a user calls into service desk to ask for assistance locating a specific file. the user is not familiar with their macbook and is unable to locate the missing file from a list of over 700. andy, being the service desk technician, shows the user how to locate the folder. he clicks the search icon on the right side of the file, the menu bar and a search bar are then populate. the user was then able to search for the folder they were looking for. what is the process that andy used to assist in finding the lost folder?
Answers
Employ Spotlight: Double-click the file in the search results after starting Spotlight and typing in the file name. View Spotlight's Search page; Look at in the Finder: Select View > Group By > Date Last Opened by selecting the Finder icon in the Dock, selecting Recents in the Finder pane, and finally. Choose View > Use Groups if you can't find Group By in the View menu.
A help desk is what?When an IT user needs assistance, they can call a help desk, which can be an individual, a group, an organizational function, or an outside service.
IT support: What is it?In its broadest sense, IT support refers to any kind of technical support given to people or businesses for hardware or software. Typically, it concentrates on aiding a user in troubleshooting a particular issue.
To know more about service desk visit :-
https://brainly.com/question/15544717
#SPJ1
Related Questions
Normally, by the time teenagers have finished high school, they have formed their own identities and belief systems and have less
need for
against authority figures.
Answers
Answer:
The answer is rebellion
Explanation:
I took the test.
Answer:
rebellion
Explanation:
___________ is the number of pixels per inch
Answers
Answer:
Explanation:
What ever the number is inches is divide it by pixels
Kenny works with an IT company. His company is about to launch new software in the market. He has to ensure that this new software is functional and meets all of the quality standards set up at the planning stage. Which job profile is Kenny likely to have?
Kenny is likely to have the job profile of a _______.
Answers
The job profile that Kenny is likely to have is software analyst.
What is a job profile?This is known to be that which states the details of an employee in regards to their job.
Note that a software analyst is known to be that person who examines and maintain the software development process, carry out configuration management, and others.
So, The job profile that Kenny is likely to have is software analyst.
Learn more about job profile from
https://brainly.com/question/3700565
#SPJ1
Compare and contrast the features of the four computer career fields. Write a paragraph on each and specify how the four career options differ from each other, and explain how they are similar to each other. For your research, you can browse through the Bureau of Labor Statistics website.
Answers
1.Big data engineer · 2. Applications architect · 3. Web developer · 4. Database administrator.
What is computer ?
A computer is a device that may be configured to automatically perform series of mathematical or logical operations (computation). Modern digital computers are capable of running programmes, which are generalised sets of operations. These apps give machines the ability to carry out a variety of tasks. A computer is a minimally functional computer that contains the peripheral devices, operating system (primary software), and hardware required for proper operation. This phrase may also apply to a collection of connected computers that work as a unit, such as a computer system or group of computers. Computers are used as control systems in a wide range of commercial and industrial goods.
To know more about computers visit:
brainly.com/question/21474169
#SPJ1
A film producer is having difficulty with distribution. After major and minor theaters show no interest in the film, what would the logical next move be for him to take?
release the soundtrack on compact disc
make a sequel
give up
pursue Internet distribution
Answers
Answer:
pursue internet distribution
Explanation:
Answer:
B: pursue internet distribution
Explanation:
edg2021

indicate whether each system or process supports routine processes or decision making by selecting the appropriate circle. system or process routine processes decision making 1. accounting information system (ais) 2. expert system 3. executive support system (ess) 4. management information system (mis) 5. data warehouse 6. neural networks 7. decision support system (dss) 8. business intelligence (bi) 9. executive information system (eis) 10. artificial intelligence (ai) 11. enterprise resource planning (erp) 12. intelligent agents 13. robotic process automation (rpa)
Answers
Indicate whether each system or process supports routine processes or decision making by selecting the appropriate circle:
1. accounting information system (ais).
2. expert system✓
3. executive support system (ess)
4. management information system (mis)
5. data warehouse
6. neural networks✓
7. decision support system (dss)
8. business intelligence (bi)✓
9. executive information system (eis)
10. artificial intelligence (ai)✓
11. enterprise resource planning (erp)
12. intelligent agents✓
13. robotic process automation (rpa)✓
Routine processesRoutine processes refer to regular and predictable business procedures. Routine procedures are typically systematized and automated to ensure that each step of the process is completed in the same manner every time.
Decision making is not required in routine procedures, which include everyday activities like as stocking shelves or running payroll.
