1. If I install a freeware program that analyzes my computer and then finds 40,000 exploits and asks me to purchase the full version, what type of att
Answers
The type of attack in this scenario is likely a scareware or rogue security software scam.
Scareware or rogue security software scams involve tricking users into believing their computer is infected with malware or vulnerabilities. The freeware program in question appears to be a part of this scam. It falsely claims to have detected 40,000 exploits on your computer, creating a sense of urgency and fear. The intention is to persuade you to purchase the full version of the software, which is usually unnecessary or non-existent. These scams rely on social engineering tactics to exploit users' fears and coerce them into paying for a fraudulent solution. It is important to be cautious of such scams and rely on reputable security software from trusted sources.
To learn more about software click here
brainly.com/question/32237513
#SPJ11
Related Questions
isten
Dria is sending files to be printed on a printing press from a program like Adobe InDesign. Which files should Dria
include to ensure proper printing of all items?
Select all that apply.
- native InDesign file
- IDML file
- low resolution, watermarked -images
- placeholder text
- Linked images
Answers
Printing of the highest caliber is crucial for branding, marketing, and other company endeavors. In actuality, they are crucial to a company's success. A company's branding is their opportunity to make the best first impression; high-quality printing will not be disregarded. Thus option A, D,E is correct.
What ensure proper printing of all items?The most common unit of measurement for print quality is DPI, which is quite similar to how pixels are defined in terms of digital images and even screen resolution.
Therefore, DPI is the same as a printer's capacity to duplicate the quantity of pixels or the resolution of the original picture.
Learn more about printing here:
https://brainly.com/question/29851169
#SPJ1
What are the three different common divisions of cloud computing?
Answers
Answer:
1-private clouds
2-public clouds
3-hybrid clouds
Jane has been asked to investigate a method that would ensure email traffic gets priority on the corporate network. She would need to implement?TCPVOIPQOSCANS
Answers
To ensure email traffic gets priority on the corporate network, Jane can implement Quality of Service (QoS) policies.
QoS is a technique that allows network administrators to prioritize certain types of traffic over others, such as email traffic over web traffic. With QoS policies, Jane can assign specific bandwidth limits, packet prioritization, and traffic shaping rules to email traffic to ensure that it gets the priority it needs. By doing so, Jane can improve the performance of email services and reduce the chances of email delays or disruptions caused by network congestion. Additionally, QoS policies can help Jane ensure that other business-critical applications receive the necessary network resources they require.To know more about E-mail visit:
https://brainly.com/question/30363901
#SPJ1
which one of the following is not hardware
Answers
Answer:
There r no options
Explanation:
I think the application r not the hardware.
What will print to the console after running this code segment?
A. 15.
B. 16.
C. 18.
D. 21.
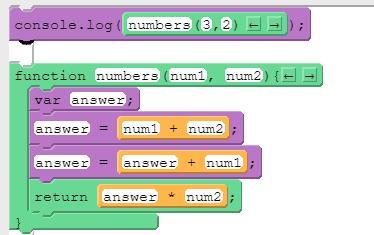
Answers
Answer:
16
Explanation:
answer =3+2
answer =5+3
return 8 × 2
16 will print to the console after running this code segment. Therefore, option B is correct.
What do you mean by code segment ?A code segment, also known as a text segment or simply text, is a section of an object file or the program's virtual address space that contains executable instructions.
A character array segment that represents a text fragment. Even though the array is directly accessible, it should be treated as immutable. This allows for quick access to text fragments without the overhead of copying around characters.
In memory, the code segment functions normally as read-only memory and has a fixed size; thus, without the need for loading, it can generally be found in read-only memory (ROM) on embedded systems.
answer = 3+2, answer = 5+3
return 8 × 2
= 16
Thus, option B is correct.
To learn more about the code segment, follow the link;
https://brainly.com/question/20063766
#SPJ2
Please help I have errors codes and don’t know that they are.
Please help thank You.

Answers
IN NEED OF HELP WITH ELECTRICITY & CIRCUITS PLEASE!!
