1 // Application contains a starting list of three products for sale2 // The user is prompted for additional items3 // After each new entry, the alphabetically sorted list is displayed4 import java.util.*;5 public class DebugNine36 {7 public static void main(String[] args)8 {9 ArrayListproducts = new ArrayList();10 products.add(shampoo);11 products.add(moisturizer);12 products.add(conditioner);13 Collections.sort(products);14 display(products);15 final String QUIT = "quit";16 String entry;17 Scanner input = new Scanner(System.in);18 System.out.print("\nEnter a product or " + QUIT + " to quit >> ");19 entry = input.nextLine();20 while(entry.equals("quit"))21 {22 products.add(entry);23 Collections.sort(products);24 display()25 System.out.print("\nEnter a product or " + QUIT + " to quit >> ");26 entry = input.nextLine();27 }28 public static void display(ArrayList products)29 {30 System.out.println("\nThe size of the list is " + products.size());31 for(int x = 0; x == products.size(); ++x)32 System.out.println(products.get(x));33 }34 }35//Debugging Exercises, Chapter 9;Java Programming, Joyce Farraell, 8th
Answers
Answer:
Here is the corrected code:
import java.util.*;
public class DebugNine36 { //class name
public static void main(String[] args) { //start of main method
ArrayList<String>products = new ArrayList<String>(); //creates an ArrayList of type String names products
products.add("shampoo"); //add shampoo to product array list
products.add("moisturizer"); //add moisturizer product array list
products.add("conditioner"); //add conditioner product array list
Collections.sort(products); //sort the elements in products array list
display(products); //calls display method by passing products array list
final String QUIT = "quit"; //declares a variable to quit the program
String entry; //declares a variable to hold product/element or quit
Scanner input = new Scanner(System.in); //creates Scanner object
System.out.print("\nEnter a product or " + QUIT + " to quit >> "); //prompts user to enter a product or enter quit to exit
entry = input.nextLine(); //reads the entry value from user
while(!entry.equals("quit")) { //loops until user enters quit
products.add(entry); //adds entry (product) to products array list
Collections.sort(products); //sorts the elements in products array list
display(products); //calls display method by passing products arraylist
System.out.print("\nEnter a product or " + QUIT + " to quit >> "); //keeps prompting user to enter a product or enter quit to exit
entry = input.nextLine(); } } //reads the entry value from user
public static void display(ArrayList products) { // method to display the list of products
System.out.println("\nThe size of the list is " + products.size()); //displays the size of the array list named products
for(int x = 0; x < products.size(); ++x) //iterates through the arraylist products
System.out.println(products.get(x)); } } //displays each item/element in products array list
Explanation:
In the code the following statement are corrected:
1.
ArrayListproducts = new ArrayList();
This gave an error: cannot find symbol
This is corrected to :
ArrayList<String>products = new ArrayList<String>();
2.
products.add(shampoo);
products.add(moisturizer);
products.add(conditioner);
Here shampoo moisturizer and conditioner are String type items that are to be added to the products so these strings have to be enclosed in quotation marks.
This is corrected to :
products.add("shampoo");
products.add("moisturizer");
products.add("conditioner");
3.
display();
This method is called without giving any arguments to this method. The method display takes an ArrayList as argument so it should be passed the arraylist products to avoid error that actual and formal argument lists differ in length .
This is corrected to :
display(products);
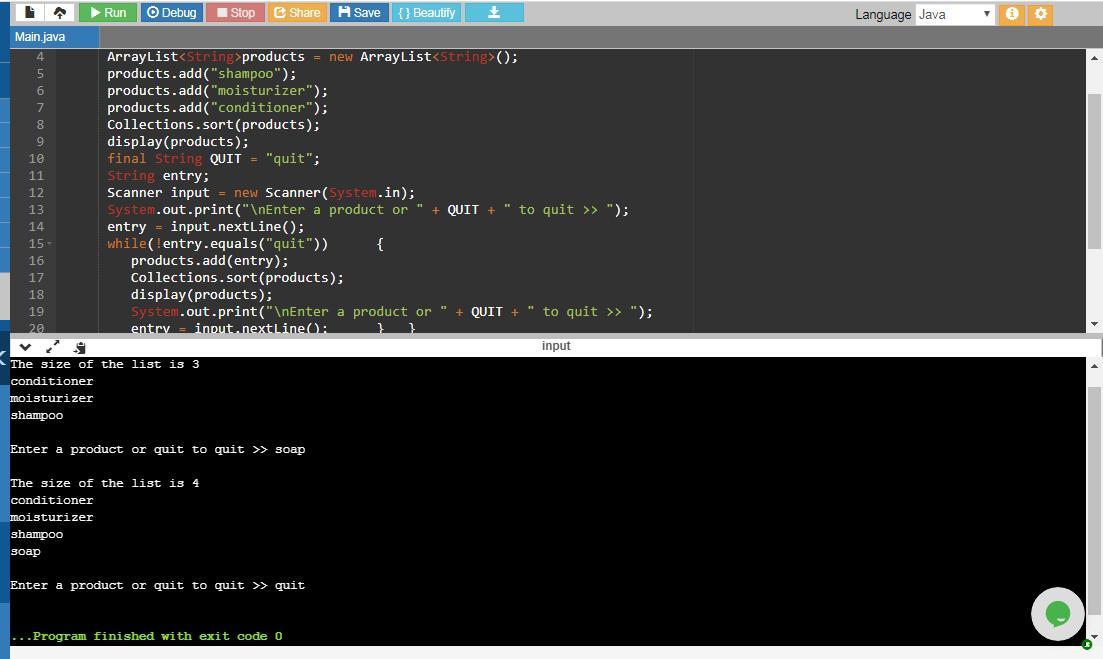
The screenshot of output is attached.
Related Questions
A Meera array is defined to be an array containing only numbers as its elements and for all n values in the array, the value n*2 is not in the array. So [3, 5, -2] is a Meera array because 3*2, 5*2 or 2*2 are not in the array. But [8, 3, 4] is not a Meera array because 2*4=8 and both 4 and 8 are elements found in the array. Write a function that takes an array of numbered elements and prints “I am a Meera array” in the console if its array does NOT contain n and also n*2 as value. Otherwise, the function prints “I am NOT a Meera array” ○ Test 1: checkMeera([10, 4, 0, 5]) outputs “I am NOT a Meera array” because 5 * 2 is 10 ○ Test 2: checkMeera([7, 4, 9]) outputs “I am a Meera array” ○ Test 1: checkMeera([1, -6, 4, -3]) outputs “I am NOT a Meera array” because -3 *2 is -6
Answers
The program based on the question requirements:
The Programfunction checkMeera(arr) {
for (let num of arr) {
if (arr.includes(num*2)) {
console.log("I am NOT a Meera array");
return;
}
}
console.log("I am a Meera array");
}
The function takes an array as input and iterates through each element using a for-of loop.
For each element, it checks if its double is also present in the array using the includes() method.
If found, the function prints "I am NOT a Meera array" and returns. If no such element is found, the function prints "I am a Meera array".
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1
Answer all questions

Answers
For one to be able to draw a times table via the use of PHP, a person need to use a nested for loop to iterate via each row and column of the table as well as display the product of the two numbers.
What is the loop?The Difference between MD5 and that of SHA1 are :
MD5 and SHA1 are known to be used both as a form of hashing algorithms that are employed to change data of arbitrary size into a fixed-size hash value.Note that SHA1 is seen as secure when compared to MD5 but slightly slower, and that MD5 is faster.
Learn more about loop from
https://brainly.com/question/26568485
#SPJ1
See text below
How to draw a times table using php
Difference between MD5 and SHA1
Write a program to check if a number is positive or negative
Write a count down program using switch statement
Write a program to display a pyramid pattern using increment or decreament
What is a loop
What is a for loop
What is a while loop
Write a program to make use of logical statement



Write a C program that creates a function bitFlip() that takes an int parameter and returns an int that has all of the int that was passed in bits flipped.
It changes all 0s to 1s and all 1s to 0s. In the main function, read in an int num using scanf, call bitFlip(), and the function returns num with its bits flipped.
