0.0% complete Question For the office network upgrade to Gigabit Ethernet, you need proper cabling. What is your choice of cabling to achieve at least 1 Gbps speed
Answers
To achieve at least 1 Gbps speed for an office network upgrade to Gigabit Ethernet, a suitable choice of cabling would be Category 5e (Cat5e) or Category 6 (Cat6) Ethernet cables.
Cat5e cables are an enhanced version of the original Category 5 cables and are designed to support Gigabit Ethernet and provide transmission speeds of up to 1 Gbps.
They have improved specifications for crosstalk and interference, allowing for reliable and high-speed data transmission.
Cat5e cables are widely available, cost-effective, and commonly used in various network installations.
Cat6 cables are an even more advanced option, providing superior performance compared to Cat5e.
They offer higher bandwidth and reduced crosstalk, enabling better signal integrity and supporting higher data rates.
Cat6 cables are designed for Gigabit Ethernet and can support speeds up to 10 Gbps over short distances.
While upgrading to Cat6 cables may provide future-proofing and additional performance headroom, they are generally more expensive than Cat5e cables.
When choosing between Cat5e and Cat6, factors such as budget, anticipated network requirements, and the length of cable runs should be considered.
If the office network upgrade primarily requires 1 Gbps speeds and cost-effectiveness is a priority, Cat5e cables would be a suitable choice.
For more questions on Gigabit Ethernet
https://brainly.com/question/31941605
#SPJ11
Related Questions
Some one help pls will mark brainless !!!!!
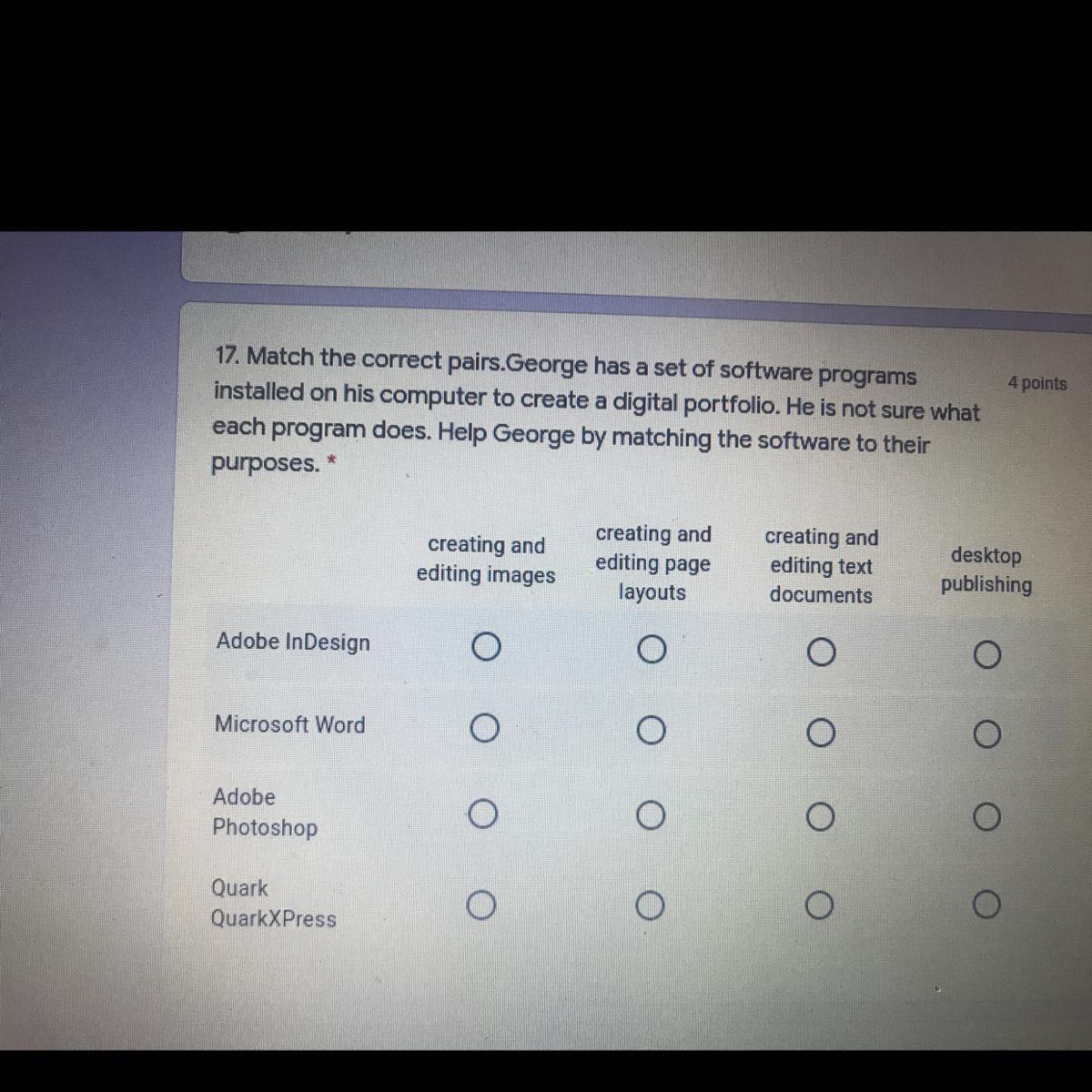
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
uses computer resources from multiple locations to solve a common problem
Answers
I think is the answer
Answer:grid computing
Explanation:
write the steps to insert date and time in a cell
Answers
Answer:
Do one of the following:
To insert the current date, press Ctrl+; (semi-colon).
