) A 0.3m-wide panel is made of a metal sheet with toughness (KIC) 50 MPa.m1/2 and yield strength 420 MPa. Calculate the maximum permissible crack size in a single-edge-cracked panel subjected to a uniform tensile stress of 140 MPa (i.e., Single-edge notched tension specimen). (b) Does the situation satisfy the small scale yielding condition
Answers
The maximum permissible crack size in a single-edge-cracked panel is calculated in the attached image below:
Cracks with a width of less than 0.3 mm are often acceptable and have no effect on the structure. They may, however, develop and evolve to become structural fissures. As a result, minor fractures in buildings or constructions should be monitored. A crack width of more than 0.3 mm might jeopardize the structure's durability.
For the determination of the crack width in reinforced concrete flexural members, several building code equations and equations devised by researchers are employed. Five reinforced concrete rectangular models were theoretically explored to study code regulations in addition to various formulae available in the literature about the crack width estimation of reinforced concrete members exposed to flexure. Different characteristics, such as reinforcing steel ratio, steel rebar arrangement, and reinforcement grade, are included in the models.
Learn more about the crack panels here:
https://brainly.com/question/31492832
#SPJ4


Related Questions
Determine the transfer function H(s) for a high pass filter with the following characteristics:
1. a cutoff frequency of 100 kHz
2. a stopband attenuation rate of 40 dB/decade
3. a nominal passband gain of 20 dB, which drops to 14 dB at the cutoff frequency
Write the formula for H(s) that satisfies these requirements.
Answers
Answer:
H(s) = 10 / [ 1 + s / (200*10^3π ) ]^2
Explanation:
Characteristics of the high pass filter
Cutoff frequency = 100 kHz
stopband attenuation rate = 40 dB/decade
nominal passband gain = 20dB = 20logK = 20
Formula for H(s) satisfying the requirements above
given that the stopband attenuation = 40 dB/decade the formula for H(s) that will satisfy the requirements is a second order filter
H(s) = K / ( 1 + s/Wo ) ^2 ----- ( 1 )
Wo = 2πf = 2π ( 100 * 10^3 ) = 200 * 10^3 π
K = 10
back to equation ( 1 )
H(s) = 10 / [ 1 + s / (200*10^3π ) ]^2
Question 18 of 25
If you see an increase in traffic, step in and direct traffic to ensure safety. Is this a
safe or unsafe practice?
Select the best option.
O
Safe
Unsafe
Answers
We are required to explain if it is safe or unsafe to see an increase in traffic, step in and direct traffic to ensure safety.
Increase in traffic is the high influx of vehicles on the road. This means the number of vehicles using the road at a particular time is much. Traffic causes slow movement of vehicles and lack of patient of drivers could lead to accident.It is safe to direct traffic when there is an increase in traffic if you are a professional traffic worker. Meanwhile, it is very unsafe for a person who is not a professional traffic worker to direct traffic.Therefore, it is encouraged for only traffic officials to direct traffic.
Read more:https://brainly.com/question/23346590
Answer:
Unsafe
Explanation:
URGENT NEED HELP BY AN HOUR
C++ ONLY
Given a line of text as input: (1) output the number of characters excluding the three characters commonly used for end-of-sentence punctuation( period, exclamation point, and question mark), (2) then output the number of end-of-sentence punctuation characters that were found. You can just do (1) to pass the first few test cases for partial credit, then do (2) for full credit.
Ex: If the input is "Listen, Sam! Calm down. Please.", the output is:
28
3
Ex: If the input is "What time is it? Time to get a watch! O.K., bye now.", the output is:
43
5
Answers
Using the knowledge in computational language in python it is possible to write a code that output the number of characters excluding the three characters commonly used for end-of-sentence punctuation.
