this scenario, Nadia wants to make changes to her Excel spreadsheet. She wants to keep her original file with its current file name, and save the changed document as a new file.
Hence, the command Nadia should use is "Save as" of the file options in Microsoft Excel.
Basically, the Save as command would save the updated version of the Excel spreadsheet while keeping the previous version of the spreadsheet.
what are the prerequisites to integrate qualys with servicenow cmdb
Answers
To integrate Qualys with ServiceNow CMDB, there are a few prerequisites that need to be fulfilled. These prerequisites include: Access to both Qualys and ServiceNow: To integrate Qualys with ServiceNow CMDB, you need to have access to both the Qualys and ServiceNow platforms.
Qualys API access: To integrate Qualys with ServiceNow CMDB, you need to have access to the Qualys API. You will need to generate an API key from the Qualys platform and ensure that the key has the necessary permissions to access the data you want to integrate. ServiceNow API access: To integrate Qualys with ServiceNow CMDB, you need to have access to the ServiceNow API.
You will need to generate an API key from the ServiceNow platform and ensure that the key has the necessary permissions to access the data you want to integrate. Data mapping: Before you can integrate Qualys with ServiceNow CMDB, you need to map the data fields from Qualys to the corresponding fields in ServiceNow. This will ensure that the data is properly synced between the two platforms. Integration setup: Finally, you need to set up the integration between Qualys and ServiceNow CMDB. This can be done using a third-party integration tool or by writing custom scripts to handle the data transfer. Overall, integrating Qualys with ServiceNow CMDB can be a complex process, but with the right tools and expertise, it can be done successfully. The prerequisites to integrate Qualys with ServiceNow CMDB include access to both Qualys and ServiceNow, Qualys API access, ServiceNow API access, data mapping, and integration setup.To integrate Qualys with ServiceNow CMDB, the prerequisites are as follows: ServiceNow Instance: Ensure you have an active ServiceNow instance running on a supported version. Qualys Subscription: You need a valid Qualys subscription with access to Vulnerability Management and/or Policy Compliance modules. ServiceNow App: Install the "Qualys Vulnerability Integration" app from the ServiceNow Store on your ServiceNow instance. Qualys API Credentials: Obtain the API credentials (username and password) for your Qualys account, which will be used for the integration setup. ServiceNow API Credentials: Obtain the API credentials (username and password) for your ServiceNow instance, which will be used in the Qualys integration setup. Define Asset Groups: Identify and define asset groups in Qualys that you want to synchronize with ServiceNow CMDB.
To know more about Qualys visit:
https://brainly.com/question/31200365
#SPJ11
what does bLINK mean?
Answers
Answer:
people who stan blackpink are known as blinks.
another meaning is blinking your eyes.
computers that can be identified and traced are of no value to thieves. so maguda inc. has instituted a plan to reduce theft by etching the serial number of each computer on both the fram of the monitor and on the hard drive, where it will be possible to overlook. maguda's plan relies on which assumption?
Answers
Maguda Inc.'s plan to reduce computer theft by etching serial numbers on both monitor frame and hard drive relies on assumption that criminals will be deterred by the easily traceable nature of the computers.
Maguda Inc.'s plan to reduce theft of computers by etching the serial number on both the frame of the monitor and the hard drive relies on the assumption that computers that are identifiable and traceable are worthless to robbers. This assumption is that criminals who steal computers will be deterred by the knowledge that the computer can be easily traced and identified, making it difficult for them to profit from the stolen property.
This assumption is based on the idea that the risk of being caught and facing legal consequences will outweigh the potential benefit for the thief, and thus they will avoid stealing computers that have easily traceable serial numbers. If the serial numbers are easily visible and can be used to identify and trace the stolen property, it becomes less attractive to potential thieves and less likely to be stolen. By implementing this plan, Maguda Inc. is hoping to reduce the risk of computer theft and increase the security of their assets.
Learn more about hard drive here:
https://brainly.com/question/963946
#SPJ4
What will you see on the next line? >>> int(6.5)
Answers
Answer:
6
Explanation:
The int functions founds down to the nearest whole number, which in this case would be 6.
Answer:
6
Explanation:
Please! I need help matching this.
