30 POINTS!!
Ruslan works in an advertising agency. He has been tasked with developing a poster for a sunglasses campaign. The poster is supposed to be put up on a highway billboard.
What file format should he use to create a high-resolution picture?
A. JPEG
B. PNG
C. TIFF
D. GIF
E. PSD
Answers
Answer:
c. TIFF..............
Related Questions
pls answer fast in five mins

Answers
The answer is true!! I hope this helps!!
How to code 2.9.5: Four colored triangles {Code HS}
Answers
Answer: penup()
backward(100)
for i in range(4):
pensize(5)
pendown()
left(60)
color("green")
forward(50)
right(120)
color("blue")
forward(50)
color("red")
right(120)
forward(50)
penup()
left(180)
forward(50)
Explanation:
L
In this exercise we have to use the knowledge of computational language in python to write the code.
This code can be found in the attached image.
To make it simpler the code is described as:
ipenup()
backward(100)
for i in range(4):
pensize(5)
pendown()
left(60)
color("green")
forward(50)
right(120)
color("blue")
forward(50)
color("red")
right(120)
forward(50)
penup()
left(180)
forward(50)
See more about python at brainly.com/question/22841107

If you aren’t familiar with the idea of a leap year, read “Why Is There a Leap Day?” before continuing with the lab.
Your friend is writing a program that will allow the user to input a year and then print “LEAP!” if that year is a leap year or print “not a leap year” if it is not. However, the program isn’t working properly, and your friend asked you for help in debugging.
Before you take a look at the program, you should know these rules for leap years:
A year is a leap year if it can be divided by 400 without a remainder.
A year is a leap year if it can be divided by 4 without a remainder, unless it can also be divided by 100 without a remainder; if that is the case, it is not a leap year.
All other years are not leap years.
Here is your friend’s code:
year=int(input()
if year%400=0:
print("LEAP!")
else:
print(not a leap year")
elseif year%4==0 and year%100!=0
print(“not a leap year")
Note: You may not have seen the % symbol used this way before. It calculates the remainder of the number to the left of it when it is divided by the number to the right of it. So, 10%3 is 1, because when you divide 10 by 3, the remainder is 1.
Answers
The correct debugged code is attached below
What is a leap yearA leap year is a year with 366 days and this year occurs once every 4 years. The debugged code line of code of the program written, is as attached below. because the line of code in the question lacks some functions and symbols
Hence we can conclude that the correct debugged code is attached below.
Learn more about Python coding : https://brainly.com/question/16397886
#SPJ1

TRUE / FALSE. is a data-hiding technique that uses host files to cover the contents of a secret message.
Answers
False. The statement is incorrect. The described data-hiding technique that uses host files to cover the contents of a secret message is known as steganography, not encryption.
Steganography is a method of concealing information within other data or files in such a way that it is not easily detectable. It involves embedding the secret message or data within a carrier file, such as an image, audio file, or text document. The goal is to make the presence of the hidden message indistinguishable from the carrier file.
Encryption, on the other hand, is a technique used to secure data by transforming it into an unreadable format, known as ciphertext, using encryption algorithms and keys. Encryption focuses on protecting the confidentiality and integrity of data by preventing unauthorized access or tampering.
While both steganography and encryption are methods used to protect information, they serve different purposes. Steganography is primarily concerned with hiding the existence of information, while encryption focuses on securing the content and making it unreadable to unauthorized parties.
In the case described, the use of host files to cover the contents of a secret message aligns with the concept of steganography rather than encryption.
Learn more about encryption here:
https://brainly.com/question/28283722
#SPJ11
Copyright protection begins as soon as the work is created. group of answer choices
a. true
b. false
Answers
Copyright protection begins as soon as the work is created. group of answer choices is a true statement.
What is Copyright protection?Copyright is known to be one that do not need to be registered to be able to have its protection but, the body that it is under is one that provides owners of copyrights the ability to be able to deposit a copy of their works and they will be able to have a certificate that tend to serves as a kind of a notification of the presence of the work to all of the general public.
Therefore, Copyright protection begins as soon as the work is created. group of answer choices is a true statement.
Learn more about Copyright protection from
https://brainly.com/question/20225852
#SPJ1
What is the name of tool

Answers
Answer:
bro the pic is hazy
Explanation:
but it is looking like octagon
hope it helps you
please mark me as brainlist
______ is data that has been shaped into a form that is meaningful to human beings.
Answers
When we talk about information, we mean data that has been transformed into a format that is understandable to people.
