A customer is having trouble with their hard drives. The computer is not recognizing all the drives in the machine. Your task is to diagnose and correct the problem. In the computer, the top hard drive contains the operating system files. Troubleshoot the hard drives to see why they are not all being recognized. Verify that all drives are detected in the BIOS.
Answers
Check BIOS for all drives; ensure secure connections. If still not recognized, consult technician.
How to troubleshoot unrecognized hard drives?To troubleshoot the issue of the computer not recognizing all the hard drives, we will follow a step-by-step process. Since you mentioned the top hard drive contains the operating system files, we will start by checking the BIOS to ensure that all drives are detected. Here's what you can do:
Restart the computer and enter the BIOS setup. The specific key to access the BIOS may vary depending on the computer manufacturer, but commonly used keys include F2, Del, or Esc. Refer to your computer's manual or manufacturer's website for the exact key.Once you are in the BIOS setup, navigate to the section that displays the connected drives. The location and name of this section may vary depending on the BIOS version and manufacturer.Check if all the hard drives are listed in the BIOS. They should be visible with their respective names and capacities. If any drives are missing or not detected, it indicates a hardware issue or improper connection.If any drives are not listed, check the following:a. Ensure all power and data cables are securely connected to the drives. Sometimes loose connections can cause detection issues.
b. If the drives are connected via SATA cables, try swapping the cables and ports with known working ones to rule out faulty cables or ports.
After verifying the connections, save any changes made in the BIOS (if applicable) and exit the BIOS setup. Allow the computer to boot into the operating system.Once the operating system is loaded, check if the missing hard drives are now recognized. Open "Disk Management" in Windows or use the appropriate disk management utility for your operating system.In Disk Management, verify if the missing hard drives are listed. If they are shown as unallocated space or offline, you may need to initialize the drives and assign them drive letters.If the drives are still not recognized in Disk Management or if you encounter any errors, there might be a hardware issue with the drives themselves. In such cases, it's advisable to consult a professional technician or contact the manufacturer's support for further assistance.By following these steps, you should be able to diagnose and correct the problem of the computer not recognizing all the hard drives.
Learn more about hard drives
brainly.com/question/10677358
#SPJ11
Related Questions
what is the full form of COF ?
Answers
Answer:
COF - Central Operations Facility
Explanation:
COF - Central Operations Facility
Answer:
Central Operations Facility
Explanation:
COF is a place where all facilities usually come from. COF is the biggest facility industry in the world. Nevertheless, it needs other industry to rely on.
Hopefully this answer helps you :)
What is the definition of a nested function?
O a cell that is used in two different functions
O arguments defined inside of two functions
O arguments defined inside of arguments inside of a function
O a function defined inside of another function
Answers
Answer:
d
Explanation:
Answer:
D. a function defined inside of another function
Explanation:
hope this helps :)
This is a python program my teacher assigned:
Create a list of days of the week. (yes, this uses strings)
A) Print each day using a for loop.
B) for non-school days, print “freedom” next to the day of the week.
How would I execute this?
Answers
Answer:
#Create an array for week
week = ["Monday", "Tuesday", "Wednesday", "Thursday", "Friday", "Saturday","Sunday"]
#Create a varable index and use index to loop through week(array)
for index in week:
#if the index is on Saturady or Sunday then, print freedom
if index == "Saturday" or index == "Sunday":
print(index + " Freedom")
#else just pint out the other days
else:
print(index)
What do I click on to add a smooth inner bevel to my text layer ?
Answers
Choose the text layer that you want to emboss and bevel. Select Bevel and Emboss under Layer > Layer Style. Decide on a bevel style. Set the options for Depth, Direction, Size, and Soften. Select a shading technique.
How much text beveled in Illustrator?Normally, after typing your text and selecting it, you would choose Effect > 3D > Extrude & Bevel. You would then choose the Front for Position preset, Classic Bevel, specify the height, and check the Preview option in the dialog box.