Writting the code:import re
def check_sentence(text):
result = re.search(r"^[A-Z][A-Za-z\s]*[\.\?!]$", text)
return result != None
print(check_sentence("Is this is a sentence?")) # True
print(check_sentence("is this is a sentence?")) # False
print(check_sentence("Hello")) # False
print(check_sentence("1-2-3-GO!")) # False
print(check_sentence("A star is born.")) # True
See more about python at brainly.com/question/19705654
#SPJ1

In Female, the twenty-third pair of chromosomes is called in in
Answers
Which of the following is the term for a sliding device that moves against or is moved by fluid pressure?
turbine
valve
piston
fluid
Answers
I hope I helped ! ((:
Answer:
piston
a sliding device that moves against or is moved by fluid pressure; usually consists of a cylindrical body within a cylindrical chamber
Explanation:
2021 EDGE I got it correct :D
Determine T and magnitude of R

Answers
Answer:
The magnitude of a vector →PQ is the distance between the initial point P and the end point Q . In symbols the magnitude of →PQ is written as | →PQ | . If the coordinates of the initial point and the end point of a vector is given, the Distance Formula can be used to find its magnitude.
Explanation:
A new plug-and-play storage device was installed on a PC in the corporate environment. Which of the following safeguards will BEST help to protect the PC from malicious files on the storage device?
a. Change the default settings on the PC
b. Define the PC firewall rules to limit access
c. Encrypt the disk on the storage device
d. Plug the storage device in to the UPS
Answers
The BEST safeguard to protect the PC from malicious files on the newly installed plug-and-play storage device is to encrypt the disk on the storage device.
Encrypting the disk on the storage device will provide an additional layer of protection to the data stored on the device, making it more difficult for any malicious files to be accessed or extracted. Changing the default settings on the PC or plugging the storage device into the UPS will not directly protect against malicious files. Defining firewall rules can be useful in limiting network access, but may not necessarily prevent malicious files from being transferred to the PC via the storage device.
To know more about encryption refer:
https://brainly.com/question/17017885
#SPJ11
vết nứt tế vi là gì?
Answers
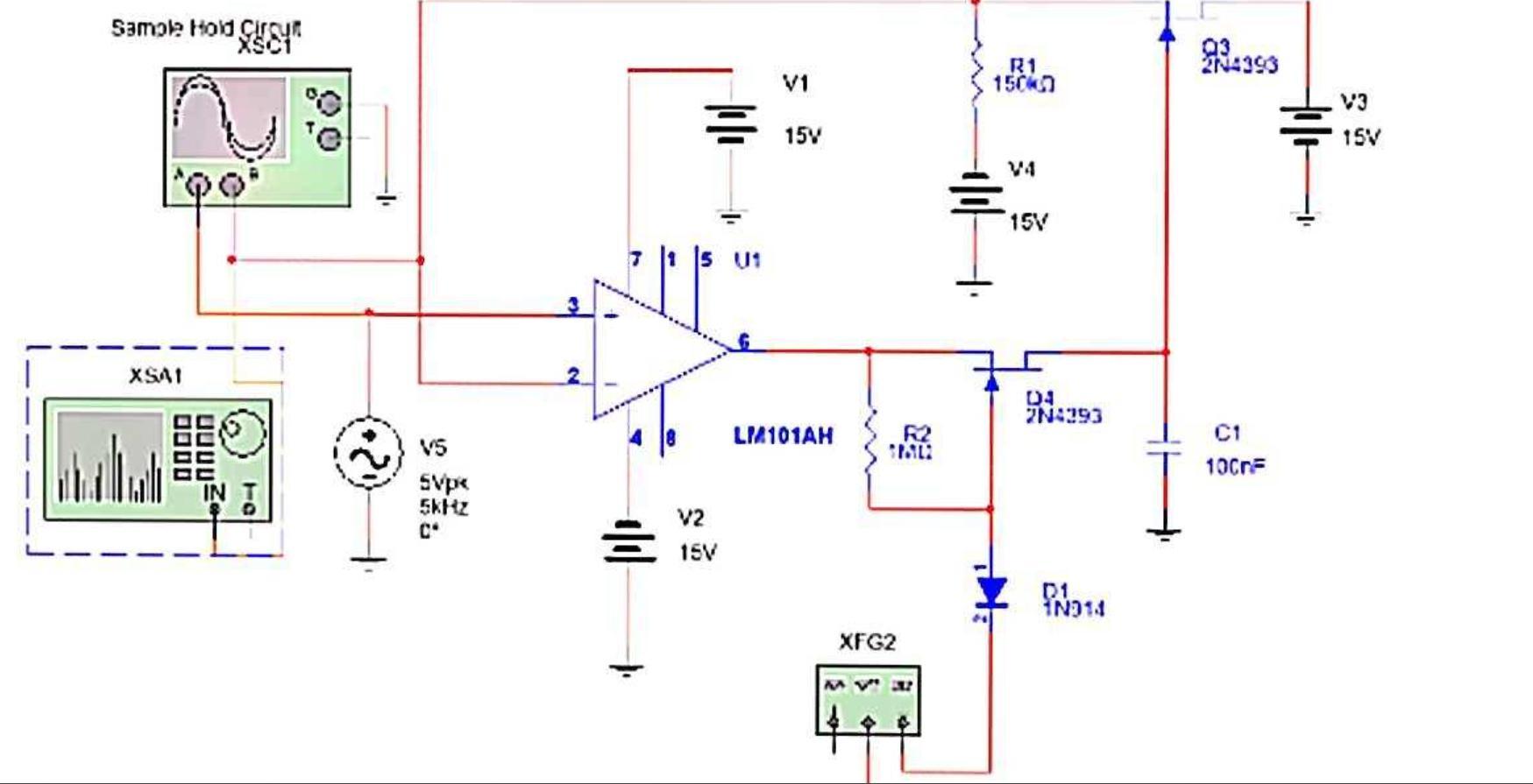
FigE8-2 contains a sampled waveform. Use the spectrum analyzer to determine the frequencies being sampled. If you wish to sample the 5 kHz waveform adequately, at what sampling frequency should you be at? Run the simulation for a number of different sampling frequencies and obtain screen shots. Where does the 3kHz signal come from in the first undersampled instance? Give a screen shot from the spectrum analyzer of the properly sampled waveform
Answers
To preserve the full information in the signal, it is necessary to sample at twice the maximum frequency of the signal.
Given,
Spectrum analyzer .