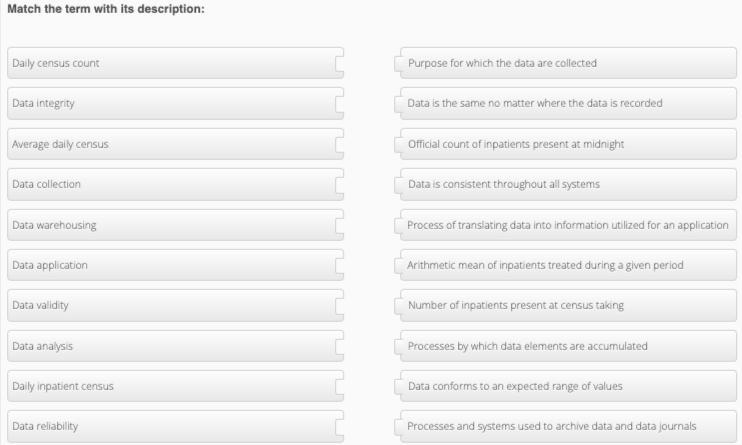
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
WILL GIVE BRAINLIEST
What is the missing term?
A(n) _______ explains how an app’s functions must be coded. It is needed if your app has complex communication functions.
Answers
Answer:
application
Explanation:
Answer:
Technical specification document
Explanation:
If a forensic document examiner can make a definitive determination of authorship or source they use the term:
Answers
If a forensic document examiner can make a definitive determination of authorship or source they use the term identification.
Identification is the process of comparing known samples (exemplars) of writing to questioned materials in order to determine authorship or to establish the source of the document. In other words, forensic document examiners use a comparison between known samples and questioned documents to identify the author of a document.
The term identification is used when the examiner has found a sufficient number of significant handwriting characteristics or features of the author’s signature in the questioned and known samples. based on a significant degree of similarity, and therefore, the examiner can conclude that the author of the known and the questioned document is the same.
the document examiner can come to a definitive determination of authorship or source. The document examiner’s is usually based on a high level of confidence in the accuracy of the opinion.
since handwriting and other characteristics can change over time, identification of an individual’s handwriting may not always be possible. forensic document examiners follow a strict procedure in document examination and comparison in order to ensure accuracy.
To know more about forensic visit:-
https://brainly.com/question/31441808
#SPJ11
Evaluate if the following function is a good candidate to be placed in a library. Why or why not?

Answers
Answer:
It cannot be a good candidate because the creator of the library is attempting to update the global variables player1Points and player2Points. The updated scores for each player won't be retained unless someone creates the global variables player1Points and player2Points in their program.
The updateScore function is meant to update the point of player1 and player2 ; since the variables player1 and player2 are only defined in the function, then they do not have a global scope. Hence, the function isn't right to be placed in a library.
Variables defined outside a function are called global variables ; hence, they can be referenced anywhere within the program.
Since the function references a global variable, then any program which intends to use the function must have the variables player1 and player2 must be defined globally in the program.
Hence, it is not a good candidate to be placed in a library.
Learn more:https://brainly.com/question/20720413
Choose the word that matches each definition.
___ computer technology that uses biological components to retrieve, process, and store data
___use of the Internet to access programs and data
___innovations that drastically change businesses, industries, or consumer markets
Answers
Answer:
1. Biocomputing
2. Cloud computing
3. Disruptive Technology
Hope this helps! ^-^
-Isa
Biocomputing is a computer that employs biological components (such as DNA molecules) instead of electrical components.
What is Biocomputing?Biocomputing is a computer that employs biological components (such as DNA molecules) instead of electrical components. The gadget is simple—it can only do basic high-school arithmetic problems.
The given blanks can be filled as shown below:
1. Biocomputing is the computer technology that uses biological components to retrieve, process, and store data
2. Cloud computing is the use of the Internet to access programs and data
3. Disruptive Technology is the innovations that drastically change businesses, industries, or consumer markets
Learn more about Biocomputing:
https://brainly.com/question/17920805
#SPJ2
A company is monitoring the number of cars in a parking lot each hour. each hour they save the number of cars currently in the lot into an array of integers, numcars. the company would like to query numcars such that given a starting hour hj denoting the index in numcars, they know how many times the parking lot reached peak capacity by the end of the data collection. the peak capacity is defined as the maximum number of cars that parked in the lot from hj to the end of data collection, inclusively
Answers
For this question i used JAVA.