To insert the current time, press Ctrl+Shift+; (semi-colon).
To insert the current date and time, press Ctrl+; (semi-colon), then press Space, and then press Ctrl+Shift+; (semi-colon).
what are the shell commands to list defined message queues and delete a defined message queue, respectively?
Answers
The shell commands to list defined message queues and delete a defined message queue, respectively, are:
1. To list defined message queues, use the command `ipcs -q`. This command will display a list of message queues with their IDs, permissions, and other related information.
2. To delete a defined message queue, use the command `ipcrm -Q `. Replace `` with the actual ID of the message queue you want to delete. This command will remove the specified message queue from the system.
The command "ipcs -q" is used in Unix-like operating systems (such as Linux) to display information about message queues. The "ipcs" command is a utility for reporting inter-process communication (IPC) facilities status. By appending the "-q" option, you specifically request information about message queues. When you run the "ipcs -q" command, it will display details about the active message queues on the system, including their identifiers (IDs), message queue size, number of messages in the queue, and various permissions and ownership information.
The command "ipcrm -Q" is used in Unix-like operating systems (such as Linux) to remove (delete) message queues. The "ipcrm" command is a utility for removing IPC (inter-process communication) resources. By appending the "-Q" option, you specifically indicate that you want to remove message queues. When you run the "ipcrm -Q" command followed by the identifier (ID) of the message queue you wish to remove, it will delete the specified message queue and release the associated system resources.
Learn more about identifier:https://brainly.com/question/13437427
#SPJ11
Describe the indicators and hazards of a metal deck roof fire in an unprotected steel joist warehouse as well as the techniques to deal with the problem.
Answers
Answer:
Explanation:
Joist mansory building is a type of building with the exterior wall of mansory, which is capable of withstanding combustion or fire for nothing less than an hour.
Therefore, the best method to deal with fire is to build with materials that are fire resistant.
Based on the information given, it's vital to make the construction with materials that are fire resistant.
Within the fire service, building construction can simply be defined as the study of how buildings can be put together. It's also how materials and connections are used.
From the information given, it's stated that the metal deck roof is in an unprotected steel joist warehouse. Therefore, in order to prevent hazard, it's important to make the construction with materials that are fire-resistant.
Read related link on:
https://brainly.com/question/17050293
A Chief Security Officer (CSO) has asked a technician to devise a solution that can detect unauthorized execution privileges from the OS in both executable and data files, and can work in conjunction with proxies or UTM. Which of the following would BEST meet the CSO's requirements?
A. Fuzzing.
B. Sandboxing.
C. Static code analysis.
D. Code review.
Answers
A solution which would best meet the CSO's requirements is: B. Sandboxing.
What is a sandbox?A sandbox can be defined as an isolated environment in a computer system or on a network that is designed and developed to mimic end user operating system (OS) and environments, so as to detect unauthorized execution privileges from the operating system (OS).
In cybersecurity, sandboxing is typically used to safely execute suspicious code and data files without causing any harm to the host device or network. Also, sandboxing can work in conjunction with proxies or unified threat management (UTM).