The sampling interval is an important parameter which must be chosen carefully, if measurements of the direct, global, and diffuse irradiance or illuminance are carried out to determine their averages over a given period.
The sampling theorem states that a real signal, f(t), which is band-limited to f Hz can be reconstructed without error from samples taken uniformly at a rate R > 2f samples per second.
This minimum sampling frequency, fs = 2f Hz, is called the Nyquist rate or the Nyquist frequency. If the signal contains high frequency components, we will need to sample at a higher rate to avoid losing information that is in the signal.
Generally, Nyquist's work states that an analog signal waveform can be converted into digital by sampling the analog signal at equal time intervals. The sampling frequency should be at least double the maximum frequency.
If your measurement is done in the pass-band (2.38 GHz-2.46 GHz), so the maximum frequency is 2.46 GHz which means that the sampling frequency should be at least 2x2. 46 GHz = 4.92 GHz. For most music applications, 44.1 kHz is the best sample rate to go for. 48 kHz is common when creating music or other audio for video.
The images of the screen shot are attached below.
Know more about nyquist criteria,
https://brainly.com/question/31854793
#SPJ4

What happens if the TEV bulb loses its charge?
Answers
Answer:
When a loss of charge exists, There is not a sufficient force to throttle the value open to it's correct position.
Derive input space partitioning test inputs for the GenericStack class assuming the following method signatures:
• public GenericStack ();
• public void push (Object X);
• public Object pop ();
• public boolean isEmpty ();
Assume the usual semantics for the GenericStack. Try to keep your partitioning simple and choose a small number of partitions and blocks.
(a) List all of the input variables, including the state variables.
(b) Define characteristics of the input variables. Make sure you cover all input variables.
(c) Partition the characteristics into blocks.
(d) Define values for each block
Answers
Assuming the usual semantics for the GenericStack( Input variables:
- Object X (input parameter for push method for array)
State variables:
- The stack (represented as an array, linked list, or any other data structure)
(b) Characteristics of input variables:
- Type: Object
- Value range: Any valid Object value, including null
Characteristics of state variables:
- Size of the stack: An integer value representing the number of elements in the stack
- Elements in the stack: An array, linked list, or any other data structure containing the elements in the stack
(c) Partitioning:
- Type of input: valid Object, null
- Size of the stack: 0, 1, >1
(d) Values for each block:
- Type of input: valid Object, null
- Size of the stack: 0, 1, >1
Valid Object:
- Size 0: any valid Object
- Size 1: any valid Object
- Size >1: any valid Object
Null:
- Size 0: null
- Size 1: null
- Size >1: null
Thus, this is the list of all of the input variables, including the state variables.