6. Describe the energy transformations that occur in a circuit that includes a battery, wire, and an
incandescent light bulb.
7. How can you determine if a circuit is a series circuit or a parallel circuit?
8. What changes might you make to a circuit in order to slow the flow of electrical energy?
which contains all the circuit
9. Many electronic devices use a(n)
parts in a miniature form.
10.
design electrical circuits for larger power grids and for all kinds of devices
such as phones, televisions, robots, electric cars, and computers.

Answers
Answer:
wanna work on this togetherrrrrrre I need this question tooo
Exercise: Use appropriate formulas to count the requested items in each of the 3 columns. For example, the formula in cell B15 should count the numbers in the range B6:B13.
Answers
In the given problem, you are given three columns, and you need to count the requested items in each of the columns. You are also given an example of the formula used in cell B15. You can apply the same formula to count the items in all the three columns.
By using the COUNT function with the respective range for each column, you will obtain the count of non-empty cells in each column.
The formulas will ignore blank cells and text values, focusing on cells that contain numbers or logical values.
To summarize, you can apply the following formulas to count the requested items in each column:
Formula in cell B15: =COUNT(B6:B13)
Formula in cell C15: =COUNT(C6:C13)
Formula in cell D15: =COUNT(D6:D13)
By dragging or copying these formulas to the respective cells, you will obtain the count of items in each column based on the specified range.
To know more about COUNT function visit:
https://brainly.com/question/28180711
#SPJ11
Harry makes pizzas to sell in his café. He buys packets of grated cheese and boxes of mushrooms and then uses them for the pizza toppings. For example, a bag of grated cheese is divided into 4 portions and used to top 4 pizzas. What formula is in cell D3?

Answers
Answer:
=B3 / 4
Explanation:
The price of a packet of grated cheese is $2.60. To make pizza, this packet of cheese is divided into four to make 1 pizza. Therefore, the price of the grated cheese used to make 1 pizza = price of packet of cheese / 4 = $2.60 / 4 = $0.65
This price is the price inserted in cell D3. The price for each packet of grated cheese is inserted in cell B3.
Therefore the formula used in cell D3 to find the price of each grated cheese required for one pizza is:
Formula for D3 is "=B3 / 4"
with respect to computer networks, ________ are also referred to as wi-fi networks.
Answers
Answer: Wireless LANs
Explanation:
Positives and negatives side effects of government the stimulus check
Help pls☹️
Answers
Answer:
Stımulus check ıs the check offered to cıtızens of America inorder to help them to meet thier needs at that particular point in time. This is done, if there is an unforseen circumstances that made them not to earn an income.
Some of the postitves of stimulus check include:
1. Ability of the citizens to pay for their rent and other bills.
2. Ability to do some shopping and feeding
3. It create the sense of recognition among the citizens that the government always remember them in their moment of their needs.
4. To let the working class people know that their tax payment is used judiciously in helping other citizens.
The negative side effects of stimulus check include:
1. It makes people lazy since it is free money.
2. More money would be spent in the course of trying to meet the needs of everyone.
3. People would manipulate the system thereby getting more than one stimulus pay check.
4. Working class people would be angry with the system. This is because, they wil feel that all their hard work and taxes isbeing used to feed some lazy citizens who has never contributed anything to the country.
5. It would increase the debt profile of the government.
Explanation:
what are the tyoe of typical application of mainframe computer
Answers
Explanation:
customer order processingfinancial transactions production and inventory control payrollhope it is helpful to you
which type of attack does the attacker infect a website that is often visited by the target users? smishing vishing phishing watering hole
Answers
50 POINTS In a screen 480 units wide, what pattern of movement would you see if you scripted an enemy’s movement with the following blocks in Scratch:
Forever
Move, pick random x: 0 to 240, y: 0
Wait 3 secs
(loop arrow)
Answers
The pattern of movement that you would see if you scripted an enemy’s movement with the following blocks in Scratch is Move, pick random x: 0 to 240, y: 0.