Output example:
Enter an integer: 2
Integer before bits were flipped: 00000000000000000000000000000010
Integer after bits were flipped: 11111111111111111111111111111101
The flipped number is: -3
Answers
Answer:
Here's an example C program that implements the bitFlip() function:
#include <stdio.h>
int bitFlip(int num) {
return ~num; // Use bitwise NOT operator to flip all bits
}
int main() {
int num;
printf("Enter an integer: ");
scanf("%d", &num);
printf("Integer before bits were flipped: %032d\n", num); // Use %032d to print leading zeros
num = bitFlip(num);
printf("Integer after bits were flipped: %032d\n", num);
printf("The flipped number is: %d\n", num);
return 0;
}
The bitFlip() function takes an int parameter num and returns an int with all of its bits flipped using the bitwise NOT operator ~.
In the main() function, we first read in an integer num using scanf(). We then print out the binary representation of num using the %032d format specifier to ensure that it has 32 bits with leading zeros. We then call bitFlip() to flip the bits of num and print out the binary representation of the flipped number. Finally, we print out the value of the flipped number using %d.
Sample output:
Enter an integer: 2
Integer before bits were flipped: 00000000000000000000000000000010
Integer after bits were flipped: 11111111111111111111111111111101
The flipped number is: -3
Explanation:
The instructions that make up a computer program are sometimes referred to as __________.
a. statements
b. function
c. control
d. encapsulation
Answers
Answer:
a. statements
Explanation:
GIVE ME BRAINLEST
Write three tasks students can perform in a digital classroom.
Answers
Students can perform several tasks in a digital environment. For example, they can watch instructional videos, take notes, and participate in peer discussions.
A digital classroom is a study space that has been electronically improved and allows students to use the internet and web-based applications to improve their learning.
What is digital classroom?A digital classroom is one that improves student learning by utilizing computers, tablets, the internet, and instructional software.
The digital classroom can be a supplement to the physical classroom, offering more chances for study and cooperation.
A digital classroom is a learning environment that has been enhanced electronically so that students can access the internet and web-based tools to enhance their learning.
The following tasks could be carried out in such a setting:
Using apps for meetings and online forums to collaborate with colleagues.The ability to access more educational content and materials from pertinent websites and applications.Online tests and assignments allowed for real-time progress monitoring for students.Thus, a digital classroom's capabilities give students the resources they need for easier, more seamless learning.
For more details regarding digital classroom, visit:
https://brainly.com/question/4178835
#SPJ6
List the five component of information system
Answers
Answer:
hardware, software, database, network and people
where do you think data mining by companies will take us in the coming years
Answers
In the near future, the practice of companies engaging in data mining is expected to greatly influence diverse facets of our daily existence.
What is data miningThere are several possible paths that data mining could lead us towards.
Businesses will sustain their use of data excavation techniques to obtain knowledge about each individual customer, leading to personalization and customization. This data will be utilized to tailor products, services, and advertising strategies to suit distinctive tastes and requirements.
Enhanced Decision-Making: Through the use of data mining, companies can gain valuable perspectives that enable them to make more knowledgeable decisions.
Learn more about data mining from
https://brainly.com/question/2596411
#SPJ1
Which of the following is the MOST important reason for creating separate users / identities in a cloud environment?
Answers
Answer:
Because you can associate with other
Answer:
Explanation:
To avoid cyberbully
Hey tell me more about your service
Answers
Answer:
look below!
Explanation:
please add more context and I’ll be happy to answer!
8. To be a Bunk Leader, a staff member must have over 4 service years and have completed leadership training. In cell L2, enter a formula using the IF and AND functions, as well as structured references to determine if Adam Moriarty can be a bunk leader. a. The logical test in the IF function should determine if the staff member’s Service Years is greater than 4 AND the staff member’s Leadership Training status is "Yes". Remember to use a structured reference to the Service Years and the Leadership Training columns. b. The function should return the text Yes if a staff member meets both of those criteria.
Answers
Answer:
=IF(AND([Service Year]>4,[Leadership Training]="Yes"),"Yes","No")
Explanation:
To make use of structured references, a table has to be defined (created). Assume that the table definition is as follows;
Staff --- Service Year --- Leadership Training --- Status
In cell L2, type the above formula
Analyzing the formula:
=; An Excel formula must start with an = sign
IF; This signifies that the formula is an "IF" function
AND; This signifies that there are more than one condition in thee formula and all conditions must be true
[Service Year]>4; The question requires that the formula uses a structured referencing. Structured referencing is such that the columns of a table are called instead of cell names;
Here, reference is being made to [Service Year] because Service Year is a column name and its value must be greater than 4
[Leadership Training]="Yes"; The above analysis is applicable here too because Leadership Training is column name and it must be "Yes" for it to return a true value.
"Yes"; Return Yes if both conditions are true
"No"; Otherwise, return No.
________ databases are better than relational databases at handling unstructured data such as audio clips, video clips, and pictures.
Answers
Answer:
"Object-oriented" would be the correct choice.
Explanation:
An object-oriented database seems to be a database that subscribes to a framework containing object-depicted details. Throughout the context of the relational database management system, object-oriented is a unique product that is not as popular and most well-known as traditional web applications.This indicates that internet connectivity to existing records has to implement the previously defined connections for interacting components established by that same containers.Number the steps to describe how Tristan can complete
this task.
Cut the Television and related equipment row.
Paste the Television and related equipment row.
Click the plus sign on the left side of the table between
the last two rows.
Answers
Answer:
Cut the Television and related equipment row.Click the plus sign on the left side of the table between the last two rows.Paste the Television and related equipment row.Explanation:
In order to move the row, Tristan should first select the row and then cut it. This will ensure that the row will be moved completely instead of copied.
Tristan should then hover with the mouse between the last two rows and click on the plus sign on the left side. It will add a new row to the sheet. between the last two rows.
Tristan should then select the topmost cell and click paste. The television row will be pasted there and Tristan would have successfully moved it.
Answer:
2 3 1 Your Welcome
Explanation:
Write a program in which given an integer num, return the sum of the multiples of num between 1 and 100. For example, if num is 20, the returned value should be the sum of 20, 40, 60, 80, and 100, which is 300. If num is not positive, return 0.
Answers
Answer:
#include<iostream>
using namespace std;
int main()
{
int num=0,sum=0;
cout<<"Insert Number to find sum of mutiples.";
cin>>num;
int temp=num;
if(num>0){
sum+=num;
while(num<100){
num+=temp;
sum+=num;
}
cout<<"Sum of Multiples is ="<<sum<<endl;
}else{
return 0;
}
return 0;
}
Explanation:
This code is written in c++. Written by Saad-Ur-Rehman.
Which of the following if statements uses a Boolean condition to test: "If you are 18 or older, you can vote"? (3 points)
if(age <= 18):
if(age >= 18):
if(age == 18):
if(age != 18):
Answers
The correct if statement that uses a Boolean condition to test the statement "If you are 18 or older, you can vote" is: if(age >= 18):
In the given statement, the condition is that a person should be 18 years or older in order to vote.
The comparison operator used here is the greater than or equal to (>=) operator, which checks if the value of the variable "age" is greater than or equal to 18.
This condition will evaluate to true if the person's age is 18 or any value greater than 18, indicating that they are eligible to vote.
Let's analyze the other if statements:
1)if(age <= 18):This statement checks if the value of the variable "age" is less than or equal to 18.
However, this condition would evaluate to true for ages less than or equal to 18, which implies that a person who is 18 years old or younger would be allowed to vote, which is not in line with the given statement.
2)if(age == 18):This statement checks if the value of the variable "age" is equal to 18. However, the given statement allows individuals who are older than 18 to vote.
Therefore, this condition would evaluate to false for ages greater than 18, which is not correct.
3)if(age != 18):This statement checks if the value of the variable "age" is not equal to 18.
While this condition would evaluate to true for ages other than 18, it does not specifically cater to the requirement of being 18 or older to vote.
For more questions on Boolean condition
https://brainly.com/question/26041371
#SPJ8
A printer is considered to be in the category of
a. software
Selected:b. hardware
c. operational system
d. equipment
Answers
A printer is considered to be in the category of b. hardware.
What is hardware?Computer hardware contains the physical characteristics of a computer, such as a case, central processing unit (CPU), random access memory (RAM), monitor, mouse, keyboard, computer data storage, pictures card, sound card, speakers, and motherboard.
Hardware directs to the physical components of a computer. Also directed to as the machinery or the equipment of the computer. Examples of hardware in a computer exist the keyboard, the monitor, the mouse, and the processing unit However, most of a computer's hardware cannot be caught; It's inside the computer case.
A printer exists as an external hardware output device that brings the electronic data stored on a computer or other device and develops a hard copy.
Hence, A printer is considered to be in the category of b. hardware.
To learn more about hardware refer to:
https://brainly.com/question/24370161
#SPJ2
Changing the position of text on the screen is called ________.
Answers
Answer:
Formatting
Explanation:
Hope this helps
Your teacher has asked you to redesign a common board game to depict the historical periods of
technology. The board game should include instructions and questionis specific to the design problem. All
resources should include APA or MLA citations.
Answers
Answer:
APA include citations correct answer
It specifies the amount of memory needed to store data.
Answers
magbigay ng limang magandang lugar na tinatawag na tourist spot sa iyo sa inyong lugar o probinsya
Answer: Is it RAM? Random Access Memory
Explanation: Ram is used to reading/writing data. It might control the amount of memory that is stored.
How does a distributed operating system work?
Answers
Answer:
A distributed operating system is system software over a collection of independent, networked, communicating, and physically separate computational nodes. They handle jobs which are serviced by multiple CPUs. Each individual node holds a specific software subset of the global aggregate operating system.
These systems run on a server and provide the capability to manage data, users, groups, security, applications, and other networking functions.
plz mark it as brainliest
Answer:
Explanation:A distributed operating system is system software over a collection of independent, networked, communicating, and physically separate computational nodes. They handle jobs which are serviced by multiple CPUs. Each individual node holds a specific software subset of the global aggregate operating system.
tape is magnetic tape which sound ca be recorded , true or false?
Answers
Answer:
I think true
Explanation:
While onsite at a customer location, it is determined the processor in the Processor and Heatsink Module (PHM) must be replaced. What are the steps to remove the processor from the PHM? Click and drag the steps into the correct sequence, then click Submit.
Answers
The steps to remove the processor from the PHM:
1. Power off the system and disconnect all cables.
2. Remove the system cover.
3. Remove the processor heatsink.
4. Remove the processor from the socket.
What is PHM?
A longitudinal actionable patient record is created by combining and managing patient data from various health information technology resources, analysing that data, and then taking the necessary steps to enhance clinical and financial outcomes. The PHM programme provides actionable insights for efficiency and patient care by combining clinical, financial, or operational data from many platforms. The PHM program's key components include care management including gap analysis, risk stratification infrastructure, a coordinated delivery system, and a carefully managed partnering network.
To learn more about PHM
https://brainly.com/question/29375394
#SPJ9
Show that in a simple graph with at least two vertices there
must be two vertices that have the same degree.
Answers
To prove that in a simple graph with at least two vertices there must be two vertices that have the same degree, we can use the Pigeonhole Principle.
How to do the proofLet G be a simple graph with n vertices. The degree of a vertex in G is the number of edges incident to that vertex. The degree of a vertex can range from 0 (if the vertex is isolated) to n-1 (if the vertex is adjacent to every other vertex in the graph).
Suppose for the sake of contradiction that all n vertices of G have distinct degrees. Then the possible degrees of the vertices are 0, 1, 2, ..., n-1, and there are n different degrees.
However, since there are only n vertices in the graph, there are only n possible degrees that the vertices can have. Therefore, by the Pigeonhole Principle, there must be at least two vertices in G that have the same degree.
This contradiction shows that our assumption that all n vertices of G have distinct degrees must be false, and thus there must be two vertices in G that have the same degree.
Read more on vertices here:https://brainly.com/question/1217219
#SPJ1
1. What are the main uses for Protein in the body?
2. What are the main types of food you get Protein from?
Answers
Answer:
1 muscle building
2 meats, nuts
Explanation:
1 proteins are needed for growth ,they are used to repair worn out tissues, they are used to make enzymes and hormone they give energy ,they are used to make white blood cells stronger.
2 meat egg fish milk beans
In what year was napier bone invented
Answers
The Napier's Bones is a manually-operated calculating device, invented by the Scottish mathematician John Napier in the early 17th century, around the year 1617.
What is Napier bone used for?Napier's Bones, also known as Napier's rods, are used for multiplication, division, and square root calculations. The device consists of a set of rectangular rods or bones with each bone representing a single digit in the multiplication table.
