a device is response for making the connection between the local loop and the customer premise equipment, usually a data terminal equipment (dte) device such as a router?
Answers
The statement is true. A device, typically a data terminal equipment (dte) device like a router, is responsible for connecting the local loop to the client premises equipment.
What is data terminal equipment ?Data terminal equipment (DTE) refers to any device that is used to transmit or receive data over a communication link. DTE devices are typically connected to a communication network through a communication interface, such as a modem or network interface card (NIC).Examples of DTE devices include computers, servers, routers, switches, hubs, and other networking equipment. These devices are typically used to transmit and receive data, as well as to perform various functions such as routing, switching, and networking.DTE devices are usually contrasted with data communication equipment (DCE), which refers to devices that provide the physical connection between DTE devices and the communication network. Examples of DCE devices include modems, network interface cards (NICs), and other types of communication interfaces.To learn more about router refer :
https://brainly.com/question/28180161
#SPJ4
Related Questions
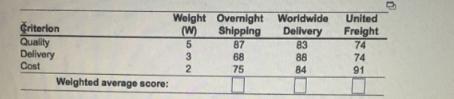
Fernando Garza's firm wishes to use factor rating to help select an outsourcing provider of logistics services. With weights from 1 - 5 (5 being the highest) and ratings from 1 - 100 (100 being the highest), use the following table to help Garza make his decision. In the following table, compute the weighted average score for each of the three companies (enter your responses rounded to one decimal piece). The best outsource provider is Garza decides to increase the weights for quality, delivery, and cost to 10, 6, and 4. respectively. If each weight is doubled, the best outsource provider is How does this change your conclusions? The conclusion changes since the weighted averages change The conclusion changes but the weighted averages do not change at all. The conclusion does not change since the weighted averages do not change at all The conclusion does not change but tho weighted averages change If Overnight Shipping's ratings for each of the factors increase by 10%. what are the new results? Overnight Shipping's ratings for each of the factors increase by 10%, the best outsource provider is with a weighted average score of (enter your response rounded to one decimal place).
Answers
The way that this changes the conclusions is B. The conclusion does not change since the weighted averages do not change at all
How does the conclusion change ?For the second scenario, where the weights for quality, delivery, and cost are doubled to 10, 6, and 4 respectively, the total weight now is 20. However, the relative importance of the three factors has not changed – quality is still the most important, followed by delivery and then cost.
Doubling the weights will not change the relative comparison of the companies and thus the decision will not change. This is why the conclusion will not change as the weights are the same and so are the weighted averages.
Find out more on weighted averages at https://brainly.com/question/24215541
#SPJ4
When you purchase a device, system software is already loaded on it. Which of the following system software settings can you customize?
Answers
Answer:
Screen resolution
Explanation:
The brightness of the words and pictures displayed on computer screen is referred to as screen resolution. Items seem crisper at larger resolutions, such as 1600 x 1200 pixels. They also seem smaller, allowing for more objects to be displayed on the screen. The greater the resolution supported by a display, the larger it is.
i need help pls help me
Answers
Microsoft Access uses the same pure N:M relationships that occur in data modeling. True or false
Answers
The answer is False, in Microsoft Access there is no N: M relationships.
What is N: M relationship?It basically stands for Many-to-Many relationship, N:M connection is a relationship between two entities that may have multiple relationships with each other.
A good example is a book authored by several authors. An Author may have written multiple books at the same time.
In a database, there are three sorts of relationships: one-to-one, two-to-
one, and three to three.one-to-many.many-to-many.Learn more about N: M relationship here:
https://brainly.com/question/15055104
#SPJ1
If a driver update creates a problem, you can __________________ the driver update if the previous drivers were working.
Answers
Answer:
rollback the driver update if the previous drivers were working
what is one advantage offered by vdi over rds and vnc?
Answers
One advantage offered by Virtual Desktop Infrastructure (VDI) over Remote Desktop Services (RDS) and Virtual Network Computing (VNC) is that VDI provides a dedicated, isolated desktop environment for each user.