What are the motion blocks in Scratch?Motion blocks is known to be a kind of movement that is part of the categories of Scratch blocks. They are known to be used to control a sprite's movement.
Note that The pattern of movement that you would see if you scripted an enemy’s movement with the following blocks in Scratch is Move, pick random x: 0 to 240, y: 0 as it shows a pattern.
Learn more about movement from
https://brainly.com/question/12234
#SPJ1
of the following occupations, which is predicted to have the greatest job growth?
Answers
Answer:
"Web designer" is the appropriate answer.
Explanation:
If we follow the market pattern, the number of purchases made by online shopping will continue to rise from 2002 to 2018 as well as the times to obtain no indication of slowing or stopping. Because of the same, web designers are expected to have the greatest increase in jobs, as it is very important to customize the website so that online customers can appear more interactive.So that the above is the correct answer.
Computational artifacts can include various forms of bias that result in the _____
of certain groups of people.
Answers
Answer:
Exclusion
Explanation:
Right on Egenuity
Answer:Below
Explanation:

Dominick is responsible for security at a medium-sized insurance company. He is very concerned about detecting intrusions. The IDS he has purchased states that he must have an IDS on each network segment. What type of IDS is this
Answers
The type of IDS that Dominick has purchased is a network-based IDS (NIDS).
A NIDS is an intrusion detection system that monitors network traffic for suspicious activity and identifies potential security threats. It does this by analyzing the contents of network packets and comparing them against known attack signatures or behavior patterns. A NIDS can be deployed at strategic locations within a network to monitor traffic on multiple network segments and provide a centralized view of network activity.
In Dominick's case, the IDS vendor has specified that he needs to deploy an IDS on each network segment, which indicates that the IDS is a NIDS. This would allow him to monitor all network traffic on each segment and detect any suspicious activity or potential security threats.
Other types of IDS include host-based IDS (HIDS), which is installed on individual computers or servers and monitors system activity, and application-based IDS (AIDS), which monitors specific applications or services for security violations.
To learn more about Dominick's click here:
brainly.com/question/28392936
#SPJ11
Find solutions for your homework
engineering
computer science
computer science questions and answers
this is python and please follow the code i gave to you. please do not change any code just fill the code up. start at ### start your code ### and end by ### end your code ### introduction: get codes from the tree obtain the huffman codes for each character in the leaf nodes of the merged tree. the returned codes are stored in a dict object codes, whose key
Question: This Is Python And Please Follow The Code I Gave To You. Please Do Not Change Any Code Just Fill The Code Up. Start At ### START YOUR CODE ### And End By ### END YOUR CODE ### Introduction: Get Codes From The Tree Obtain The Huffman Codes For Each Character In The Leaf Nodes Of The Merged Tree. The Returned Codes Are Stored In A Dict Object Codes, Whose Key
This is python and please follow the code I gave to you. Please do not change any code just fill the code up. Start at ### START YOUR CODE ### and end by ### END YOUR CODE ###
Introduction: Get codes from the tree
Obtain the Huffman codes for each character in the leaf nodes of the merged tree. The returned codes are stored in a dict object codes, whose key (str) and value (str) are the character and code, respectively.
make_codes_helper() is a recursive function that takes a tree node, codes, and current_code as inputs. current_code is a str object that records the code for the current node (which can be an internal node). The function needs be called on the left child and right child nodes recursively. For the left child call, current_code needs increment by appending a "0", because this is what the left branch means; and append an "1" for the right child call.
CODE:
import heapq
from collections import Counter
def make_codes(tree):
codes = {}
### START YOUR CODE ###
root = None # Get the root node
current_code = None # Initialize the current code
make_codes_helper(None, None, None) # initial call on the root node
### END YOUR CODE ###
return codes
def make_codes_helper(node, codes, current_code):
if(node == None):
### START YOUR CODE ###
pass # What should you return if the node is empty?