import java.time.Duration;
import java.util.Arrays;;
class chegg1{
public static int getRandom (int min, int max){
return (int)(Math.random()*((max-min)+1))+min;
}
public static void display(int[] array){
for(int j=0; j< array.length; j++){
System.out.print(" " + array[j]);}
System.out.println("----TIME SLOT----");
}
public static void main(String[] args){
int[] parkingSlots= new int[]{ -1, -1, -1, -1, -1 };
display(parkingSlots);
for (int i = 1; i <= 5; i++) {
for(int ij=0; ij< parkingSlots.length; ij++){
if(parkingSlots[ij] >= 0){
parkingSlots[ij] -= 1;
}
else if(parkingSlots[ij]< 0){
parkingSlots[ij] = getRandom(2, 8);
}
}
display(parkingSlots);
// System.out.println('\n');
try {
Thread.sleep(2000);
} catch (InterruptedException e) {
e.printStackTrace();
}
}
}
}
output:
-1 -1 -1 -1 -1----TIME SLOT----
8 6 4 6 2----TIME SLOT----
7 5 3 5 1----TIME SLOT----
6 4 2 4 0----TIME SLOT----
5 3 1 3 -1----TIME SLOT----
4 2 0 2 4----TIME SLOT----
You can learn more through link below:
https://brainly.com/question/26803644#SPJ4
What best describes proprietary file format?
A format that is closed but free of cost.
A format that is considered a trade secret.
A format that is not bound by copyright law.
A format that is open and free of cost.
Answers
Answer:
A
Explanation:
I took its on my quiz and i certainly go it correct!
A format that is closed but free of cost is the best describes proprietary file format. Thus, option (a) is correct.
What is the cost?
The term cost refers to the actual money are spent on the manufacturing of the product. The product are manufacture to spend on money are raw material, transportation, wages, salary, and other expenses add. The all expenses are added to identify the cost.
Each business was responsible for managing the data on file. A proprietary file format is one that a firm, person, or organization develops in order to keep itself or its operations hidden. It allows for the decoding and interpretation of stored data to be documented. A business kept track of the files and prepared for free of cost.
As a result, the format that is closed but free of cost is the best describes proprietary file format. Therefore, option (a) is correct.
Learn more about cost, here:
https://brainly.com/question/15135554
#SPJ2
Read the Hefty Hardware Case Study on pages 76-79 in the textbook. Answer the Discussion Questions at the end of the Case Study. 1. Overall, how effective is the partnership between IT and the business at Hefty Hardware? Identify the shortcomings of both IT and the business. 2. Create a plan for how IT and the business can work collaboratively to deliver the Savvy Store program successfully. Please add the abstract and conclusion to the case study, answer up to 1000 to 1500 words
Answers
Question 1: Overall, how effective is the partnership between IT and the business at Hefty Hardware?
Identify the shortcomings of both IT and the business
Hefty Hardware is a renowned company for their hardware products in the industry. In the case study, it has been understood that they were having a communication gap between their IT and their business unit.
So, the first issue, which I have identified, is that the IT and the business unit had a huge communication gap between them. As we know that the relationship between two different units are based on competence, credibility, interpersonal communications and trust.These components were missing in their relationship. While working together, business unit thought that the IT is having lack of competence.
on the other hand, IT unit did not have much knowledge about the business goal and the business processes. Also, business unit was having an impression about the IT unit that they were lacking credibility so it is hard to trust IT units with the business protects to be successful. The time IT units found out the issue and tried to resolve it, it was pretty late on their end, which resulted Hefty Hardware with a huge CIO turnover.
Finally, the interpersonal communications between the two parties were failure mostly. In the most of the meetings, business unit would mostly describe their business goals and e&pectations,which IT was not able to translate and at the same time IT talked about their technical language,which turned out to be foreign language for the business unit of Hefty Hardware. Hefty Hardware is absence of a strong establishment and a solid connection between the business andIT divisions has turned into a fundamental center issue in current dealings, and in building future development for the organization
2. Question 2: Create a plan for how IT and the business can work collaboratively to deliver the Savvy Store program successfully.
After reading the case study, I have come to a conclusion that, the IT unit and the business unit of Hefty Hardware must come to an agreement to work together and understand each other. They should build more trust and communication between them to resolve all the gaps that they are having. To do that, they should introduce a team building training program for both of the units where both of the teams will spend time and try to understand each other.
This team building training will help both the units to have better relationship based on trust, functionality and processes.Hefty Hardware has a few alternatives accessible to actuality their program. One choice is to get preparing with a group building proficient, where the employers would spend a selective number of hours in a day in an classroom type of environment.
Also, continuous booked short gatherings can happen where group(building activities can be performed around a meeting table. This would guarantee the IT and business division)s relationship stays strong.Once the both of the units understand each other and working on the same page, they will be able to deliver the work on time and Savvy Store program would be successful.
Learn more about Hefty Hardware at https://brainly.com/question/14526426.