Decision making is the process of selecting one option from among many alternatives. Decision making is the act of selecting the best option from a group of choices based on available information. It is not a system, but rather a process that occurs throughout the organization, particularly at the managerial level.
Learn more about decision making at
https://brainly.com/question/13244895
#SPJ11
you are running out of time and budget for your game development project you had great ideas for making a randomized highly customizable game experience with high levels of emerg but now you can only fit in the features of one of those qualities highly immersive highly randomize or highly customized briefly describe your imaginary games style then explain which of these three qualities would be best to implement in that type of game on a limited budget
Answers
My games style in terms of their qualities will be made up of:
Movement from Attack to Defense.Set up Defense.Movement from Defense to Attack. Set Pieces. What is a game style?Game style is known to be a term that is made or used by coaches, sports scientists, etc., to show the patterns of play in a scenario of team sports.
Therefore, My games style in terms of their qualities will be made up of:
Movement from Attack to Defense.Set up Defense.Movement from Defense to Attack. Set Pieces.Learn more about Games from
https://brainly.com/question/5144258
#SPJ1
What do computers use to represent on and off?
A.0 and 1
B.1 and 2
C.RGB
D.Megabyte
Answers
distinguish between the desktop publishing packages and multimedia packages
Answers
Answer:
___________________________________________________________
Word processing software is used for working with text, while desktop publishing software involves production of documents that combine text with graphics. DTP software is perfect for making flyers, brochures, booklets. This type of software is usually more advanced than word processing apps.
___________________________________________________________
You have created a Web page in HTML. When it fails W3C validation, you try changing the HTML standard to make your code more compliant. But the page fails W3C validation tests each time, regardless of standard. Which element that you used to structure the page is failing to validate
Answers
Answer:
<table>
Explanation:
W3C validation is a test applied to web pages codes, containing HTML, CSS and other important web frameworks, to make sure that they follow the right syntax and semantics prescribed by the W3C - World Wide Web Consortium.
When a web page, or simple an HTML document, passes this test then it shows that the set rules for creating web pages, that can be easily rendered across many browsers, have been well followed.
There are many reasons why the test may fail. Some of them are highlighted as follows;
i. Not specifying the Doctype at all. For an HTML document to pass the W3C validation test, it is important to specify the Doctype which tells the browser how to treat the document. If HTML is specified as Doctype, then the browser treats the document as HTML. If none is specified, the browser does not know and may have to guess how to treat the document.
ii. Missing closing tags. HTML is a markup language and the use of tags are very important. Many tags have opening and closing parts such as;
<p> </p>.
Some are self closing such as;
<br />
Now, opening a tag and not closing it will make the test fail.
iii. Not completing important child tags. Some tags have child tags that are very important. Child tags are put inside another tag called the parent tag. An example is the <table> tag which has a few child tags such as <tr>, <tbody> e.t.c
Now, when creating a table, according to the W3C specifications, one or more of the <tr> or <tbody> child tag should be inserted.
for the following structure, we have a person variable called bob, and a person pointer variable called ptr, assign ptr to the address of bob. struct person { int age; char letter; };
Answers
The pointer variable `ptr` is assigned to the address of the `bob` variable.
How is the pointer variable assigned to the address of the `bob` variable?In the given structure, there are two variables: `bob`, which is of type `person`, and `ptr`, which is a pointer variable. The `ptr` variable is assigned to the address of the `bob` variable using the address-of operator (`&`). This operator retrieves the memory address of a variable. By assigning `ptr` to the address of `bob`, `ptr` now "points" to `bob` in memory.
This assignment allows us to access and manipulate the `bob` variable indirectly through the `ptr` pointer. For example, we can access the `age` field of `bob` using the arrow operator (`->`) like this: `ptr->age`. This syntax dereferences the pointer and retrieves the value of the `age` field from the `bob` variable.
Learn more about pointer variable
brainly.com/question/33441313
#SPJ11
A new pet supply company plans to primarily sell products in stores. They need a system that will track their large inventory and keep customer sales records.
Which evaluation factor will be most important when choosing technology for the company?
speed
size
storage
connectivity
Answers
The evaluation factor that will be most important when choosing technology for the company is known as storage .
What is an evaluation factor?An Evaluation factor is made up of those key areas that are said to be of importance and tells more about source selection decision.
Note that The evaluation factor that will be most important when choosing technology for the company is known as storage because it is a factor that need to be considered.
Learn more about evaluation factor from
https://brainly.com/question/4682463
#SPJ1
How can get a cup stain off my Chromebook top? Like I tried everything. And I start school on the 1st of September. Plz help me

Answers
Answer:
Try using vinegar or baking soda and water. There's also products for your problem.
Computers that communicate over a network must follow certain ___ to ensure that the transmission is sent properly and understood.
Answers
Computers that communicate over a network must follow certain protocols or rules, in order to ensure that data are transmitted properly and understood.
What is a protocol?A protocol can be defined as a formatted blocks of data that have been designed and established to obey a set of standard rules (conventions) such as the Transmission Control Protocol and Internet Protocol (TCP/IP).
In Computer networking, all computers and other network devices that communicate over a network must follow certain protocols or rules, in order to ensure that data are transmitted properly and well understood by end users.
Read more on protocol here: https://brainly.com/question/17387945
State one criteria that makes a piece of malware a virus.
Answers
Answer: Self replication
Explanation: Malware is a catch-all term for any type of malicious software, regardless of how it works, its intent, or how it's distributed. A virus is a specific type of malware that self-replicates by inserting its code into other programs.
the most powerful computers, , can evaluate complex data very quickly. many of these computers in the united states are owned by the government or major research institutions and can cost $1 million dollars or more.
Answers
The most powerful computers, supercomputers, can evaluate complex data very quickly. Many of these computers in the United States are owned by the government or major research institutions and can cost $1 million dollars or more.
What is a computer?A computer can be defined as an electronic device that is designed and developed to receive data in its raw form as an input and processes these data through the central processing unit (CPU) into an output (information) that could be seen and used by an end user.
What is a supercomputer?A supercomputer simply refers to one of the most powerful computers that is designed and developed for handling, evaluating, and solving very complicated problems or tasks. Additionally, supercomputers have the ability to carry out trillions of calculations per second.
Read more on supercomputer here: https://brainly.com/question/14883920
#SPJ1
Complete Question:
The most powerful computers, _____, can evaluate complex data very quickly. Many of these computers in the United States are owned by the government or major research institutions and can cost $1 million dollars or more.
Queries are a very useful object in a database, please explain why.
Answers
Answer:
they tell the producer what to do to make their website better
Explanation:
Which is the best example of an unreliable narrator?
O A. A guilty criminal
O B. A loyal friend
O C. A strict parent
O D. A bored academic
Answers
Since blockchain technology is public, how are the identities of users protected?
Answers
Blockchain technology is indeed public, but it manages to protect user identities through the following mechanisms.
1. Pseudonymity: Users on a blockchain network interact using pseudonyms, which are randomly generated addresses (combinations of numbers and letters). This means that their real-life identities are not directly connected to their blockchain addresses, providing a layer of privacy.
2. Cryptography: Blockchain technology employs cryptographic techniques like public and private keys. Public keys are visible on the network, while private keys are kept secret by the users. These keys help secure transactions and keep user identities anonymous.
3. Hash functions: A hash function is an algorithm that takes input data and produces a fixed-length output, called a hash. In a blockchain, each transaction and block is represented by a unique hash. This process conceals the original data and helps protect user identities.
4. Zero-knowledge proofs: Some blockchain networks use zero-knowledge proofs, which allow a user to prove they possess certain information without revealing the information itself. This further enhances privacy and prevents the exposure of user identities.
5. Layered solutions: Additional privacy layers, like the Lightning Network for Bitcoin, can be built on top of a blockchain to further improve anonymity by enabling off-chain transactions that don't reveal user identities on the public blockchain.
In summary, blockchain technology protects user identities by using pseudonyms, cryptographic techniques, hash functions, zero-knowledge proofs, and layered solutions. These methods work together to provide a secure and private environment for users, despite the public nature of the blockchain.
For more such question on cryptographic
https://brainly.com/question/88001
#SPJ11
write any four characteristics of desktop computer
Answers
1. What is an AUP? (1 point)
O the abbreviation for the school administrator in an online education environment
a document outlining what is acceptable behavior when using the Internet for schoolwork
a policy outlining the proper formatting to use in Microsoft Office documents for online education
O a short course students can take to understand the school's policies better
Answers
The term AUP is option B: a document outlining what is acceptable behavior when using the Internet for school work.
What is an AUP?An Acceptable Use Policy (AUP) is a set of rules and guidelines that outline the appropriate and responsible use of a school's computer equipment, networks, and other digital resources. It is designed to protect the school's technology infrastructure, as well as the privacy and security of students, teachers, and other users.
An AUP may include guidelines for a variety of activities, such as:
Accessing and using the school's computer networks and equipmentUsing the Internet for schoolwork, research, and communicationProtecting personal privacy and security onlineUsing social media and other online communication toolsDownloading and installing software and appsTherefore, based on the context of the above, i can say that an AUP may also specify the consequences for violating the terms of use, which can include disciplinary action, revocation of access to digital resources, and other penalties.
Learn more about Acceptable Use Policy from
https://brainly.com/question/24951641
#SPJ1
Instructions in the PDFs, must be written in C++.
Answers
Here is an example of how you might implement the movie struct, the add movie function, and the list function in C++:
#include <iostream>
#include <vector>
#include <string>
struct Movie {
std::string title;
std::string actor;
int year;
double rating;
};
void addMovie(std::vector<Movie>& movies) {
Movie newMovie;
std::cout << "Enter the title of the movie: ";
std::getline(std::cin, newMovie.title);
std::cout << "Enter the name of the main actor: ";
std::getline(std::cin, newMovie.actor);
std::cout << "Enter the year the movie was released: ";
std::cin >> newMovie.year;
std::cout << "Enter the rating of the movie (1-10): ";
std::cin >> newMovie.rating;
movies.push_back(newMovie);
}
void listMovies(const std::vector<Movie>& movies) {
std::cout << "List of movies:" << std::endl;
for (const auto& movie : movies) {
std::cout << movie.title << " (" << movie.year << ") - Rated: " << movie.rating << std::endl;
}
}
Note that the addMovie function takes the vector of movies by reference using the '&' operator so that changes made to the vector within the function will persist outside of it. the listMovies take it as read only by const ref.
You can use these functions in your main menu as follows:
int main() {
std::vector<Movie> movies;
int choice;
while (true) {
std::cout << "Main Menu:" << std::endl;
std::cout << "1. Add a movie" << std::endl;
std::cout << "2. List current movies" << std::endl;
std::cout << "3. Exit" << std::endl;
std::cout << "Enter your choice: ";
std::cin >> choice;
std::cin.ignore();
if (choice == 1) {
addMovie(movies);
} else if (choice == 2) {
listMovies(movies);
} else if (choice == 3) {
break;
} else {
std::cout << "Invalid choice. Please try again." << std::endl;
}
}
return 0;
}
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Why do you think that network and telecommunications security careers are some of the fastest growing in the field of technology? What are the requirements necessary to pursue this career?
Answers
Write an SQL query to answer the following question: Is any instructor qualified to teach ISM 3113 and not qualified to teach ISM 4930?
Answers
an SQL query to answer the question is:
SELECT instructor.instr_name
FROM instructor
JOIN teaches ON instructor.ID = teaches.ID
JOIN course ON teaches.course_id = course.course_id
WHERE course.course_title = 'ISM 3113' AND teaches.qualify = 'Y'
EXCEPT
SELECT instructor.instr_name
FROM instructor
JOIN teaches ON instructor.ID = teaches.ID
JOIN course ON teaches.course_id = course.course_id
WHERE course.course_title = 'ISM 4930' AND teaches.qualify = 'Y';
This query first selects the name of instructors who are qualified to teach ISM 3113 by joining the instructor, teaches, and course tables, and filtering for the course title ISM 3113 and qualified instructors.
It then uses the EXCEPT operator to remove any instructors who are also qualified to teach ISM 4930 by joining the same tables, filtering for the course title ISM 4930 and qualified instructors, and returning their names.
Learn more about ISM 3113: https://brainly.com/question/29236437
#SPJ11
Recently, a serious security breach occurred in your organization. An attacker was able to log in to the internal network and steal data through a VPN connection using the credentials assigned to a vice president in your organization. For security reasons, all individuals in upper management in your organization have unlisted home phone numbers and addresses. However, security camera footage from the vice president's home recorded someone rummaging through her garbage cans prior to the attack. The vice president admitted to writing her VPN login credentials on a sticky note that she subsequently threw away in her household trash. You suspect the attacker found the sticky note in the trash and used the credentials to log in to the network. You've reviewed the vice president's social media pages. You found pictures of her home posted, but you didn't notice anything in the photos that would give away her home address. She assured you that her smart phone was never misplaced prior to the attack. Which security weakness is the most likely cause of the security breach
Answers
Answer: Geotagging was enabled on her smartphone
Explanation:
The security weakness that is the most likely cause of the security breach is that geotagging was enabled on the vice president's smartphone.
Geotagging, occurs when geographical identification metadata are added to websites, photograph, video, etc. Geotagging can be used to get the location of particular place.
In this case, since geotagging was enabled on her smartphone, it was easy for the attacker to locate her house.
What kind of animation is used in the powerpuff girls show??
Answers
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
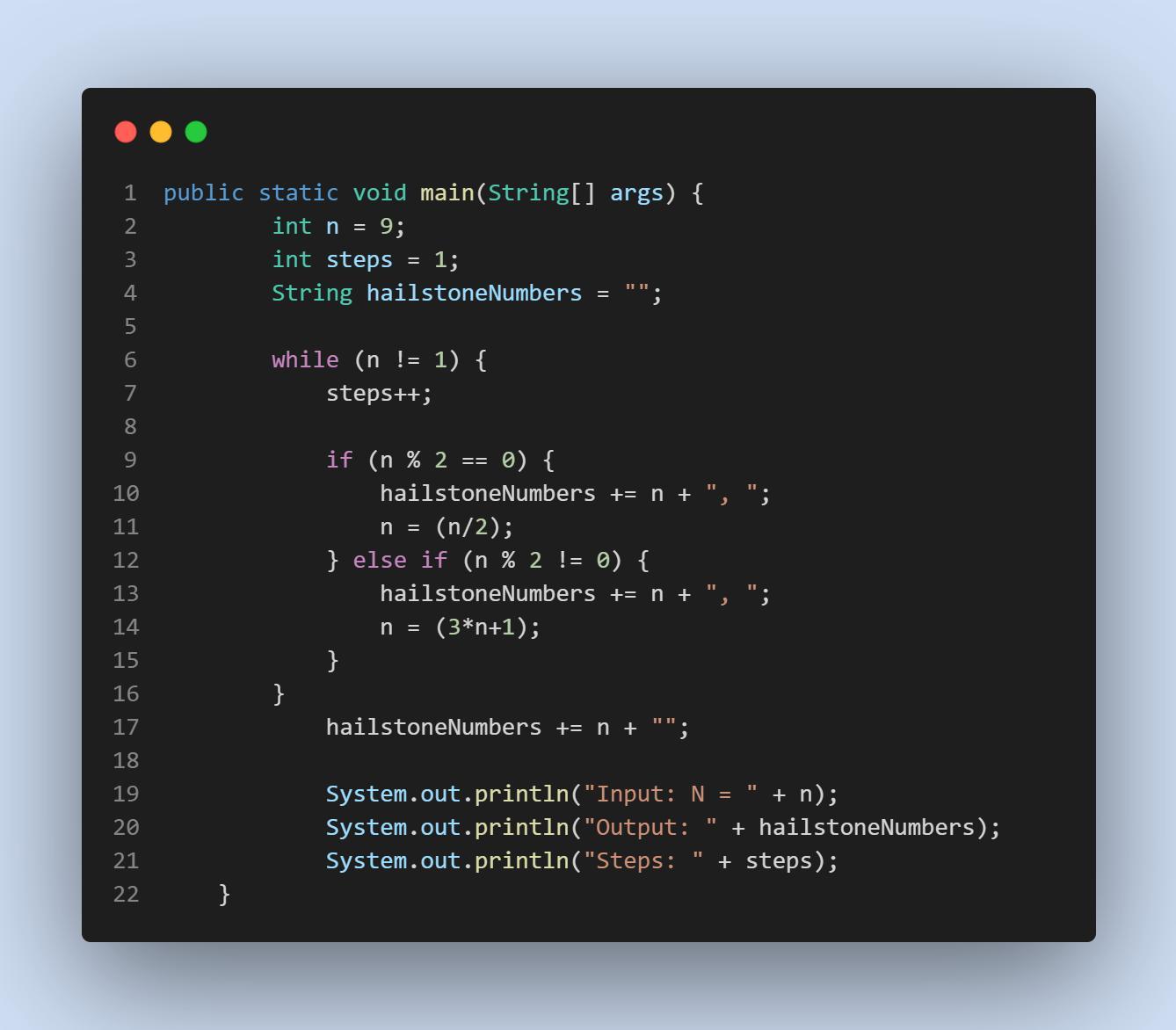
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
e. Define the term ‘user interface’, giving examples.
f. What is a mobile application?
g. Explain briefly what a multi-tasking system is and how it works?