### END YOUR CODE ###
if(node.char != None):
### START YOUR CODE ###
pass # For leaf node, copy the current code to the correct position in codes
### END YOUR CODE ###
### START YOUR CODE ###
pass # Make a recursive call to the left child node, with the updated current code
pass # Make a recursive call to the right child node, with the updated current code
### END YOUR CODE ###
def print_codes(codes):
codes_sorted = sorted([(k, v) for k, v in codes.items()], key = lambda x: len(x[1]))
for k, v in codes_sorted:
print(f'"{k}" -> {v}')
Test code:
# Do not change the test code here
sample_text = 'No, it is a word. What matters is the connection the word implies.'
freq = create_frequency_dict(sample_text)
tree = create_tree(freq)
merge_nodes(tree)
codes = make_codes(tree)
print('Example 1:')
print_codes(codes)
print()
freq2 = {'a': 45, 'b': 13, 'c': 12, 'd': 16, 'e': 9, 'f': 5}
tree2 = create_tree(freq2)
merge_nodes(tree2)
code2 = make_codes(tree2)
print('Example 2:')
print_codes(code2)
Expected output
Example 1:
"i" -> 001
"t" -> 010
" " -> 111
"h" -> 0000
"n" -> 0001
"s" -> 0111
"e" -> 1011
"o" -> 1100
"l" -> 01100
"m" -> 01101
"w" -> 10000
"c" -> 10001
"d" -> 10010
"." -> 10100
"r" -> 11010
"a" -> 11011
"N" -> 100110
"," -> 100111
"W" -> 101010
"p" -> 101011
Example 2:
"a" -> 0
"c" -> 100
"b" -> 101
"d" -> 111
"f" -> 1100
"e" -> 1101
Answers
Get codes from the treeObtain the Huffman codes for each character in the leaf nodes of the merged tree.
The returned codes are stored in a dict object codes, whose key (str) and value (str) are the character and code, respectively. make_codes_helper() is a recursive function that takes a tree node, codes, and current_code as inputs. current_code is a str object that records the code for the current node (which can be an internal node). The function needs be called on the left child and right child nodes recursively. For the left child call, current_code needs increment by appending a "0", because this is what the left branch means; and append an "1" for the right child call.CODE:import heapq
from collections import Counter
def make_codes(tree):
codes = {}
### START YOUR CODE ###
root = tree[0] # Get the root node
current_code = '' # Initialize the current code
make_codes_helper(root, codes, current_code) # initial call on the root node
### END YOUR CODE ###
return codes
def make_codes_helper(node, codes, current_code):
if(node == None):
### START YOUR CODE ###
return None # What should you return if the node is empty?
### END YOUR CODE ###
if(node.char != None):
### START YOUR CODE ###
codes[node.char] = current_code # For leaf node, copy the current code to the correct position in codes
### END YOUR CODE ###
### START YOUR CODE ###
make_codes_helper(node.left, codes, current_code+'0') # Make a recursive call to the left child node, with the updated current code
make_codes_helper(node.right, codes, current_code+'1') # Make a recursive call to the right child node, with the updated current code
### END YOUR CODE ###
def print_codes(codes):
codes_sorted = sorted([(k, v) for k, v in codes.items()], key = lambda x: len(x[1]))
for k, v in codes_sorted:
print(f'"{k}" -> {v}')
Test code:
# Do not change the test code here
sample_text = 'No, it is a word. What matters is the connection the word implies.'
freq = create_frequency_dict(sample_text)
tree = create_tree(freq)
merge_nodes(tree)
codes = make_codes(tree)
print('Example 1:')
print_codes(codes)
print()
freq2 = {'a': 45, 'b': 13, 'c': 12, 'd': 16, 'e': 9, 'f': 5}
tree2 = create_tree(freq2)
merge_nodes(tree2)
code2 = make_codes(tree2)
print('Example 2:')
print_codes(code2)
To know more about Huffman codes visit:
https://brainly.com/question/31323524
#SPJ11
Write a short Ċ program compiled with GCC on your Raspberry Pi that: a. Accepts two integers (A and B) from the user. b. Displays the value of A && B, A || B, and !(A || B) on the screen. c. Verify that these outputs match the values in steps 5, 7, and 9.