For more details regarding semantics, visit:
https://brainly.com/question/873851
#SPJ4
You are tasked to perform a linear regression using the least squares method on the following (x,y) data points:
(2,0)
(5,4)
(8,5)
From the list of answers, pick the point that will be part of the regression line
Hint: Find the equation of the line (slope, intercept) as you did in the regression assignment. Then for a (X1, Y1) given below, replace the value of X in the equation with the value of X1, and find out if you get the value of Y1. If you do (meaning the equivalence is true), that point is part of the regression line.
Group of answer choices
(5,3)
(5,4)
(0,0)
(2,4)
Answers
Based on the information, the point that is part of the regression line is (5, 4).
How to calculate the valueThe intercept can be found by plugging in one of the data points and solving for b. Let's use the point (2, 0):
y = mx + b
0 = (1/2) * 2 + b
0 = 1 + b
b = -1
The equation of the line is therefore y = 1/2 * x - 1.
To find which point is on the regression line, we can plug in the x-coordinate of each point into the equation and see if we get the y-coordinate. The only point that satisfies this condition is (5, 4).
Therefore, the point that is part of the regression line is (5, 4).
Learn more about regression on
https://brainly.com/question/25987747
#SPJ4
how can the wheatstone bridge be used as a sensor? provide explanation and illustrations
Answers
The Wheatstone bridge is a circuit that is commonly used in measuring changes in resistance. This circuit can also be used as a sensor to detect changes in physical quantities such as temperature, pressure, and strain.
In a Wheatstone bridge sensor, four resistors are arranged in a diamond shape as shown below:
```
+Vcc ---- R1 ---- R3 ---- Output
| |
| Sensor|
| |
Gnd ---- R2 ---- R4 ----
```
When the Wheatstone bridge sensor is in a balanced state, the voltage at the output terminal is zero. If the sensor experiences any changes in resistance, the voltage at the output terminal will no longer be zero, and the magnitude of this voltage will depend on the extent of the resistance change.
For example, if the sensor experiences an increase in temperature, its resistance will also increase. This increase in resistance will cause a voltage imbalance in the Wheatstone bridge, resulting in a non-zero output voltage. This output voltage can be measured and used to determine the change in temperature.
Similarly, a Wheatstone bridge sensor can be used to detect changes in pressure or strain. By measuring the output voltage of the Wheatstone Bridge, it is possible to determine the extent of these physical changes.
Overall, the Wheatstone bridge is a versatile circuit that can be used as a sensor to detect changes in various physical quantities. Its ability to accurately measure changes in resistance makes it a popular choice for many applications.
Learn more about Wheatstone here:
https://brainly.com/question/30354245
#SPJ11
differentiate between isohyetal method and arithmetical average method of rainfall
Answers
Answer:
Explained below
Explanation:
The isohyetal method is one used in estimating Rainfall whereby the mean precipitation across an area is gotten by drawing lines that have equal precipitation. This is done by the use of topographic and other data to yield reliable estimates.
Whereas, the arithmetic method is used to calculate true precipitation by the way of getting the arithmetic mean of all the points or arial measurements that will be considered in the analysis.
The rafter is fastened to the outside wall so that the plumb cut in the birdsmouth is tight to the exterior wall sheathing
Select one:
O True
O False
Answers
1. suppose we have a stack that can grow indefinitely. we want to create a new type of stack data structure. the contents are templated and will always contain only comparable items (e.g., integers or strings, although you may not assume anything about the contents of the stack other than that any two are comparable: this means, given two elements a and b, we can determine if a < b and can also determine if a and b are equal). this new structure will have the usual stack public operations and also a new function findmin, which will return the smallest element currently in the stack. we could implement this by searching the contents, but that takes time linear in the number of elements in the stack. explain how you would change the new stack data structure to allow for this function to run in o(1) time. if you are storing additional private member data, state what else you are storing. if you are changing existing functions push, pop, or top (or the constructor/size functions), explain briefly how you are changing them. their running times must still be o(1); for example, you cannot search the full stack for the newest minimum value at every push and pop. explain in a few sentences how each change works and how, after any valid sequence of push and pop operations, we can always find the minimum element in the stack in o(1) time. your explanation should be sufficient that if, six months from now, you had to write the necessary modifications to a stack data structure written in your favorite programming language, using only your written description, you could do so. you may assume that there will never be a duplicate item pushed to the stack.