By manipulating the rods, users can quickly perform calculations that would otherwise be time-consuming to complete by hand. The Napier bone is an early example of a calculating device and is considered a predecessor to modern mechanical calculators.
Learn more about Napier bone at:
https://brainly.com/question/24242764
#SPJ1
Mr. Johnny Jackson, a student at UB is trying to develop a wireless network at his home. He needs to connect three desktop PCs and a printer. Mr. Jackson would require at a minimum.A. An ISP, a router, Bluetooth B. An ISP, a router, WiFi cards C. A router, a hub, WiFi cards D. A router, Bluetooth, signal booster
Answers
The correct answer regarding the Desktop is B. An ISP, a router, WiFi cards.
What is Desktop?Desktop is a term used to refer to a computer that is meant to be used in a single location, typically at a desk or table. It is a powerful machine that is capable of running a variety of applications and programs. Desktops are larger than laptops, and typically have more powerful components that allow them to run more intensive applications and processes. Desktops are also more customizable than laptops, allowing users to upgrade components as needed and keep their machine up to date. Common components of a desktop include a monitor, keyboard, mouse, and tower. Desktops can be connected to the internet via an Ethernet cable or through a wireless network connection.
This is because an ISP (internet service provider) is required to provide the connection to the internet, a router is used to connect multiple devices and a WiFi card is needed for each device to be connected to the wireless network. Bluetooth and signal boosters are not necessary for this application.
To learn more about Desktop
https://brainly.com/question/8317079
#SPJ4
what is the most fast WIFI.
5G
1G
no WIFI
Answers
Answer:
In my mind I would say 5G
Explanation:
Answer:
5G is the fasted
Explanation:
5G is currently the fasted
What is it called when there is stored energy in the battery after an accident that has caused damage to the protective case or wiring harness?
A) Stranded energy
B) Explosive energy
C) Lost energy
D) Entrapped energy
Answers
B) Explosive energy is when there is stored energy in the battery after an accident that has caused damage to the protective case or wiring harness.
Is the energy stored when released may cause serious accidents or physical damage?Stored energy are known to be any form of mechanical, gravitational, hydraulic that is known to be energy stored in machines as well as in equipment.
Stored energy hazards if released accidentally can cause serious injury.
Therefore, B) Explosive energy is when there is stored energy in the battery after an accident that has caused damage to the protective case or wiring harness.
Learn more about energy from
https://brainly.com/question/13881533
#SPJ1
You enjoy helping people find solutions to problems that they are having with technology. Which job might be best for you?
A database manager
B technical support
C website design
D data scientist
Answers
Answer: B - technical support
Explanation:
Fritz is a big fan of the racerville rockets. unfortunate;y, the team has been accused of cheating during their games. Fritz reads many articles and posts about this developing news story. His social media algorithms have "learned" that he's a fan of the team, so his feed doesnt show him any articles that argue the accusations are true. From this, Fritz decides his favorite team must be innocent of all cheating charges. Fritz is now in
A. a filter bubble
B. A third party
C. A subculture
D. an echo chamber
Answers
Option(D) is the correct answer. Fritz is now in an echo chamber.
Fritz's situation aligns with the concept of an echo chamber. An echo chamber refers to an environment, such as social media, where individuals are exposed to information and opinions that reinforce their existing beliefs and perspectives.
In this case, Fritz's social media algorithms have filtered out articles that present arguments in favor of the cheating accusations, creating an echo chamber that only confirms his preconceived notion of the team's innocence.
As a result, Fritz is insulated from diverse viewpoints and alternative perspectives, which can hinder critical thinking and a comprehensive understanding of the situation.
for similar questions on Fritz.
https://brainly.com/question/5100081
#SPJ8
if a mosquito on the right is moving 10m/s and has kinectic enegry 0.25 j what is the mass
Answers
Answer:
Mass = 0.005 kg
Explanation:
Given:
Velocity V = 10 m/s
kinetic energy 0.25 j
Find:
Mass of mosquito
Computation:
K.E = 1/2(m)(v²)
0.25 = 1/2(m)(10²)
0.5 = m x 100
Mass = 0.005 kg