Answers
The following C program accepts two integers from the user and displays the logical AND (A && B), logical OR (A || B), and logical NOT (!(A || B)) values on the screen. This allows verifying whether the outputs match the expected results.
Here's an example of a short C program that performs the required operations:
#include <stdio.h>
int main() {
int A, B;
printf("Enter the value of A: ");
scanf("%d", &A)
printf("Enter the value of B: ");
scanf("%d", &B);
int andResult = A && B;
int orResult = A || B;
int notResult = !(A || B);
printf("A && B: %d\n", andResult);
printf("A || B: %d\n", orResult);
printf("!(A || B): %d\n", notResult);
return 0;
}
This program uses the scanf function to accept the values of A and B from the user. Then, it calculates the logical AND, logical OR, and logical NOT results based on these values. Finally, the program prints the results on the screen using the printf function.
By running this program on a Raspberry Pi with GCC (GNU Compiler Collection) installed, the user can input their desired values for A and B and verify that the outputs of A && B, A || B, and !(A || B) match the expected values.
Learn more about Raspberry Pi here:
https://brainly.com/question/31084397
#SPJ11
My serious question that needs answering pronto!!!
How do I turn my computer??? I keep on telling it very clearly to turn on and it doesn't budge. I'm pretty sure I pressed all the buttons and none of them worked. There is a button that is litten up in the corner but I'm afraid that if I press it, my computer will go in self-destruct mode. PLEASE HELP!!!
Answers
Answer:
It depends on what the button looks like but sometimes you need to press it. If it is an actual computer press the power on button attached to the box that should be hooked up to the computer.
Explanation:
heyyyyyy
byeeeeeeeeeeeeeeeeeeeeeee
Answers
Answer:
byeeeeeeee
Explanation:
Answer:
Heyyyyyyy
Byeeeeeee
Explanation:
Concerns about health information systems in general and EHRs in particular include which of the following?
A. Interoperability of systems
B. Cybersecurity
C. Integrity of the data itself
D. The adoption of and transition to ICD-10
E. Interoperability of systems, cybersecurity, and integrity of the data itself
F.All of these are correct.
Answers
All of the choices are correct due to all the multiple information systems and EHR’s
Hope this helps
how are the strings playing the b' section? strings are tapped with the wood side of the bow two strings are bowed simultaneously plucked muted
Answers
In the B' section, the strings are played by tapping them with the wood side of the bow, bowing two strings simultaneously, plucking, and muting.
To achieve the tapping effect, the musician uses the wooden part of the bow to strike the strings gently. This creates a percussive sound on the strings, adding a unique texture to the music. Additionally, bowing two strings at the same time allows for the creation of rich harmonies and layered tones. By applying pressure and movement with the bow, the musician can control the dynamics and intensity of the sound produced.
Plucking the strings involves using the fingers to pluck or snap the strings, resulting in a sharp and distinct sound. This technique adds variety to the overall timbre and allows for precise articulation of individual notes. Furthermore, muting the strings involves lightly touching them with the fingers or using special mutes to dampen the vibrations. This technique can be used to create muted or "muffled" sounds, altering the tone color and adding a sense of depth to the music.
By incorporating these techniques into the B' section, the strings produce a diverse range of sounds and textures, contributing to the overall expressiveness and musicality of the composition.
Learn more about dynamics programming here: brainly.com/question/30885026
#SPJ11
source intends to use any one of the following two strategies, to transmit independent and equiprobable BITS B
1
,B
2
∈{−1,1} over an INDEPENDENT GAUSSIAN NOISE CHANNEL; Treat the BITS as BERNOULLI 1/2 random variables and V
i
:i∈{1,2} as zero mean INDEPENDENT Gaussian r.vs with variance σ
2
. Assuming (Single BIT per channel use): Y
1
=B
1
+V
1
Y
2
=B
2
+V
2
Devise a suitable Inferencing rule For detecting bits B
1
and B
2
, when Measurements at the receiver's side are available as Y
1
=y
1
and Y
2
=y
2
Determine the Prob(ERROR). \begin{tabular}{|l|} \hline Assuming (WITH PRE-CODING): \\ Y
1
=B
1
+B
2
+V
1
\\ Y
2
=B
1
−B
2
+V
2
\end{tabular} Compare the Prob(ERROR) in both cases and comment!!