The smooth tool is absent from Illustrator 2022.PRO HINT: On Illustrator, the smooth tool may be located in the toolbar next to the "Pencil" tool. You can use it to smudge your drawings' edges. Choose the points you wish to utilize for the curve first in order to produce a smooth curve. The points can be moved around to form the desired shape.
to know more about Illustrator here:
brainly.com/question/17221744
#SPJ1
what is database management?
Answers
Answer:
Database management is the process of organizing, storing, retrieving, and protecting data using a database management system (DBMS). The DBMS is a software application that enables users to interact with the database and manage data efficiently.
Database management involves designing the database schema, creating tables and fields, defining relationships between tables, and ensuring data integrity by enforcing constraints and validation rules. It also involves querying the database using SQL or other programming languages, updating or deleting data, and creating reports or visualizations of data.
you click the "full extent" tool and your data disappears, what is a possible cause of this problem?
Answers
One possible cause of the problem where data disappears after clicking the "full extent" tool could be an **unexpected software glitch or bug**. Glitches in software can lead to unintended consequences, including data loss or unexpected behavior.
The "full extent" tool is typically used to zoom or navigate to the entire extent or coverage of a dataset or map. If a glitch occurs within the software or the tool itself, it might trigger an undesired action, such as inadvertently clearing or removing the data.
Another potential cause could be **user error or accidental selection**. It's possible that the user unintentionally selected an option or performed an action that triggered the removal or hiding of the data. This could happen due to a mistaken click, keyboard shortcut, or unfamiliarity with the tool's functionality.
To resolve the issue, it is advisable to check for any available software updates or patches that might address known bugs. Additionally, verifying user actions and exploring options to restore or recover the lost data may be necessary. It's important to regularly backup data to prevent the permanent loss of important information in case such incidents occur.
To know more about glitch, visit
https://brainly.com/question/30637424
#SPJ11
unified communications (uc) is an umbrella term for integrated, multi-media communications controlled by an individual user for both business and social purposes. uc integrates all of the following except? Select one: a.Social media. b.Data. c.Voice. d.Video
Answers
Unified communications (UC) is an umbrella term for integrated, multi-media communications controlled by an individual user for both business and social purposes. UC integrates all of the following except: b. data.