#SPJ4
does an efficient algorithm exists for all computational problems
Answers
Answer:
no, there are to many variables for a algorithm to consider
No, an efficient algorithm does not exist for all computational problems.
There are certain computational problems that are classified as "intractable," meaning that they cannot be solved efficiently using any known algorithm. These problems are often referred to as NP-hard problems, and they are characterized by the fact that they require an exponential amount of time to solve. While there may be efficient algorithms for some computational problems, there are many others for which no efficient algorithm has been found.
There are many computational problems for which efficient algorithms do exist, and they have been studied extensively. However, for many other important problems, no efficient algorithm is known, and researchers continue to explore ways to improve our understanding of these problems and develop better algorithms for solving them.
Learn more about an efficient algorithm here:https://brainly.com/question/29562548
#SPJ11
with the ________ delivery model, cloud computing vendors provide software that is specific to their customers’ requirements.
Answers
Cloud Computing is simply known to be a type of computing. Software-as-a-Service (SaaS) delivery model, cloud computing vendors provide software that is specific to their customers’ requirements.
Software-as-a-Service (SaaS) is simply define as a type of cloud computing vendors that gives software that is particular to their customers' needs.It is the most used service model as it gives a broad range of software applications. It also gives web-based services to its user.
Learn more from
https://brainly.com/question/14290655
what does not stand for
Answers
which query will use the given columns and column aliases from the product table to determine the total value of inventory held on hand and display the results in a column labeled totvalue?
Answers
The following SQL query will use the given columns and column aliases from the product table to determine the total value of inventory held on hand and display the results in a column labeled totvalue is:
SELECT (on_hand_qty * price) AS totvalue FROM product;
SQL stands for Structured Query Language. SQL is used to communicate with a database. According to the problem, the given columns and column aliases from the product table to determine the total value of inventory held on hand and display the results in a column labeled totvalue.So, we use SELECT, FROM, and AS clauses to create the query. In the SELECT clause, we multiply the on_hand_qty and price columns and name it totvalue using the AS keyword. In the FROM clause, we specify the product table. Finally, we end the query with a semicolon.SQL Query:SELECT (on_hand_qty * price) AS totvalueFROM product;
Learn more about SQL query: https://brainly.com/question/25694408
#SPJ11
Describe one activity that belongs to the organizing phase software engineering.
Answers
Answer:
Initiation
Explanation:
The initiation phase typically begins with the assignment of the project manager and ends when the project team has sufficient information to begin developing a detailed schedule and budget. Activities during the initiation phase include project kickoff meetings, identifying the project team, developing the resources needed to develop the project plan, and identifying and acquiring the project management infrastructure (space, computers).
Linux uses a logical directory tree to organize files into different folders.
True or False?
Answers
True. Linux uses a logical directory tree to organize files into different folders. Linux uses a tree-like structure to store and arrange files in directories.
A directory, also known as a folder, is a container for files and other directories. It contains all of the data associated with the files stored in it, such as the file's content and metadata. Linux's directory tree is hierarchical, with directories branching out from the root directory to the other directories.
All of the directories in the tree are related to one another. The top-level directory is the root directory, denoted by a forward slash (/). This directory contains all other directories and files in the file system. As the system administrator, you can create new directories and files in the appropriate folders, assign users and groups to them, and set permissions. Linux directory system provides an organized method for keeping track of files and folders, making it easy to find and manage files. The Linux file system's logical tree structure allows for more secure and efficient access to files. It is an important aspect of the Linux operating system and one that is frequently referenced when dealing with its many features.
To know more about Linux visit :
https://brainly.com/question/33210963
#SPJ11
the frequency that vendor patches are applied varies by organization. you are responsible for the it environment at a local small-medium business which has both windows and linux servers on-site. how frequently should the servers be patched and why? if you make any assumptions be sure to state them.
Answers
It is recommended that servers be patched at least once a month in order to keep the IT environment secure and up to date.
This is because new vulnerabilities are constantly being discovered and exploited, and it is important to stay ahead of potential threats. However, it is also important to test patches before applying them to the production environment, as they can sometimes cause issues or conflicts.
Assumptions:
- The organization has a test environment where patches can be tested before being applied to the production environment.
- The organization has the resources and staff to dedicate to monthly patching.
It is important to note that the frequency of patching may vary depending on the specific needs and resources of the organization. Some organizations may choose to patch more frequently, such as every week or every other week, while others may choose to patch less frequently, such as every quarter. The key is to find a balance between keeping the environment secure and minimizing the potential for issues caused by patches.
Learn more about the frequency of patching:
https://brainly.com/question/18304540
#SPJ11