This means that each user has their own personal desktop with their own settings, applications, and data, which is separate from the desktops of other users. This is in contrast to RDS and VNC, which both share a single desktop environment among multiple users.
The advantage of this is that it provides a more secure and stable environment, as each user's desktop is isolated from the others, reducing the risk of one user's actions affecting the stability or security of the entire system.
It also allows for more flexibility in terms of customizing the desktop environment to meet the specific needs of each individual user, such as different software or configurations.
Additionally, VDI provides better performance, as each user has their own resources and does not have to share them with other users.
VDI also allows for better mobility, as users can access their virtual desktops from any device, as long as it has the necessary client software installed. This allows for users to work from anywhere, at any time, and on any device, which is very useful for organizations that have a remote workforce.
To learn more about VDI, use the link:
brainly.com/question/14763327
#SPJ4
during the installation process for a new device, what are used in order to control how the device driver software is installed?
Answers
Device drivers control the connected peripherals and devices, enabling them to perform tasks that are specific to them. Every connected device to a computer needs a device driver to function.
What is the way the device driver software is installed?Expand the branch associated with the device you want to install when Device Manager launches. Select Update Driver from the menu by performing a right-click on the device.
Therefore, Choose Browse my computer for drivers from the menu that appears on the next screen. Locate the files for the driver installation by clicking the Browse option.
Learn more about device driver here:
https://brainly.com/question/28902184
#SPJ1
When it is aware that the destination address is not present on the other side, then the
blocks the data from crossing it.
Answers
Answer:
answer is c
Explanation:
help pls I will mark brainliest the top answer i need it rn
Nonsense = REPORT
Answer the question 3-5 sentences.
"Why is recycling very important and beneficial to you and your community?"

Answers
Answer:
to reduce outbreak of diseases
Explanation:
materials recycled, funds earned from it are used developmental projects in my community
How does the brain influence your emotions, thoughts, and values?
Answers
Amygdala. Each hemisphere of the brain has an amygdala, a small, almond-shaped structure. The amygdalae, which are a part of the limbic system, control emotion and memory and are linked to the brain's reward system, stress, and the "fight or flight" reaction when someone senses a threat.
What are the effects of the brain?Serotonin and dopamine, two neurotransmitters, are used as chemical messengers to carry messages throughout the network. When brain areas get these signals, we recognize things and circumstances, give them emotional values to direct our behavior, and make split-second risk/reward judgments.Amygdala. The amygdala is a small, almond-shaped structure found in each hemisphere of the brain. The limbic systems' amygdalae control emotion and memory and are linked to the brain's reward system, stress, and the "fight or flight" response when someone perceives a threat.Researchers have demonstrated that a variety of brain regions are involved in processing emotions using MRI cameras. Processing an emotion takes happen in a number of different locations.To learn more about Amygdala, refer to:
https://brainly.com/question/24171355
#SPJ1
A favorably adjudicated background investigation is required for access to classified information
a. True
b. False
Answers
A favorably adjudicated background investigation is required for access to classified information: A. True.
What is a classified source material?In Computer technology, a classified source material is sometimes referred to as classified information and it can be defined as an information source that comprises very important, restricted, and sensitive information that must only be shared and disseminated secretly with authorized persons.
What is an adjudicative process?In Computer technology, an adjudicative process can be defined as a strategic process which typically involves an examination and background investigation of a sufficient period of the life of a person, in order to make an affirmative determination that he or she is eligible for a security clearance and access to a classified source material or classified information.
Read more on classified source material here: brainly.com/question/15346759
#SPJ1
the united kingdom is using what technology to help locate pipes buried underground?
Answers
Answer:
They are using drowsing rods.
Explanation:
Which composer below was not part of the classical period?
A. Beethoven B. Bach
C. Mozart
Answers
Explanation:
B. Bach
Thanks for your point
What is one way sprite properties are the same as variables?
Answers
An element in a 2D list is a_____
Answers
An array is a type of element in a 2D list. A collection of data is stored in an array, although it is frequently more helpful to conceive of an array as a collection of variables of the same type.