Unified Communications (UC) is an all-in-one communications system that combines the integration of real-time communication tools like voice, instant messaging (IM), video conferencing, desktop sharing, data sharing, and more, with non-real-time communication tools like email, voicemail, SMS, and fax.The primary objective of Unified Communications (UC) is to unify all communication channels and tools, making communication more straightforward, faster, and more efficient. UC technology also integrates these different channels into a single interface or platform, allowing users to access and manage them all from one place. Therefore, UC integrates all of the following except data.
Learn more about Unified communications: https://brainly.com/question/30177142
#SPJ11
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
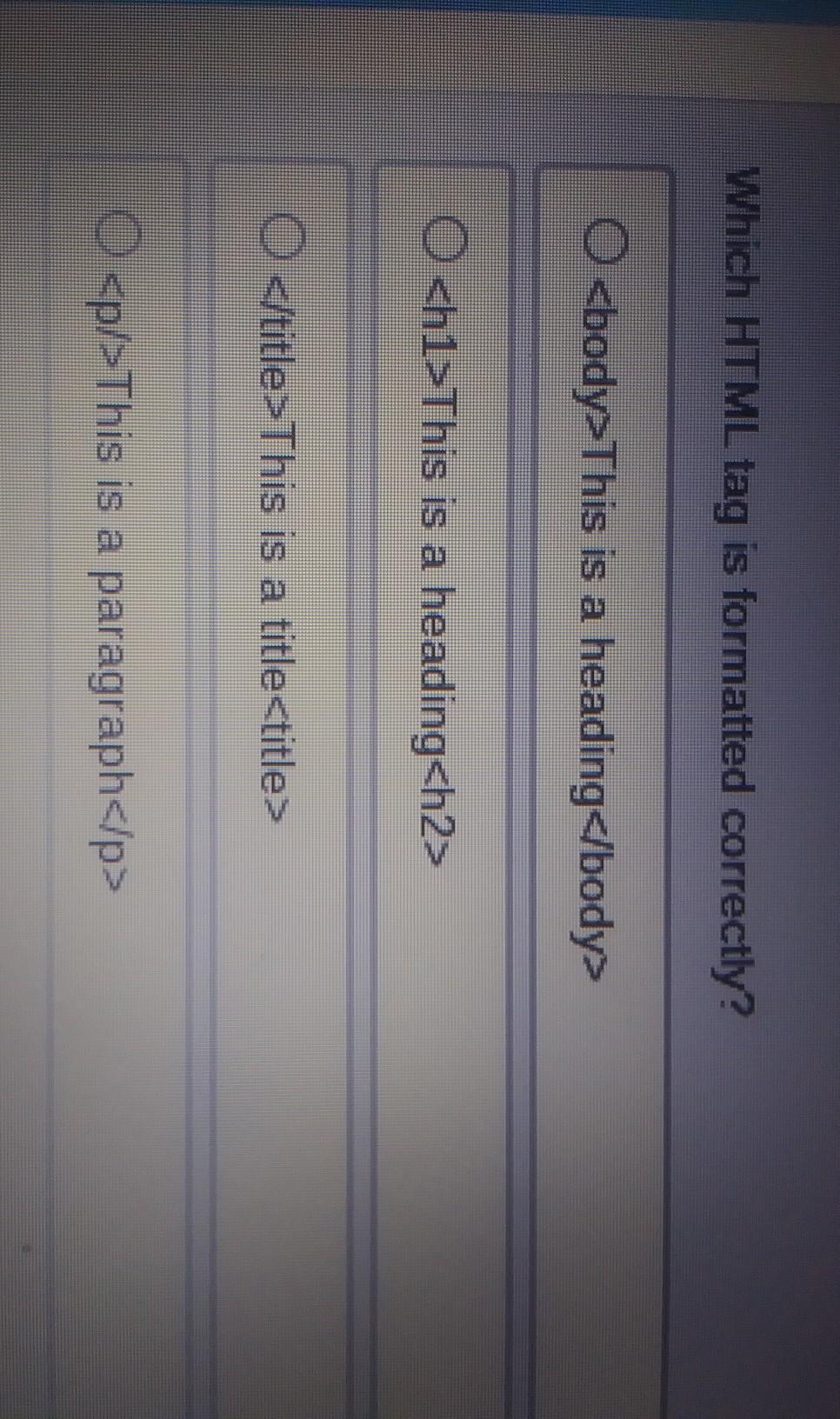
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
What might you see by turning a surface model to a certain angle? *
PLEASE HELP!!! THANK U SO MUCH! GOD BLESS!

Answers
Answer:
Turning a surface model to a certain angle can control whether or not you it can go right or left :)
Explanation:
Neil, a business analyst, needs to analyze and examine a proposed project. Which study will help him do so?
А
study will help Neil analyze and examine the proposed product.
Reset
Next
Answers
Answer:
Business Analysis studies along with Project Management certifications.
Explanation:
Neil is a business analyst. he must have gained business analysis certification or degree in order to become a business analyst. He is now analyzing the proposed project for which he must understand the insight of the project cashflows. He should gain project management certification in order to be able to examine and analyze the project. NPV and IRR are most common techniques used to analyze a project.
Directions: To avoid early damage in the tools, how will you sanitize and store the
following tools in your kitchen. Write your answers in the activity notebook following
the given columns.
Tools Proper Sanitation Proper Storage
Answers
Answer:
1)sterilizing
2)use bleach and water
3)when you wash the measuring spoon,wash them using warm soapy water then rinse them in clear water
4)use a fresh solution of 1 tablespoon of unscented,liquid chlorine bleach per gallon of water
5)let it set in soapy water over night
6)set it in soapy water five minutes and scrub each potter
7)wash mixing bowl in hot ,soapy water to add it to a dishwasher load
8)use a ratio of one part bleach to 20parts of water
9)pour water on thr blender and add dish soap
10)wipe it using clean and smooth towel
Jack is a forensic specialist who wants to examine a network router for potential evidence in a case. What is the first step he should take to safely examine the router
Answers
The step that can be carried by Jack for the safe examination of the router as the case evidence is connecting the router to the network.
What is a network router?The network router is given as the connection between the two networks that mediate the delivery of the packed information.
The safety of the router in the forensic evidence is important as the incorrect connection resulting in corruption and deletes all the data.
Being the specialist, to check the router, the first step to be followed by Jack was connecting the router to the network.
Learn more about routers, here:
https://brainly.com/question/15851772
#SPJ1
You discover that your border router is receiving packets on its external interface with a source address subnet of?
Answers
This is an indication of an IP Spoofing Attack. This is explained in detail below , IP Spoofing is an attack in which attackers forge the source addresses of packets so that the victims end up sending responses to another location.
By changing the source IP address of a packet, an attacker can cause the packet to appear as if it originated from another machine. As a result, the packet will be accepted by the receiving system as if it were legitimate, and a response will be generated and sent back to the spoofed source address.
The first and foremost indication of an IP Spoofing Attack is when a router starts receiving packets with the source address belonging to a different network. When packets with a false source address are received by a router, the router changes the source address to its own address and forwards it to the destination system.
To know more about IP visit:
https://brainly.com/question/29976006
#SPJ11
the following statement creates an arraylist object. what is the purpose of the notation?
Answers
The purpose of the notation <> (diamond operator) in the given statement is to specify the type of objects that the ArrayList will hold.
In Java, the diamond operator <> is used to implement type inference, introduced in Java 7. It allows the programmer to omit the type declaration on the right-hand side of an assignment when the type information can be inferred from the left-hand side. In the context of the statement creating an ArrayList object, the diamond operator is used to provide type information for the ArrayList. For example, consider the statement: ArrayList<String> myList = new ArrayList<>();. Here, the diamond operator <> is used after the ArrayList class to specify that the ArrayList object will hold objects of type String. The type information is inferred from the variable declaration on the left-hand side (ArrayList<String> myList), allowing the programmer to omit the type declaration when creating the object.
The diamond operator simplifies the code by reducing redundancy and improving code readability. It ensures that the ArrayList object created will be of the specified type, in this case, String, and provides type safety during compile-time checks.
Learn more about information here: https://brainly.com/question/31713424
#SPJ11
what is digital native
Answers
A person who was raised in the information age or around digital technology is known as a "digital native."
What is the purpose of digital native?Digital natives are accustomed to and proficient in technology because they were raised in an IT-centric environment.
The generations born after 1980 are referred to be digital natives since they have spent their entire lives surrounded by technology, social media, mobile devices, computers, and the internet.
Therefore, a person who was raised in the information age or around digital technology is known as a "digital native."
To learn more about digital native, refer to the link:
https://brainly.com/question/8450699
#SPJ1
Text books are not a good source for finding ideas about what to study because the teachers make up the test questions. Please select the best answer from the choices provided T F
Answers
Answer:
Text books are not a good source for finding ideas about what to study because the teachers make up the test questions. False- most teachers use the textbooks as guides. Visiting the library to seek books on your current topic will not help you in determining what to study.
Explanation:
Text books are not a good source for finding ideas about what to study because the teachers make up the test questions. False- most teachers use the textbooks as guides. Visiting the library to seek books on your current topic will not help you in determining what to study.
Answer:
False
Explanation: I took the test and passed!!
Which command should you run after installing a new kernel module to update the module dependency database?
Answers
Answer:
depmod
Explanation:
During Iteration planning, the PO introduces multiple new stories to the team. After a lot of discussion, the team decides to insert spikes into the iteration for research. Why is this situation an anti-pattern? a. The team is committing to stories with many unknowns b. The PO and team created spikes c. The team will engage the dependent teams to work on the stories d. The PO and the team arrived at the planning session without preparation
Answers
Answer:
The answer is "Option d".