What is an information system, exactly?We define information as data that has been transformed into a format that is understandable and practical for people. As opposed to information, which is a collection of organised and sorted facts that may be used and understood, data is a stream of unorganised facts that represents events that take place in organisations or the physical environment. Information is what is created when unprocessed data is transformed into something meaningful. In order to gather usable data, particularly within an organisation, an information system combines hardware, software, and communication networks. Many organisations rely on information technology to carry out and manage their operations, communicate with customers, and outperform their rivals.To learn more about information system, refer to:
https://brainly.com/question/24944623
Check ALL of the correct answers.
What would the following for loop print?
for i in range(2, 4):
print(i)
2
2
3
4.
1
Help now please
Answers
Answer:
2,3,4
Explanation:
Starts at two, goes to four. Thus it prints 2,3,4
Choose one skill needed to become Computer Network Administrator?
The ability to Drive.
The ability to Plan.
The ability to Code Software.
Answers
Answer:
I think 1 is ans of this question
How many bits are in an IPv6 address?
16
32
64
128
256
Answers
An IPv6 address contains 128 bits.
An IPv6 address is a 128-bit address that is used to identify devices on a network.
This is a significant increase in the number of bits compared to IPv4 addresses, which are only 32 bits.
The larger address space in IPv6 allows for more unique addresses to be assigned, which is important as the number of devices connected to the internet continues to grow.
In fact, the total number of unique IPv6 addresses is 2 to the power of 128, or 340,282,366,920,938,463,463,374,607,431,768,211,456.
This means that there are more than enough addresses to support the current and future needs of the internet.
Therefore, an IPv6 address contains 128 bits.
For more such questions on IPv6 address:
https://brainly.com/question/31103106
#SPJ11
do you think you have the qualities of an enterpreneur in you? If yes, give examples when you have shown these qualities.
Answers
The quality that all successful entrepreneurs must possess is determination and the ability to take action. They have to think and make decisions quickly and they discipline themselves to act and implement their decisions.
What is entrepreneurs?An entrepreneur is defined as a person who has the ability and desire to establish, manage and succeed in a start-up company with his own risks, in order to generate profit.
It is classified into the following types:
Small Business- Scaling of Initial Business Large Corporate Business Social Business5 Qualities of a Better Entrepreneur
Willingness to fail. Fear of failure is a common affliction.Critical Thinking. As the first trait, critical thinking enables entrepreneurs to move away from the herd mentality Clarity of Vision. Use yourself. Strong communication.Entrepreneurship accelerates economic growthEntrepreneurs are important for a market economy because they can act as the wheels of a country's economic growth. By creating new products and services, they increase new jobs, which ultimately leads to an acceleration of economic development.
To learn more about entrepreneurs, refer;
https://brainly.com/question/13897585
#SPJ9
which tool is used to terminate cables into a 66-block
Answers
Answer: Circuit pairs are connected to the block with a punch-down tool by terminating the tip wire on the leftmost slot of one row and ring wire on the leftmost slot of the row beneath the mating tip wire.
Does the USA share the F-22 raptor technology with anyone else?True or False?
-Get it right and you get that brainliest!
-Go check out my other questions, there waaaaaaaaaaaay below
Answers
Answer:
False
Okay now I have to go to my school--
Answer:
FALSE
Explanation:
False because They were going to but it got canceled because our USA military couldn't share it with anyone
Which term was used to define the era of the Internet, when the web became a "platform" for user-generated input, as opposed to static web pages?
A. web 1.0
B. usernet
C. AOL
D. web 2.0
Answers
Hello, The answer to your question is:-
Option "Web 2.0"
Reference and proof:-
Web 2.0 refers to websites that emphasize user-generated content, ease of use, participatory culture and interoperability (i.e., compatible with other products, systems, and devices) for end users.
Hope it helps you...
Answered by Benjemin ☺️
✅
which information purpose uses video from a security camera?
Answers
Answer:
robbery
Explanation:
it records a robbery so that police can later find out who did it
Some one help pls will mark brainless !!!!!
