A measurement of the percentage of individuals who should have been granted access to a system via biometrics but were not allowed access is called the ________. Group of answer choices
Answers
A measurement of the percentage of individuals who should have been granted access to a system via biometrics but were not allowed access is called the the False Rejection Rate or FRR.
FRR is also known as a type II error in biometric recognition technology. False Rejection Rate (FRR) is the measurement of the percentage of individuals who should have been granted access to a system via biometrics but were not allowed access. It is the probability that the biometric system rejects the right match. FRR is also known as a type II error in biometric recognition technology.
FRR can be calculated by the following formula: FRR = FR / (MR + FR).Where,FR is the number of False RejectionsMR is the number of Genuine Matches.The False Rejection Rate (FRR) plays an essential role in evaluating the performance of a biometric system. It is crucial for authentication because it can reject legitimate users, and it might affect the user experience of the system. If the FRR is high, it means that the system is more likely to reject the authorized users.
Learn more about False Rejection Rate: https://brainly.com/question/16940729
#SPJ11
Related Questions
Which two keys are commonly used to move or insert data?.
Answers
Answer:
control and shift
Explanation:
The two keys that are commonly used to move or insert data is Ctrl and Shift. The correct option is d.
What are shortcut keys?When pressed, a keyboard key will launch a function in the operating system or application.
Shortcut keys, which may involve pressing two or three keys at the same time, are programmed to perform common tasks such as launching a favorite program.
Keyboard shortcuts are commonly used to speed up common operations by reducing input sequences to a few keystrokes, hence the term "shortcut."
To distinguish themselves from standard keyboard input, most keyboard shortcuts require the user to press and hold several keys at the same time or a sequence of keys one after the other.
Ctrl and Shift are the two most commonly used keys for moving or inserting data.
Thus, the correct option is d.
For more details regarding keyboard shortcut, visit:
https://brainly.com/question/12531147
#SPJ2
a) Tab and Ctrl
b) Esc and Shift
c) Alt and Shift
d) Ctrl and Shift
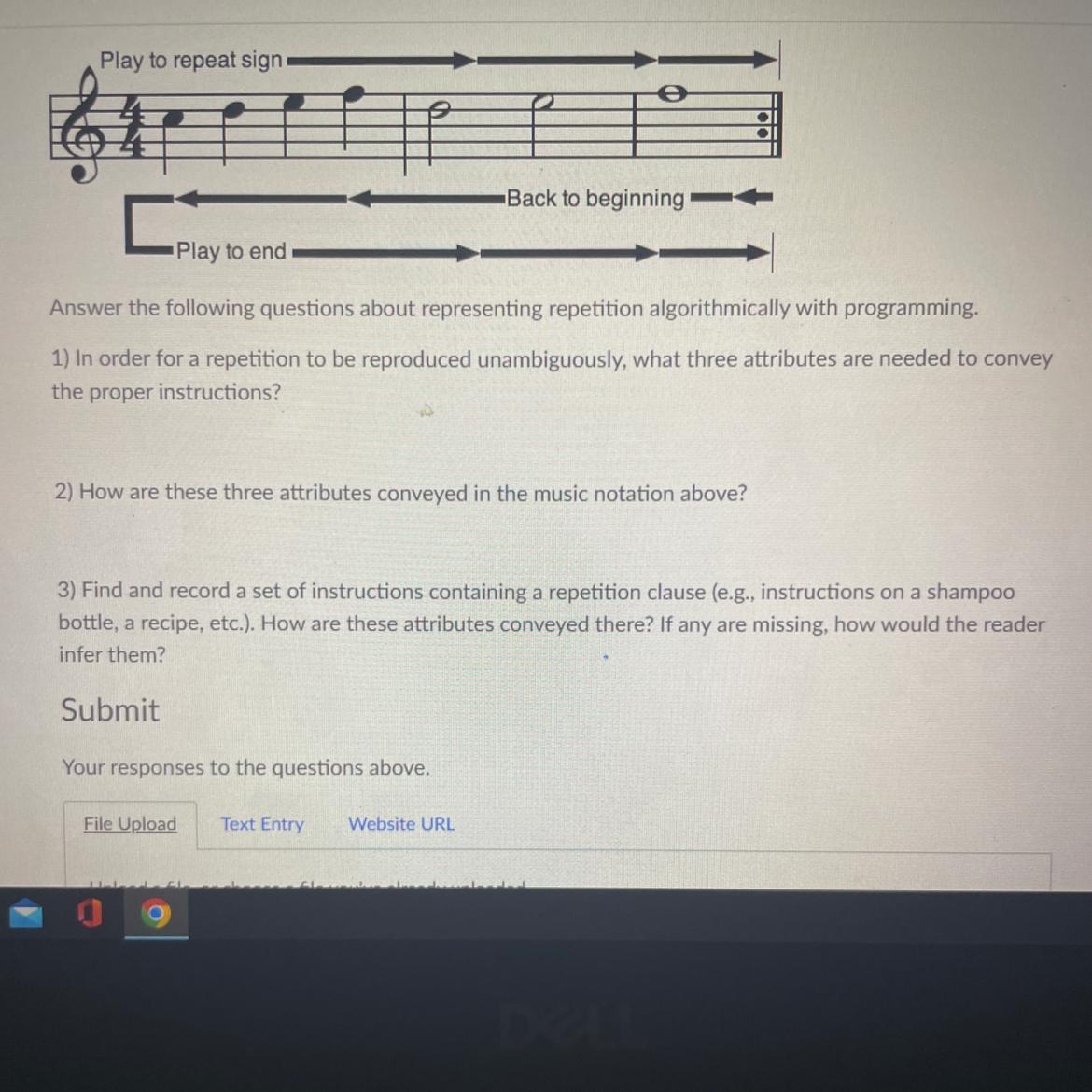
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
Need help computer science

Answers
Answer:
357*7 = 2499 calories
Explanation:
List the steps you can use to change a word document to a Pdf document.
Answers
Answer:
This can be achieved using any of the following ways
1. Save As
2. Export
Explanation:
This can be achieved in any of the aforementioned ways.
# Save As
# Export
The breakdown step is as follows;
#Using Save As
- Open the word document
- Click the FILE tab
- Select Save As
- Browse file destination directory
- Enter file name
- Choose PDF in Select File type
- Click Save
#Using Export
- Open the word document
- Click the FILE tab
- Select Export
- Click Create PDF/XPS Document
- Browse file destination directory
- Enter file name
- Choose PDF in Select File type
- Click Save
which two commands could be used to check if dns name resolution is working properly on a windows pc?
Answers
To view the configured name resolution servers on Windows, type ipconfig /all. Use the ipconfig command to display information about DNS servers. Use the Windows network graphical tool to display information about DNS servers.
What are windows?Windows is a collection of many Microsoft-developed, proprietary graphical operating system families. Each family provides services to a certain sphere of the computing industry. Windows NT, for example, is used by consumers, Windows Server, by servers, and Windows IoT, by embedded systems. A window is a distinct viewing area on a computer screen that is part of a system that supports several viewing areas as part of a graphical user interface ( GUI ). A windowing system's windows are handled by a windows manager. The user can often change the size of a window.Microsoft Windows, often known as Windows and Windows OS, is a personal computer operating system (OS) created by Microsoft Corporation (PCs).To learn more about windows, refer to:
https://brainly.com/question/29892306
DNS resolution refers to the process by which domain names are translated into their corresponding IP addresses. By using both nslookup and ping, you can gather more comprehensive information about the DNS resolution status on your Windows PC.
To check if DNS name resolution is functioning correctly on a Windows PC, you can use the following two commands:
nslookup: The nslookup command is a built-in Windows tool that allows you to query DNS servers and obtain information about domain names and IP addresses. You can use it to check if DNS resolution is working by performing a DNS lookup for a specific domain name. Open the Command Prompt (press Windows Key + R, type "cmd," and hit Enter) and then type the following command:
nslookup example.com
Replace "example.com" with the domain name you want to test. If the DNS resolution is working properly, you should see the corresponding IP address for the domain name.
ping: While ping is primarily used to check network connectivity, it can also indirectly verify DNS resolution. The ping command sends an ICMP echo request to an IP address or domain name and waits for a response. By pinging a domain name, you can determine if it can be resolved to an IP address. Open the Command Prompt and enter the following command:
ping example.com
Replace "example.com" with the domain name you want to test. If the DNS resolution is functioning correctly, you should see responses from the IP address associated with the domain name.
Thereofre, by using both nslookup and ping, you can gather more comprehensive information about the DNS resolution status on your Windows PC.
For more details regarding DNS resolution, visit:
https://brainly.com/question/32414200
#SPJ2
When formulating a linear programming model on a spreadsheet, the decisions to be made are located in the data cells.
a. True
b. False
Answers
Question 7 (1 mark) In a computer information system control procedures that provide reasonable assurance that the recording, processing and reporting of data are properly performed for specific appli
Answers
Control procedures in a computer information system ensure proper recording, processing, and reporting of data for specific applications.
In a computer information system, control procedures play a vital role in maintaining the integrity, accuracy, and reliability of data. These procedures are designed to provide reasonable assurance that the recording, processing, and reporting of data are performed correctly and in accordance with predefined standards and objectives.
Control procedures encompass a range of measures implemented to minimize the risks associated with data manipulation and ensure the system operates effectively. They can include both preventive and detective controls. Preventive controls aim to prevent errors or irregularities from occurring in the first place, while detective controls focus on identifying and correcting errors or discrepancies that may have occurred.
Examples of control procedures include access controls, segregation of duties, data validation and verification, data backup and recovery mechanisms, error handling procedures, and audit trails. These procedures are typically documented and enforced through policies, protocols, and system configurations.
By implementing control procedures, organizations can reduce the risk of data inaccuracies, unauthorized access, and fraudulent activities. They provide a level of assurance that data is processed in a controlled and secure manner, ensuring the reliability of the information produced by the computer information system.
Learn more about control procedures
brainly.com/question/30623695
#SPJ11
Complete the method/function so that it converts dash/underscore delimited words into camel casing. The first word within the output should be capitalized only if the original word was capitalized. Specifications Challenge.toCamelCase(str) given a string with dashes and underscore, convert to camel case Parameters str: String - String to be converted Return Value String - String without dashes/underscores and camel cased Examples str Return Value "the-stealth-warrior" "theStealthWarrior" "A-B-C" "ABC"
Answers
Answer:
I am writing a Python program. Let me know if you want the program in some other programming language.
def toCamelCase(str):
string = str.replace("-", " ").replace("_", " ")
string = string.split()
if len(str) == 0:
return str
return string[0] + ''.join(i.capitalize() for i in string[1:])
print(toCamelCase("the-stealth-warrior"))
Explanation:
I will explain the code line by line. First line is the definition of toCamelCase() method with str as an argument. str is basically a string of characters that is to be converted to camel casing in this method.
string = str.replace("-", " ").replace("_", " ") . This statement means the underscore or dash in the entire are removed. After removing the dash and underscore in the string (str), the rest of the string is stored in string variable.
Next the string = string.split() uses split() method that splits or breaks the rest of the string in string variable to a list of all words in this variable.
if len(str) == 0 means if the length of the input string is 0 then return str as it is.
If the length of the str string is not 0 then return string[0] + ''.join(i.capitalize() for i in string[1:]) will execute. Lets take an example of a str to show the working of this statement.
Lets say we have str = "the-stealth-warrior". Now after removal of dash in by replace() method the value stored in string variable becomes the stealth warrior. Now the split() method splits this string into list of three words the, stealth, warrior.
Next return string[0] + ''.join(i.capitalize() for i in string[1:]) has string[0] which is the word. Here join() method is used to join all the items or words in the string together.
Now i variable moves through the string from index 1 and onward and keeps capitalizing the first character of the list of every word present in string variable from that index position to the end. capitalize() method is used for this purpose.
So this means first each first character of each word in the string starting from index position 1 to the end of the string is capitalized and then all the items/words in string are joined by join() method. This means the S of stealth and W of warrior are capitalized and joined as StealthWarrior and added to string[0] = the which returns theStealthWarrior in the output.

Technician A states that in a brake-by-wire system, the computer detects a
panic stop if the driver quickly releases the accelerator. Technician B states
that brake-by-wire systems are not efficient in detecting panic stops. Who is
correct?
O a. Technician A
O b. Technician B
O c. Both Technician A and Technician B
O d. Neither Technician A nor Technician B
Answers
The brake-by-wire system can detect panic stops if the driver abruptly releases the accelerator, so Technician A is only partly accurate. Technician B is mistaken because panic stops can be accurately detected by brake-by-wire devices.
How well do brake-by-wire devices work at spotting panic stops?That period of time and distance can be cut down in a brake-by-wire device. The driver's abrupt release of the accelerator can be detected by the computer, which could be a sign of a panic halt.
What does an anti-lock braking device (MCQ) do?In order to keep tractive contact with the road surface and give the driver more control over the car, ABS works by preventing the wheels from locking up when braking.
To know more about panic stops visit:
https://brainly.com/question/28779956
#SPJ9
A scientific theory can never be disproven. true or false
Answers
Answer:
false
Explanation:
I just think its false because a theory hasn't become a law and laws cannot be disproven.
Hope this helped!
:)
computer system allows three users to access the central computer simultaneously. Agents who attempt to use the system when it is full are denied access; no waiting is allowed. of 28 calls per hour. The service rate per line is 18 calls per hour. (a) What is the probability that 0,1,2, and 3 access lines will be in use? (Round your answers to four decimal places.) P(0)= P(1)= P(2)= P(3)= (b) What is the probability that an agent will be denied access to the system? (Round your answers to four decimal places.) p k
= (c) What is the average number of access lines in use? (Round your answers to two decimal places.) system have?
Answers
In the given computer system scenario, there are three access lines available for users to access the central computer simultaneously. The arrival rate of calls is 28 per hour, and the service rate per line is 18 calls per hour.
We are required to calculate the probabilities of different numbers of access lines being in use, the probability of an agent being denied access, and the average number of access lines in use.
(a) To calculate the probabilities of different numbers of access lines being in use, we can use the formula for the probability of having k lines in use in a system with three lines, given by P(k) = (1 - p) * p^(k-1), where p is the utilization factor. The utilization factor can be calculated as p = λ / μ, where λ is the arrival rate and μ is the service rate per line.
Using the given values, we can calculate the probabilities as follows:
P(0) = (1 - p) * p^2
P(1) = (1 - p) * p^0
P(2) = (1 - p) * p^1
P(3) = p^3
(b) The probability of an agent being denied access is equal to the probability of all three access lines being in use, which is P(3) = p^3.
(c) The average number of access lines in use can be calculated using the formula for the average number of customers in a system, given by L = λ / (μ - λ). In this case, since there are three lines available, the average number of access lines in use would be L / 3.
By plugging in the values and calculating the probabilities and average number of access lines, we can obtain specific numerical answers.
Learn more about arrival rate here :
https://brainly.com/question/29099684
#SPJ11
Question in photo below

Answers
Answer:
A
Explanation:
(Hope this helps brainliest?) :)
Answer:
I think the answer is A.
Explanation:
because it helps keeps people from being in your stuff you dont want others to see and it will tell your that there might be something going on.
how to implement domain controller?
Answers
Answer:
Log in as an administrator to the Windows 2000 or 2003 server host.
From the Start menu, go to Administrative Tools > Manage Your Server. ...
Install the Active Directory Domain Controller. ...
Install Windows Support Tools. ...
Create a new user account. ...
Create a user account to map to the Kerberos service.
Explanation:
Answer:
Log in as an administrator to the Windows 2000 or 2003 server host.
What is the worst case time complexity of get() in an externally chained hashmap backed by "2-4 trees"
Answers
The worst-case time complexity of the get() operation in an externally chained hashmap backed by "2-4 trees" is O(log n), where n represents the total number of elements in the hashmap.
In an externally chained hashmap, each bucket in the hashmap is associated with a "2-4 tree" data structure. A "2-4 tree" is a balanced search tree where each node can have 2 to 4 child nodes. The tree maintains a sorted order of its elements, allowing for efficient searching.
To perform a get() operation in the hashmap, the key is hashed to determine the appropriate bucket, and then a search is performed within the corresponding "2-4 tree" to find the desired key-value pair.
The worst-case time complexity of searching in a "2-4 tree" is O(log n), where n is the number of elements in the tree. This is because the tree is balanced and ensures a roughly equal number of elements in each level, allowing for efficient searching. Therefore, the get() operation in the externally chained hashmap also has a worst-case time complexity of O(log n), as it relies on the search operation within the "2-4 tree".
Learn more about hashmap here:
https://brainly.com/question/31022640
#SPJ11
Once a business determines that change needs to occur, what ahould the
business create?
A. Business operation
B. Business analysis
C. Business model
D. Business strategy
Answers
Answer:
D. Business strategy
Explanation:
Kono Dio Da!!
Login
c. Unscramble the following wewards and uurite them
Korrectly win the blandes
1.ELLC:
2. RMULAFO:
3.CTIONFUN:
1. COUMNL:
Answers
Answer:
1. Cell
2. Formula
3. Function
4. Column
cmu 2.5.4 scoreboard i need help with all of cmu 2.5.4
Answers
Answer:
Explanation: i can not see your sreeen
The ____ view displays the worksheet the way it will look when it prints.
A) Normal
B) Page layout
C) Break
D) Page settings
Answers
Research the latest advancements in camera equipment and write a report. The research should discuss how these advancements have improved the quality of the final product, and reduced risks in the production process.
Answers
Advancements in camera equipment have significantly improved the quality of the final product and have helped reduce risks in the production process. Here are some of the latest advancements that have made a huge impact on the industry:
1. Mirror less Cameras:- Mirror less cameras are the latest in camera technology. They have no mirror to reflect light into the camera, which makes them smaller and lighter than DSLRs. They are also quieter, faster, and offer better image quality. They are a game-changer for the industry.
2. Auto focus:- The latest auto focus systems are incredibly fast and accurate. They can track subjects, predict their movement, and adjust focus as needed. They make shooting in challenging conditions much easier, and they help to ensure that shots are in focus.
3. High Dynamic Range (HDR):- HDR is a feature that allows for better detail and color reproduction in the highlights and shadows of an image. HDR images look more realistic and more natural than images shot without it. HDR is a standard feature in many modern cameras.
4. In-Body Image Stabilization (IBIS):- IBIS is a feature that stabilizes the camera's sensor, which helps to reduce camera shake and produce sharper images. It is particularly useful when shooting in low light or when using longer lenses. It also helps to make handheld video footage smoother and more stable.
5. Wireless Connectivity:- Many modern cameras have built-in Wi-Fi and Bluetooth connectivity. This makes it easy to transfer images and videos to a smartphone or computer, and it also makes it possible to control the camera remotely.
6. Artificial Intelligence (AI) and Machine Learning (ML):- AI and ML are being used in cameras to make them more intelligent. For example, some cameras can recognize faces, detect smiles, and track subjects. This helps to make shooting easier and more efficient.
In conclusion, advancements in camera equipment have helped improve the quality of the final product and have reduced risks in the production process. These latest advancements in technology, such as mirrorless cameras, autofocus, HDR, IBIS, wireless connectivity, AI, and ML, have made a huge impact on the industry.
For more such questions on camera, click on:
https://brainly.com/question/26320121
#SPJ8
please answer as soon as possible and don't write wrong answer .wrong answer will be reported and correct answer will be marked as brainiest

Answers
Answer:
a sprite
6 operator boolean blocks
11 operator reporter blocks
trojan/ trojan horse
a podcast
a container
the trash
Explanation:
This program has a bug. When the green flag is clicked, nothing happens.
How would you fix it?
Answers
Connect the event block directly to the “repeat” block *if it is Scratch that is)
using the "groups of 4" method in reverse. ch of the following hexadecimal numbers to its equivalent binary representation a) D b) 1A c) 16 d) 321 e) BEAD
Answers
The "groups of 4" method involves breaking down the hexadecimal number into groups of 4 digits and then converting each group into its equivalent binary representation. To convert a hexadecimal digit to binary, you can use the following table:
Hexadecimal | Binary
--- | ---
0 | 0000
1 | 0001
2 | 0010
3 | 0011
4 | 0100
5 | 0101
6 | 0110
7 | 0111
8 | 1000
9 | 1001
A | 1010
B | 1011
C | 1100
D | 1101
E | 1110
F | 1111
Now, let's apply this method in reverse to each of the given hexadecimal numbers:
a) D = 1101 (group of 4: D)
b) 1A = 0001 1010 (groups of 4: 1A)
c) 16 = 0001 0110 (groups of 4: 16)
d) 321 = 0011 0010 0001 (groups of 4: 0321)
e) BEAD = 1011 1110 1010 1101 (groups of 4: BEAD)
Learn more about Binary Representation: https://brainly.com/question/13260877
#SPJ11
The "groups of 4" method involves breaking down the hexadecimal number into groups of 4 digits and then converting each group into its equivalent binary representation. To convert a hexadecimal digit to binary, you can use the following table:
Hexadecimal | Binary
--- | ---
0 | 0000
1 | 0001
2 | 0010
3 | 0011
4 | 0100
5 | 0101
6 | 0110
7 | 0111
8 | 1000
9 | 1001
A | 1010
B | 1011
C | 1100
D | 1101
E | 1110
F | 1111
Now, let's apply this method in reverse to each of the given hexadecimal numbers:
a) D = 1101 (group of 4: D)
b) 1A = 0001 1010 (groups of 4: 1A)
c) 16 = 0001 0110 (groups of 4: 16)
d) 321 = 0011 0010 0001 (groups of 4: 0321)
e) BEAD = 1011 1110 1010 1101 (groups of 4: BEAD)
Learn more about Binary Representation: https://brainly.com/question/13260877
#SPJ11
when does iron most likely to develop rust on it
Answers
When you connect several home devices using a wireless router, what network topology are you using? A. bus B. mesh C. star D. ring
Answers
Answer:
Star Topology
Explanation:
Because the definition of Star Topoplogy is: In star topology each device in the network is connected to a central device called hub. Unlike Mesh topology, star topology doesn’t allow direct communication between devices, a device must have to communicate through hub. If one device wants to send data to other device, it has to first send the data to hub and then the hub transmit that data to the designated device.
Fill in the blank with the correct response.
If you display an image at a size that is smaller than the image size, the view on the website will be _____.
(no answer choices)
Answers
Which option in Outlook allows a user to look at multiple calendars in a side-by-side fashion?
Select multiple calendars.
Select multiple calendars and choose Overlay.
Select a single calendar.
This is not possible.
Answers
Answer:
Its A
Explanation:
I just took the review
Answer: a
Explanation: its a on edge
What is the cell name of the cell where the age of Kim is located?
Answers
In Excel, every individual cell has a distinct identity that is represented by its own unique cell reference or name. Here is how to ID them.
How can you identify the cell name?This identity comprises both its column letter and row number designation. To illustrate further, consider a cell situated in the first column and first row; such a cell will have the name "A1."
Moreover, another cell positioned at the third column and fifth row will have an entirely different identity known as "C5."
Note that once a particular Excel web page loads up onto your device screen with any selected cell on it, you can easily see that chosen spot's appropriate title written inside an indicant box found atop of program dashboard.