Read more on sandboxing here: https://brainly.com/question/25883753
____ is the order of arrangement of files and folders
Answers
Answer:
Organization is the order of arrangement of files and folders.
Which of the following device categories includes ultrabooks and netbooks? Select one: a. laptop b. supercomputers c. tablet d. smartphones. b. processor.
Answers
The device category that includes ultrabooks and netbooks is laptops. Laptops are portable computers that are designed for on-the-go use. Ultrabooks and netbooks are both subcategories of laptops. Ultrabooks are thin and lightweight laptops that are designed to be ultra-portable.
They are typically less than 0.8 inches thick and weigh less than 3 pounds. Netbooks, on the other hand, are small laptops that are designed primarily for web browsing and basic computing tasks. They are typically less powerful than traditional laptops but are also more affordable. It is important to note that while ultrabooks and netbooks are both subcategories of laptops, they do have some key differences.
Ultrabooks are typically more powerful and expensive than netbooks, and they are designed for more intensive computing tasks. Netbooks, on the other hand, are designed for basic tasks such as web browsing, email, and word processing. In summary, the device category that includes ultrabooks and netbooks is laptops. While there are differences between ultrabooks and netbooks, both are subcategories of laptops that are designed for on-the-go use. the device category that includes ultrabooks and netbooks is a. Ultrabooks and netbooks are both subcategories of laptops. Ultrabooks are thin and lightweight laptops that are designed to be ultra-portable. They are typically less than 0.8 inches thick and weigh less than 3 pounds. Netbooks, on the other hand, are small laptops that are designed primarily for web browsing and basic computing tasks. They are typically less powerful than traditional laptops but are also more affordable. It is important to note that while ultrabooks and netbooks are both subcategories of laptops, they do have some key differences. Ultrabooks are typically more powerful and expensive than netbooks, and they are designed for more intensive computing tasks. Netbooks, on the other hand, are designed for basic tasks such as web browsing, email, and word processing. laptop. Ultrabooks and netbooks are both subcategories of laptops, designed to be portable and lightweight compared to traditional laptops. They do not fall under the categories of supercomputers, tablets, smartphones, or processors.
To know more about Laptops visit:
https://brainly.com/question/28525008
#SPJ11
how many instructions are supercomputers capable of processing in a single second?
Answers
Answer:
Trillions
Explanation:
A Supercomputer can process trillions of instructions in a second
How does Harrison react to the news that Katherine has to walk 800m to the bathroom? in hidden figures
Answers
Answer: Your welcome!
Explanation:
Harrison is outraged at the news that Katherine has to walk 800m to the bathroom. He angrily tells the building manager that this is unacceptable and demands that a bathroom be provided for the female employees. He also demands that Katherine and the other female employees be allowed access to the same facilities as their male counterparts. He then suggests that the NASA official in charge of the building should be reprimanded for allowing this situation to occur.
39
1. The following situation uses a robot in a grid of squares. The robot is represented by a triangle which
is initially in the top right square and facing left. The robot may not travel through the black squares.
L
Create a solution that would enable the robot to be in the position found below using at least 2
loops.

Answers
A solution that would enable the robot to be in the position found below using at least 2 loops is given below:
The ProgramPROCEDURE moveRobot
{
IF (CAN_MOVE (forward))
{
ROTATE_LEFT()
}
ELSE
{
ROTATE_RIGHT ()
}
{
MOVE_FORWARD ()
}
}
The given command helps enable the robot to move in different directions, provided it can move forward, so it would be able to rotate left and right.
Read more about programming here:
https://brainly.com/question/20119860
#SPJ1
the idea of programming by modeling real-world things into computer code is called _____________.
Answers
The concept of programming by translating elements of the actual world into computer code is known as programming that is object-oriented.
This is used in a notion that restricts specific areas of a program's access to open channels. Constants are identifiers that track values; however, unlike variables, constants are immutable. In object-oriented programming, objects are the customized models created from class templates.
A symbolic representation of binary machine language, assembly is a low-level computer language that is understandable by humans. A computer security concept known as the principle of least privilege (POLP) restricts users' access permissions to just those that are absolutely necessary for them to do their duties. Users are only allowed to access, write, or execute the files or resources they need in order to complete their tasks.
Learn more about programming Visit: brainly.com/question/28732193
#SPJ4
Selah is organizing all of the folders on her computer so she can find everything faster. She decides to make a "Work" folder, which she puts inside a "2021" folder, which she puts inside a "Budget" folder. Which method of organization is she using?