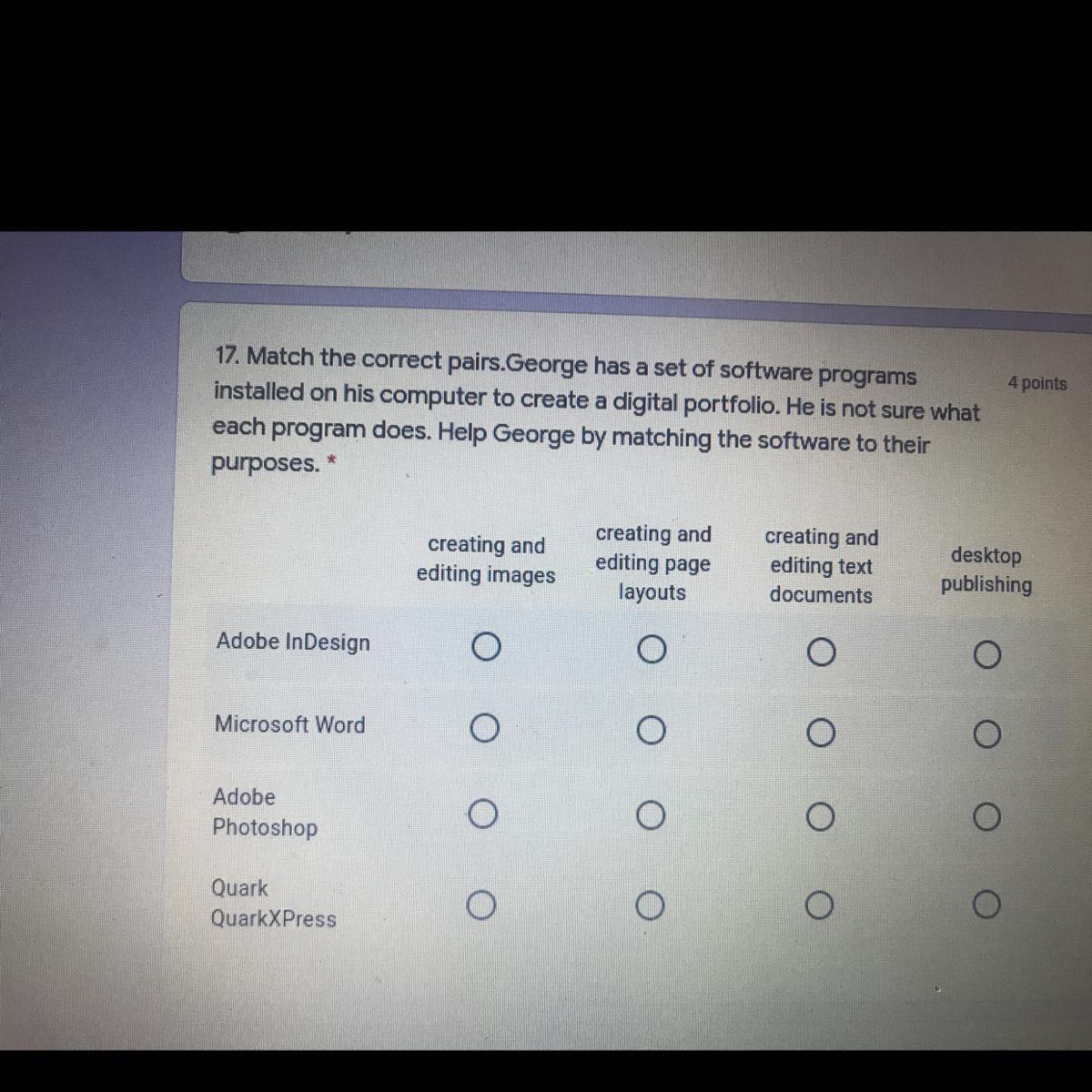
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
system software cannot handle technical details without user intervention.
Answers
System software refers to a collection of programs that work together to manage and control the operation of a computer system. They manage the hardware, middleware, and other software components that make up the overall computing environment of a system.
System software, unlike application software, interacts with the computer system's internal components and is critical to ensuring that all programs function effectively. System software is a type of software that cannot handle technical details without user intervention.
System software includes device drivers, operating systems, and utility software. System software often operates in the background and does not require the user's attention, but it does require user input to carry out certain operations. For example, when installing new device drivers, the user must choose the correct driver for the device and confirm that the installation is complete.
Overall, while system software cannot handle technical details without user intervention, it plays a crucial role in ensuring that the computer system runs smoothly and that application software can interact effectively with the hardware.
Know more about the System software
https://brainly.com/question/24321656
#SPJ11
in this code how many times will it repeat? for(i = 0; i < 8; i++) {forward();}
Answers
Answer:
It will repeat 8 times. because in the statement above the variable i has to be more then 8, so until the variable i has the value of it it will repeat. So it will repeat 8 times .