Answers
In order to accomplish operations, the stack uses the LIFO (last in, first out) sequence or methodology. Two types of data structures, an array, and a linked list, can be used to build stacks in data structures.
Array: When a stack is used, an array is used to create it. Arrays are the working tool for every action. Pushing an item into the stack and popping an item out of the stack are the only two operations permitted in pushdown stacks. It is only possible to add and delete components from a stack from the top, making it a limited-access data structure. Adding anything to the stack's top with a push, taking something away with a pop, is known as pushing.
To know more about operations,
https://brainly.com/question/27529825
#SPJ4
Electrical Circuit question..

Answers
Answer:
Cool.
Explanation:
2. The moist weight of 0.1 ft3 of soil is 12.2 lb. If the moisture content is 12% and the specific gravity of soil solids is 2.72, determine the following: a) dry unit weight, b) void ratio, c) porosity, d) degree of saturation, and e) volume occupied by water.
Answers
The answers to dry unit weight, void ratio, porosity, degree of saturation, volume occupied by water are respectively;
γ_d = 108.93 lb/ft³; e = 0.56; n = 0.36; S = 0.58; V_w = 0.021 ft³
Calculation of Volume and Weight of soil
We are given;
Moist weight; W = 12.2 lb
Volume of moist soil; V = 0.1 ft³
moisture content; w = 12% = 0.12
Specific gravity of soil solids; G_s = 2.72
A) Formula for dry unit weight is;
γ_d = γ/(1 + w)
where γ_w is moist unit weight as;
γ_w = W/V
γ_w = 122/0.1 = 122 lb/ft³
Thus;
γ_d = 122/(1 + 0.12)
γ_d = 108.93 lb/ft³
B) Formula for void ratio is;
e = [(G_s * γ_w)/γ_d] - 1
e = [(2.72 * 122)/108.93] - 1
e = 0.56
C) Formula for porosity is;
n = e/(1 + e)
n = 0.56/(1 + 0.56)
n = 0.36
D) Formula for degree of saturation is;
S = (w * G_s)/e
S = (0.12 * 2.72)/0.56
S = 0.58
E) Volume occupied by water is gotten from;
V_w = S*V_v
where;
V_v is volume of voids = nV
V_v = 0.36*0.1
V_v = 0.036 ft³
Thus;
V_w = 0.58 * 0.036
V_w = 0.021 ft³
Read more about Specific Gravity of Soil at; https://brainly.com/question/14932758
(6) effects of urbanization on the urban hydrology
Answers
Answer:
123456
Explanation:
what is the predicate ___ for the following query and its result? ?- ____(f(a,b),f,a). a = 2 f = f
Answers
The query's 'f/3' predicate determines the outcome, which is dependent on the specific information and guidelines laid down in the Prologue knowledge base.
The outcome will be 'true' if the query matches a rule or fact in the Prologue knowledge base.
However, it is impossible to deliver the precise outcome without access to the particular Prologue knowledge base or rules.
'?- f(a,b), f(a).' calls the predicate 'f/3' with the arguments 'f(a,b)', 'f', and 'a'. Whether there is a rule or fact that meets these arguments and evaluates to "true" in the Prologue knowledge base will determine the outcome.
Thus, this is the predicate for the given query.
For more details regarding predicate, visit:
https://brainly.com/question/1761265
#SPJ4
What are the 3 types of irony and examples?.
Answers
The three types of irony are Verbal Irony, Situational Irony, and Dramatic Irony.