Answers
For the independent and equiprobable BITS B1 and B2, the optimal inference rule is to compare Y1 and Y2 to determine B1 and B2. The probability of error depends on the noise variance.
In the first case without pre-coding, the inference rule is to compare Y1 and Y2 individually with a threshold of zero. If Y1 > 0, then B1 = 1; otherwise, B1 = -1. Similarly, if Y2 > 0, then B2 = 1; otherwise, B2 = -1. The probability of error can be calculated based on the error probability of individual Gaussian variables.In the second case with pre-coding, the inference rule involves adding Y1 and Y2. If Y1 + Y2 > 0, then B1 = 1; otherwise, B1 = -1. The inference for B2 depends on the subtraction Y1 - Y2. If Y1 - Y2 > 0, then B2 = 1; otherwise, B2 = -1. The probability of error in this case can also be determined based on the error probability of Gaussian variables.Comparing the probabilities of error in both cases would require specific values for the noise variance (σ^2) and a comparison of the error probabilities calculated based on those values.
To know more about noise click the link below:
brainly.com/question/29991623
#SPJ11
someone please tell me if you watch drag race (rupauls drag race) I need someone to talk to about it
Answers
Your grandfather got a call from Microsoft telling him that, according to their records, his computer is running very slow lately. They guide him to a website where he downloads a program that lets the person on the phone interact directly with his computer to fix the problem. What has your grandfather fallen victim to
Answers
codehs python 4.7.6 Powers of Two
it says I'm wrong because I need


Answers
\(\huge\fbox\orange{A} \huge\fbox\red{N}\huge\fbox\blue{S}\huge\fbox\green{W}\huge\fbox\gray{E}\huge\fbox\purple{R}\)
\(\huge\underline\mathtt\colorbox{cyan}{in attachment}\)

Following are the program to calculate the power of two:
Program Explanation:
Defining an integer variable "i" that hold an integer value.Defining a for loop that checks "i" value in between 20, inside this it calculates power of two.At the last use print method to print its value.Program:
i=1#holding integer value in i
for i in range(20):#defining a for that starts 1 to 20
i = 2 ** i#calculate power of 2 in i variable
print(i)#print value
Output:
Please find the attached file.
Learn more:
brainly.com/question/23170807

how do you solve 3.2.8 Repeating Message in Code HS

Answers
The program is an illustration of loops.
Loops are used to perform iterative and repetitive operations.
The correct program where comments are used to explain each line is as follows:
public class MyProgram extends ConsoleProgram {
public void run() {
//This prompts the user for the number of times to repeat the message
echo(" ", readInt("Times to repeat: "));
}
private void echo(String lineOne, String lineTwo, int numTimes) {
//The following iteration is repeated numTimes times
for (int i = 0; i < numTimes; i++){
//This prints lineOne
System.out.println(lineOne);
//This prints lineTwo
System.out.println(lineTwo);
}
}
}
Read more about similar programs at:
brainly.com/question/17972093
Which operator can be used in string concatenation?
Answers
Because the & operator is exclusively defined for strings and lowers the possibility of an accidental conversion, it is advised for string concatenation.
Using the + or += operator in Java or the function from the java. lang. String class, two strings can be joined together. The SQL server's || operator is a concatenation operator that creates a connection between two or more strings or columns and produces the result. One string is appended to the end of another string using the Java String function. The value of the string that was supplied into the method is appended to the end of the string that this method returns.
Learn more about string here-
https://brainly.com/question/14528583
#SPJ4
to find a value in an ordered array of 200 items, how many values must binary search examine at most?
Answers
Answer:
8
Explanation: