A 4"x6" photo is digitized using 10,000 pixels. An 11"x7" photo is digitized using 30,000 pixels. Which image will have the better resolution?
the 11"x7" photo
the 4"x"6 photo
the photos will have the same resolution
Answers
An image which will have the better resolution is: A. the 11"x7" photo.
What is a camera lens?A camera lens can be defined as a transparent optical instrument that is used in conjunction with a digital camera, so as to refract rays of light coming into the lens.
What is a resolution?A resolution can be defined as the number of pixels that are contained in an image (picture or photo) or on a display monitor of a computer system such a laptop.
In this scenario, we can infer an logically deduce that an image which will have the better resolution is the 11"x7" photo because it has a higher number of pixel (30,000 pixels) than the 4"x"6 photo.
Read more on resolution here: https://brainly.com/question/14294025
#SPJ1
Related Questions
Python - Write a program to print the multiplication table as shown in the image by using for loops.

Answers
Answer:
Explanation:
The following python code creates the multiplication table for 10 rows and 10 columns. This code uses nested for loops to traverse the table and print out the product of each multiplication. The image attached shows the output of the code.
for x in range(1, 11):
for y in range(1, 11):
z = x * y
print(z, end="\t")
print()

The program to print the multiplication table as shown in the image by using for loops is in the Source code.
The Python program that uses nested for loops to print the multiplication table:
Source code:
for i in range(1, 11):
for j in range(1, 11):
if i == 1 and j == 1:
print("x", end=" ")
elif i == 1:
print(j, end=" ")
elif j == 1:
print(i, end=" ")
else:
print(i * j, end=" ")
print()
This program will iterate through the values of `i` from 1 to 10 and `j` from 1 to 10. It checks for special cases when `i` or `j` is equal to 1 to print the headers (x and the numbers 1 to 10).
For other cases, it calculates the multiplication of `i` and `j` and prints the result.
Learn more about Nested loop here:
https://brainly.com/question/33832336
#SPJ6
(25 POINTS) Some applications work on all devices while others work on some devices. True or False?
Answers
Answer:
True.
Explanation:
It is true that some applications work on some devices but not on others. This is so because it depends on the operating system of each device, that is, if the device has an operating system compatible with the application in question, said application will work, but if, on the contrary, the operating system is not compatible, the application will not be useful in this.
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
1. List five types of information data brokers are collecting about
you.
2. What is Disconnect?
Answers
Data brokers collect a wide variety of information, such as personal, demographic, and behavioral data. Disconnect is a software application designed to help protect users' online privacy and security.
Data brokers might collect the following types of information: (1) Personal details like name, age, gender, and contact information, (2) Online activities, including browsing history and social media behavior, (3) Financial information, such as credit scores, income, and purchasing habits, (4) Demographic details, including education level, marital status, and family size, (5) Health-related data, including medical conditions and insurance information. Meanwhile, Disconnect is an app that blocks trackers to improve browser speed and performance while ensuring your online privacy. It protects against unwanted tracking and encrypts your internet connection, enhancing your overall online experience and ensuring your data isn't harvested without your consent.
Learn more about data brokers here:
https://brainly.com/question/12448881.
#SPJ11
Write a method that is passed an array, x, of doubles and an integer rotation amount; n. The method creates a new array with the items of x moved forward by n positions. Elements that are rotated off the array will appear at the end. For example, suppose x contains the following items in sequence: 1234567 After rotating by 3, the elements in the new array will appear in this sequence: 4567123 Array x should be left unchanged by this method. Use the following code to help you get started. Be sure to test your program with different rotation amounts.
Answers
We can see here that writing a method that is passed an array, x, of doubles and an integer rotation amount; n, we have below:
What is an array?An array is a data structure that stores a fixed-size sequence of elements of the same type. It provides a way to organize and access a collection of values in a contiguous block of memory. Each element in the array is identified by its index or position within the array.
Below is the code that reveals a method that is passed an array, x, of doubles and an integer rotation amount; n.:
public class ArrayRotation {
public static double[] rotateArray(double[] x, int n) {
int length = x.length;
double[] rotatedArray = new double[length];
for (int i = 0; i < length; i++) {
int newPosition = (i + n) % length; // Calculate the new position after rotation
rotatedArray[newPosition] = x[i]; // Move the element to the new position
}
return rotatedArray;
}
public static void main(String[] args) {
double[] x = {1, 2, 3, 4, 5, 6, 7};
int rotationAmount = 3;
double[] rotatedArray = rotateArray(x, rotationAmount);
// Display the original and rotated arrays
System.out.println("Original array: " + Arrays.toString(x));
System.out.println("Rotated array: " + Arrays.toString(rotatedArray));
}
}
Learn more about array on https://brainly.com/question/19634243
#SPJ4
over time, you have noticed unauthorized configuration changes made to virtual machine cloud settings. you need a way to track who made these changes and when. what should you do?
Answers
One way to track who made these changes to the virtual machine cloud settings and when is to: D. enable cloud resource activity auditing.
What is a cloud?In Computer technology, a cloud can be defined as the elastic leasing of pooled computer resources such as physical hardware through virtualization and over the Internet, so as to enable the storage and sharing of files and documents virtually and in real-time.
In this scenario, we can reasonably infer and logically conclude that one way to track who made these changes to the virtual machine cloud settings and when is to enable cloud resource activity auditing because it would provide a log of actions such as information about the engineer who made configuration changes.
Read more on a virtual machine here: https://brainly.com/question/12060797
#SPJ1
Complete Question:
Over time, you have noticed unauthorized configuration changes made to virtual machine cloud settings. You need a way to track who made these changes and when. What should you do?
A. Enable virtual machine API integration.
B. Rotate the cloud access keys.
C. Deploy an OSI layer 7 firewall.
D. Enable cloud resource activity auditing.
Which punctuation mark should go in the underlined space to show a break in the speech?
Michael said, "Let's find the ___"
. . .
—
'
.
Answers
Answer:
...
Explanation:
The elipses show a pause while showing that the information is relevant
Answer:
its a
Explanation:
Check all that apply to Raster Graphics
in photoshop
only use certain colors
infinitely scalable
made from pixels
based on math
limited scalability
Answers
Answer: made from pixels, limited scalability
Explanation:
everything in PS is made up of pixels and you can see this if you zoom in too much or scale up too much, it will look like Mario 64. It is not like a vector based program, wich uses math to calulate lines so you can scale it indefinetly and it will remain crisp.
Please answer these computer fill in the blanks
1) operators are the _______________ used in formulas to perform a particular calculation
2) the____________feature of Excelhelps to copy the formula quickly
3) Excel provides over ________________used to perform calculations
4) ____________ category of functions includes functions for calculation, and tracking principal and interest
5) ___________ functions returns one of two results you specify based on whether the value is TRUE or FALSE
Answers
Answer:
best
cool
Explanation:
what are the basics to learn for ethical hacking?
Answers
Answer:
1. Run on OS which is similar to UNIX, like Linux. UNIX as well as UNIX-like OS are the operating systems of the Internet. Though a person can learn ...
2. Learn HTML.
3. Gain the knowledge of Programming.
4. Be a Creative Thinker.
5. Make a habit of Solving Problems.
Explanation:
Tips: Be highly smart with it, code may mess you up at times, changing things you'd never touched!
which applications or services allow hosts to act as client and server at the same time?client/server applicationsemail applicationsP2P applicationauthentication server
Answers
The applications or services that allow hosts to act as client and server at the same time are client/server applications, email applications, P2P applications, and authentication servers.
Applications or services that allow hosts to act as both client and server at the same time are called P2P (peer-to-peer) applications. P2P applications enable direct communication between hosts without the need for a centralized server, making them distinct from client/server applications and email applications. Authentication servers, on the other hand, are specifically used to verify user identities and manage access control.A network host is a computer or other device connected to a computer network. A host may work as a server offering information resources, services, and applications to users or other hosts on the network. Hosts are assigned at least one network address.
A computer participating in networks that use the Internet protocol suite may also be called an IP host. Specifically, computers participating in the Internet are called Internet hosts. Internet hosts and other IP hosts have one or more IP addresses assigned to their network interfaces. The addresses are configured either manually by an administrator, automatically at startup by means of the Dynamic Host Configuration Protocol (DHCP), or by stateless address autoconfiguration methods.
learn more about client/server here:
https://brainly.com/question/30466978
#SPJ11
Which is an example of a crime that might occur in an e-commerce transaction?
A customer’s new purchase is stolen after delivery.
A customer’s credit card information is stolen and used by someone else.
A customer can easily take merchandise without having to pay for it.
A customer pays an unfair price for the merchandise she bought.
Answers
Answer:
A costumers credit card information is stolen and used by someone else.
Answer:
A customer's credit card information is stolen and used by someone else.
Explanation:
Since e-commerce is online sales, the customer can not take merchandise without having to pay for it.
Also the customer can search for the best price.
Sports photography is not included in news coverage.
True
False
Answers
Answer:
False yes it is
Explanation:
pls answer the question

Answers
Answer:
hi
Explanation:
why is computer called an information processing device ?
Answers
Since, the computer accepts raw data as input and converts into information by means of data processing, it is called information processing machine (IPM).
Computer is called information processing machine because it gives you meaningful information after processing raw data......
what is computer system
Answers
Answer:
A computer system is a basic, complete and functional hardware and software setup with everything needed to implement computing performance.
Explanation:
Hope this was helpful,Have an amazing, spooky Halloween!!
what is pirating means in technical terms?
Answers
Answer:
the illegal copying, distribution or use of software
Pirating refers to the unauthorized copying, distribution, or use of copyrighted material, such as software, music, movies, or books, without the permission of the copyright holder.
Here,
In technical terms pirating refers to the unauthorized copying, distribution, or use of copyrighted material.
This can include activities such as downloading or sharing copyrighted content without paying for it or using cracks to bypass licensing or copy protection mechanisms.
Pirating is considered illegal and unethical because it infringes upon the rights of the copyright holder and can result in legal consequences.
Know more about pirating,
https://brainly.com/question/29769277
#SPJ6
Play to end-
Back to beginning
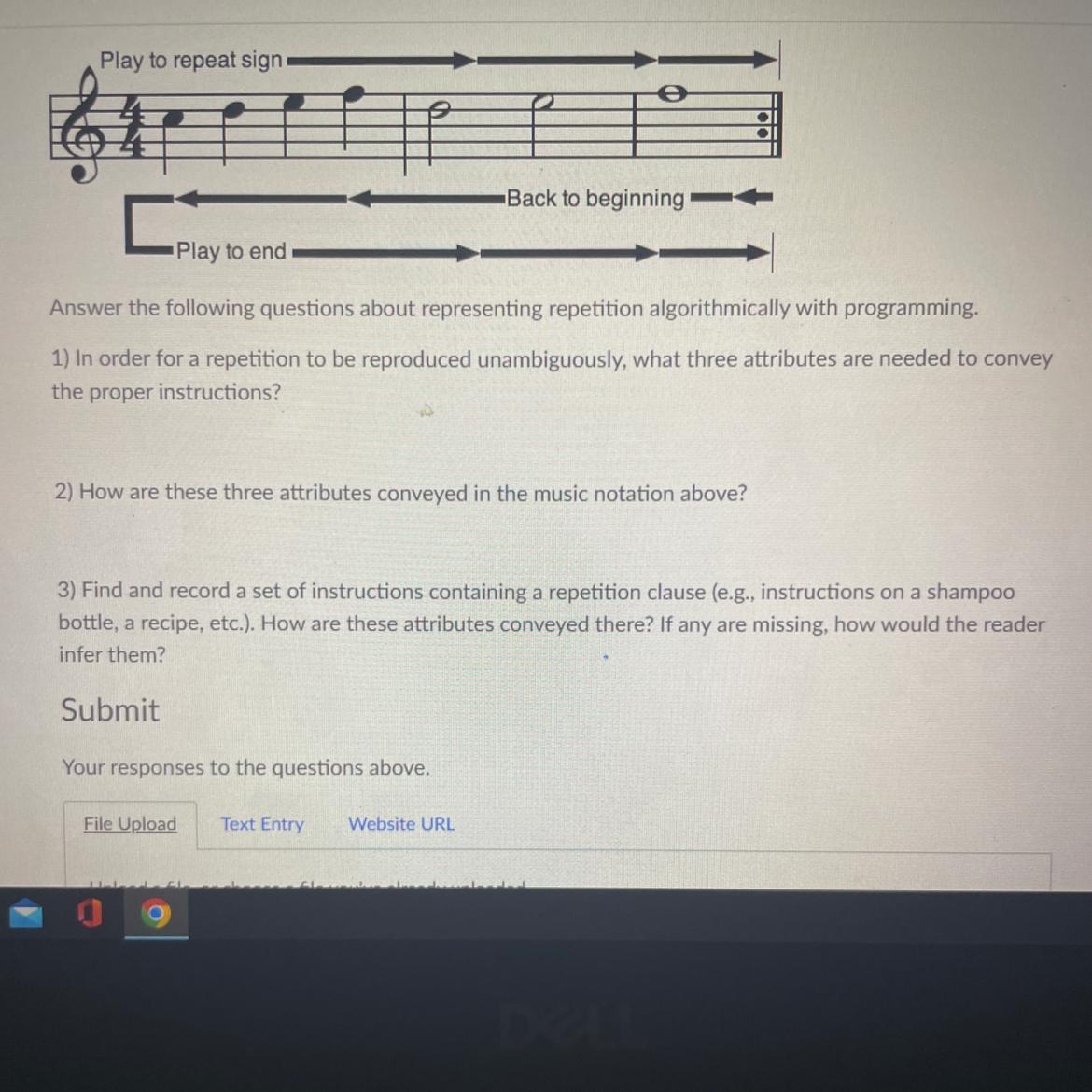
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
)
What is the name of the information about a digital photograph, such as its file name, date created and copyright information, that can be
embedded within the actual image file?
Answers
Photo metadata
Hope this helps
Select the loop that computes the average of an array of integers called iArray that has been previously declared and initialized. Store the result in a variable of type integer called iAverage that has been previously declared and initialized to zero.
Answers
To compute the average of an array of integers called `iArray`, you can use a for loop. Here's an example of how you can do it:
```java
int iSum = 0;
int iAverage;
int arrayLength = iArray.length;
for (int i = 0; i < arrayLength; i++) {
iSum += iArray[i];
}
iAverage = iSum / arrayLength;
```
In this code, we initialize a variable `iSum` to store the sum of all the elements in `iArray`. We also initialize `arrayLength` to store the length of `iArray`.
Then, using a for loop, we iterate through each element in `iArray` and add it to `iSum`. After the loop, `iSum` will contain the sum of all the elements in the array.
Finally, we calculate the average by dividing `iSum` by `arrayLength` and store the result in the `iAverage` variable.
Make sure to replace `iArray` with the name of your actual array variable and adjust the variable types accordingly.
To know more about average of an array of integers visit:
https://brainly.com/question/33343017
#SPJ11
6.3 code practice edhisive
You should see the following code in your programming environment:
Import simplegui
Def draw_handler(canvas):
# your code goes here
Frame = simplegui.creat_frame(‘Testing’ , 600, 600)
Frame.set_canvas_background(“Black”)
Frame.set_draw_handler(draw_handler)
Frame.start()
Use the code above to write a program that, when run, draws 1000 points at random locations on a frame as it runs. For an added challenge, have the 1000 points be in different, random colors.
Answers
Answer:
import simplegui
import random
def draw_handler(canvas):
for x in range(1000):
colorList = ["Yellow", "Red", "Purple", "White", "Green", "Blue", "Pink", "Orange"]
c = random.choice(colorList)
x = random.randint(1,600)
y = random.randint(1,600)
canvas.draw_point([x, y], c)
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("Black")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
I used a for loop, setting my range to 1000 which is how you create exactly 1000 points. Next, I defined my color array, my x randint value, and my y randint value. I set both the x and y randint values to 1 - 600 since the frame is 600x600. The rest is pretty self explanatory.
What should you do if you copy a sentence from a book into a document
you are writing for your employer?
A. Ask your boss to read the document.
B. Give credit to the author for the work you used in your document.
C. Check the spelling of your document.
ОА
OB
Ос
HINT
SUBMIT
PREVIOUS
5 of 18
here to search
A
The
Answers
Answer:
Your answer is going to be B
Joseph Haydn's Symphony No. 101 in D Major, composed in 1794, has what nickname, after the rhythmic two-note sequence that repeats throughout the second movement?
Answers
101 has a reason for its quirky nickname…
Listen to the bassoons and the strings in the second movement of Haydn's Symphony No. 101, nicknamed 'The Clock', and you'll hear something quite striking. That incessant rhythmic pulse sounds so much like a timepiece going round and round it was given the perfect moniker.
_____ lay(s) out a framework for the future and provide(s) a blueprint for control
Answers
Strategic planning lay(s) out a framework for the future and provide(s) a blueprint for control. This planning process helps organizations set their goals, priorities, and actions to achieve desired outcomes and sustainable success.
Strategic planning serves as a framework for the future by setting the organization's trajectory and providing a blueprint for control by defining the strategies, tactics, and measures required to steer the organization towards its desired outcomes.
By engaging in strategic planning, organizations assess their current situation, identify opportunities and challenges, and develop a roadmap for success. This roadmap, often referred to as a strategic plan, outlines the organization's vision, mission, values, goals, and objectives.
The strategic plan serves as a guiding document that outlines the steps to be taken, the resources needed, and the timelines for implementation. It provides a clear direction for decision-making and helps establish control mechanisms to monitor progress and make necessary adjustments along the way.
To learn more about blueprint: https://brainly.com/question/4406389
#SPJ11
What is the answer to this A term career is usually applied to a Someone please HEEEEEEEEEELP MEEEEEEE. THX
Answers
Answer:
Position that allows for professional growth and advancement
The term career is used in a number of ways but is usually applied to means the same thing: a position that allows for professional growth and advancement. It relates to a person’s occupation or profession and his journey of life, learning (training or formal education) and work.
Answer:
Position that allows for professional growth and advancement
Explanation:
a p e x
samuel is working on a project within the ubuntu server and would like further details on example. he uses a specific command and receives further dns information on the website. what command(s) did he use to gain the dns information?
Answers
Samuel is working on a project within the Ubuntu server and would like further details on an example. He uses a specific command and receives further DNS information on the website. The command(s) he most likely used to gain the DNS information is "dig" or "nslookup".
To gain DNS information on a website within the Ubuntu server, Samuel likely used the "dig" command. This command is used to perform DNS queries and obtain information about various DNS records associated with a domain name.
dig example.comThis command would provide Samuel with various DNS information such as the IP address associated with the domain name, the name servers used by the domain, and any additional DNS records such as MX or TXT records.It's important to note that the "dig" command may not be installed by default on all Ubuntu servers, so Samuel may need to install it before he can use it. He can do this by running the following command:
sudo apt-get install dnsutilsOnce installed, he can use the "dig" command to gain the DNS information he needs for his project.
Know more about the DNS records
https://brainly.com/question/29454775
#SPJ11
a system uses simple/pure paging and tlb each memory access requires 100ns tlb access requires 5ns tlb hit rate is 90%. work out the actual speedup because of the tlb? speedup
Answers
Each process in the operating system will have its own page table, which will contain Page Table Entry (Memory Management Technique: Paging) (PTE).
What is Translation Lookaside Buffer (TLB) in Paging?The frame number (the address in main memory to which we want to refer) and a few other essential bits (such as the valid/invalid bit, dirty bit, protection bit, etc.) will be included in this PTE. This page table entry (PTE) will indicate where the actual page is located in main memory.The issue now is where to put the page table such that overall access time (or reference time) will be less.Fast main memory content access using a CPU-generated address (i.e., a logical or virtual address) presented a challenge at first. Since registers are high-speed memory, some people at first considered utilizing them to store page tables since access times would be shorter.The concept employed here is to store the page table entries in registers, so that when a request is created from the CPU (virtual address), it will be matched to the correct page number of the page table, which will then reveal where in the main memory the corresponding page is located.Everything appears to be in order, but the issue is that the register size is small (in practice, it can only hold a maximum of 0.5k to 1k page table entries) and the process size may be large, so the required page table will also likely be large (let's say this page table contains 1M entries). As a result, the registers might not be able to hold all of the PTEs of the page table. Therefore, this strategy is not workable.The Complete Question is Page Table Entry.
To Learn more About Page Table Entry refer to:
https://brainly.com/question/15409133
#SPJ4
if bptr is assigned b (the name of an array), then array element b[3] can alternatively be referenced with the pointer expression
a) bPtr + 5 b) *b [bPtr + 5] c) b[bPtr + 5] d) *( bPtr + 5)
Answers
The correct option is c) b[bPtr + 5)
Given that bptr is assigned b (the name of an array), then array element b[3] can alternatively be referenced with the pointer expression b[bPtr + 5].Step-by-step explanation:Given that,bptr is assigned b (the name of an array).bPtr holds the base address of the array b.The expression `b[bPtr + 5]` is equivalent to *(b+8), because the value of bPtr is the address of b[0].Thus, b[bPtr + 5] is the same as b[3].
The definition of an array in C is a way to group together several items of the same type. These things or things can have data types like int, float, char, double, or user-defined data types like structures. All of the components must, however, be of the same data type in order for them to be stored together in a single array. The items are kept in order from left to right, with the 0th index on the left and the (n-1)th index on the right.
Know more about array here:
https://brainly.com/question/13261246
#SPJ11
In one to three sentences, describe how a digital ink pen could make a task more efficient.
Answers
Answer:
First, digital ink pens will never run out of ink as they do not use ink at all for writing, making it more efficient for the writer to right for longer periods of time. Second, digital ink pens can be used to take notes on any device such as cell phones, tablets, etc.
Explanation:
Turtle X has a hard, sharp beak with a short neck; and Turtle Y has no beak and has a very long neck. What is the correct typical diet for the two turtles
Answers
Based on the characteristics described, Turtle X with a hard, sharp beak and a short neck is likely adapted for a diet that includes hard-shelled prey, such as crustaceans or mollusks.
Its beak allows it to crush and consume these tough food items. On the other hand, Turtle Y with no beak but a long neck is adapted for a different feeding strategy. The long neck suggests that Turtle Y is adapted to reach vegetation or food sources in water or on land that are out of reach for other turtles. Therefore, Turtle Y's typical diet is likely to consist of plant material, such as aquatic plants, algae, or vegetation on land.
Learn more about here;
https://brainly.com/question/12534888
#SPJ11