Example of Verbal Irony:
When a statement's intended meaning differs from what is actually said, it is said to be verbally ironic.In Shrek, Donkey asks Shrek if he can stay with him. Shrek replies, "Of course," when he really means, "No, not really."Example of Situational Irony:
Situational irony occurs when a situation's conclusion is completely unanticipated. For instance, everyone in Emerald City believes that Oz is strong and impressive in the book The Wonderful Wizard of Oz. Oz, however, turns out to be the exact opposite—an aged guy devoid of any supernatural abilities.Example of Dramatic Irony:
Dramatic irony occurs when characters are unaware of information that the audience is aware of.When the readers are aware that a deadly shark is present in the water but the carefree beachgoers are unaware that they are being pursued.What is Irony?
When something unexpected occurs, it is ironic. The thing opposite to what we anticipate usually occurs, and this is either humorous or dramatic.
To learn more about Irony:
https://brainly.com/question/24267033
#SPJ4
Consider a W12×79 tension member with end connections as shown below. Determine the member's available strength given 3/4 in. bolts at 3 in. on center. Assume adequate bolt strength. 2. Consider a W12×79 tension member with end connections as shown below. Determine the member's available strength given 3/4in. bolts at 3in. on center. Assume adequate bolt strength.
Answers
To determine the member's available strength, we need more information about the specific end connections and their design.
The provided description mentions a W12×79 tension member and end connections with 3/4 in. bolts at 3 in. on center, but without additional details, it is not possible to calculate the member's available strength accurately.
The available strength of a tension member depends on various factors, including the type and arrangement of the end connections, the load distribution, and the material properties. These factors need to be considered in the design and calculation of the member's strength.
If you provide more specific information about the end connections and their design, I can assist you in calculating the member's available strength.
Learn more about strength here
https://brainly.com/question/31719828
#SPJ11
With direct fuel injection the gasoline is injected:
Answers
Answer:
Gasoline is injected directly into the cylinder.
Explanation:
In a direct injection system, the air and gasoline are not pre-mixed. Rather, air comes in using the intake manifold, while the gasoline is injected directly into the cylinder.
Are spent lead acid batteries exempt from hazardous waste regulations if they are recycled?
Answers
Answer: Spent lead acid batteries (SLABs) are considered hazardous waste under the Resource Conservation and Recovery Act (RCRA) in the United States. However, they are exempt from the regulations that apply to other hazardous waste if they are recycled properly.
According to the Environmental Protection Agency (EPA), when spent lead acid batteries are recycled, they are considered a "universal waste" under RCRA. Universal wastes are certain types of hazardous waste that are considered less hazardous than other hazardous wastes and are subject to less stringent regulations. The regulations for universal waste are intended to encourage the collection and proper recycling or disposal of these materials.
To be considered for this exemption, the spent lead-acid batteries must be managed in accordance with the regulations for universal waste, which include proper labeling, storage, and transportation, as well as the requirement that the batteries be sent to a facility that is authorized to manage universal waste.
It is important to note that individual states may have different regulations regarding management and disposal of spent lead-acid batteries, so it is best to check with your state's environmental agency for specific information.
A 0.5 m rod of some material elongates 0.1 mm on heating from 20 to 112°C. Determine the value of the linear coefficient of thermal expansion [in (°C)-1] for this material.
Answers
Answer:linear coefficient of thermal expansion of the rod =2.17 x10^-6(°C)^-1
Explanation:
The Linear thermal expansion is calculated as
ΔL = αLΔT,
where ΔL = change in length L,
ΔT = the change in temperature,
α is the coefficient of linear expansion
Change in length ΔL= 0.1 mm =0.1/1000= 0.0001m
change in temperature,ΔT= Final - Initial temperature
= (112- 20)°C=92°C
Solving, we have that
ΔL = αLΔT
α=ΔL/LΔT
= 0.0001 / 0.5 x 92
=0.0001/46
=2.17 x10^-6 / °C
The linear coefficient of thermal expansion of the rod, α =2.17 x10^-6(°C)^-1
What must engineers keep in mind so that their solutions will be appropriate? O abstract knowledge O context O scientists perseverance
Answers
Answer: Context
Explanation: It is always very important for an engineer to keep the context of his/her expirament in mind.
Answer:
context
Explanation:
Answer the following questions about your own experience in the labor force.
a. When you or one of your friends is looking for a part-time job, how many weeks does it typically take? After you find a job, how many weeks does it typically take?
b. From your estimates, calculate (in a rate per week) your rate of job finding, f, and your rate of job separation, s. (Hint: If f is the rate of job finding, then the average spell of unemployment is 1/f.)
c. What is the natural rate of unemployment for the population you represent?