What is meant by array?An array is a type of data structure used in computer science that consists of a group of elements (values or variables) with the same memory size and at least one common array index or key. Each element of an array is stored in a way that allows a mathematical formula to determine its position from its index tuple. Multiple values can be stored in a variable called an array. As an illustration, you could make an array to hold 100 numbers. A collection of identically typed objects arranged in a row or column of memory that can each be independently referred to using an index to a special identifier is known as an array.
To learn more about array, refer to:
https://brainly.com/question/28565733
Pasta is best if cooked and served immediately. What do you need to
do to follow this golden rule in presenting pasta dishes?
Answers
sprinkle a little bit of cheese on there, maybe add a few meatballs.
Differences between input device and storage device
Answers
Input, used to interact with, or send data to the computer (mouse, keyboards, etc.) Output, which provides output to the user from the computer (monitors, printers, etc.) Storage, which stores data processed by the computer (hard drives, flash drives, etc.)...
hope this will help u
Answer:
There are three different types of peripherals: Input, used to interact with, or send data to the computer (mouse, keyboards, etc.) Output, which provides output to the user from the computer (monitors, printers, etc.) Storage, which stores data processed by the computer (hard drives, flash drives, etc.)
What is responsible for getting a system up and going and finding an os to load?
Answers
The computer's BIOS (Basic Input/Output System) is responsible for getting the system up and running and finding an operating system to load.
When a computer is turned on, the first piece of software that runs is the BIOS. The BIOS is a small program stored on a chip on the motherboard that initializes and tests the computer's hardware components, such as the CPU, memory, and storage devices. Once the hardware is tested and initialized, the BIOS searches for an operating system to load.
It does this by looking for a bootable device, such as a hard drive or CD-ROM, that contains a valid operating system. If the BIOS finds a bootable device, it loads the first sector of the device into memory and transfers control to that code, which then loads the rest of the operating system. If the BIOS cannot find a bootable device, it will display an error message or beep code indicating that there is no operating system to load.
Learn more about Basic Input/Output System here:
https://brainly.com/question/28494993
#SPJ11
how have computer affected education
Answers
Answer:
It encourage students to procrastinate, and reduces the efficiency of the time they spend in class. Regarding students' belief in their aptitude to multitask
explain the following types of storages
flash disk
Answers
Explanation:
a data storage device that uses flash memory specifically : a small rectangular device that is designed to be plugged directly into a USB port on a computer and is often used for transferring files from one computer to another. — called also thumb drive.
Answer:
storage module made of flash memory chips. Flash disks have no mechanical platters or access arms, but the term "disk" is used because the data are accessed as if they were on a hard drive. The disk storage structure is emulated.
The first flash disks were housed in Type II PC Cards for expanding laptop storage. Subsequently, flash memory disks have arrived in a variety of formats, including entire hard drive replacements (see SSD), memory cards for digital cameras (see flash memory) and modules that fit on a keychain (see USB drive
refers to the increasing accessibility of technology, allowing more people to access information, create content, and develop applications.refers to the increasing accessibility of technology, allowing more people to access information, create content, and develop applications.
Answers
Answer:
Democratization of technology
Explanation:
Democratization of technology refers to the increasing accessibility of technology. More people have better access to the tools needed to view content and create technology solutions of their own.
Answer:
democratization of technology: the increasing accessibility of technology, allowing more people to access and create content and applications
Explanation:
- Edge 2022
What is one example of a servant leader behavior pattern?
- Understands and empathizes with others
- Focuses on individual task metrics
- Thinks about the day-to-day activities
- Uses authority rather than persuasion when necessary
Answers
One example of a servant leader behavior pattern is the ability to A. understand and empathize with others.
Servant leaders prioritize understanding and empathizing with others. They actively listen to their team members, seek to understand their needs, challenges, and aspirations, and show genuine empathy toward them.
They put themselves in others' shoes to gain insight into their perspectives, emotions, and experiences. This understanding and empathy enable servant leaders to support their team members effectively, address their concerns, and provide the necessary guidance and resources for their success.