Explanation:
The Iteration Management is also an activity in which all members of the team will determine how many the backlog team will allocate towards the next Iteration, and each team wraps up the work only as a group of determined iteration targets. in the given question the "choice d" is correct because The plans to achieve without training entered PO or design staff and requirements have not even been identified, and the wrong choice can be defined as follows:
In choice A, T' he PO doesn't give the story detail, that's why it's incorrect. In choice B, the doesn't a team left the past for more refining with the PO in the Project Backlog, that's why it's incorrect. In choice C, The Development Team has not found some other team dependency, that's why it's incorrect.Which of the following is a set of security controls designed to protect payment account security such as a credit card transaction?
CIS Critical Security Control
ONIST Framework
OPII Framework
Payment Card Industry Data Security Standard (PCI DSS)
Answers
technician a says the obd-ii evap system leak test monitor will not run if the fuel level is too high. technician b says the monitor will not run if the fuel level is too low. who is correct?
Answers
Technician A says the OBD-II EVAP system leak test monitor will not run if the fuel level is too high. Technician B says the monitor will not run if the fuel level is too low, so Technician A is correct because the OBD-II EVAP system leak test monitor will not run if the fuel level is too high.
According to Technician A, the OBD-II EVAP system leak test monitor will not run if the fuel level is too high. Technician A is correct because fuel slosh can cause inaccurate readings, and high fuel levels can cause fuel to spill out during testing, resulting in a fire hazard. As a result, when carrying out OBD-II EVAP system leak testing, it is critical to ensure that the fuel level is between one-quarter and three-quarters full.How does the OBD-II EVAP system leak test monitor work?The OBD-II EVAP system leak test monitor operates by comparing the ambient pressure reading to a vacuum reading from the EVAP system through a leak check valve.
Learn more about OBD-II EVAP: https://brainly.com/question/16608402
#SPJ11
Python program to display the mark report. If mark is above 90 Graded A+ If mark is between 80 and 90 Graded A If mark is between 60 and 79 Graded B If mark is less than 59 display Practice well
Answers
Answer:
grade = int(input("Enter grade: "))
if grade>90:
print("A+")
elif grade<90 and grade>80:
print("A")
elif grade>60 and grade<79:
print("B")
elif grade<59:
print("Practice well")
Unlike email, ______ is having a live, online, text-based conversation with one or more individuals. Select your answer, then click Done.
Answers
Unsolicited messages sent in bulk via email are referred to as email spam, junk email, spam mail, or simply spam (spamming).
is a short-range wireless technology that enables phone and text communication without the need for a hand?A short-range wireless technology standard called Bluetooth is used to create personal area networks and exchange data over short distances between stationary and mobile devices (PANs).
Which of the following can store user data even when the computer's power is off?Non-volatile storage is a type of storage that keeps the data current even when the device is not powered by electricity. A solid state drive (SSD) or hard disc drive (HDD) that stores all of the data is an example of this.
To know more about spam mail visit:-
brainly.com/question/30487737
#SPJ1
To which state does a process move when the cpu scheduling algorithm determines it may next use the cpu?
Answers
When a process is in Running state, it may be moved by the CPU scheduling algorithm when it is determined that the process may next use the CPU. This can happen for a variety of reasons, including when the process is preempted by another process or when the process itself voluntarily relinquishes the CPU.
There are two types of process Scheduling algorithms- those that preempt running processes, and those that don't. The preemptive scheduling algorithms are further classified as either voluntary or involuntary.
Voluntary algorithms allow a process to voluntarily relinquish the CPU before its time slice is complete- usually in response to an event like an I/O completion. Involuntary algorithms preempt a running process and move it to a waiting state when another process needs the CPU.
The most common involuntary algorithms are priority-based. A process with a higher priority is given the CPU first, regardless of when it last ran. If two processes have the same priority, then the process that has been waiting the longest is given the CPU next.
Learn more here:
https://brainly.com/question/14400616
#SPJ4
They want to move to a more agile and innovative software development model, in which their developers can focus on application features and functionality, rather than underlying environments and infrastructure. which cloud computing model would provide healthyapp with the framework to help achieve this goal?
Answers
PAAS (platform as a service) is known to be the cloud computing model that would provide healthy app with the framework to help achieve this goal.
What platform is a service PaaS?Platform as a service (PaaS) is known to be a kind of a total or complete development and also the deployment of the environment in what is known to be the cloud.
Note that this is often done with resources that helps a person to be able to send everything via the use of a simple cloud-based apps to any kind of sophisticated, cloud-based firm applications.
Hence, PAAS (platform as a service) is known to be the cloud computing model that would provide healthy app with the framework to help achieve this goal.
Learn more about agile from
https://brainly.com/question/7246595
#SPJ1
It deals with integration approaches and techniques that connect different components of IT infrastructure
Answers
Answer:
Integrative programming.
Explanation:
Software integration can be defined as a strategic process which typically involves the combination of existing software components to build or create a complete system.
Integrative programming deals with the integration approaches and techniques that connect different components of IT infrastructure.
Basically, the different components such as platforms, software applications, databases and people of an information technology (IT) infrastructure are connected through the use of an integration technique or framework in order to facilitate a safe, secure, private (intra) and public (inter) application collaboration.
The main purpose of Integrative programming is to enable business firms or companies to integrate internal and external business processes with their business partners and unlimited sharing of data. Therefore, integrative programming improves the growth and development of a business dynamically.
clock skew is a problem for: group of answer choices address buses. control buses. synchronous buses. asynchronous buses.
Answers
Clock skew is a problem for synchronous buses.
Clock skew is a problem primarily for synchronous buses because these buses rely on a common clock signal to coordinate data transfer and communication among various components in a system. In synchronous buses, all operations occur at specific points in time based on the clock signal, and if the clock signals arrive at different times for different components (clock skew), it can lead to incorrect or unpredictable results.
Asynchronous buses, on the other hand, do not rely on a common clock signal and use other methods, such as handshaking, to coordinate communication, making them less susceptible to clock skew issues.
You can learn more about clock signals at: brainly.com/question/17417288
#SPJ11
Which of the following would include a company's audited annual financial statements with no spin?
Answers
The option that would include a company's audited annual financial statements with no spin is: "10-K filing." (Option A)
Why is this so?A 10-K is a thorough report on a public company's financial performance that is filed yearly. The Securities and Exchange Commission (SEC) requires the report, which is significantly more extensive than the annual report.
This form must be filed within 60-90 days of a company's fiscal year ending, which may or may not coincide with the end of the calendar year. The 10-K is published online, through the SEC database, and on a company's website.
Learn more about annual financial statements at:
https://brainly.com/question/13161732
#SPJ1
Which of the following would include a company's audited annual financial statements with no spin?
O 10K
O 10-0
O Earnings Estimates
O Annual Report
Klout was hyped as a platform that could track online influence but became inactive. Why?.
Answers
Scalzi, in his CNN Money column, makes a witty remark about Klout practically sucking in data from all social media platforms and "throwing it into an algorithmic pot."
As a result, Peter Hess, Khoros's then-CEO, sent out a message indicating that Klout had finally lost its Klout.
How did Klout went down?Even though some people took Klout seriously, Andrew Hutchinson writes for a social media website that its critics saw it as "a vanity metric - and like all vanity metrics, it can be gamed, it can be cheated, and thus it's rendered largely useless" .
Lithium Technologies confirmed earlier rumors that it had purchased Klout for about $200 million in March 2014. For businesses to create online communities, Lithium offered the necessary tools. After it combined with Spredfast (a company that specializes in social media marketing, community management, and software), it ceased to exist as a separate entity and was renamed Khoros LLC.
Learn more about Klout
https://brainly.com/question/11383000
#SPJ1
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future
Answers
Answer:
The organization could make it so that specific websutes that seem fake/unsafe are not accessible to the users. For example, downloading an extension into all the devices, that blocks these malicious websites (uBlock Origin)
I NEED an example of output plssss