Answers
Answer:
Following are the solution to this question:
Explanation:
In point a:
This takes me six weeks for both the took ideas that I was searching for but it continued for 3 years (12 weeks) as it's an intern.
In point b:
Finding job:
\(\to f = \frac{1}{6} = 0.166\) jobs weekly
Separation of jobs:
\(\to \frac{ 1}{12}=0.083\) employment per week.
In point c:
Its natural rate of unemployment is: \(\frac{U}{L} = s+(s \times f)\).
The normal level of employment for that community I represent, once we add up from that preceding section, is as follows:
\(\to \frac{U}{L} = 0.083+ (0.083\times 0.166) = 0.096\)
If on average, it requires six weeks to find another job or the work lasted 12 weeks, the group's unemployment level is \(0.096 \ \%\).
This is a classification of back pain based on duration. A) AcuteB) RecurrentC) ChronicD) All of the above
Answers
Answer:
D) All of the above.
Complete the Pyramid for Enterprise Design – Identify and explain each level – hardware needed, software needed, Application needed, data collected, dashboards or KPIs, what kind of business decision would be made using the data for autonomous driving technology.
Answers
The Pyramid for Enterprise Design in autonomous driving involves hardware, software, data collection, and dashboards for making informed business decisions.
Pyramid for Enterprise Design:
1. Hardware Needed: Autonomous driving technology requires various hardware components such as sensors, cameras, radars, GPS systems, processors, and actuators. These components enable the collection of real-time data and facilitate the functioning of the autonomous vehicle.
2. Software Needed: The software layer consists of the operating system and the algorithms required for autonomous driving. This includes perception systems for object detection and recognition, decision-making algorithms, and control systems for navigation, acceleration, and braking.
3. Application Needed: The application layer involves the development of specialized software applications specifically designed for autonomous driving. These applications integrate the hardware and software components, enabling the vehicle to perform tasks like lane keeping, adaptive cruise control, and automated parking.
4. Data Collected: Autonomous vehicles generate vast amounts of data through their sensors and onboard systems. This data includes information about the vehicle's surroundings, such as road conditions, traffic patterns, and the behavior of other vehicles. It also includes internal vehicle data like speed, acceleration, and fuel consumption.
5. Dashboards or KPIs: Dashboards or Key Performance Indicators (KPIs) provide visual representations of the collected data. These dashboards enable users to monitor the performance of autonomous driving technology, track key metrics, and identify areas for improvement. Examples of KPIs in this context could be the number of successful autonomous trips, average reaction time, and fuel efficiency.
The data collected and analyzed from autonomous driving technology can be used to make various business decisions. For example, analyzing traffic patterns and congestion data can help businesses optimize delivery routes and reduce transportation costs. Additionally, data on driving behavior and vehicle performance can be utilized to improve safety measures, enhance maintenance protocols, and optimize fleet management. By leveraging the insights gained from the data, businesses can make informed decisions to improve the efficiency, reliability, and safety of autonomous driving technology.
To learn more about software Click Here: brainly.com/question/32393976
#SPJ11
A binary tree has L leaves and K nodes, each with two children. What is the relation of L and K ?
Option
L = K -1
L = 2K + 1
L = K - 1
There is no fixed relation between L and K
Answers
K=2*L-1 is the relationship between the number of nodes (K) and leaves (L). Therefore, L and k do not always have a stable relationship.
Number of internal nodes for L leaves = L - 1
So total nodes = 2L – 1
The following relation applies for a k-ary tree where each node has k offspring or none at all: L = (k-1)*n + 1.
where n represents the number of internal nodes and L represents the number of leaf nodes.
Every internal node will have K children since the k tree is fully developed.
A pointer to the topmost node of the tree, sometimes referred to as the "root," serves as the representation of a binary tree. The root's value is NULL if the tree is empty. The following components are present in each node of a binary tree:
Pointer to left kid in data
to the right-hand kid
Basic Binary Tree Operation:
adding a new element.
Learn more about Nodes here:
brainly.com/question/24068343
#SPJ4