Learn more about cell at:
https://brainly.com/question/14780601
#SPJ4
Which patient is undergoing aquatic therapy with therapeutic exercises? What is the length of the session? Who is the therapist in charge?
a. Tierra Falls, 15 minutes, Bridgette McClain
b. Tierra Falls, 30 minutes, Jonathan Risk
c. Tierra Falls, 30 minutes, Bridgette McClain
d. Robbie Koehler, 30 minutes, Steven Wilder
Answers
The answer is c. Tierra Falls, 30 minutes, Bridgette McClain.
What is aquatic therapy?Aquatic therapy is a type of physical therapy that involves exercises performed in a pool under the supervision of a licensed therapist. It is a low-impact form of therapy that can help patients recover from a variety of injuries or conditions, including chronic pain, arthritis, and post-surgical rehabilitation.
The patient undergoing aquatic therapy with therapeutic exercises is Tierra Falls, as indicated in options a, b, and c.
The length of the session is 30 minutes, as stated in options b and c. The therapist in charge is Bridgette McClain, as mentioned in option c.
The therapist in charge of Tierra Falls' aquatic therapy session is Bridgette McClain, who is likely a licensed physical therapist or aquatic therapist trained to provide specialized care for patients undergoing aquatic therapy.
McClain will be responsible for designing and supervising Falls' therapy plan, adjusting it as needed to ensure that it is safe and effective for her specific needs.
To know more about therapeutic visit:
https://brainly.com/question/14598348
#SPJ1
Ill give 100 points to whoever gives me the CORRECT answer. I keep getting syntax errors when I do the "add:" part. Can someone walk me through this code?
Part A One of the biggest benefits of writing code inside functions is that we can reuse the code. We simply call it whenever we need it! Let’s take a look at a calculator program that could be rewritten in a more reusable way with functions. Notice that two floats (decimal numbers, but they can also include integers) are inputted by the user, as an operation that the user would like to do. A series of if statements are used to determine what operation the user has chosen, and then, the answer is printed inside a formatted print statement. num1 = float(input("Enter your first number: ")) num2 = float(input("Enter your second number: ")) operation = input("What operation would you like to do? Type add, subtract, multiply, or divide.") if operation == "add": print(num1, "+", num2,"=", num1 + num2) elif operation == "subtract": print(num1, "-", num2,"=", num1 - num2) elif operation == "multiply": print(num1, "*", num2,"=", num1 * num2) elif operation == "divide": print(num1, "/", num2,"=", num1 / num2) else: print("Not a valid operation.") Your job is to rewrite the program using functions. We have already looked at a function that adds two numbers. Using that as a starting point, we could call the add function from within our program in this way: if operation == “add”: result = add(num1, num2) print(num1, "+", num2,"=",result) Now it’s your turn to do the following: Type all of the original code into a new file in REPL.it. Copy the add function from the unit and paste it at the top of your program. Write 3 additional functions: subtract, multiply, and divide. Pay careful attention to the parameters and return statement. Remember to put the three functions at the top of your Python program before your main code. Rewrite the main code so that your functions are called. Part B There are many different ways that a user could tell us that he or she would like to add two numbers in our calculator program. The user could type “add”, “Add”, “ADD”, or “+”, to name a few possibilities. Of cour
Answers
Answer:
sorry but there is not enough information to complete this
Explanation:
working on rewriting my code so i can paste it here! itll be done in a sec
How to create license in maxon app in 2023
Answers
By dragging and dropping the User onto the License, you can assign a License. To remove a licence from a User, identify the User in the licensing's list of Users and click the X to release the licence.
How do I licence my content?Obtaining written consent from the owner of the copyright is a requirement for licencing digital content. This may be a publisher, author, or rights licencing agency. Then, your team will need to establish what channels you would like to disseminate this content, so you can determine what rights you will need.
How is creative work licenced?To share your work, use the Creative Commons licence selector. Provide details about your project, and it will generate the licence for you. Then copy
To know more about License visit:-
https://brainly.com/question/11355350
#SPJ1