What is the default file system used by Windows 7?A. FAT32B. CDFSC. NTFSD. FAT
Answers
The default file system used by Windows 7 is NTFS (New Technology File System).
Option C. NTFS is correct.
The default file system used by Windows 7 is NTFS (New Technology File System).
NTFS was introduced by Microsoft in 1993 as an improvement over the older FAT (File Allocation Table) file system. NTFS is a more advanced and robust file system that supports larger files and provides better security and data reliability.
NTFS offers several advantages over FAT, such as support for larger file sizes, improved performance, better security, and more efficient use of disk space.
With NTFS, you can store files larger than 4GB, which is the maximum file size supported by FAT32. This is especially useful for users who work with large media files, such as videos, images, and audio files.
Another advantage of NTFS is its support for advanced security features such as file and folder permissions, encryption, and auditing.
This allows users to set permissions on individual files and folders, control who can access them, and track changes made to them.
NTFS also supports journaling, which means that file system changes are logged to a journal file before they are written to disk.
This helps prevent data loss in case of a power failure or system crash.
In summary, NTFS is the default file system used by Windows 7, and it offers several advantages over the older FAT file system.
NTFS provides better performance, larger file size support, enhanced security, and more efficient use of disk space, making it the preferred choice for modern Windows operating systems.
For similar question on Windows 7.
https://brainly.com/question/30438692
#SPJ11
This tool lets you insert text anywhere in your document. O Cut О сору O Drag O Paste
Answers
Answer:
Drag or paste (im not 100% sure tho)
Explanation:
What is the output of the following snippet?
my_list =
[[0, 1, 2, 3] for i in range (2) ]
print (my_list [2] [0])
Answers
Answer:
Explanation is being shown in the file that takes you to the link
How would you describe the relationship between blocks of code and commands?
Answers
Part B
There are many different ways that a user could tell us that he or she would like to add two numbers in our calculator program. The user could type “add”, “Add”, “ADD”, or “+”, to name a few possibilities. Of course, as humans, we know exactly what is meant, even if the word is capitalized. But the Python Interpreter can’t tell that “add” is the same as “Add”.
We can use a list to make our program a bit more robust. We can also use the IN operator to check for certain values in that list. Take a look at this if statement’s opening line:
if operation in [“add”, “Add”, “ADD”, “+”]:
Make those changes in your program and verify that it works.
Consider all of the possible words the user might enter to subtract, multiply, or divide.
Rewrite the first lines of each of your if statements to use lists.
Thoroughly test your new program, trying out each of the four operations.
Share the link to your Python code in REPL.it with your teacher by clicking on the share button and copying the link.
Answers
Answer:
The Python programming language is a great tool to use when working with numbers and evaluating mathematical expressions. This quality can be utilized to make useful programs.
This tutorial presents a learning exercise to help you make a simple command-line calculator program in Python 3. While we’ll go through one possibile way to make this program, there are many opportunities to improve the code and create a more robust calculator.
We’ll be using math operators, variables, conditional statements, functions, and handle user input to make our calculator.
Prerequisites
For this tutorial, you should have Python 3 installed on your local computer and have a programming environment set up on the machine. If you need to either install Python or set up the environment, you can do so by following the appropriate guide for your operating system.
Step 1 — Prompt users for input
Calculators work best when a human provides equations for the computer to solve. We’ll start writing our program at the point where the human enters the numbers that they would like the computer to work with.
To do this, we’ll use Python’s built-in input() function that accepts user-generated input from the keyboard. Inside of the parentheses of the input() function we can pass a string to prompt the user. We’ll assign the user’s input to a variable.
For this program, we would like the user to input two numbers, so let’s have the program prompt for two numbers. When asking for input, we should include a space at the end of our string so that there is a space between the user’s input and the prompting string.
number_1 = input('Enter your first number: ')
number_2 = input('Enter your second number: ')
After writing our two lines, we should save the program before we run it. We can call this program calculator.py and in a terminal window, we can run the program in our programming environment by using the command python calculator.py. You should be able to type into the terminal window in response to each prompt.
Output
Enter your first number: 5
Enter your second number: 7
If you run this program a few times and vary your input, you’ll notice that you can enter whatever you want when prompted, including words, symbols, whitespace, or just the enter key. This is because input() takes data in as strings and doesn’t know that we are looking for a number.
Explanation:
Hope This helps with your coding
( If it doesn't then sorry)
_____ is a very short-range wireless connectivity technology designed for cell phones and credit cards.
Answers
The term that fills the blank space is NFC. NFC stands for Near Field Communication, which is a type of wireless connectivity technology designed for cell phones and credit cards that allows them to communicate with each other over short distances without requiring an internet connection or a Wi-Fi connection.