Answers
Answer:
Explanation:
Use Subdirectories
The simplest and most obvious advice. Whichever organization system you choose, you'll have to create folders to put your files in. Get in the habit of creating new directories constantly.
C://Budget/2021/Work

Upload a picture of your work needed to solve the problem using the Graphical Method of solving linear programs. Be sure to show all your work including the use of the each corner point to find the objective function value(s). The graph should be done as accurately as possible using and labeling appropriate unit values on the axis that reflect the context values...not too big and not too small. A farmer is going to divide her 40 acre farm between two crops. Seed for crop A costs $20 per acre. Seed for crop B costs $40 per acre. The farmer can spend at most $1000 on seed. If crop B brings in a profit of $230 per acre, and crop A brings in a profit of $100 per acre, how many acres of each crop should the farmer plant to maximize her profit? Let x be the number of crop A and y be the number of crop B. 1) Form a linear program that illustrates this problem. Be sure to show appropriate notations and include domain restrictions. 2) Graph the feasible region solution of the constraints. Find and label the corner points of the feasible region showing all the algebra needed to solve for the intersections of lines. 3) How many acres of each crop should the farmer plant to maximize her profit? acres of cropA acres of crop B $ is the best profit
Answers
The farmer should plant 15 acres of crop A and 25 acres of crop B to maximize her profit. The best profit she can achieve is $5,750.
In the given problem, the objective is to maximize the profit from crop planting. Let x represent the number of acres of crop A and y represent the number of acres of crop B. The objective function is Z = 100x + 230y, representing the total profit. The domain restrictions are as follows: x ≥ 0 (non-negativity constraint), y ≥ 0 (non-negativity constraint), x + y ≤ 40 (total farm size constraint), and 20x + 40y ≤ 1000 (seed cost constraint).
To graph the feasible region, we plot the constraints on a graph. The x-axis represents the number of acres of crop A, and the y-axis represents the number of acres of crop B. The constraints form a feasible region bounded by the lines x + y = 40, 20x + 40y = 1000, x ≥ 0, and y ≥ 0. By solving the equations of the lines, we find the corner points of the feasible region: (0, 0), (20, 0), (30, 10), and (0, 40).
To determine the optimal solution, we evaluate the objective function at each corner point. The objective function values are as follows: Z(0, 0) = 0, Z(20, 0) = 2,000, Z(30, 10) = 5,750, and Z(0, 40) = 9,200. The maximum profit of $5,750 occurs at (30, 10), indicating that the farmer should plant 30 acres of crop A and 10 acres of crop B to maximize her profit.
In summary, to maximize her profit, the farmer should plant 30 acres of crop A and 10 acres of crop B. This will result in a profit of $5,750.
learn more about maximize here
https://brainly.com/question/30072001
#SPJ11

Determine which problem matches the given inequality. c less-than 5 and one-half There are 5 and one-half fewer cups of sugar than flour. There are 5 and one-half more cups of sugar than flour. There are less than 5 and one-half cups of sugar. There are more than 5 and one-half cups of sugar.
Answers
Answer:
There are less than 5 1/2 cups of sugar.
Explanation:
Given
\(c < 5\frac{1}{2}\)
Required
Select a matching expression for the inequality
The inequality sign <, mean less than
So: we can say that \(< 5\frac{1}{2}\) means less than \(5\frac{1}{2}\)
From the given options, only option c shows less than \(5\frac{1}{2}\)
i.e. less than \(5\frac{1}{2}\) cups of sugar
Hence, (c) answers the question
Answer:
C
Explanation:
Which data type is –7?
int
single
string
float
Answers
Answer:
Int
Explanation:
Good Luck!
What is by far the most popular dns server software available?.
Answers
Answer:
I use the server
8.8.8.8
and
8.8.4.4
Explanation:
BIND (Berkeley Internet Name Domain) is by far the most popular DNS server software available.
What is the BIND?BIND(Berkeley Internet Name Domain) is open-source software that executes the Domain Name System (DNS) protocols for the internet. It is widely used on Unix-like operating systems, including Linux and macOS, as well as on Microsoft Windows.
BIND is developed and sustained by the Internet Systems Consortium (ISC), a nonprofit organization that encourages the development of the internet.
It is the most widely deployed DNS software in the world and is used by many internet service providers, businesses, and organizations to manage their DNS infrastructure.
Thus, BIND (Berkeley Internet Name Domain) is by far the most widely used DNS server software.
To learn more about DNS server software click here:
https://brainly.com/question/13852466
#SPJ12
How to create a shortcut to a website on your desktop?.
Answers
Answer:
open web browser, open your favorite website or webpage, right click on the web address located in the address bar of your web
Inputs should be blue colored font and should have ________ only. Process and outputs should be in black colored font and have _______ only.
Answers
Inputs should be blue colored font and should have hardcoded number only. Process and outputs should be in black colored font and have formulas only.
What does input implies?
Input refers to any data that is given to a computer or software application. Data input refers to the process of entering information into a computer because the information delivered is also regarded as data.
What does Output implies?
The output is how the computer presents the results of the process, such as text on a screen, printed materials, or sound from a speaker.
What is a hardcoded number?
Software developers may hardcode a distinct serial number directly into a program as a digital rights management technique. Or a public key is frequently hardcoded, resulting in DRM that is impossible to produce a keygen for.
What is DRM?
Copyrights for digital media can be secured through the use of digital rights management (DRM). This strategy makes use of tools that restrict the duplication and utilization of works protected by copyright as well as proprietary software.
Note that, process and outputs should be in black font with just formulas, while inputs should be in blue font with only hardcoded numbers.
Learn more about input click here:
https://brainly.com/question/20489800
#SPJ4
1. Given address of 195.223.50.0 and you need 6 subnets.
-How many bits needed to be borrowed?
-The new subnet mask?
-The block size for the subnet scheme?
-How many subnets created and useable host for this?
Answers
By borrowing 3 bits from the host portion of the IP address, we can create 6 usable subnets with 30 usable host addresses per subnet, and the new subnet mask will be 255.255.255.224.
1. To create 6 subnets, we need to borrow 3 bits from the host portion of the IP address. This is because 2^3 = 8, which is greater than or equal to 6.
2. The new subnet mask will be 255.255.255.224. This is because we borrowed 3 bits from the host portion, which means that the first 27 bits of the address will be used for the network portion and the remaining 5 bits will be used for the host portion. In binary, the subnet mask will be 11111111.11111111.11111111.11100000, which is equivalent to 255.255.255.224 in decimal.
3. The block size for the subnet scheme will be 32. This is because there are 5 bits remaining for the host portion of the address, and 2^5 = 32.
4. With 3 bits borrowed, we can create 8 subnets. However, 2 of these subnets will be reserved for the network address and broadcast address, so only 6 subnets will be usable. Each subnet will have 32 addresses, but 2 of these addresses will be reserved for the network address and broadcast address, so there will be 30 usable host addresses per subnet.
Learn more about IP address:
https://brainly.com/question/14219853
#SPJ11
(03 MC)Why is it important to set goals and share them with others?
A) Sharing goals makes you feel like you are better than the other person.
B) If you share your goals, you are more likely to achieve them.
C) Sharing goals is something you should do in order to get a good grade.
D) If you share your goals with others, people will like you more.
ANSWER: B) If you share your goals, you are more likely to achieve them.
Answers
Answer:
answer is b
Explanation:
hope it was helpful
Answer: B, If you share your goals, you are more likely to achieve them.
We know sharing goals can be helpful to everyone, one of the main reasons people share goals is so that they can get the motivation to carry on doing their work. For example, If you and a friend had a goal of going to the gym 3 times a week you would feel responsible if you told your friend that you wouldn't be able to complete the goal this week. Which would make you feel bad for your friend who wants to complete the goal. It also helps with motivation if your friend doesn't want to go then you encourage them and make sure they remember the goal.
Answer choice A, would not make much sense since you are doing the goal together, and + this is a school question and they wouldn't encourage ego. Answer choice C, could be a result of sharing goals with others but doesn't suit the question as much as B. Answer choice D, does apply to the question at all people could end up liking you more but it could also end up the other way around.
Our answer is without a doubt B
Enjoy!
can
you do keyword analysis and strategy for contiki app.
Answers
Yes, keyword analysis and strategy can be done for the Contiki app. Keyword analysis is a crucial part of search engine optimization (SEO) that enables the optimization of web content for various search engines.
Keyword analysis and strategy involve conducting research to identify the most relevant keywords to target and how to use them. The analysis and strategy help in making sure that the keywords used are relevant to the content on the Contiki app. The keywords can be used on different aspects of the Contiki app, such as its title, descriptions, app content, and app screenshots.An effective keyword analysis and strategy for the Contiki app involves researching various keywords and choosing the most relevant ones to use.
The keywords chosen should have a high search volume and low competition. The keyword strategy should also include the use of long-tail keywords to enhance the app's visibility.The keyword analysis and strategy for the Contiki app should also involve monitoring and analyzing the performance of the keywords. This will help in identifying any changes or trends in user behavior and updating the keyword strategy accordingly.In summary, keyword analysis and strategy are essential for optimizing the Contiki app for search engines. By choosing the most relevant keywords and using them effectively, the app can increase its visibility and attract more downloads.
To know more about search engines visit:
https://brainly.com/question/32419720
#SPJ11
which line of code will allow you to only load the localtime() method into active memory

Answers
Answer:
from time import localtime
Explanation:
have a lovely day :)
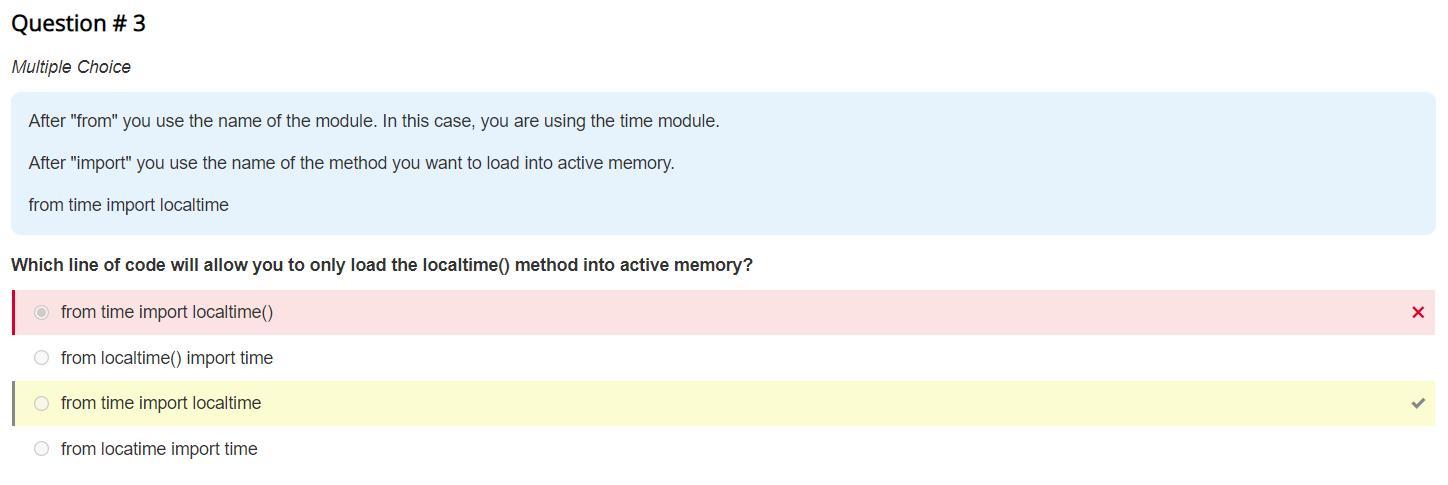
The line of code that will allow you to only load the localtime method into active memory is time.
The localtime function is simply known to be time in seconds as long as Epoch is targeted by timer into a broken-down time.
It is mostly written in local time. The function is known to be of timezone and any seasonal time adjustments. Local timezone information is used as though localtime() calls tzset().LocalTime cannot have a muted date-time object that shows a time, often viewed as hour-minute-second. Time is shown in nanosecond precision.
Learn more from
https://brainly.com/question/19639119
Place the steps for creating a subfolder in the inbox and moving a message into the new folder in order.
Name the new folder.
Click the message.
Drag and drop in the
folder.
Select New Folder.
Right-click on Inbox.
Answers
Right-click on Inbox
Select "New Folder"
Name the new folder
Click the message
Drag and drop in the folder
what is the best application to keep track of inventory for a store?
Answers
The best application to keep track of inventory for a store would depend on your specific needs and preferences. However, one highly recommended application is Square for Retail.
This user-friendly app helps manage your inventory efficiently by offering features such as real-time tracking, customizable alerts for low stock levels, and bulk item imports. Additionally, Square for Retail allows you to manage multiple store locations and can seamlessly integrate with Square's Point of Sale (POS) system. Another excellent option is Shopventory, which is compatible with popular POS systems like Square, Shopify, and Clover. Shopventory provides detailed analytics and inventory management track of inventory tools to streamline your store's operations. With automatic reordering, barcode scanning, and customizable reporting, Shopventory can significantly enhance your inventory management process. Both of these applications can effectively help you keep track of inventory for your store while offering unique features to cater to your specific requirements. Consider your store's size, operational needs, and the POS system you use when selecting the most suitable inventory management application.
Manual inventory inspections are no longer required thanks to perpetual inventory, a computerised point-of-sale system that constantly logs inventory changes in real time. It provides a very precise picture of changes in inventory coupled with instantaneous reporting of the amount of inventory in stock, accurately reflecting the quantity of goods on hand. By using this strategy, a company neglects to keep meticulous records of the goods it has on hand; instead, purchases are recorded as debits to the inventory database.The cost of products sold actually includes things like direct labour and material costs as well as direct factory overhead charges.
Learn more about track of inventory here
https://brainly.com/question/29031628
#SPJ11
how many different truth tables are there with 2 boolean variables, p and q (assuming the order of the truth values of p and q is fixed)?
Answers
There are 4 different truth tables with 2 boolean variables, p and q.
For two boolean variables, p and q, each variable can have two possible truth values: true (T) or false (F). Therefore, there are 2^2 = 4 possible combinations of truth values for p and q. These combinations form the rows of the truth table. The order of the truth values is fixed, meaning the first column represents the truth values of p and the second column represents the truth values of q. Hence, there are 4 different truth tables.
To know more about truth tables click here,
https://brainly.com/question/30588184
#SPJ11
Within the creditcard selection list add the following options and values: Credit Card Type (leave the value as an empty text string), American Express (value="amex"), Discover (value="disc"), MasterCard (value="master"), and Visa (value="visa").
Make the selection list and cardname field required.
Make the cardnumber field required and add the regular expression pattern indicated in the comment section of the HTML file to help ensure that a valid card number is used.
Within the cardmonth selection list add options for each month starting with the text Month and a value of a blank text string followed by the option text January (01) through December (12) with the corresponding values 01 through 12. Make the selection list required.
Within the cardyear selection list add options for each year starting with the text Year and a value of a blank text string followed by the option text 2020 through 2024 with the corresponding values 2020 through 2024.
Make the cardcsc field required with a maximum character length of 3 characters following the regular expression pattern: ^\d{3}$ .
Open the code7-3_valid.css file and add the following style rules to the file:
Display any input or select element that has the focus with a yellow background color.
Display any input element with invalid data in a red font, surrounded by a red border, and red box shadows that are offset 0 pixels horizontally and vertically with a shadow blur of 5 pixels.
Answers
Answer:
input:focus {
background-color: yellow;
}
input:invalid {
color: red;
border: 1px solid red;
box-shadow: 0 0 5px red;
}
Which of the following uses replication to Infect multiple computers?
Viruses
Trojan horse
Spyware
Worms
Answers
Answer:
Trojan horse
Explanation:
mostly all the above mentioned use replication to infect computers but the one that uses replication to invest multiple computers at a time is Trojan horse.
hope it helps .
Answer:
trojan house
Explanation:
i just took the house
which command creates a new table named ‘make’ that contains the fields ‘make_id’ and ‘year’?
Answers
The SQL command that creates a new table named 'make' with fields 'make_id' and 'year' would be:
e
CREATE TABLE make (
make_id INT,
year INT
);
This command creates a new table named 'make' with two fields: 'make_id' of type INT and 'year' of type INT. The CREATE TABLE statement is used to define and create a new table in a database. In this case, the table 'make' is created with the specified fields.
Please note that the exact syntax may vary slightly depending on the specific database management system (DBMS) you are using. The example provided follows the standard SQL syntax.
Learn more about SQL command here:
https://brainly.com/question/31852575
#SPJ11
which cables are immune to electromagnetic interference
Answers
Answer:
Fibre optic cables are non-metallic... they transmit signals using pulses of light in glass threads! As a result, they are immune to Electro-Magnetic Interference and Radio Frequency Interferenc