Answers
Answer:
uExplanation:
iiiiiiiiiiiiiiiiiiii
for Jenny's personal computer?
id videos. Which operating
system would be appropriate Jenny's needs to buy a computer to create word documents, make presentations, listen to music, and watch movies and videos.
OA. UNIX
O B. Linux
O C. Microsoft Windows
O D. MS-DOS
Answers
Answer: C
Explanation: Microsoft Windows would be the most viable option here because UNIX and Linux are used for server-side applications, and MS-DOS is an old operating system which is not supported anymore. There is also the Microsoft 365 suite on Microsoft Windows, which can allow Jenny to make presentations using powerpoint, and edit videos.
Creates a table in MS Excel with each of the following accounts and indicates their effect on the expanded accounting equation The 1. in February 2020, Miguel Toro established a home rental business under the name Miguel's Rentals. During the month of March, the following transactions were recorded: o To open the business, he deposited $70,000 of his personal funds as an investment. He bought equipment for $5,000 in cash. O Purchased office supplies for $1,500 on credit. He received income from renting a property for $3,500 in cash. He paid for utilities for $800.00. He paid $1,200 of the equipment purchased on credit from the third transaction. O He received income from managing the rent of a building for $4,000 in cash. He provided a rental counseling service to a client for $3,000 on credit. He paid salaries of $1,500 to his secretary. He made a withdrawal of $500.00 for his personal use. O 0 0 O O 0 00
Answers
To create a table in MS Excel and indicate the effect of each account on the expanded accounting equation, you can follow these steps:
1. Open Microsoft Excel and create a new worksheet.
2. Label the columns as follows: Account, Assets, Liabilities, Owner's Equity.
3. Enter the following accounts in the "Account" column: Cash, Equipment, Office Supplies, Rental Income, Utilities Expense, Accounts Payable, Rental Counseling Service, Salaries Expense, Owner's Withdrawals.
4. Leave the Assets, Liabilities, and Owner's Equity columns blank for now.
Next, we will analyze each transaction and update the table accordingly:
Transaction 1: Miguel deposited $70,000 of his personal funds as an investment.
- Increase the Cash account by $70,000.
- Increase the Owner's Equity account by $70,000.
Transaction 2: Miguel bought equipment for $5,000 in cash.
- Increase the Equipment account by $5,000.
- Decrease the Cash account by $5,000.
Transaction 3: Miguel purchased office supplies for $1,500 on credit.
- Increase the Office Supplies account by $1,500.
- Increase the Accounts Payable (Liabilities) account by $1,500.
Transaction 4: Miguel received income from renting a property for $3,500 in cash.
- Increase the Cash account by $3,500.
- Increase the Rental Income account by $3,500.
Transaction 5: Miguel paid $800 for utilities.
- Decrease the Cash account by $800.
- Decrease the Utilities Expense account by $800.
Transaction 6: Miguel paid $1,200 of the equipment purchased on credit.
- Decrease the Accounts Payable (Liabilities) account by $1,200.
- Decrease the Equipment account by $1,200.
Transaction 7: Miguel received income from managing the rent of a building for $4,000 in cash.
- Increase the Cash account by $4,000.
- Increase the Rental Income account by $4,000.
Transaction 8: Miguel provided a rental counseling service to a client for $3,000 on credit.
- Increase the Rental Counseling Service account by $3,000.
- Increase the Accounts Payable (Liabilities) account by $3,000.
Transaction 9: Miguel paid $1,500 salaries to his secretary.
- Decrease the Cash account by $1,500.
- Decrease the Salaries Expense account by $1,500.
Transaction 10: Miguel made a withdrawal of $500 for his personal use.
- Decrease the Cash account by $500.
- Decrease the Owner's Equity account by $500.
Now, you can calculate the totals for the Assets, Liabilities, and Owner's Equity columns by summing the respective account values. The Assets column should include the totals of Cash, Equipment, and Office Supplies. The Liabilities column should include the total of Accounts Payable. The Owner's Equity column should include the total of Owner's Equity minus Owner's Withdrawals.
By creating this table and updating it with the effects of each transaction, you can track the changes in the expanded accounting equation (Assets = Liabilities + Owner's Equity) for Miguel's Rentals during the month of March.
To know more about MS Excel, visit
https://brainly.com/question/30465081
#SPJ11