NFC technology has been around for a while, but it has only recently become more popular due to its inclusion in a number of modern smartphones. The reason for this is because NFC technology is a quick and easy way to share information between devices, such as contact information, photos, and videos. This makes it a very useful feature for people who are constantly on the go and need to stay connected with others.
To know more about technology visit:
https://brainly.com/question/9171028
#SPJ11
Compared with other PC operating systems, the Linux-based operating systems:
are free or very inexpensive.
are much less secure.
do not run on a wide variety of hardware.
have a much higher ease of use.
Answers
The PC operating systems are operating systems that run on personal computers
The Linux-based operating system are (a) free or very inexpensive
Several operating systems run on PC; the most popular are Windows, Linux and, macOS.
The Windows operating system costs between $100 and $250, for a genuine copyThe macOs costs between $69 and $115, for a genuine copyHowever, the Linux operating system is free, and it is also open source.
Hence, in comparison to the other PC operating systems, the Linux based operating system is free or very inexpensive
Read more about operating systems at:
https://brainly.com/question/2126669
Answer:
a
Explanation:
a
Write a program using integers user_num and x as input, and output user_num divided by x three times.
Answers
Code:
user_num = int(input("user_num: "))
x = int(input("x: "))
print(user_num / x ** 3)
Explenation:
First, we make the user give us the values of user_num and x using the input() function. However, to later perform math with them, we first have to convert them into "int" using the int() function. Then we assign a variable to the values. At last we print user_num / x ** 3, since it's the same as dividing user_num by x three times.
He can borrow a CD RW from school but he has a 128 Mb memory stick of his own.
(a) Give two advantages of using the CD RW.
1
2
(b) Give two advantages of using the memory stick.
1
Answers
Answer:
Larger storage capacity: CD RWs generally have larger storage capacity compared to memory sticks. Depending on the type of CD RW used, it can store up to several GBs of data.
Durability: CD RWs are relatively more durable compared to memory sticks, which are prone to damage and data loss due to physical wear and tear.
(b) Two advantages of using the memory stick could be:
Portability: Memory sticks are small and compact, making them easy to carry around. They can fit in a pocket or on a keychain, which makes them a convenient option for transferring data between different devices.
Speed: Memory sticks can transfer data at high speeds compared to CD RWs, which can be important if you need to transfer large amounts of data quickly. This can be particularly useful if you need to transfer data frequently, such as in a work or academic setting.
Which option is the easiest way to configure macros in Access 2016?
O Edit VBA code.
Create VBA code.
O Use the Macro Builder.
O Use the Database Analyzer.
Answers
The easiest way to configure macros in Access 2016 is to use the Macro Builder. The Macro Builder is a graphical interface that allows you to create macros without having to write any code.
Here's how you can use the Macro Builder:
1. Open your Access database and go to the "Create" tab in the ribbon.
2. In the "Macros" section, click on "Macro" to open the Macro Builder.
3. In the Macro Builder window, you will see a list of actions on the left side. These actions represent different tasks that you can perform using macros.
4. To create a macro, you can simply drag and drop actions from the left side into the main area of the Macro Builder.
5. Once you have added an action, you can specify any required parameters by clicking on the action and filling in the necessary information.
6. You can add multiple actions to your macro by repeating steps 4 and 5.
7. To run the macro, you can save it and then assign it to a button or event in your Access database.
Using the Macro Builder is a great option if you're new to programming or if you prefer a visual approach to creating macros. It allows you to easily build and customize macros by selecting actions from a list and setting parameters. This way, you can automate repetitive tasks in your Access database without needing to write any code.
To learn more about macros
https://brainly.com/question/30057195
#SPJ8
can someone help me with this trace table - its computer science

Answers
TThe while loop keeps going until count is greater than or equal to 10.
count = 0, sum = 0
count = 2, sum =2
count = 4, sum = 6
count = 6, sum = 12
count = 8, sum = 20
count = 10, sum = 30
Now that count is equal to 10, it exits the while loop and the program ends. The values above complete your trace table.
If you spend time on social media, you probably see many infographics. How can you determine whether the information contained in them is trustworthy? When you create infographics, what can you do to make it more likely that the viewer will trust you?
Answers
Answer:
Provide sources.
Explanation:
Providing sources for your infographic would be the best I can think of.
Either a direct quote, a source for a graph, etc.