By focusing on understanding and empathizing with others, servant leaders foster a supportive and collaborative work environment that promotes individual growth and collective achievement.
Learn more about servant leader behavior pattern: https://brainly.com/question/15576767
#SPJ11
From the readings for this week, how has the term
"hacker" evolved since the 1950s? and describe three
"low-tech" methods that hackers have used to obtain
login names and passwords.
Answers
From the readings for this week, the term "hacker" has evolved since the 1950s as follows:In the 1950s and 1960s, hackers were seen as individuals who used their technical skills to develop software solutions to problems they encountered.
The computer security systems were not as strong as they are today, so hacking was more of a skill than a criminal activity.In the 1970s and 1980s, computer hacking began to gain recognition as a criminal activity, thanks to a number of high-profile cyber attacks.
The government, corporations, and private organizations began to pay more attention to computer security, and hacking began to be viewed as a serious threat
.In the 1990s, the public became more aware of hacking due to the increased use of the Internet. Hacking evolved from being just a hobby for computer enthusiasts to a full-blown criminal enterprise with the potential to cause significant damage and financial loss.
Three "low-tech" methods that hackers have used to obtain login names and passwords include the following:
1. Shoulder surfing: This is a technique used by hackers to observe and record login credentials by standing near the target and watching them type in their login information.
2. Dumpster diving: This involves searching through a target's trash for documents or papers containing login information
.3. Phishing: This is a social engineering technique in which hackers use emails or messages to trick the target into revealing their login information.
Learn more about hacking at
https://brainly.com/question/30546365
#SPJ11
having a legitimate reason for approaching someone to ask for sensitive information is called what?
Answers
which of the following are true statements about how the internet enables crowdsourcing? i. the internet can provide crowdsourcing participants access to useful tools, information, and professional knowledge. ii. the speed and reach of the internet can lower geographic barriers, allowing individuals from different locations to contribute to projects. iii. using the internet to distribute solutions across many users allows all computational problems to be solved in reasonable time, even for very large input sizes.
Answers
The following statements are true about how the internet enables crowdsourcing are i & ii.
i. The internet can provide crowdsourcing participants access to useful tools, information, and professional knowledge.
ii. The speed and reach of the internet can lower geographic barriers, allowing individuals from different locations to contribute to projects.
However, the following statement is not true:
iii. Using the internet to distribute solutions across many users allows all computational problems to be solved in reasonable time, even for very large input sizes.
While the internet can allow for distributed computing and parallel processing, not all computational problems can be solved in a reasonable time, even with the power of crowdsourcing.
Some problems may still require significant resources, specialized hardware, or complex algorithms to be solved efficiently, regardless of the number of participants contributing.
For more question on crowdsourcing click on
https://brainly.com/question/14490967
#SPJ11
What are the
advontages of social medio?
Answers
Answer: some advantages are making sure you’re informed about things going on in the world and connecting with you’re friends or even talking to family members. I hope this answered you’re question!
Explanation:
What type of communication takes place between two individuals or parties and involves the use of encryption so that only the desired individuals have access to what is being said or heard
Answers
Answer:
private
Explanation:
Which of the following organizations offers a family of business management system standards that details the steps recommended to produce high-quality products and services using a quality-management system that maximizes time, money and resources?
a
The World Wide Web Consortium (W3C)
b
The Internet Engineering Task Force (IETF)
c
The Institute of Electrical and Electronics Engineers (IEEE)
d
The International Organization for Standardization (ISO)
Answers
Answer:
D
Explanation:
The International Organization for Standardization (ISO) offers a family of management system standards called ISO 9000. ISO 9000 details the steps recommended to produce high-quality products and services using a quality-management system that maximizes time, money and resources.
What is the purpose of a network device?
To allow the computer to store information or programs.
To allow the user to give data or information to the computer.
O
To allow computers to connect and communicate with other computers.
To allow the computer to display or communicate the result of a
computation

Answers
Answer:
c
Explanation:
:)
which is the correct syntax for mapping drive letter w to a shared folder named accounting on the finance server
Answers
Answer:
net use W: \\Finance\Accounting
Explanation: